


Identified as targeting cryptocurrency users through nefarious cross-platform applications, a remote access trojan (RAT) dubbed ‘ElectroRAT’ has recently been in the headlines following an investigation into the threat by researchers at Intezer.
Believed active since at least January 2020, although only discovered in December 2020, those behind this RAT campaign have been observed as creating fake cryptocurrency gambling and trading applications that have been pushed through various forum and social media posts in an attempt to lure victims into installing the malicious payload.
Given the obvious cryptocurrency links, the financially-motivated final objective appears to be the theft of cryptocurrency wallets although functionality present within the RAT could facilitate the deployment of additional threats.
Ultimately delivered as a fake application, those behind this campaign have attempted to make their lures convincing through the creation of legitimate-looking websites (Figure 1) and domains.
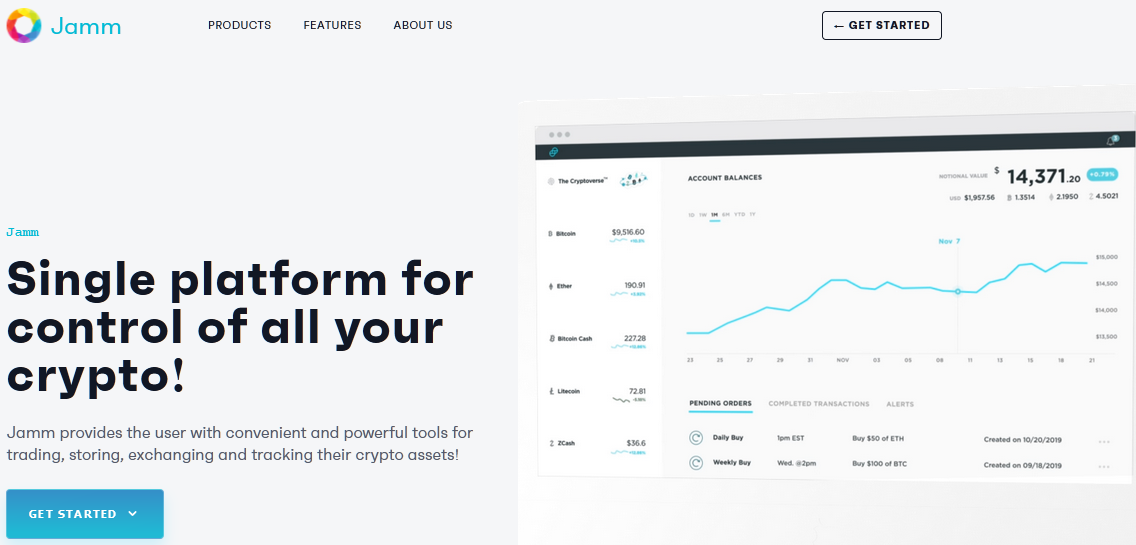 Figure 1 – ‘Jamm’ fake application lure website
Figure 1 – ‘Jamm’ fake application lure website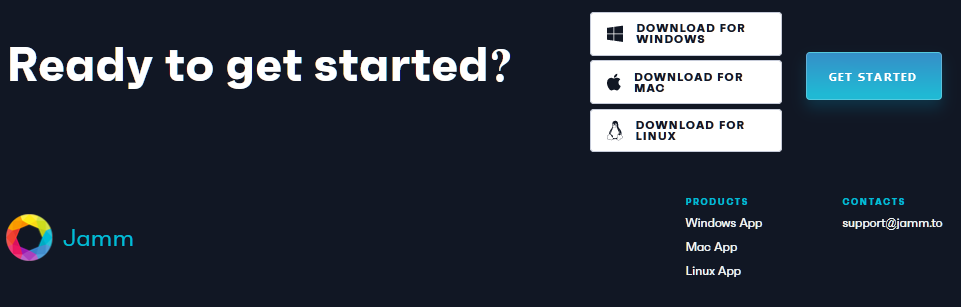 Figure 2 – ‘Jamm’ cross-platform download options
Figure 2 – ‘Jamm’ cross-platform download optionsIn order to drive victims to these websites, the threat actors behind this campaign created a variety of personas on cryptocurrency forums and social media groups in order to post messages (Figure 3 & 4) encouraging others to visit their lure websites and download the malicious applications.
In addition to domains identified by Intezer, two additional suspicious domains consistent with the cryptocurrency theme can be identified through passive DNS (pDNS) records associated with the IP addresses 213[.]226[.]100[.]140 and 213[.]226[.]100[.]143. Based on these IP addresses resolving to the lure domains identified by Intezer, two additional suspicious domains consistent with the cryptocurrency theme were identified through passive DNS (pDNS) records as resolving to 213[.]226[.]100[.]140 and 213[.]226[.]100[.]143:
cryptopro[.]tradetradecryptoblog[.]infoNotably these IP addresses have also been observed as command and control (C2) servers.
Of the two additional domains, cryptopro[.]trade appears to have been active during July 2020 and, based on cached search results, was associated with the malicious application ‘Jamm’ (Figure 5).
Likely in an attempt to increase the potential victim pool, these fake applications have been created in ‘Electron’, a cross-platform framework that supports web technologies such as HTML and JavaScript, and as such are able to target users of Apple macOS, Microsoft Windows and Linux.
Having lured the victim into downloading and installing (Figure 6) the initial cryptocurrency-related application, ElectroRAT is executed in the background whilst a decoy user interface is displayed. Notably, and to support cross-platform targets, the RAT was created anew using the opensource programming language ‘Go’ (sometimes referred to as ‘Golang’ based on the official domain) and includes common functionality including the ability to log keystrokes, capture screenshots, execute commands and download or upload files.
In the case of the fake ‘eTrader’ application, the victim is then prompted to create an account and enter a passcode (Figure 7), steps that appear somewhat benign and combine to make the application appear legitimate.
Whilst the victim is distracted, the ElectroRAT payload is dropped and executed by launching the appropriate operating system shell in a detached process with the window hidden as can be seen by unpacking the fake application to reveal the Electron JavaScript file electron.js (Figure 8).
Notably, further analysis of the Electron assets identify mentions (Figure 9) of a seemingly legitimate cryptocurrency trading application ‘Kattana’ and may suggest that this fake application is derived from the Kattana Electron package, available for macOS and Windows, especially given similarities in the user interface (Figure 10).
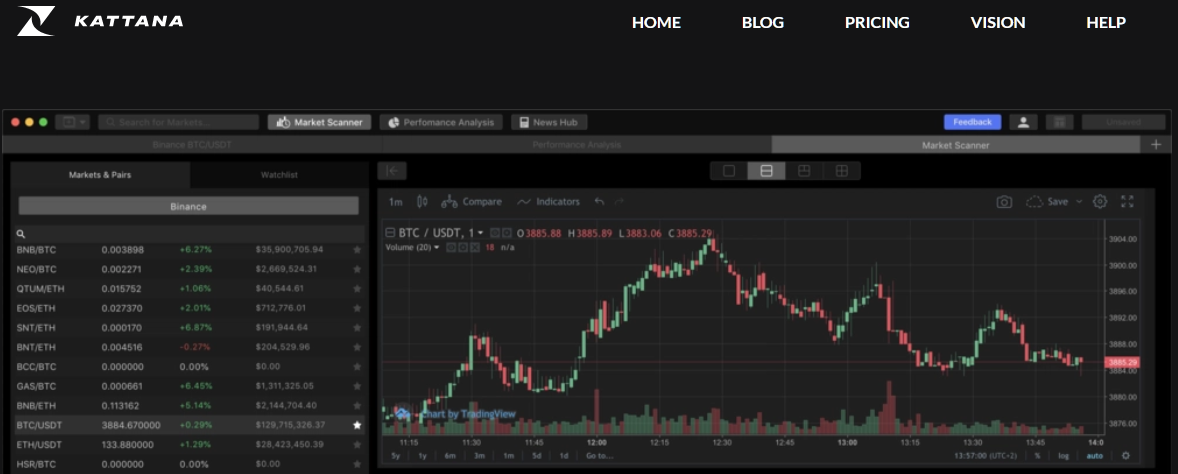
Maintaining support for these cross-platform targets, the remote access trojan (RAT) has been created using the opensource programming language ‘Go’ (sometimes referred to as ‘Golang’ based on the official domain) and, as is to be expected, contains common functionality including the ability to log keystrokes, capture screenshots, execute commands and download or upload files.
Continuing with the decoy element, the fake application seemingly uses real-world data to display convincing content (Figure 11) and seemingly mimics the Kattana application including some interaction to dispel any suspicion.
Somewhat appearing to be an attempt to gather credentials, or more specifically API keys and secrets, the ‘Performance Analysis’ tab of this fake application allows them to ‘connect’ their cryptocurrency exchange accounts (Figure 12).
Upon inspection of the code related to this prompt suggests that rather than exfiltrating the API credentials this functionality was cloned from Kattana and does not appear to function when tested. Regardless of this, the RAT element of this attack remains present in the background and does feature a keylogging capability which would presumably allow this data to be collected via other means.
Command and control (C2) activity commences with a HTTP POST beacon sent by the fake application, containing victim identifiers, being sent to a /user resource on host via TCP port 3000 and appears to utilize the same servers that host the fake application lure website.
Based on these observed communications, this initial beacon utilizes a default user-agent string of go-resty/1.12.0 (<https://github.com/go-resty/resty>) and posts JSON content with the following fields:
Once received, the C2 server responds with an apparently empty JSON response (Figure 13).
Whilst not confirmed, the beacon sent by the fake application may serve as a campaign tracker rather than being used to directly control the ElectroRAT payload.
Subsequently, ElectroRAT has been observed as obtaining its C2 IP addresses by requesting ‘raw’ text content from the legitimate text sharing website ‘Pastebin’ and posted by an account named ‘Execmac’. Reassuringly, at the time of writing, this account has been suspended and therefore the threat actor behind this campaign will need to update the configuration of the ElectroRAT payload and repackage this within fake applications in order to continue to infect new victims.
In addition to the indicators of compromise (IOC) published by Intezer, the following IOC have been observed.
e5f9fc82501da0c24d85851150c91618416506e4c8c7876728d2af8d9848c5e5b3bc325abf597e745db0d6aae178b85622527d9e3e619daab62b1b4918b639bc303acba187a409fdcc55731966ca38a7175e074ec2f272c9895b133f86b445371438833028dab0f8ea713b2f53e9c81de1a39ff6c811e1fa20f478b802ff094da32ef780ba235f8222c05302f7537b4123c41b048449c6ec8744d64103d428a34953c8b3ed37c786c6a085e7642984e3250c0d93f8f22f829a1a194b6ae4a64dba65505ffa1a92169c81e5a5994eeb23a2592425abebf78d1ec5179869412a5417b0b1a9271683f30e5bfd92eec9c0a917755f54060ef40d9bd0f12e927f540fC:\Windows\system32\cmd.exe /d /s /c ""%LOCALAPPDATA%\Programs\e-trader\Utils\mdworker.exe""/bin/sh -c /Volumes/eTrader 0.1.0/eTrader.app/Contents/Utils/mdworker213[.]226[.]100[.]140213[.]226[.]100[.]143cryptopro[.]tradetradecryptoblog[.]infogo-resty/1.12.0 (<https://github.com/go-resty/resty>)©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


