


On September 8, 2025, the JavaScript ecosystem experienced what is now considered the largest supply chain attack in npm history. A sophisticated phishing campaign led to the compromise of a trusted maintainer’s account, resulting in the injection of cryptocurrency-stealing malware into 18+ foundational npm packages. These packages collectively accounted for over 2 billion weekly downloads, affecting millions of applications globally—from personal projects to enterprise-grade systems.
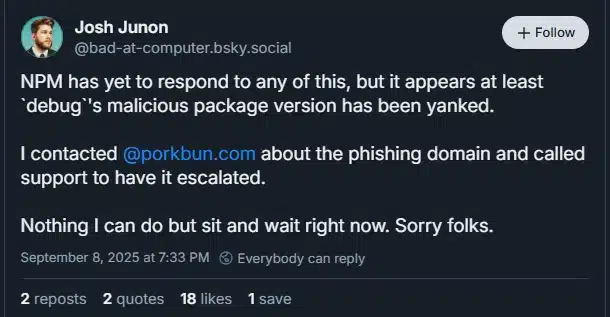
Following the discovery of the breach, the npm team began removing several of the malicious package versions published by the attackers, including the compromised debug package, which alone sees over 357 million downloads each week.
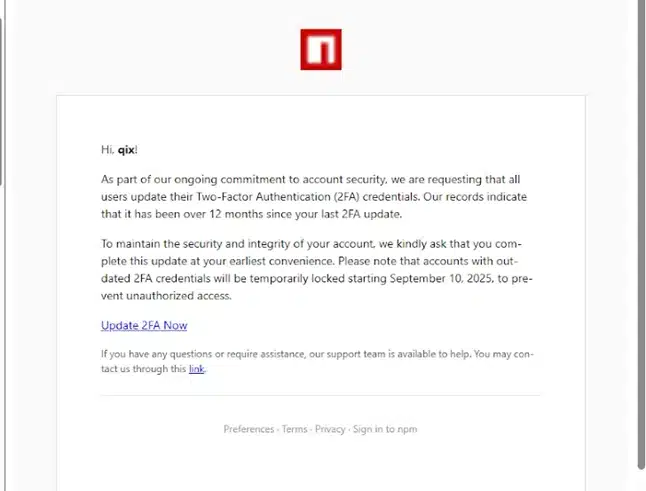
The attack began when Josh Junon, a prolific open-source maintainer known as Qix-, received a phishing email impersonating npm support. The email, sent from support@npmjs.help (a domain registered just three days earlier), warned that his account would be locked unless he updated his 2FA credentials within 48 hours.
Under pressure and during what he described as a “panicky morning,” Junon clicked the link and entered his credentials. This gave the attackers full access to his npm account. Within minutes, they began publishing malicious versions of his packages.
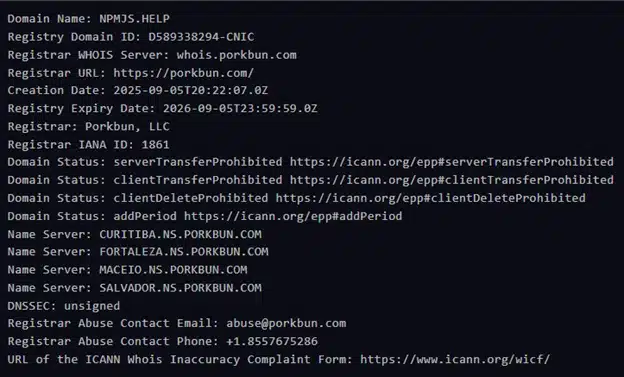
The threat actor opened a new domain – “npmjs.help” on September 5th, 3 days before the event occurred. At the time of writing, this domain is no longer accessible, but records show that it once resolved to 185.7.81.108.
This email contained a link to https://www.npmjs[.]help/settings/qix/tfa/manageTfa?action=setup-totp, which loaded content from two attacker-controlled BunnyCDN buckets: static-mw-host.b-cdn[.]net and img-data-backup.b-cdn[.]net.
One of the scripts loaded was the credential stealer, which can be found here. This is a simple script which stores the provided username, password, and 2FA code, and sends it to a remote host at websocket-api2.publicvm[.]com.
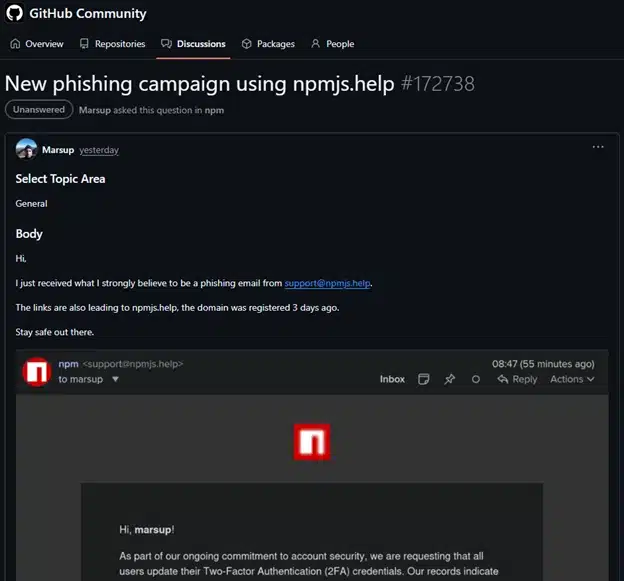
Reports from recipients of the phishing message indicate that the campaign also targeted other package maintainers and developers who shared the same email domain or address format.
The compromised packages included some of the most widely used utilities in the JavaScript ecosystem:
These packages are deeply embedded in thousands of other npm modules, creating a massive blast radius.
The injected malware was browser-specific and designed to steal cryptocurrency in two primary ways:
A deep dive into the obfuscated malware injected into several popular NPM packages reveals a highly sophisticated browser-based attack targeting cryptocurrency transactions. The malicious code was engineered to intercept outgoing wallet transactions and covertly replace the destination address with one controlled by the attacker. This substitution is made deceptively subtle by using the Levenshtein distance algorithm to select attacker-controlled addresses that closely resemble the original, making manual detection difficult.
According to Charlie Eriksen from Aikido Security, the malware functions as a multi-layered interceptor. It hijacks both network traffic and application APIs, including window.fetch, XMLHttpRequest, and window.ethereum.request, as well as other wallet provider interfaces. This enables it to manipulate both the data being sent and the responses received, effectively rewriting transaction details in real time.
The payload begins by verifying it’s running in a browser environment (typeof window !== ‘undefined’) and then hooks into critical APIs. If a user visits a site that includes the compromised code and has a connected wallet (e.g., MetaMask or Phantom), the malware can intercept and alter transactions before they are signed. While developers aren’t the primary targets, they can still be affected if they connect wallets while testing or browsing affected sites.
Aikido Security detected the attack within 5 minutes of the first malicious package being published. Their systems flagged unusual behavior in build pipelines, including ReferenceError: fetch is not defined—a result of the malware trying to run in Node.js environments.
For Developers & Teams:
For End Users:
http://npmjs.help/
https://uixie.npmjs.help/
https://npmjs.help/
http://support@npmjs.help/
https://www.npmjs.help/
npmjs.help
185.7.81.108
support@npmjs.help
Cyberint, otherwise known as Check Point External Risk Management, reduces risk by helping organizations detect and mitigate external cyber threats before they have an adverse impact.
The solution provides superior visibility through continuous discovery of the evolving attack surface, combined with the automated collection and analysis of vast quantities of intelligence from across the open, deep and dark web.

©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


