Supply Chain Intelligence
Security leaders can run a world-class cyber program and still be breached by an insecure third-party; 30% of breaches involve the supply chain. Mitigating these digital supply chain risks is essential, as they undermine other security investments.
Experience supply chain intelligence in action
The Components of Supply Chain Threat Intelligence
How it works
Uncover known and unknown assets and access points
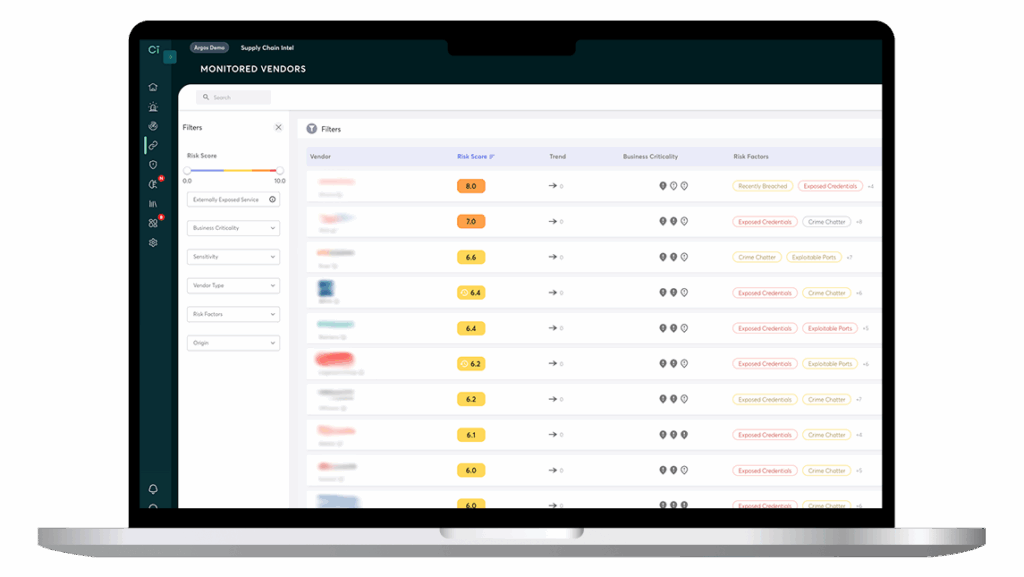
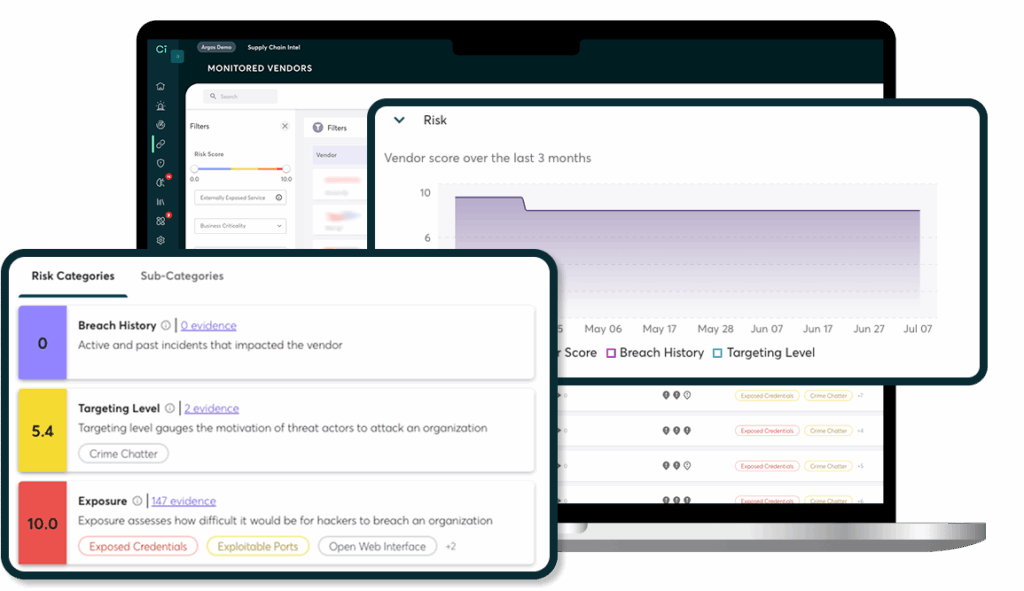
Report Vendor Risk to Management
Understand third party & supply chain risks so you can accurately report to stakeholders and make informed risk management decisions.
Pull Alerts Into Your SOC
The supply chain risk intelligence module allows you to bring alerts regarding supply chain risks into existing workflows via integrations with SIEM, XDR, and SOAR platforms.
Granular Control
Filter vendors by business criticality, sensitivity, risk score, risk type, and origin (automatically found vs. manually added) to enable you to gain granular control over your supply chain risk assessment and response.
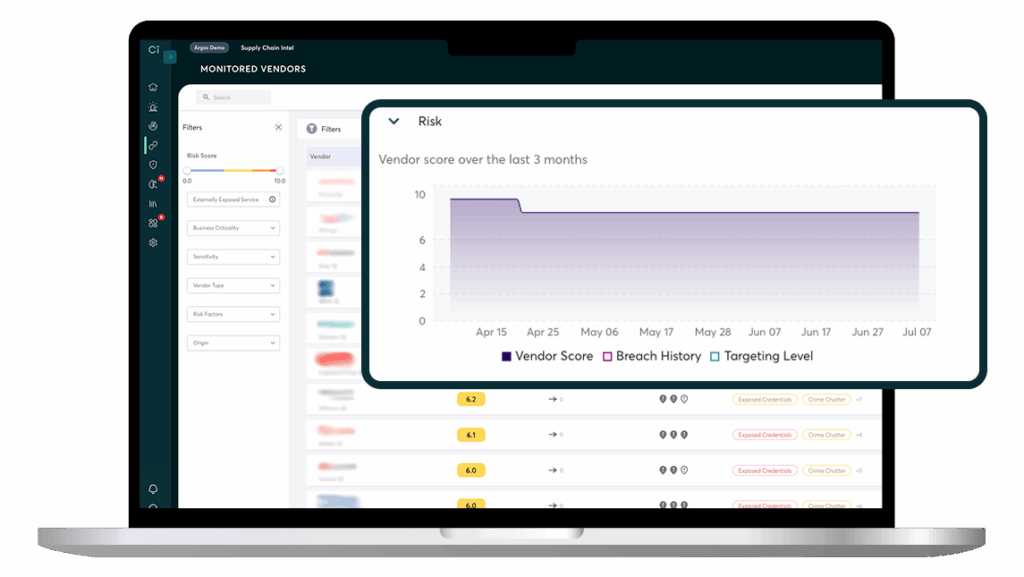
Track Changes Over Time
Monitor your vendor’s risk fluctuations using intuitive graphs and percentage change features. See how their targeting and exposure evolve, identify peak risks, and get alerted instantly if they experience a breach.
Resources
FAQs
What is supply chain intelligence?
It’s actionable insights into risks, vulnerabilities, and threats originating from your suppliers, vendors, or partners. The goal is to identify potential weak points before they impact your organization.
If a third-party vendor suffers a data breach, supply chain intelligence helps you assess exposure and respond proactively. It should be dynamic and take into account targeting level on the deep & dark web, cyber hygiene and security posture.
How does Cyberint collect supply chain intelligence?
We collect supply chain intelligence by:
-
Monitoring public sources, dark web, and underground forums for vendor-related threats.
-
Tracking third-party breaches or leaked credentials.
-
Scanning assets they own and any risks associated with them
- Utilizing Check Point’s Threat Cloud AI, that processes massive telemetry from 150,000 networks and millions of devices daily.
and more.
Can this prevent attacks, or does it just inform me after something happens?
The value comes from early detection of threats, weak security practices, and leaked credentials, giving teams time to act. But yes, the moment something happens we also alert you with a high priority alert.
How actionable is this intelligence for procurement decisions?
Cyberint translates intelligence into risk scores and recommendations, not just alerts. This can be used in a procurement decision. Our analysts are also at hand for a deep dive investigation before a procurement decision is made.
How do we integrate supply chain intelligence with existing cyber risk programs?
Our intelligence offers integrations into SIEMs/SOARs/Vendor risk management workflows and more for cohesive risk management.