Takedowns & Remediation Service
Managed takedown services to eliminate cyber risks faster
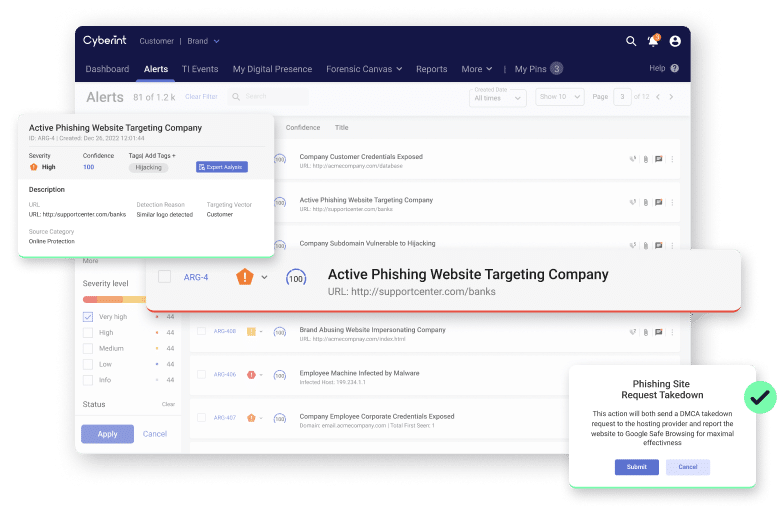
Leverage Cyberint’s dedicated takedown team to eliminate malicious phishing sites, fraudulent social media profiles, rogue applications, and more.
Rapidly Remove Threats with Takedown and Remediation
The process of finding and taking down malicious content is time-consuming and challenging. It can be especially difficult when the content is hosted by foreign entities. Without a prior relationship in place or the ability to communicate effectively, having malicious content removed is difficult. Cyberint has a dedicated, in-house takedown with years of experience to help accelerate your takedowns across phishing websites, fake social media profiles, fraudulent applications, and other malicious digital assets.
Terex corporation gains visibility into external threats and eliminates phishing attacks:
Terex is a global manufacturer of materials processing machinery and aerial work platforms. After several unsuccessful phishing campaigns targeted the company, they approached Cyberint for help. Through the partnership they uncovered and mitigated many phishing and brand impersonation risks.
Detect & Mitigate Phishing Attacks Better
Detect & Mitigate Phishing Attacks Better

FAQ
What does the takedown process look like?

On average how long should a takedown take?

Are there automated takedowns?

Do you offer social media takedowns?

How often do you scan for phishing and brand impersonation?

Testimonials
Dive into our Resources
See all resources

Terex corporation gains visibility into external threats and eliminates phishing attacks
Focused intelligence.
Groundbreaking efficiency.
Real-time threat intelligence, tailored to your attack surface