I love to get stuck in and let the creative juices flow. My strengths lie in idea generation, development and execution. Over 5 years experience in B2B cybersecurity. I reign supreme when my imagination and creativity can run wild.
One of the most pressing cyber threats businesses face today is the rampant rise in leaked credentials. Data from Cyberint, a Check Point company, reveals a staggering 160% increase in leaked credentials so far in 2025 compared to 2024. This isn’t just a statistic; it’s a direct threat to your organization’s security.
Late last year, we reported 14,000 cases in just 1 month where our customers’ employee credentials, even those adhering to company password policies, were exposed in data breaches – a clear indicator of real and present risk.
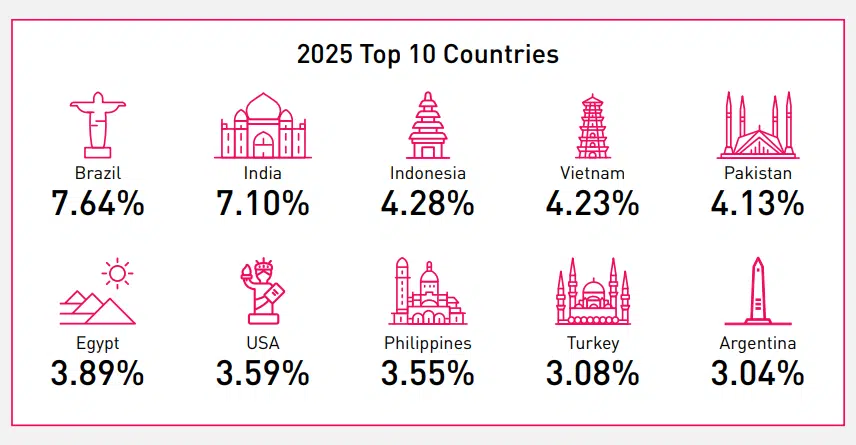
top 10 countries being targeted by ransomware attacks
One of the most pressing cyber threats businesses face today is the rampant rise in leaked credentials. Data from Cyberint, a Check Point company, reveals a staggering 160% increase in leaked credentials so far in 2025 compared to 2024. This isn’t just a statistic; it’s a direct threat to your organization’s security.

Protecting your organization requires a multi-layered approach:
Crucially, detecting leaked credentials before they are abused is paramount. Threat actors often don’t immediately exploit stolen logins; they take time to analyze the data. Effective detection methods include:
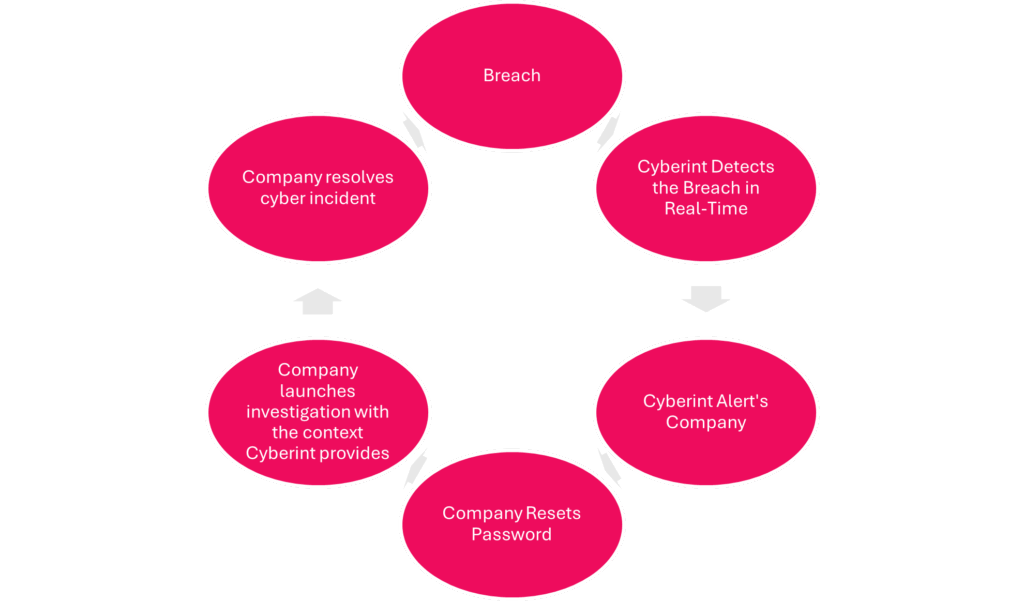
The leaked credential mitigation cycle
When it comes to detecting credential leaks that impact your company or customers, Cyberint, now a Check Point company, offers comprehensive solutions.
Beyond scanning the deep and dark webs for leaked credentials, Cyberint conducts undercover investigations to verify threats and assess their scope. Cyberint also integrates with SIEM and SOAR tools, enabling fast, automated notifications when leaked credentials appear. Businesses can also configure automated remediations, such as immediately requiring employees to update passwords when credential theft is detected.
These protections extend beyond corporate devices to personal computers. Cyberint can detect instances where employees use company accounts on personal devices, even when endpoint monitoring and security tools are absent – a critical capability given that 46% of devices associated with leaked corporate credentials lack such tools, according to Cyberint data.

©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start