



I love to get stuck in and let the creative juices flow. My strengths lie in idea generation, development and execution. Over 5 years experience in B2B cybersecurity. I reign supreme when my imagination and creativity can run wild.
How Cyberint, now a Check Point Company, supports organisations working towards cyber resilience
The UK’s Cyber Assessment Framework (CAF) was developed by the National Cyber Security Centre (NCSC) to help essential service providers and other organisations assess and improve their cyber resilience. It is especially relevant to those operating under the Network and Information Systems (NIS) Regulations, but its principles are applicable across sectors.
CAF consists of four top-level objectives, broken down into 14 principles. Each principle contains a series of outcomes that organisations can assess themselves against. The focus is not just on technical defences, but also governance, operational response, and supply chain awareness.
While its primary audience includes those delivering essential functions—such as designated Critical National Infrastructure (CNI) services under the NIS Regulations, or services tied to public safety, industrial operations, or transport—it is also widely adopted by other sectors. An organisation responsible for an essential function may be one that owns or operates an element of the CNI, has been designated as an Operator of Essential Services, or falls under cyber safety regulation more broadly.
In practice, CAF is used by both public and private sector entities to structure cyber security improvements, demonstrate good governance, and support regulatory alignment. It is especially useful for CISOs, security leads, audit teams, and risk owners seeking a measurable and outcome-focused model.
Cyberint (now a Check Point Company) offers external threat intelligence capabilities that contribute meaningfully across multiple CAF principles—providing visibility, context, and early warning to reduce risk before it becomes an incident.
In this blog we will deep dive into the 4 objectives and how we align.
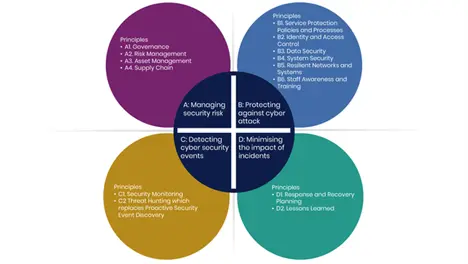
This objective focuses on governance, risk management, and supply chain oversight.
It ensures that cyber risks are actively managed at all levels, supported by strong governance, clear roles, and informed decision-making. It also addresses how asset and supply chain risks are understood and monitored. The emphasis is on embedding cyber risk into broader business risk processes, ensuring that the right people have the right information to make timely decisions, and that external dependencies are not a blind spot.
Key quotes that relate to what Cyberint, a Check Point Company does:
“A good understanding of the threat landscape and the vulnerabilities that may be exploited is essential to effectively identify and manage risks.”
“You understand the capabilities, methods and techniques of threat actors and what network and information systems they may compromise to adversely impact your essential function(s).”
“Whichever risk management method your organisation uses, asset management will play a key role as you cannot effectively manage risks without understanding what assets are part of the essential function.”
“You have a deep understanding of your supply chain, including sub-contractors and the wider risks it faces.”
Cyberint supports this by:
Here, the emphasis is on protecting systems and services from compromise. It focuses on implementing proportionate and effective controls to prevent unauthorized access, misuse, or compromise of systems and data. This includes everything from IAM, endpoint protection and secure configurations to network segmentation and patch management. The last principle focuses on security awareness and training. The principle recognizes that complete prevention is unrealistic, but a strong foundation of technical measures can significantly reduce risk of successful compromise.
Key quotes that relate to what Cyberint, a Check Point Company does:
“You have a good understanding of data important to the operation of the essential function(s), where it is stored, where it travels and how unavailability or unauthorised access, modification or deletion would adversely impact the essential function(s).”
“Organisations should protect networks and information systems from attacks that seek to exploit software vulnerabilities (flaws in software).”
“The latest mitigated vulnerabilities are often published by vendors, some providing automatic update functionality. Other vulnerabilities can be discovered through threat intelligence sources.”
Cyberint enhances this area through:
Example: In one customer deployment, Cyberint detected leaked VPN credentials within 24 hours of publication on a dark web forum, enabling credential revocation before misuse.
This objective assesses an organisation’s ability to detect attacks in a timely manner. Even with strong preventative controls, organizations must be able to detect when something goes wrong. This objective covers the capabilities required to monitor systems, identify anomalies, and recognize signs of compromise. Detection must be timely, accurate, and continuous—and ideally, it should surface events that warrant response before they become full-blown incidents.
Key quotes that relate to what Cyberint, a Check Point Company does:
“An effective monitoring strategy is required so that potential security incidents are discovered and there are appropriate processes in place to assist with a response.”
“Threat intelligence can come in many formats, volumes and quality. It can be collected from open discussion forums, trusted relationships, paid-for contracts with threat intelligence companies or generated internally.
Threat intelligence can be either automated feeds that describe Indicators of Compromise or more descriptive human readable reports. You will likely need to consume various types (e.g strategic, operational and tactical) of both internally and externally produced threat intelligence.
We would recommend that if choosing automated threat intelligence feeds you favour quality over quantity (false positives can be costly for analyst’s time) and ensure the feeds can be automatically ingested by your chosen analysis platform and made available to the necessary users as appropriate.”
Cyberint contributes by:
The final objective is focused on resilience—how quickly and effectively an organization can respond to and recover from cyber attacks. It includes the development and rehearsal of response plans, timely incident notification, communication strategies, and post-incident review. The goal is to minimize disruption, protect critical functions, and ensure lessons are captured to strengthen future defenses. The uses of Cyberint, a Check Point Company are more restricted here, but use can be made of analysts and playbooks at hand.
Cyberint supports this with:
| CAF Objective | CAF Principle | Cyberint, now a Check Point Company’s Contribution |
|---|---|---|
| A. Managing Security Risk | A.2 Risk Management | Threat-led insights into relevant attack trends; Threat Landscape Dashboard; Malware and Threat Actor intelligence. |
| A. Managing Security Risk | A.3 Asset Management | Alerts tied to exposed domains, assets, and credentials (this principle focuses more on physical assets, but digital assets are just as important). |
| A. Managing Security Risk | A.4 Supply Chain | Monitoring for third-party mentions and risks. |
| B. Protecting Against Cyber Attack | B.2 Identity & Access | Compromised credential detection and exposure alerts. |
| B. Protecting Against Cyber Attack | B.3 Data Security | Discovery of data leakage across underground channels. |
| B. Protecting Against Cyber Attack | B.4 System Security | Tracking of vulnerabilities related to your assets and prioritization by those exploited in the wild. |
| C. Detecting Cyber Security Events | C.1 Security Monitoring | Surface and dark web monitoring for attacker activity. |
| C. Detecting Cyber Security Events | C.2 Threat Hunting | Threat Hunting module with access to the threat knowledgebase, forensic canvas, and raw data lake. |
| D. Minimising Impact of Incidents | D.1 Response Planning | Playbooks tailored to ransomware, advanced persistent threats (APTs), and fraud cases. |
| D. Minimising Impact of Incidents | D.2 Lessons Learned | Analyst support for impact review and threat modelling. |
This coverage ensures that Cyberint is not just a source of alerts—it’s an operational partner across security, risk, and governance. Intelligence is delivered in the right format, to the right team, with the depth needed to take action immediately or build resilience over time.
Cyberint helps organisations detect and respond to external threats before they escalate into impact. Now operating as Check Point Intelligence, our capabilities are amplified by Check Point’s ThreatCloud AI—one of the world’s largest collaborative threat intelligence networks.
ThreatCloud AI enhances Cyberint’s coverage with:
Together, this combined solution provides:
Whether aligning to the NCSC Cyber Assessment Framework (CAF) or other global standards like NIST, ISO 27001, or DORA, Cyberint and Check Point provide the insight needed to make timely decisions and defend proactively—at every level of the organisation.
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


