


While major commercial banks have significantly hardened their digital perimeters, Check Point analysts have identified a persistent defensive maturity gap within the Philippine rural banking sector. Local threat actors, such as the individual or group identified as X3v0, are increasingly focusing their efforts on these regional institutions, capitalizing on the assumption that smaller banks often lack the sophisticated monitoring of their urban counterparts.
A recent public disclosure reveals that a local rural bank’s loan portal was compromised using a common web exploit. This allowed the attacker to bypass authentication and exfiltrate the bank’s entire user database. This report highlights that no institution is too small to be a target, and legacy web technologies remain the primary open door for cybercrime within the country’s financial ecosystem.
In late December 2025, the threat actor X3v0 published evidence confirming a successful compromise of a Philippine rural financial institution. The disseminated data included administrative directory structures and Bcrypt-protected credential sets, validating that the actor obtained unauthorized access to the bank’s backend database.
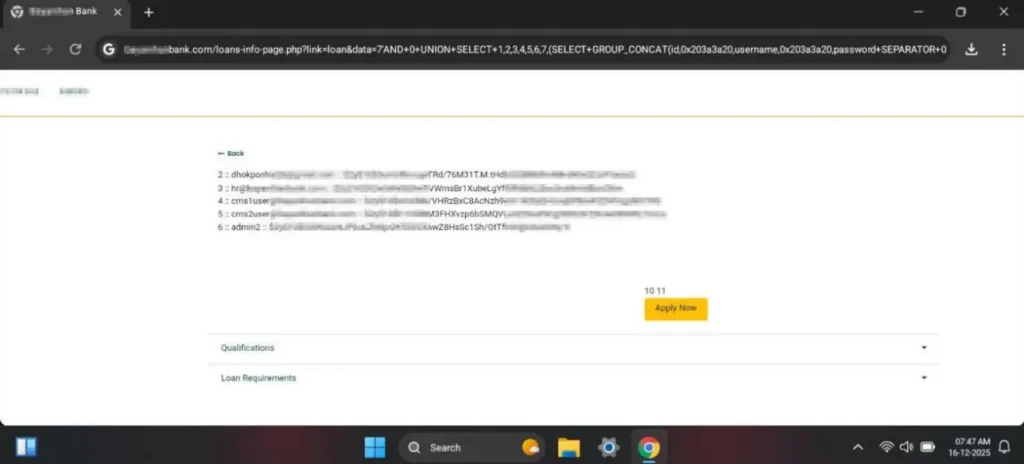
Check Point assesses that this public disclosure serves a dual purpose: it acts as reputational leverage for the actor and provides a tactical template for other opportunistic entities targeting the rural banking sector.
The evidence from the disclosure reveals that the bank was victim to a Union-Based SQL Injection (SQLi). This is an “in-band” attack where the threat actor uses the website’s own communication channel to trick the database into revealing hidden information.
Analysis of the Exploitation:
The compromise of a rural bank has consequences that reach far beyond its local branches:
Check Point assesses that this breach was entirely preventable through standard security hygiene. We recommend the following immediate actions for rural financial institutions:
Check Point’s External Risk Management solution is built to uncover threats before they cause damage. By continuously monitoring forums, credential abuse, and chatter across the open, deep and dark web, the team can detect campaigns in their earliest stages. The platform’s ability to correlate indicators across multiple clusters—ads, domains, Telegram activity, and more—helps link disparate attacks to a single network. That’s how we move fast, disrupt infrastructure, and protect organizations.

©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


