Threat Hunting License
Research, Investigate, and Proactively Hunt For Cyber Threats
Elevate your cybersecurity program with the Cyberint Threat Hunting Tool. Understand your organization’s specific threat landscape, drill down on the threats you’re most likely to face, investigate targeted attacks, and hunt for threats that have currently managed to evade detection.
Gain Access To The Tools & Data You Need
Many threat intelligence and threat hunting programs lack the tools and data needed to deliver maximum results and impact. The Cyberint Threat Hunting Tool provides a suite of product modules to support the research, investigation, and hunting of cyber threats. These capabilities help you to proactively defend against probable attacks, investigate incidents after an attack is detected, and uncover hidden threats that bypassed existing controls.
Why Customers Choose Argos
A Library Of Strategic Threat Intelligence

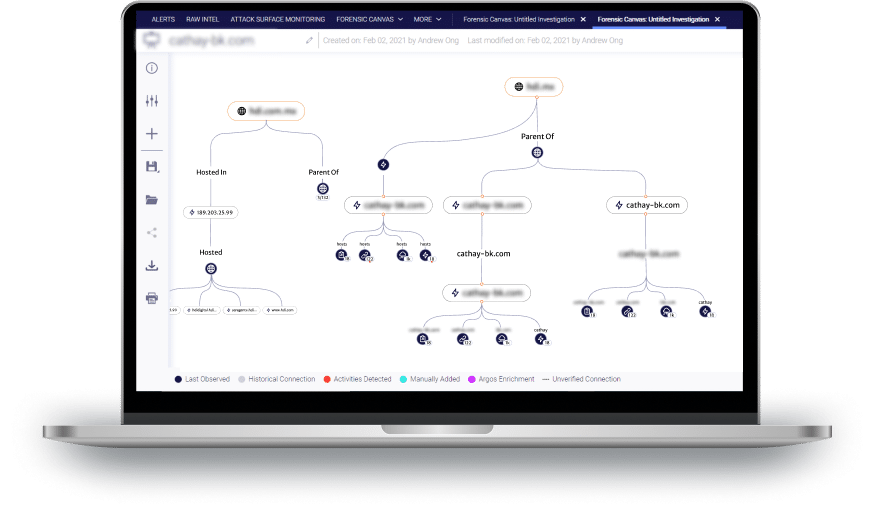
Comprehensive Investigations Tools

A Deep & Dark Web Search Engine

Quickly Validate Alerts & Threats
Testimonials
Dive into our Resources
Focused intelligence.
Groundbreaking efficiency.
Real-time threat intelligence, tailored to your attack surface