

Businesses today have become painfully aware of the importance of cybersecurity. Penetration testing (“PenTesting” for short), is a valuable tool that can test and identify the potential avenues that attackers could exploit vulnerabilities of your assets. Intelligence led pentesting help with prioritization, speed and effectiveness to prevent financial losses, protect brand reputation, and maintain customer confidence.
Each type of 6 penetration tests is signified by a color (though not as colorful as the rainbow) and comes with its own advantages and disadvantages. Organizations may choose to have only one type of penetration test performed, while others may decide to have several types performed for a more comprehensive assessment of their security posture. The black, grey, and white box testing is used to test the cyber vulnerability of an infrastructure such as apps, cloud, and connected devices. Teams of testers are also defined by colors, and each color team provides a unique function to the testing of the cyber readiness of the organization.
When conducting a black box assessment, penetration testers have limited knowledge of the network. For example, they will know the hostname and IP of a public server, but not have information for the network infrastructure, operating systems, or security protections. In attempting to penetrate the network to discover as many vulnerabilities as they can find, this method imitates a ‘real world’ environment to find vulnerabilities using many of the same tools attackers would use.
In this scenario, the testers have more access and information about the environment such as admin rights and configuration files. This type of testing is less time consuming than black box testing, but doesn’t reveal how attackers can gain unauthorized access externally. It can, however, provide insight into vulnerabilities if an attacker has gained internal access and rights.
Gray box testing falls somewhere between black box and white box testing. The customer shares some limited information, such as a user login or an overview of the network. The scope and what information and access is provided all depends on the testing requirements of the customer. Grey box has the benefits of black box testing but can also do deeper testing where needed with additional information provided.
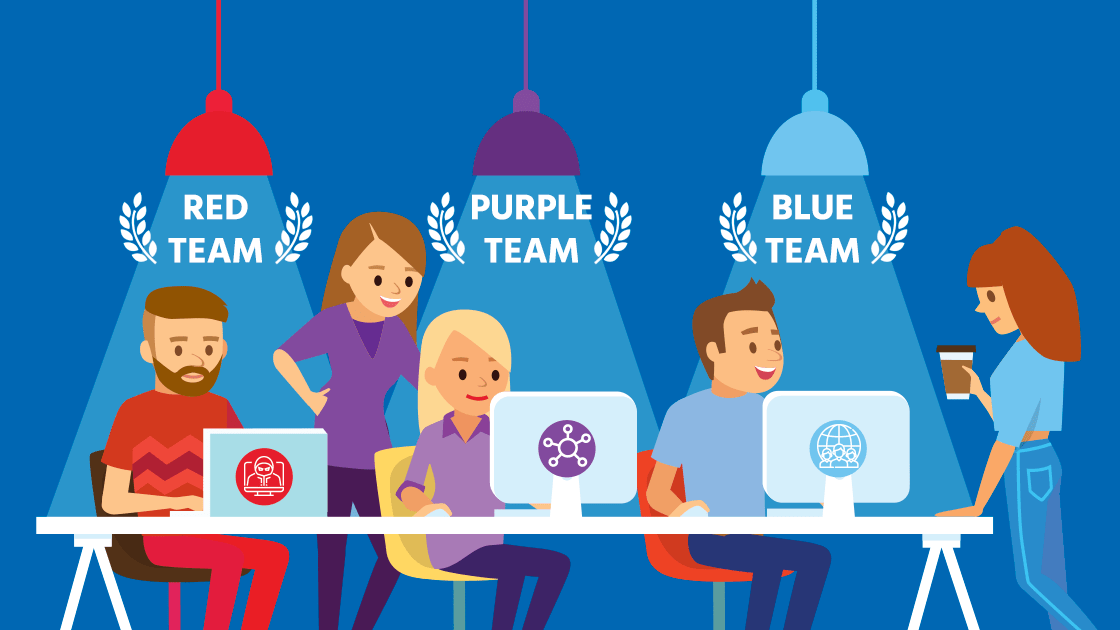
Red team members perform offensive security techniques based on specific objectives such as attempting to penetrate a database and extract sensitive records. The red team simulates an attacker and look for exploitable vulnerabilities.
The blue team is tasked with defending against attacks by the red team. They make use of logs, traffic captures, SIEM and threat intelligence data to detect and defend against red team attacks. The blue team is the internal security team of an organization and exercises with the red team are to improve the internal team’s defense and response to attacks.
The idea of the red team and blue team working together is a purple team. This type of engagement allows the blue team to gauge their detection and incident response capabilities against real-world-like threats.
So we can see here that an organization’s choice of testing really depends on what type of information they want to learn. But in addition to choosing penetration tests, you’ll also need to decide on the scope of the test and what type of systems should be included in the test.
Different areas of the network and systems can be pentested such as web, mobile, and cloud applications, or network and wireless infrastructure.
Two things go without saying:
Caroline Wong, co-author of the Pen Test Metrics Study, comments, “I see a lot of organizations do one application pen test a year because of PCI, or HIPAA, or a customer asking them for one. But more organizations are realizing to ‘do the right thing’ means more regular testing is needed in their secure development practices.”
Contact us for a consultation on what type of penetration testing is right for your enterprise.
©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


