Intelligence sur la chaîne d’approvisionnement
Les responsables de la sécurité peuvent gérer un programme cyber de classe mondiale et être malgré tout victimes d’une faille causée par un tiers non sécurisé ; 30 % des violations impliquent la chaîne d’approvisionnement. Atténuer ces risques liés à la chaîne d’approvisionnement numérique est essentiel, car ils compromettent les autres investissements en matière de sécurité.
Découvrez l'intelligence de la chaîne logistique en action
Sécuriser votre chaîne logistique numérique :
Une nouvelle approche pour gérer les risques liés aux tiers
Watch the WebinarLes composantes de la veille stratégique sur les menaces pesant sur la chaîne d'approvisionnement
Comment cela fonctionne-t-il ?
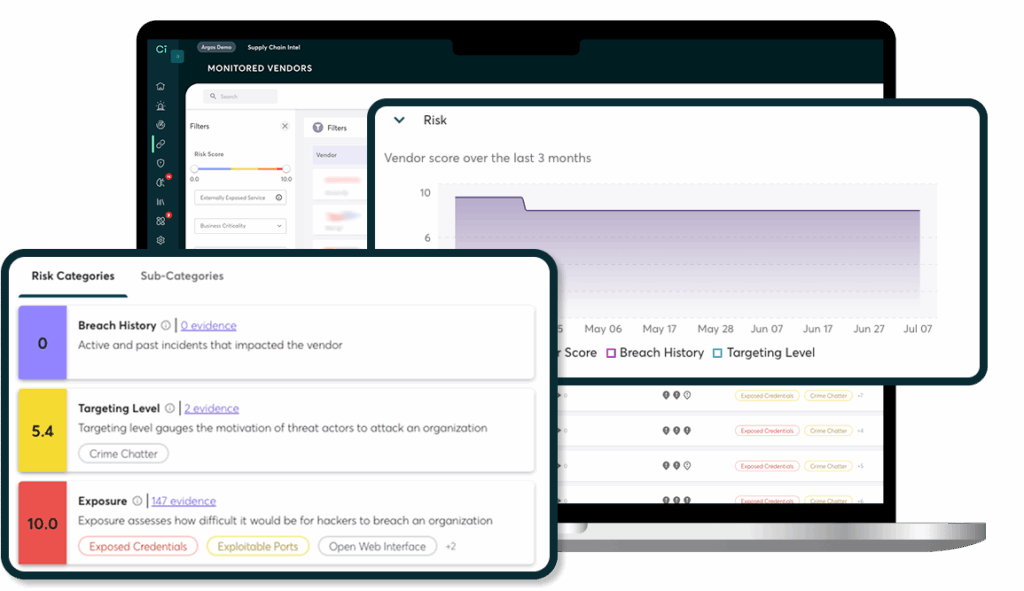
Découvrir les actifs et les points d’accès connus et inconnus
Rapport sur les risques liés aux fournisseurs à destination de la direction
Comprenez les risques liés aux tiers et à la chaîne d’approvisionnement afin de pouvoir rendre compte avec précision aux parties prenantes et prendre des décisions éclairées en matière de gestion des risques.
Intégrez les alertes dans votre SOC
Le module de renseignement sur les risques liés à la chaîne d’approvisionnement permet d’intégrer des alertes sur ces risques dans les workflows existants, via des intégrations avec des plateformes SIEM, XDR et SOAR.
Contrôle granulaire
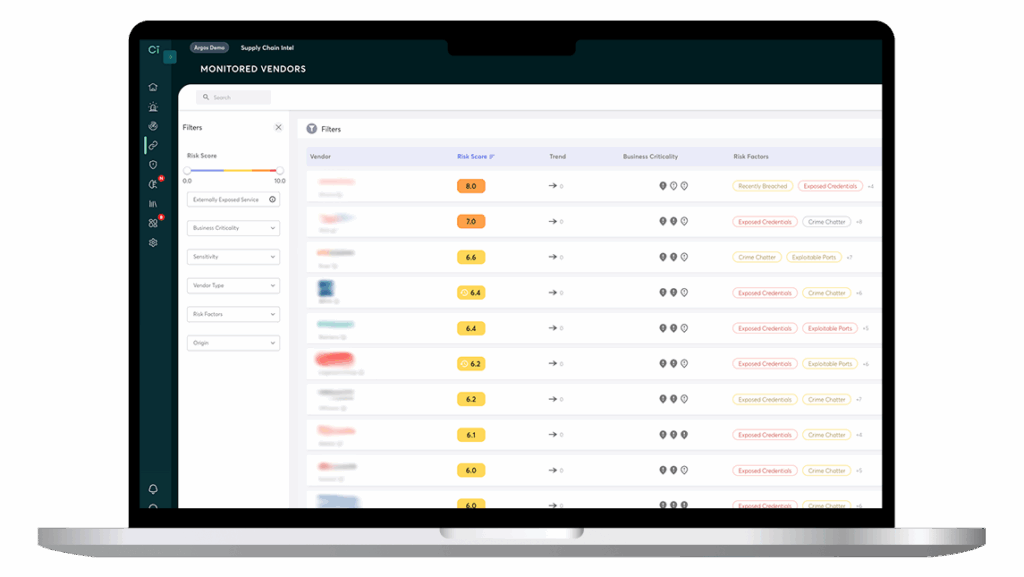
Filtrez les fournisseurs selon leur criticité métier, la sensibilité des données, le score de risque, le type de risque et leur origine (détectés automatiquement ou ajoutés manuellement), afin d’obtenir un contrôle granulaire sur l’évaluation et la gestion des risques liés à votre chaîne d’approvisionnement.
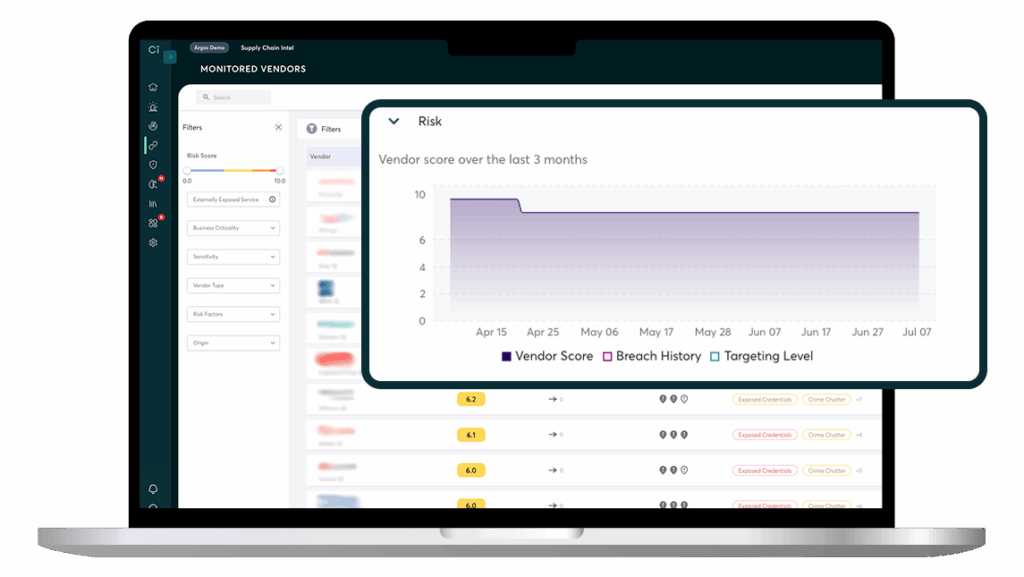
Suivez les changements au fil du temps
Surveillez les fluctuations des risques liés à vos fournisseurs à l’aide de graphiques intuitifs et de fonctionnalités d’évolution en pourcentage. Observez l’évolution de leur ciblage et de leur exposition, identifiez les risques maximaux et recevez des alertes instantanées en cas de violation.
Ressources
Découvrez-le par vous-même.
Commencez votre transformation en matière de gestion des risques externes.
Start With a DemoFAQs
Qu’est-ce que l’intelligence de la chaîne logistique ?
Il s’agit d’informations exploitables sur les risques, les vulnérabilités et les menaces provenant de vos fournisseurs, vendeurs ou partenaires. L’objectif est d’identifier les points faibles potentiels avant qu’ils n’aient un impact sur votre organisation.
Si un fournisseur tiers subit une pertes de données, les renseignements sur la chaîne d’approvisionnement vous aident à évaluer l’exposition et à réagir de manière proactive. Ils doivent être dynamiques et tenir compte du niveau de ciblage sur le deep web et le dark web, de la cyberhygiène et de la posture de sécurité.
Comment Cyberint collecte-t-il des informations sur la chaîne d’approvisionnement ?
Nous collectons des informations sur la chaîne d’approvisionnement en :
- Surveillant les sources publiques, le dark web et les forums clandestins à la recherche de menaces liées aux fournisseurs.
- Suivant les violations de données ou les fuites d’identifiants par des tiers.
- Analysant les actifs qu’ils possèdent et les risques qui y sont associés.
- Utilisant l’IA Threat Cloud de Check Point, qui traite quotidiennement d’énormes quantités de données télémétriques provenant de 150 000 réseaux et de millions d’appareils.
Et plus encore.
Cela peut-il empêcher les attaques, ou cela me permet-il simplement d’être informé après coup ?
La valeur ajoutée réside dans la détection précoce des menaces, des pratiques de sécurité insuffisantes et des fuites d’identifiants, ce qui laisse aux équipes le temps d’agir. Mais oui, dès qu’un incident se produit, nous vous alertons également par le biais d’une alerte hautement prioritaire.
Dans quelle mesure ces informations sont-elles exploitables pour les décisions d’achat ?
Cyberint traduit les renseignements en scores de risque et en recommandations, et pas seulement en alertes. Ces informations peuvent être utilisées dans le cadre d’une décision d’achat. Nos analystes sont également à votre disposition pour mener une enquête approfondie avant qu’une décision ne soit prise.
Comment intégrer les renseignements sur la chaîne d’approvisionnement aux programmes existants en matière de cyberrisques ?
Nos renseignements offrent des intégrations dans les SIEM/SOAR/workflows de gestion des risques fournisseurs et bien plus encore pour une gestion cohérente des risques.