Improving assessment policies and processes on safety and security in organizations is essential in outlining potential breaches and dangers to workers and properties. As an individual with a unique skill set, I have helped to identify security measures and appropriate solutions to mitigate various security risks.
A new alliance has emerged, posing a significant risk to governments, businesses, and individuals worldwide. On February 6th, 2024, a Telegram channel was created, uniting 18 hacking groups from across the globe under the banner of hacktivism. This report by Cyberint delves into the depths of this alliance, analyzing its origins, motives, activities, and potential impact. It then offers recommendations for organizations and individuals to strengthen their cybersecurity posture.

This alliance signifies a worrying trend in hacktivism, highlighting the growing sophistication and collaborative nature of cybercriminal activities. Their combined skills and resources pose a significant threat to critical infrastructure, sensitive data, and online safety. Understanding their motives, targets, and methods is crucial for developing effective defenses and mitigating potential damage.
As of February 16, 2024, Cyberint had observed the following Threat Groups listed below as official member of the Hacking Alliance:

While most of the Alliance Members are in Morocco, Cyberint also observed that the group consists of representatives across different regions globally, with the infamous Anonymous and LulzSec having different part of their teams as members of the forged alliance.
LulzSec started with hacktivism in June 2011 with an initial member base of 6, primarily motivated by “lulz” (meaning laughs or amusement) and causing chaos online. They are notoriously known to have targeted high-profile organizations like Sony, PBS, and the CIA, mainly through website defacement and data leaks. They also engaged in pranks and social engineering tactics.
Although the original Founding Members of LulzSec were arrested, their legacy lives on as Threat Actors and Groups have carried the banner to continue the hacktivism work for the founding members.
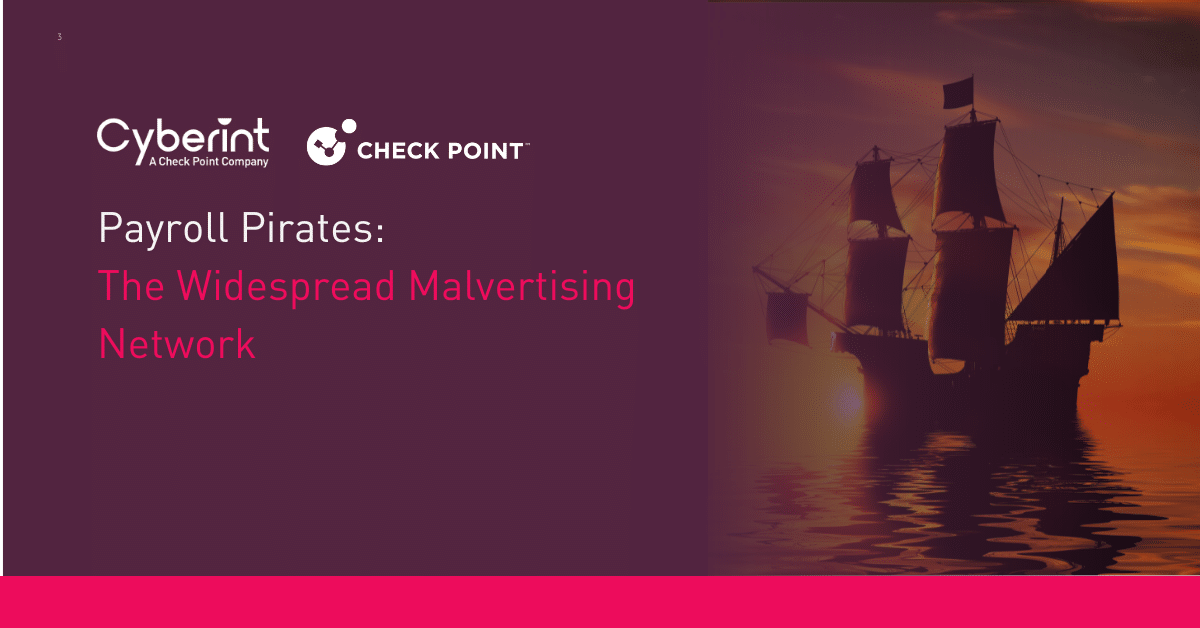
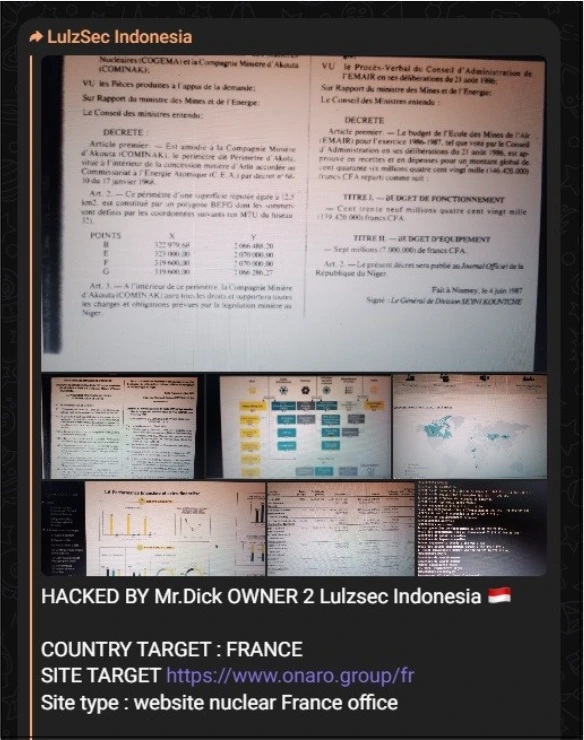
Inside the alliance’s channel, it’s evident that one of the most active members is LulzSec, which has targeted French companies and institutions as of writing as part of the “#OpFrance”.
While Anonymous, started in 2003, is decentralized and leaderless, anyone can claim to be “Anonymous.” Anonymous generally focuses on social and political activism, including freedom of speech, government transparency, and cyber justice. They are notoriously known for website defacement, distributed denial-of-service (DDoS) attacks, online protests, and information leaks.
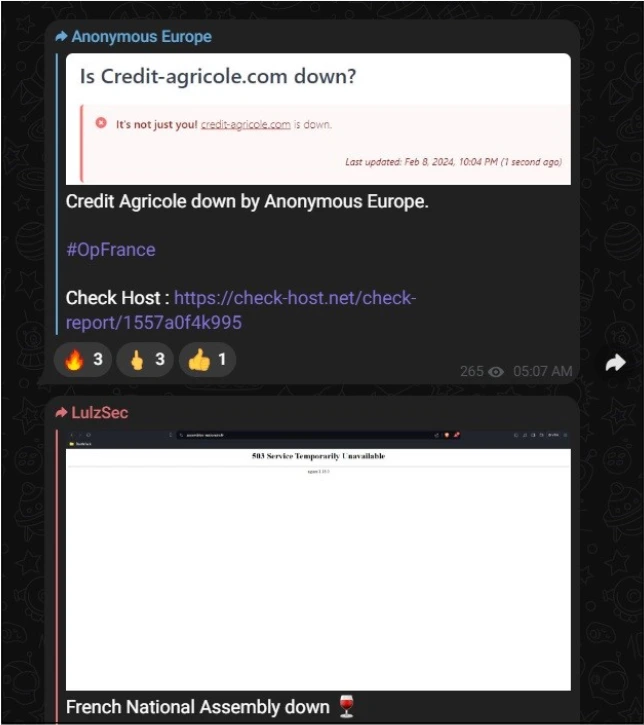
Anonymous remains active and evolving, with various operations targeting governments, corporations, and organizations perceived as corrupt or unjust. As another member of the Alliance Group, Anonymous has also targeted France, in collaboration with “LulzSec” with the current campaign labeled “#OpFrance.”
Another notable threat group listed as “LAPSUS$ GROUP”, started on late 2021, is a known international group, with members arrested in Brazil and UK, some believed to be teenagers. Primarily known for breaching high-profile companies such as Microsoft, Samsung, Nvidia, Uber, and Rockstar Games, they are motivated by extortion and notoriety, with some elements of hacktivism.
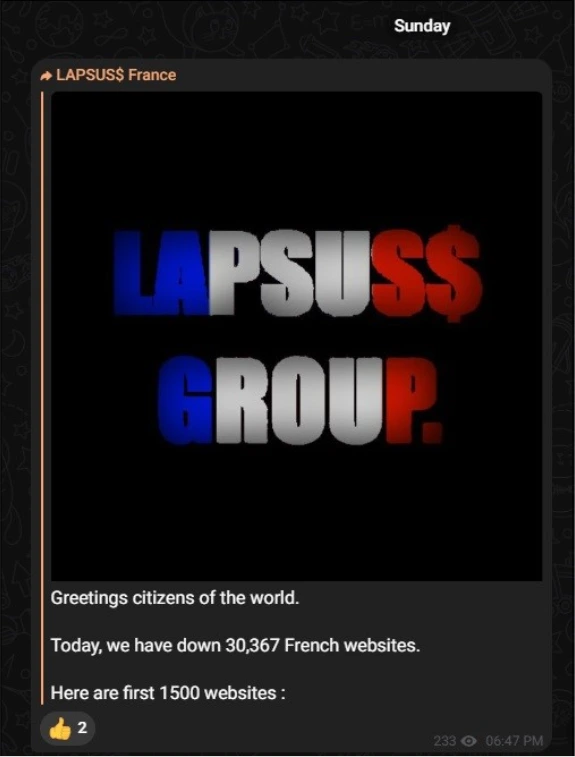
In the Alliance Group, LAPSUS$ has the most numbers of alleged websites compromised as part of their current “#OpFrance” campaign. With 30,367 French Websites targeted, they sit at the top with the raw numbers of compromised websites.
There are a few relatively new names that have made it to the Alliance Group. The threat group Robin Cyber Hood is a newcomer when it comes to hacktivism but also follows the same framework with anonymous, decentralized, and leaderless. The group had members across the globe.
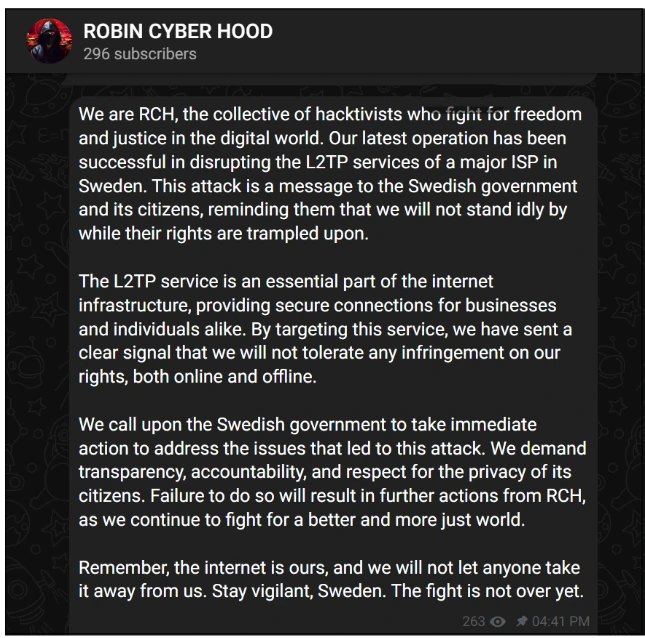
The Threat Group initially began by targeting Sweden and compromised a major ISP in the country to notify the Swedish Government about the current situation on the country for immigrants being a priority over the locals. The campaign explicitly said that the Threat Group will continue to fight for a better and more just world.
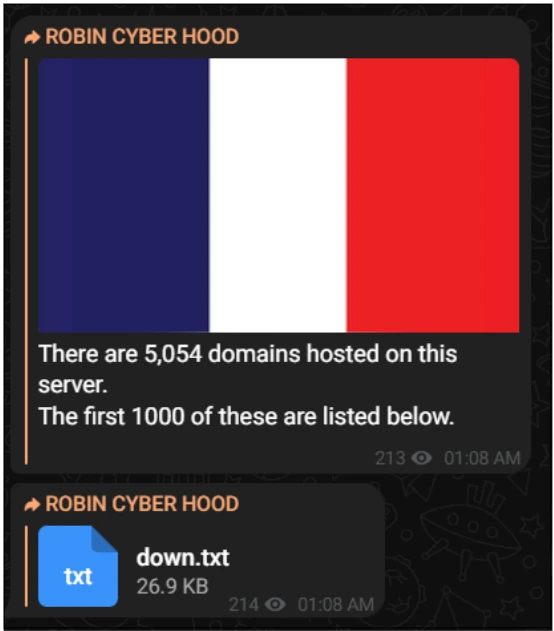
The new group, surprisingly, compromised 5,054 French domains as part of “#OpFrance” as observed on their listing on the alliance group channel.
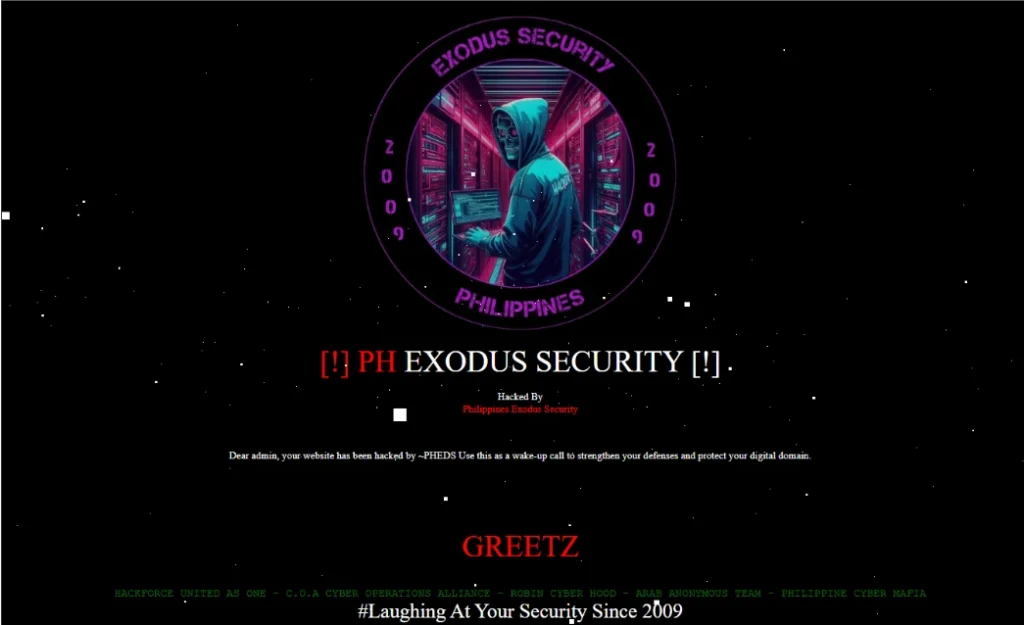
Philippines Exodus Security, a new threat group hailing from the Philippines were observed to have been included on the alliance channel. The group also primarily motivated by hacktivism, focuses on website defacement on Philippine Government Websites.
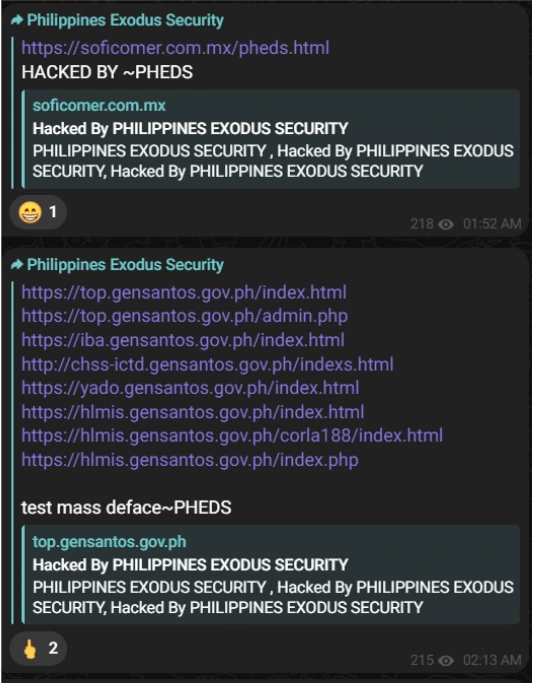
The Threat Group, being relatively new, has participated in website defacement activities primarily to gain notoriety. Part of their campaign is to deface any vulnerable website to promote their “agenda” on strengthening weak security.
The recent alliance between established hacktivist groups like Anonymous and LulzSec with newer players like Robin Cyber Hood and Philippine Exodus paints a troubling picture. This collaboration amplifies their collective impact, leveraging diverse skillsets and resources to target larger entities like the French government with campaigns like “#OpFrance”. This fusion of expertise combines established groups’ strong technical capabilities and experience in large-scale operations with newer groups’ potential regional insights.
However, concerns arise around shifting motivations, with some traditional groups advocating for social change while newer members possibly injecting financial gain or notoriety motives into the mix. Further, the alliance demonstrates a disregard for geographical boundaries, targeting countries across continents and highlighting the interconnectedness of the digital world.
These collaborative efforts could lead to a dangerous escalation. More complex and damaging attacks might target critical infrastructure, sensitive data, and government systems, causing significant disruption. Hacktivist actions often draw responses from governments, potentially leading to legal repercussions or even cyber warfare scenarios, escalating tensions further. The repeated targeting of institutions and online platforms could also erode public trust, impacting social stability and economic activity.
Addressing this complex issue requires a multifaceted approach, combining technical defenses with international cooperation, open dialogue, and a focus on promoting responsible online behavior.
Cyberint, the Impactful Intelligence company, reduces risk by helping organizations detect and mitigate external cyber threats before they have an adverse impact. The Cyberint Argos platform’s patented technology provides superior visibility through continuous discovery of the evolving attack surface, combined with the automated collection and analysis of vast quantities of intelligence from across the open, deep and dark web.
A team of global military-grade cybersecurity experts work alongside customers to rapidly detect, investigate, and disrupt relevant threats – before they have the chance to develop into major incidents. Global customers, including Fortune 500 leaders across all major market verticals, rely on Cyberint to protect themselves from an array of external risks, including vulnerabilities, misconfigurations, phishing, impersonation attacks, malware infections, exposed credentials, data leaks, fraud, and 3rd party risks. For more information get a demo.

©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start