Attackware
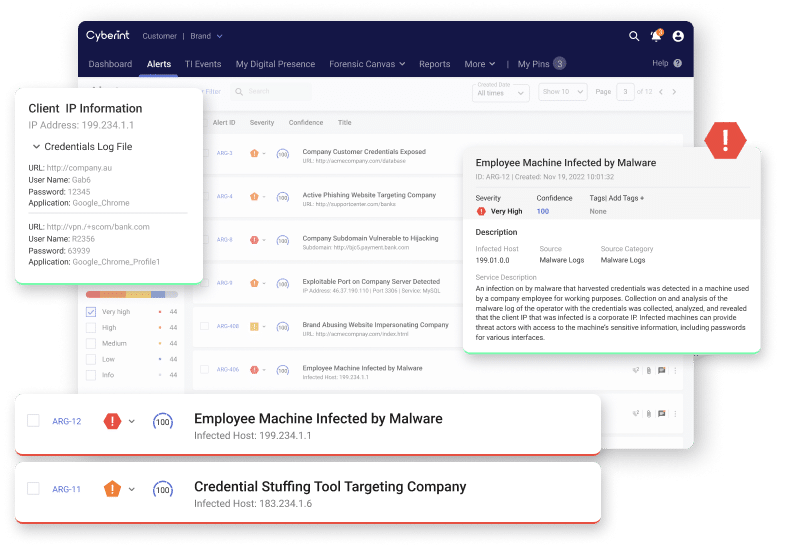
Intercept and Take Down Malware
Argos continuously monitors forums, marketplaces and code repositories to detect and intercept various malware shared and sold by cyber criminals, help customers defend against these tools, and take them down in time.
Leaked credentials in Argos data lake
New databases added annually
Fresh credentials harvested/month
New malware logs detected/month
Ensure ongoing and continuous visibility of threat actor’s tools
Malicious Files
Reconnaissance
Business Logic Bypass

Attackware