


A passionate and enthusiastic research analyst with exemplary results dealing in intelligence research, nominated for several honors during military service. Recognized consistently for performance excellence and contributions to success in operational missions. Was active in Intelligence Special Operations, has sound knowledge of research methodologies and how to efficiently find and break down new pieces of information while presenting them to senior ranking officials.
According to the latest news, the cloud-based data storage and analytics giant Snowflake has supposedly suffered a breach according to researchers that interacted with a certain Threat Actor known as ‘whitewarlock’ on the deep web hacking forum ‘exploit[.]in’. The claims are currently not corroborated by the Snowflake team.
Cyberint found the original compromised machine potentially exploited by ‘whitewarlock’. Over 500 demo environment instances were found included in the malware log. The compromised machine is linked to a current active employee of Snowflake, a sales engineer.
It is assumed that the Threat Actor could gain access to prospect and sales-related environments and newly onboarded production accounts. However, such access isn’t expected to grant the type of data that the Threat Actor claims to hold. Furthermore, Snowflake stated, alongside cybersecurity companies that it employed to investigate the incident, did not find evidence showing the attack was “caused by compromised credentials of current or former Snowflake personnel.”
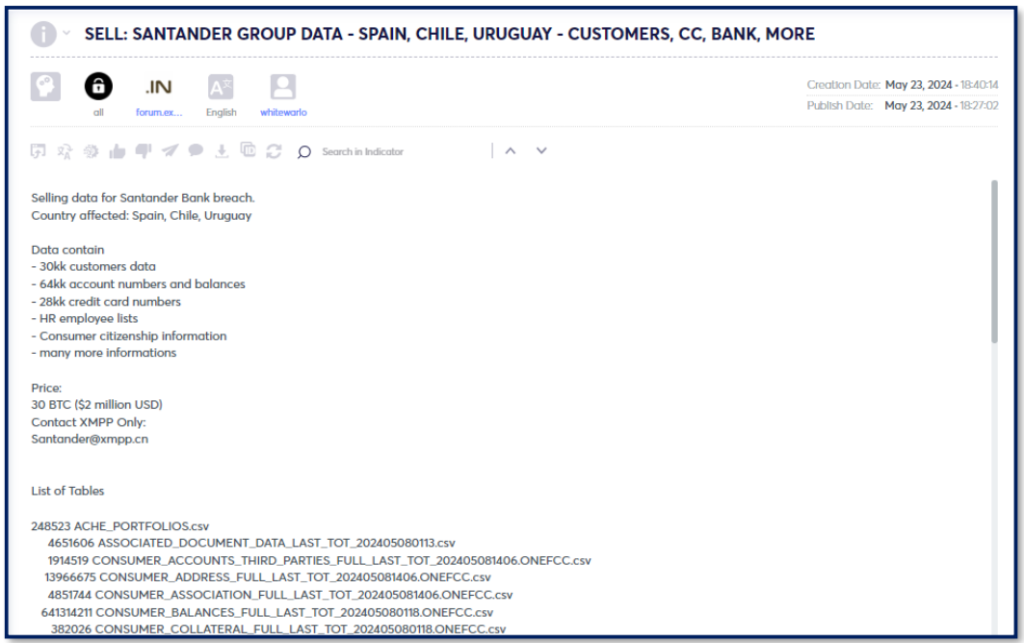
Snowflake is a cloud-based data storage and analytics company that services over 9,400 customers. Researchers investigating an independent security breach of ‘Santander Group’ have reportedly found evidence suggesting that the aforementioned breach was instigated by a compromised Snowflake account. The Threat Actor ‘whitewarlock’ suggested that as many as 400 clients were involved in the breach and attempted to extort Snowflake to pay 20 million dollars to purchase the exfiltrated data back but has received no reply.
The Threat Actor Whitewarlock posted on the deep web hacker forum ‘exploit[.]in’ breached data related to ‘Santander group’ on May 23rd . The forum account was created on the same day as the post, no other activity was found related to the account. As of May 31st, no other data is being sold by the Threat Actor, at least on the forum. Cyberint also searched for the moniker and its twists across other sources in an attempt to link to any other deep web or darknet forums, however, no such corroborating data was found.
As a result, the Threat Actor’s reputation is currently unknown, however, according to the data that was shared between the Threat Actor and the researchers, some of the information is corroborated and seems valid.
The alias ‘whitewarlock’ could potentially indicate a selective altruistic intent. This is further supported by conversations with the researchers, where it is implied that the Threat Actor has an interest in “my goal is for them to buy their data back rather than let it end up in the wrong hands”.
However, it seems highly improbable that a hacker would relinquish a data cache that is extorted at 20 million dollars. It is plausible that the Threat Actor cooperated with the researchers in an attempt to attract more traction on the breach.
The intention behind this could be to ensure that the researcher’s blog post garners significant attention, thereby escalating the pressure on Snowflake to respond or for its clients to contact the Threat Actor to purchase their own data.
Based on the conversation between the researchers and the Threat Actor, the Threat Actor claimed that the Snowflake data was exfiltrated because of one compromised account ‘adelou’ that was infected with Lumma Stealerware. Cyberint successfully captured said malware log on September 19th, 2023.
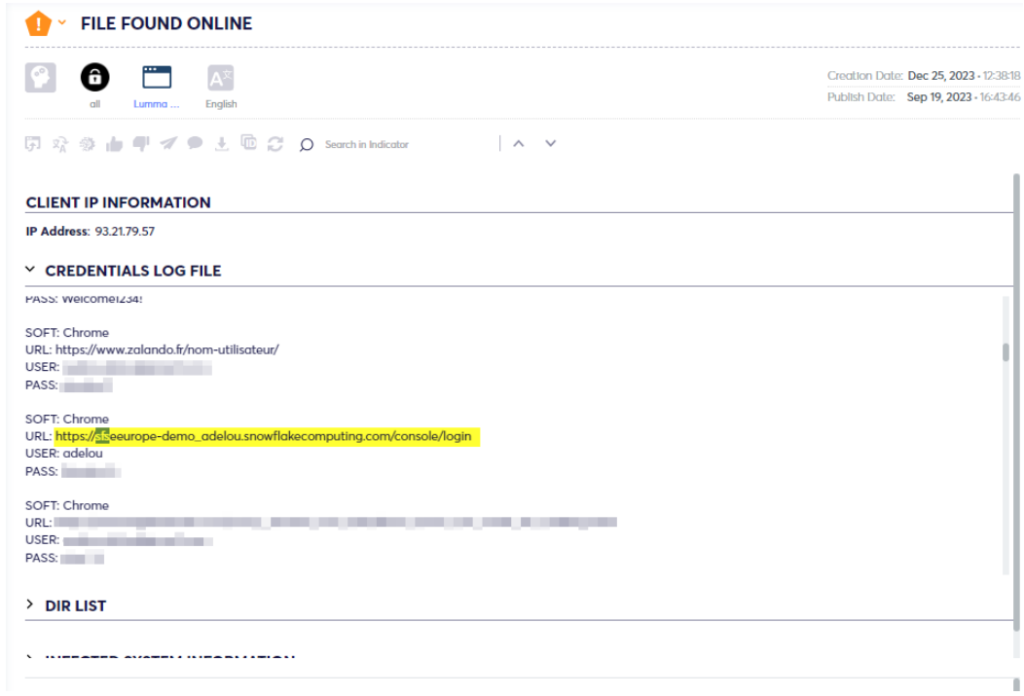
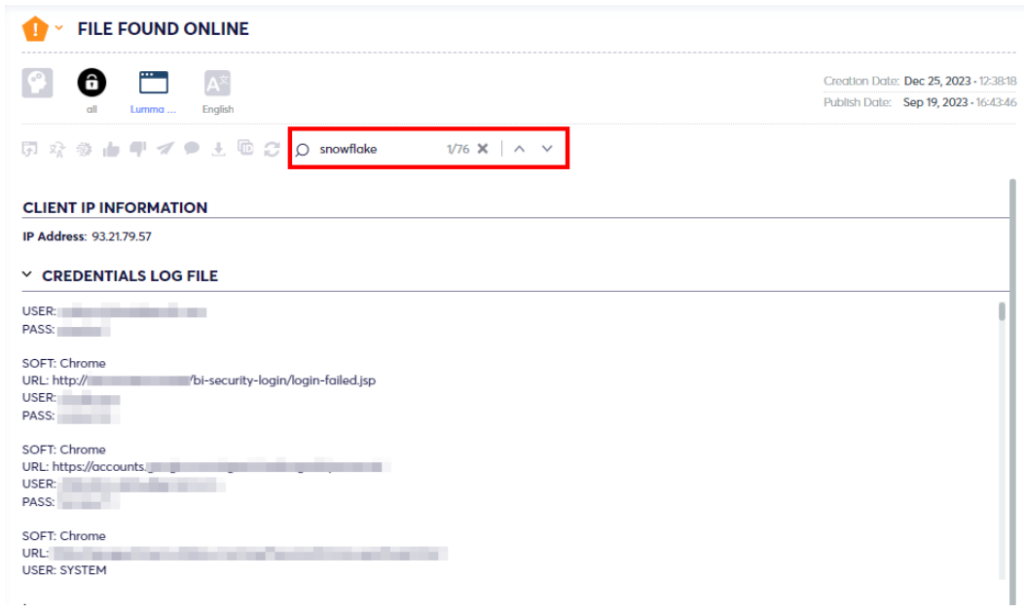
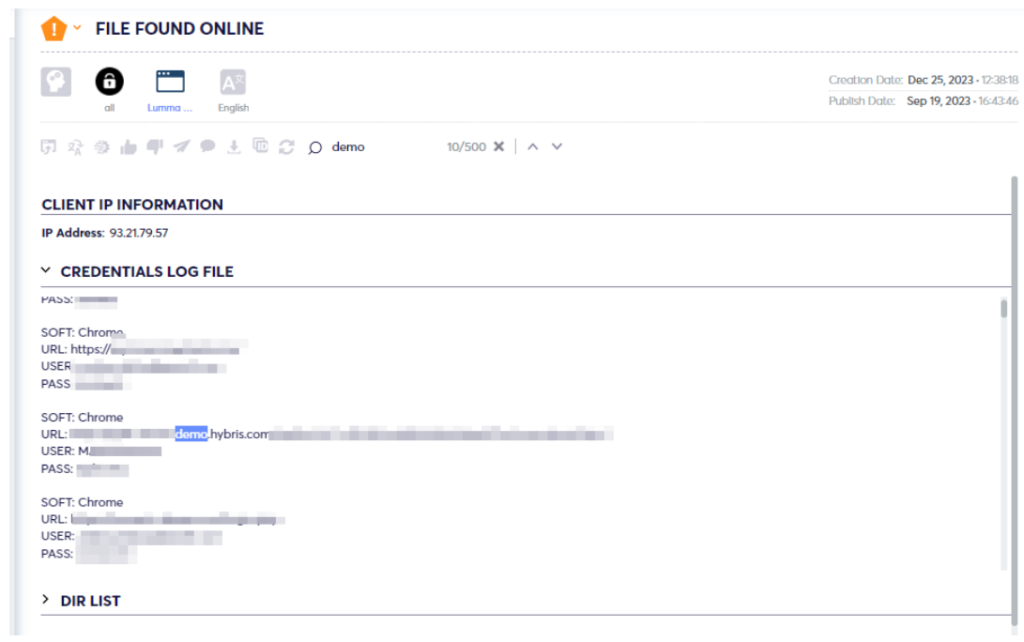
While analyzing the malware log, we were able to verify that the account is linked to a current active employee of Snowflake, a sales engineer.
Given the Threat Actor’s access to a Sales engineering account, it is more likely that he gained access to prospect, and sales-related environments, or newer production accounts. Over 500 demo environment instances were found included in the malware log.
However, Cyberint did not find a specific sensitive interface that would be expected to lead to sensitive data such as the data trove that the Threat Actor claimed to own. It is more likely that if unauthorized access was
involved a different vector is involved.
©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


