Digital Brand
Protection
Own Your Online Presence. Retain Trust. Stop phishing and impersonation campaigns at inception.
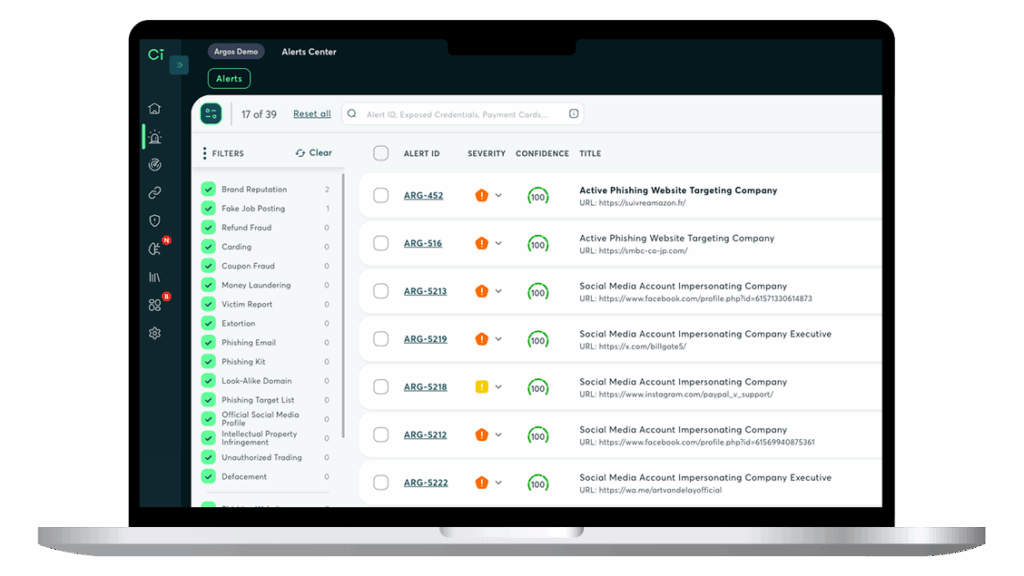
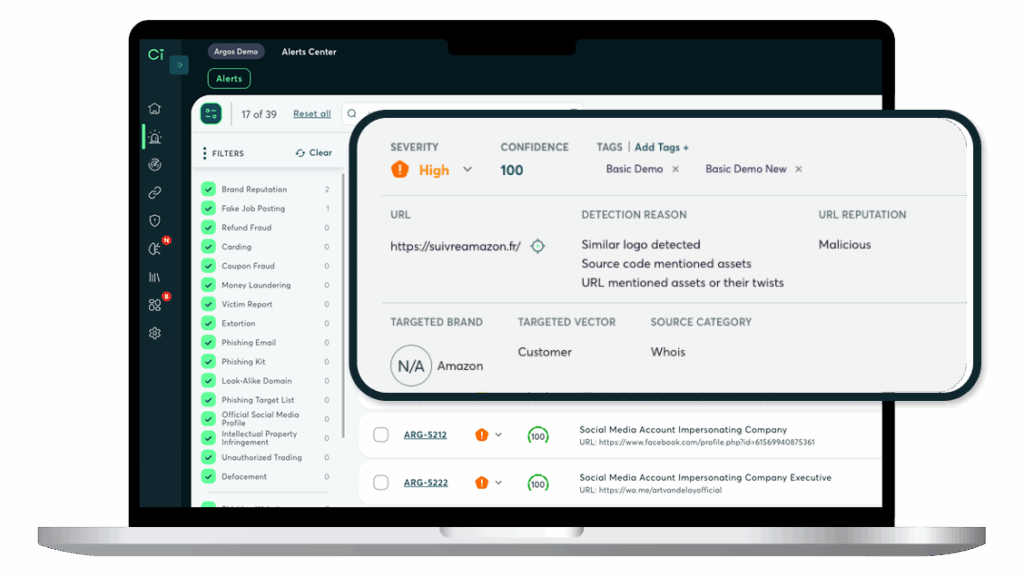
Experience how we intercept impersonations & phishing before an attack is executed
A zoom in on Cyberint’s Proprietry Phishing Beacon
66% of phishing URLs are created by copying the original page e.g. a public login page, rendering traditional phishing monitoring & prevention methods (e.g. typo-squat discovery methods, brand reconnaissance) irrelevant. Cyberint’s Phishing Beacon is a phishing detector that sends a signal within seconds of a clone of your legitimate website being published online.
How it works
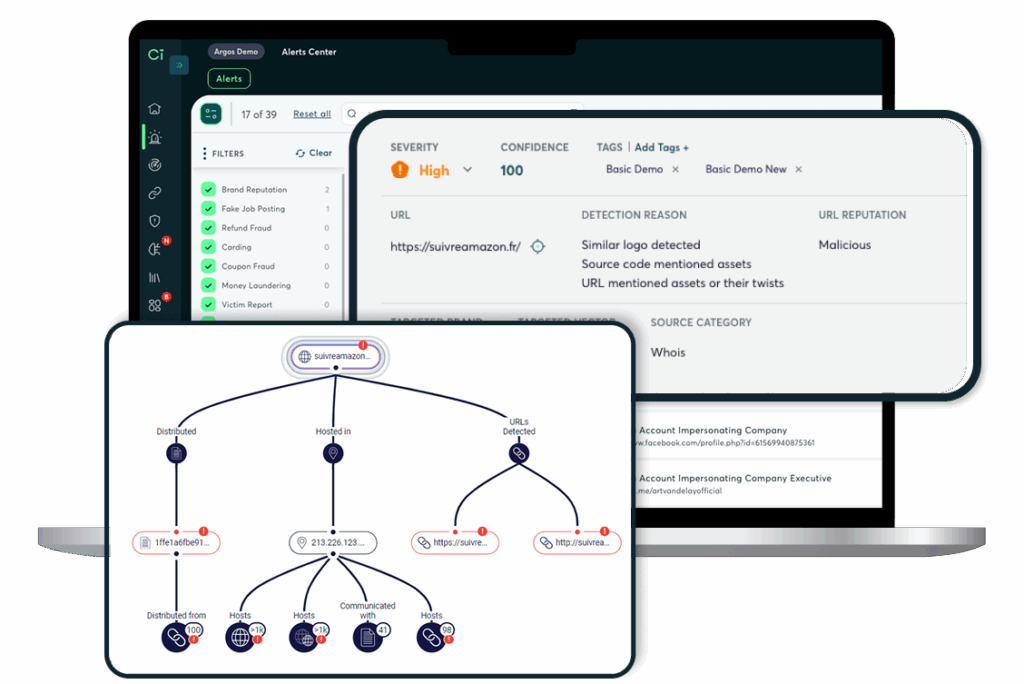
Uncover known and unknown assets and access points
Disrupt Threats Early In The Kill Chain
Detect Leaked Source Code, API Keys IP, and PII
Takedown Malicious Applications
Thwart Financial Scams
Resources
FAQs
What does the takedown process look like?
Cyberint, now a Check Point Company has an in-house remediation team specializing in takedowns. We have built relationships with a variety of hosting providers, registrars, social media platforms, and app stores around the world, and we have developed standardized procedures with these organizations. When a customer requests a takedown, a form is automatically filled out and sent from a Check Point email address to the relevant host, specifying the reasons for the request and the risks involved. Our team then monitors the requests, and customers can check the viewed in the “Takedown Requests” dashboard. We can take down phishing webpages, phishing domains, social media accounts, social media posts, pastesites, GitHub repositories, mobile applications, and more.
On average how long should a takedown take?
We pride ourselves on our success rate. More than 98% of our general takedown attempts are successful. That statistic rises to 99% for phishing takedowns. Not only that, but more than 70% are completed within 72 hours and our average MTTR is 23 hours.
Are there automated takedowns?
Yes, all our takedowns begin with an automated process of an email from a Check Point email address to a variety of hosting providers, registrars, social media platforms, and app stores. Once initiated, all takedowns are monitored in a “Takedown Request” dashboard by our analysts for progress.
Do you offer social media takedowns?
How often do you scan for phishing and brand impersonation?
How long have you been doing phishing monitoring?
Cyberint, now a Check Point company has been undertaking phishing monitoring and phishing takedowns for more than 10 years.