



Experienced in various public diplomacy projects, OSINT, WEBINT, analytical research, troubleshooting, intelligence gathering, auditing, and more.
These days, the most worrisome phishing threats against businesses often don’t arrive via email. Instead, threat actors are increasingly turning to phishing variations in the form of vishing and smishing—techniques that use alternative communication channels to deliver messages designed to elicit or outright steal sensitive information from employees or customers. These attacks often leverage social engineering, malicious links, and other tactics. Specifically, they rely on SMS messages (in the case of smishing) and phone calls or voicemail (for vishing) to reach their targets.
Although smishing and vishing were historically not major threats compared to email-based phishing attacks, data suggests that this is changing. Although traditional phishing remains a steady pervasive threat as seen below in the graph from the 2024 APWG Phishing Report:
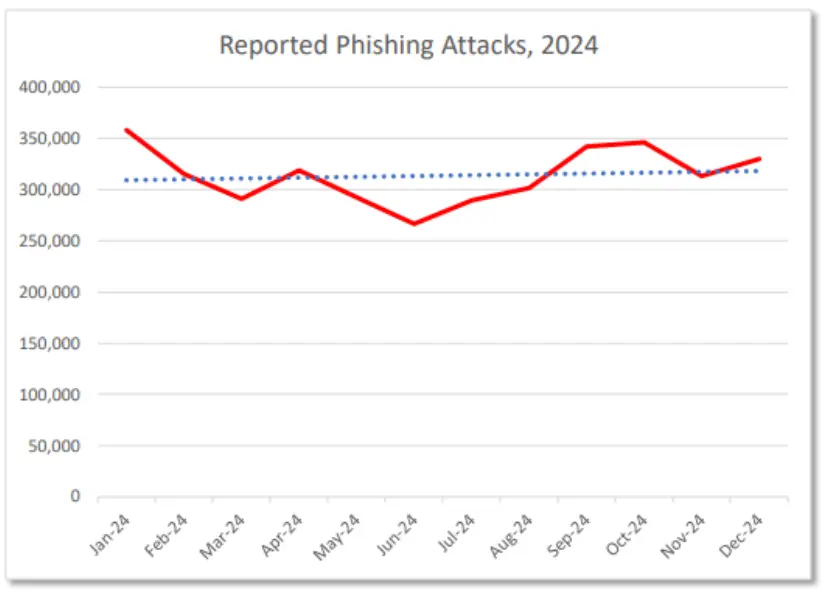
Vishing and smishing are experiencing rapid growth at present. The frequency of vishing attacks surged by 442 percent in the second quarter of 2024. The rate of smishing incidents has also risen steadily since the start of this decade.
In light of these trends, businesses must now grapple with some key questions: Why are threat actors now making such extensive use of smishing and vishing? And what can organizations do to protect themselves in a world where traditional email scams are not the only type of phishing threat they need to worry about?
Smishing and (especially) vishing offer threat actors powerful opportunities for impersonating individuals whom their targets are inclined to trust. For instance, vishing attacks sometimes involve placing phone calls to employees and posing as IT support staff in an effort to trick the workers into handing over login information. In other cases, the attacks impersonate company officials or executives.
These attack methods make smishing and vishing more difficult for some employees (especially those who are less tech-savvy) to recognize. Traditional phishing mitigation tips, such as not trusting emails that are full of typos, are less effective against smishing and vishing.
Read on for answers as we explore smishing and vishing trends in 2025, along with mitigation strategies.
Smishing and vishing are both types of phishing attacks where threat actors impersonate legitimate entities to trick victims into revealing sensitive information or carrying out other malicious actions. This could include things like downloading malware, changing invoice details to redirect payments, and many more harmful schemes.
Historically, most phishing attacks took place via email. Smishing and vishing leverage alternative attack channels. Specifically, smishing uses SMS messages, while vishing uses voice communications (i.e., phone calls, voice mai or video calls).
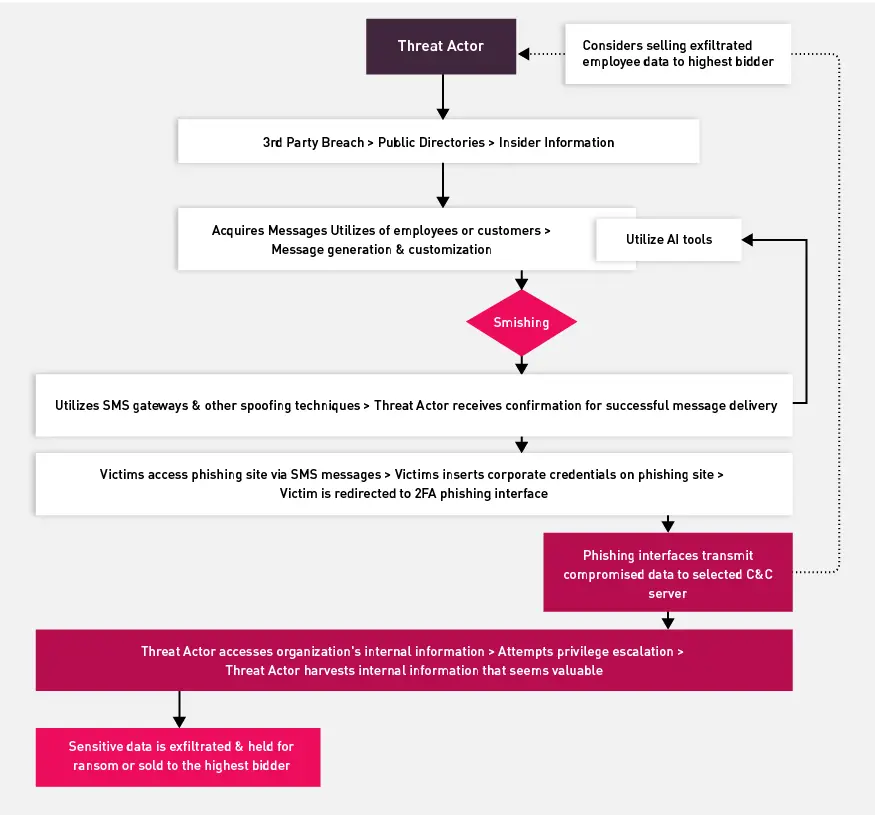
The way the attacks play out (which is illustrated in the following images) is very similar to email-based phishing in most ways. Threat actors start by finding targets and crafting content designed to trick the targets into handing over sensitive data. The delivery of the content varies, of course, because smishing uses text messages to reach users and vishing uses voice communications.
Flow of a smishing attack:
Flow of a vishing attack:
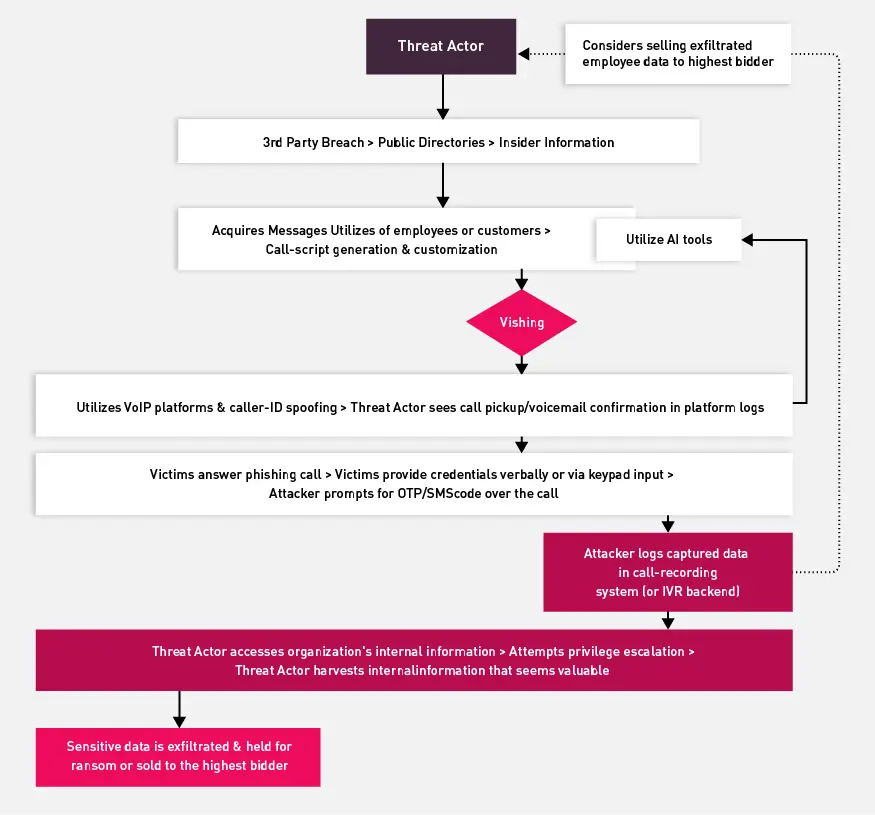
Yet, although smishing and vishing attack flows may not be radically different from phishing attack strategies, what makes these newer attack methods so worrying is their ability to convince targets of threat actors’ legitimacy. Employees and consumers may be hesitant to trust an email message from a source they don’t know. But they might not be as untrustworthy of a text message or voice call they receive on their phone – and unlike with email phishing, they can’t simply look at an email address to determine whether it looks legitimate. Verifying phone numbers is much more challenging.
Furthermore, these newer attack vectors present significant hurdles that weren’t as prevalent with traditional email phishing. Most mobile devices are personal, meaning they’re not monitored by or within the purview of Security Operations Center (SOC) teams. Plus, there aren’t dedicated security tools to automatically catch and block malicious SMS messages or phone calls, in the same way that email security tools can stop phishing emails from ever landing in an inbox. Finally, if an employee does get tricked by smishing or vishing, there’s not much of a chance of the SOC team knowing about it, unless the employee themselves realizes what happened and reports it, making detection and response much more difficult.

The most commonly targeted industries for smishing and vishing attacks appear to be email, social media, finance and retail.
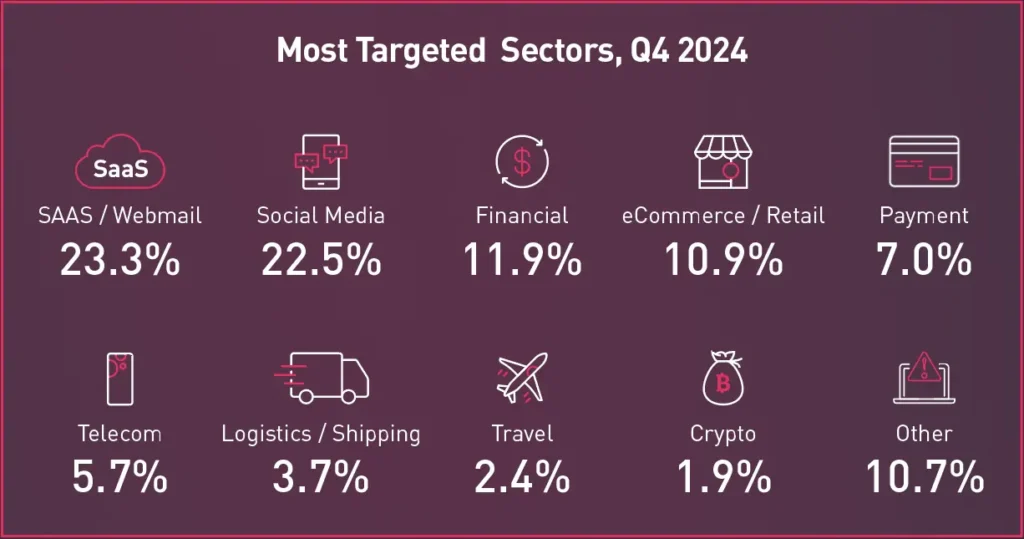
Source: 2024 APWG Phishing Report
That threat actors would focus on finance businesses may not be surprising. Tricking employees or customers into giving away data that unlocks bank accounts is a lucrative activity.
The retail industry, however, might seem like a less obvious target for smishing and vishing. But it makes sense when considered in light of the massive volume of retail sales that take place online, combined with the sensitive data that customers often share with retailers. By posing as representatives of legitimate retailers, attackers try to phish sensitive information from shoppers.
Impersonated social media accounts and SaaS/email accounts controlled by threat actors can boost the likelihood that consumers will fall for the ruse if they share content that appears to legitimize the campaigns.
The vast majority of phishing attacks target the United States, with other wealthy countries also being major targets. (The same trend holds true for countries most often targeted by ransomware attackers, too.)

This trend is not all that surprising, but it’s notable nonetheless because it suggests that although threat actors are now adopting more sophisticated types of phishing tactics by switching to smishing and vishing, the geographies they are focusing on have not changed.
What’s even more concerning is the demonstrated success of these tactics in high-profile incidents. Recently, several major retailers in the UK, fell victim to attacks reportedly orchestrated by the notorious group known as Scattered Spider. These attacks, along with Scattered Spider’s significant breaches of major US Brands last year, notably employed vishing as their initial attack vector.
As native English speakers, Scattered Spider members would call IT help desks, skillfully impersonating legitimate employees, and then social engineer staff into resetting passwords. This granted them initial access to corporate networks and employee accounts. As Lisa Forte explained, “Calling up IT help desks is a tactic that Scattered Spider seems to favour and they use social engineering techniques to manipulate someone into doing something like clicking on a link or resetting someone’s account to a password they can use.”
The group has even utilized SIM swapping capabilities, as seen in an attack on another major UK retailer, to further solidify their impersonation, potentially collaborating with individuals at ISPs or providers to obtain necessary information.
As to why businesses and consumers have experienced a dramatic increase in smishing and vishing attacks in recent years, two key factors seem to be at play.
One is (you guessed it) AI, which helps threat actors create the content for attacks, as well as orchestrate them.
For instance, a new black-hat AI platform, called Xanthorox AI, came to light in early 2025. Unlike earlier hacking tools that leveraged AI, Xanthorox doesn’t jailbreak commercially available large language models (LLMs) to abuse their functionality. It’s a system built entirely from scratch that includes capabilities for planning and carrying out social engineering attacks.
With AI tools like Xanthorox, threat actors can execute smishing and vishing more easily and quickly than ever.
The second factor (particularly in the case of smishing attacks) is the ease with which businesses can now distribute SMS messages and place voice calls on a large scale.
A variety of global bulk messaging service solutions exist, such as Textedly, SendPulse and ClickSend. They serve legitimate business purposes by helping companies to communicate with employees, customers and prospects. But they can also be abused by threat actors to distribute malicious SMS messages or place automated phone calls. Here are some of the most widely used services demonstrating how cheap it is to launch an attack.
What’s more, in cases where legitimate messaging services block communications from threat actors (this is mostly not the case and it’s relatively easy to use these services illegitimately) , the attackers can turn to services sold on the Deep and Dark Webs that serve the same purpose.
Constructing an effective bulk SMS system involves several key technical and strategic considerations. At its core, the system requires integration with an SMS gateway, which serves as a bridge between the internet and mobile network carriers, enabling the dispatch of text messages to various mobile phone numbers. This process demands a reliable and scalable infrastructure to handle high volumes of messages, ensuring timely delivery without bottlenecks. Additionally, database management is crucial for storing and managing contact lists, ensuring compliance with data privacy regulations and facilitating targeted messaging. Advanced systems often include features for message personalization, scheduling, and automation, allowing for more customized and efficient communication strategies
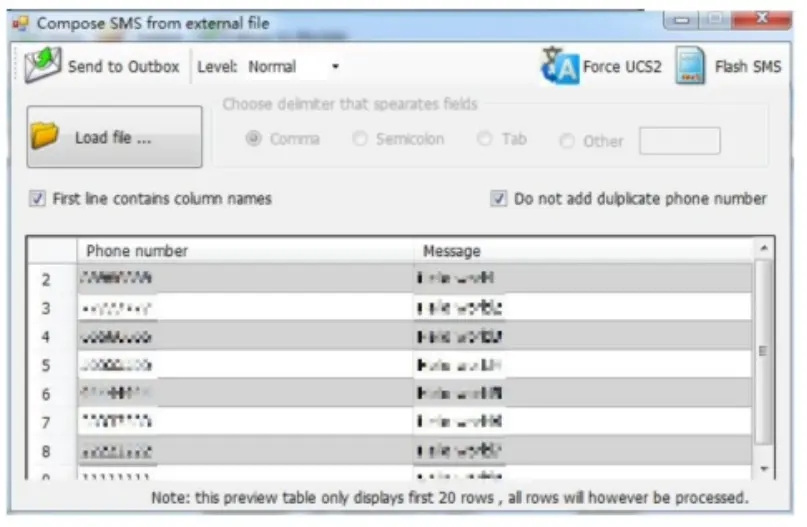
These services make it easy for attackers to send malicious messages to large groups of targets. The messages deliver information – like prompts to report suspicious activity on a bank account – that can result in threat actors gaining access to login credentials or other sensitive information.
To test how easy it is for threat actors to carry out smishing attacks, Cyberint, now a Check Point Company, went undercover for a leading Middle Eastern Bank.
To do this, Cyberint initiated contact with a threat actor and requested operational capabilities in sending SMS messages designed to impersonate the bank. The threat actor responded by providing a convincing dummy message that included a phishing link, demonstrating the attacker’s ability to distribute SMS messages in bulk that contain the malicious link and appear to originate from the bank.
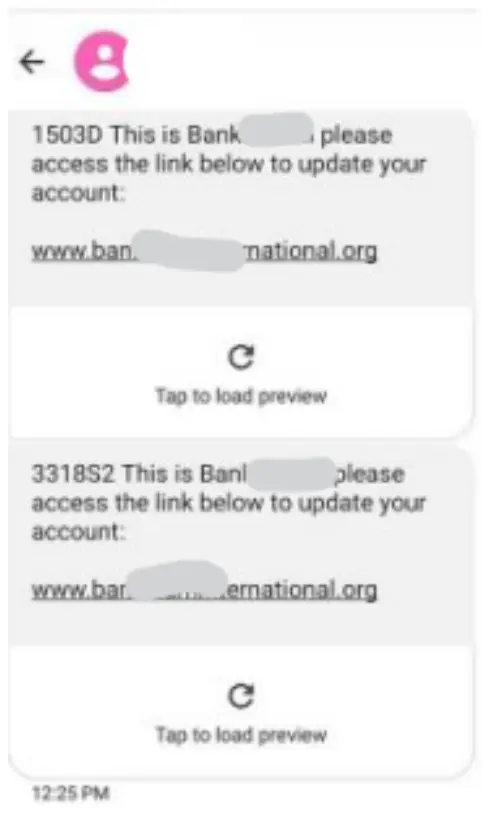
This confirmation underscores the full functionality of the bulk SMS service and its potential for orchestrating massive smishing campaigns.
Now that we’ve detailed the threat posed by vishing and smishing, let’s talk about what organizations can do to protect their brands, employees and customers.
Preventing threat actors from attempting to carry out attacks is not feasible in most cases. AI, combined with bulk messaging services, makes it too easy for threat actors to launch attacks.
Instead, protection strategies should focus on detecting and blocking smishing and vishing as rapidly as possible via practices such as:
Cyberint, now a Check Point Company, can help businesses stay a step ahead of phishing with our open, deep and dark web monitoring and our brand protection services. Contact us to learn more about protecting your brand against smishing and vishing campaigns.
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


