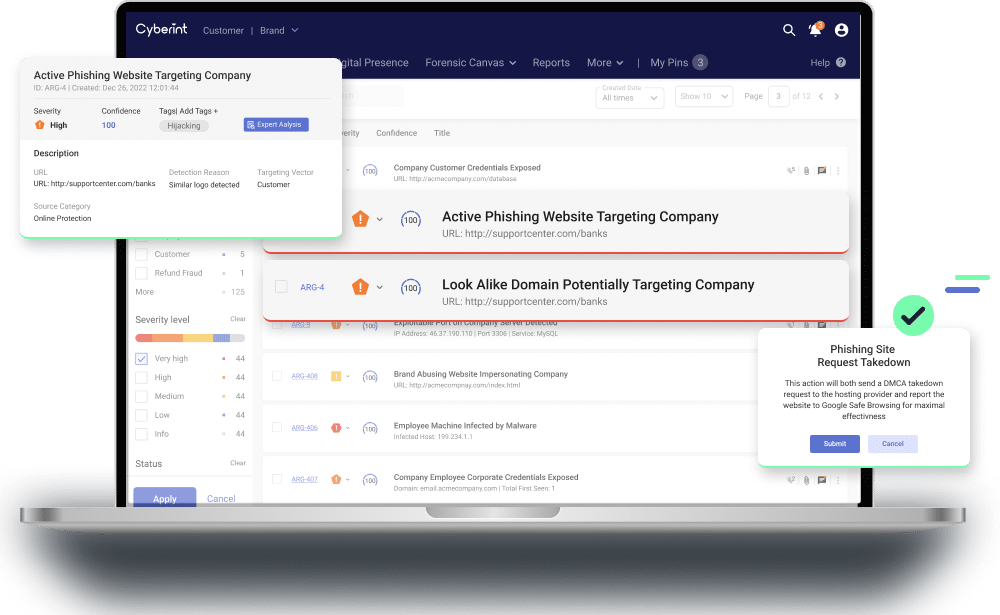
Phishing Detection
Intercept emerging phishing threats before an attack is executed.
Drastically reduce response time and number of attacks. Detect malicious website clones before they go live. Request take down of phishing pages in a click of a button.
Act fast and avoid costly incidents and brand reputation damages
Each year phishing attacks are becoming increasingly sophisticated. Today, threat actors spend months planning their phishing attacks and launch phishing scams directly targeting a specific organization, including both its customers and employees.
The potential damage of a successful phishing attack to your organization is widespread, impacting your security operations and brand reputation, in addition to your data privacy and compliance.
Why Customers Choose Argos
The ultimate phishing protection handbook
DOWNLOAD NOW!

Phishing Beacon: Forget everything you know about phishing prevention
Once implemented and configured, the beacon alerts Cyberint should the page be copied and hosted on any other domain.

End-to-end phishing coverage
Dive into our Resources
Focused intelligence.
Groundbreaking efficiency.
Real-time threat intelligence, tailored to your attack surface