Deep & Dark Web Monitoring
We collect and analyze millions of elusive deep & dark web sources others miss, swiftly identifying leaked credentials, brand mentions, PII, and more. With virtual HUMINT, our powerful AI engines and analyst teams actively engage threat actor communities.
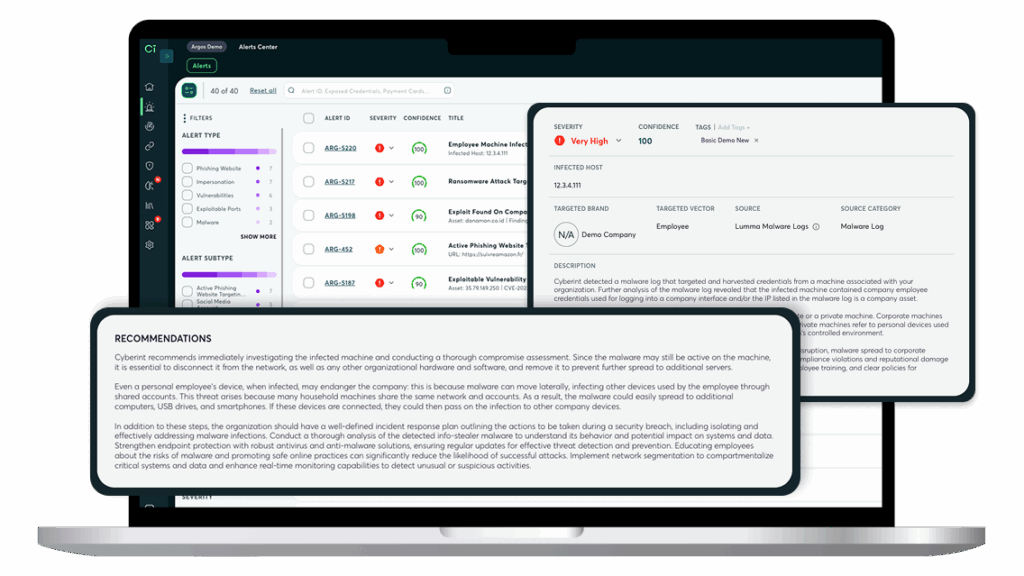
See the threat intelligence and deep & dark web monitoring solution in action
The Power of Dark Web Hunting
Elevate your cyber security program with the Cyber Hunting Tool. Understand your organization’s threat landscape, drill down into the threats you’re most likely to face, investigate targeted attacks, and hunt for threats that are evading detection.
How it works
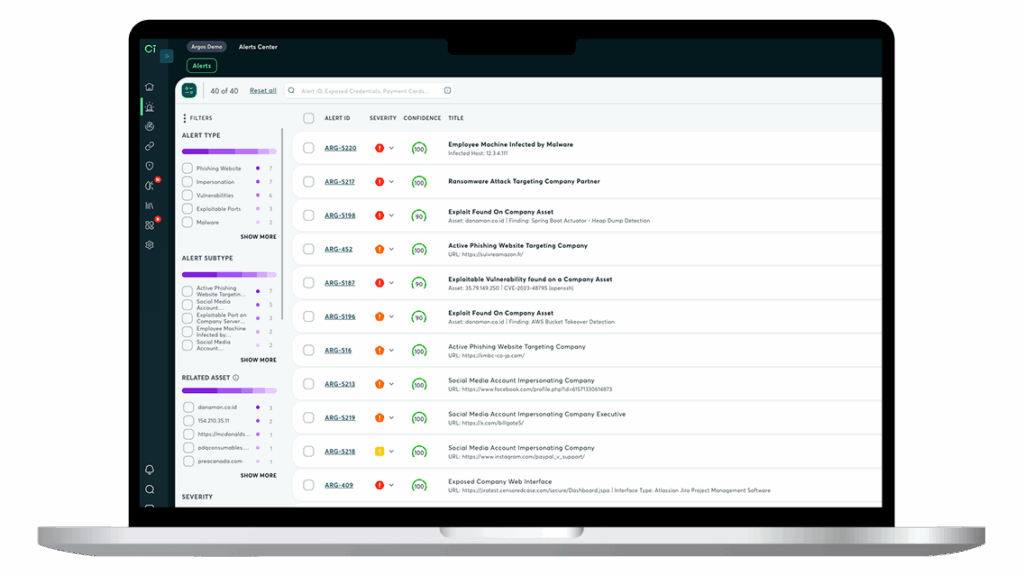
Uncover known and unknown assets and access points
Bypass the protective layer
Our dark web monitoring solution bypasses human authentication and trust mechanisms such as CAPTCHA etc. , using advanced crawlers and proxies. This enables data collection from thousands of relevant sources while maintaining anonymity. For restricted forums and sites, our analysts manage avatars to gain access.
Identify leaked data
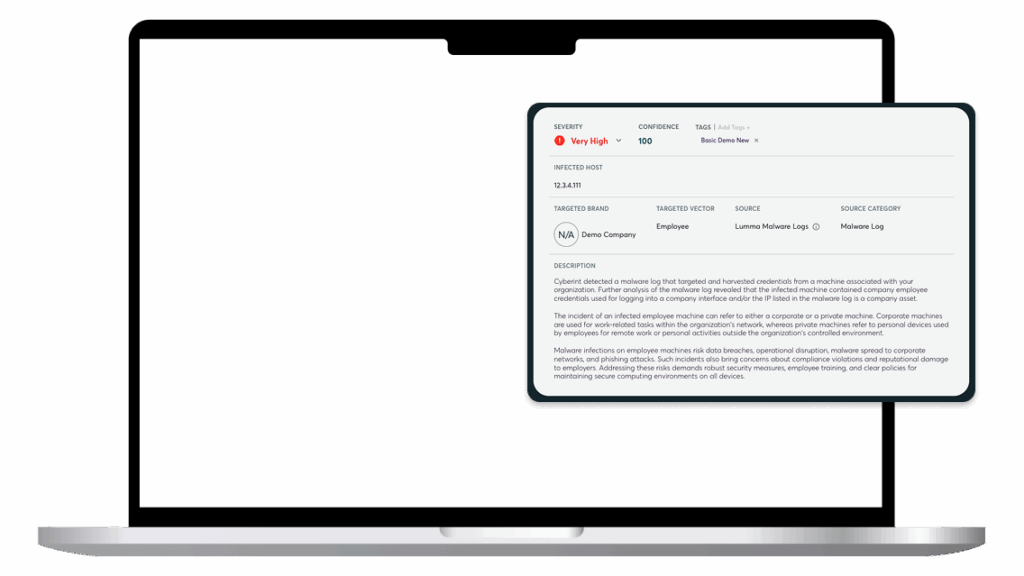
Discover employee & customer credential leaks on the deep and dark web. Determine the number of times each combination of email and password was seen, sources and recency. Act promptly to remediate malware infections, reset the credentials, and verify that they were not misused.
Determine the Source
Determine the origin of breaches. Leverage virtual HUMINT and dark web threat intelligence capabilities to confirm from the solution or the threat actor how these credentials were obtained and uncover malware infections of corporate and customer devices.
Prioritize for highest impact
Our proprietary AI correlates dark web intelligence with your assets, saving time. Tech and human expertise sanitize findings, delivering high-fidelity intelligence for maximum impact. Proactively assess and respond to physical and digital threats with skilled analysts.
Resources
FAQs
How intrusive is Cyberint’s external discovery process? When you scan is there any active testing?
Cyberint continuously discovers the open, deep and dark web to detect all of the external IT assets in a customer’s digital footprint. The process is fully automated and passive so it does not actively validate or test any security controls. The discovery process will not “set off any alarm bells” or give security teams the impression an attack is underway. There is no impact on normal operations.
There is an optional additional feature named active exposure validation, which we detail below that does actively validate.
Using publicly-available data, like DNS records, WHOIS data, and SSL certificates, Cyberint’s Attack Surface Management module is able to map out an organization’s external attack surface. All discovered assets are checked for common security issues. The categories of assets detected are: IP addresses, domains, subdomains, cloud storage, and organizations (i.e. trademarked brands).
These are the types of security issues we identify:
- Certificate Authority issues
- Compromised Credentials
- Email Security issues
- Exploitable Ports
- Exposed Cloud Storage
- Exposed Web Interfaces
- Hijackable Subdomains
- Mail Servers In Blocklist
- SSL/TLS issues
About Active Exposure Validation (AEV): Cyberint’s AEV capability goes beyond typical CVE detection to actively test for exploitability. AEV also performs other automated tests to uncover common security issues in your organization’s digital assets that fall outside the scope of a vulnerability database. Alerts are issued in real time so you can quickly identify and remediate your most urgent risks. AEV enables the crucial validation step to be tackled in the CTEM framework.
My company has many different brands, can I monitor them individually?
Yes, as our platform is multi-tenant, we can set up an Attack Surface Management (ASM) instance for each brand and monitor the brands separately.
Can you automate actions based on alerts and integrate with other tools?
Yes. All alerts can be automatically sent to SIEM/SOAR platforms to trigger automated playbooks. We have an API that can integrate our information into existing SIEM/SOAR solutions and corelate with information from other intelligence platforms. We also integrate with Splunk, Azure AD, AWS, JIRA, OKTA, Qradar, XSOAR out of the box.
We know also have a Threat Intelligence Platform that combines and prioritizes different threat intel feeds and sends to SIEM/SOAR solutions to remediate.
What sources do you cover?
We cover thousands of sources from the clear, deep, and dark web. We cover:
- Search engines such as Bing and Google
- All the major cybercrime forums such as Breach Forums etc.
- Instant messaging platforms such as Telegram & Discord
- Social media
- Blogs
- GitHub and other pastesites
- Application stores
- File sharing websites
- Security Feeds
- Data leakage sites
- Credit Card stores
- Blackmarkets such as RussianMarket and 2easy.shop
- Malware logs
- Dark networks
and more. 5% of our sources are considered “Dark web”. The rest are in the clear/deep web.
How often do you crawl and scrape your sources? And how do you evade detection?
Each source is crawled and scraped according to the allowed policies on it. For example, if a dark web forum is monitored for suspicious scraping activity, we will make sure we collect information at a pace that does not raise any suspicion. We try to keep each source up to date with no longer than a week between each scraping (often much much more).
How do you deal with language barriers?
We have automated translation mechanisms in place and our the Cyberint team speaks over 22 languages fluently, including Russian, Arabic, English, Chinese, Japanese, Filipino languages like Tagalog, Ilocano and Ilonggo and more.
Can you add new sources on demand?
Our sources team is constantly looking for and adding more sources. Every request is examined by the team and we are more than happy to add additional sources that can provide value to our customers. The turn-around time for adding a source is relatively short (1-4 weeks usually).
Do you create generic threat reports?
Check Point has a very experienced research team that tracks global threat events and releases periodic research reports. Every major global event that occurs is covered by the Cyberint/Check Point research team. – For example, we have published report on: Scattered Spider, The Russian – Ukraine war, the Log4shell vulnerability, specific Ransomware groups tracking and more.
Do you create dedicated reports for my company?
Our research team can create reports on any desired subject, using “investigation hours”. Each customer can purchase these hours and each research is priced based on the number of hours required to complete it. The subjects vary between VIP exposure reports, industry related threats, Incident response, Deep investigations and more