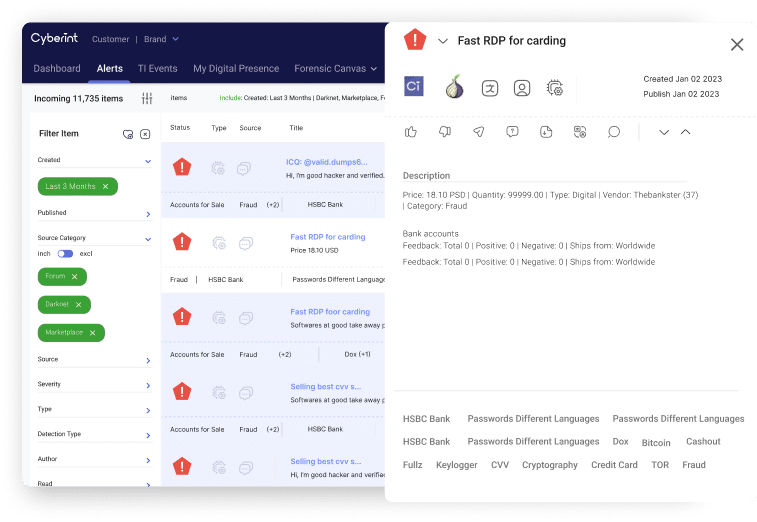
Darkweb Threat Intelligence
Get real-time, Darkweb threat intelligence for maximum business impact
Gain insights of threats from the ever-growing list of sources, such as the open, deep & dark web, social media, and more – for faster and more informed decision-making.
Tailored, focused data – minus the noise
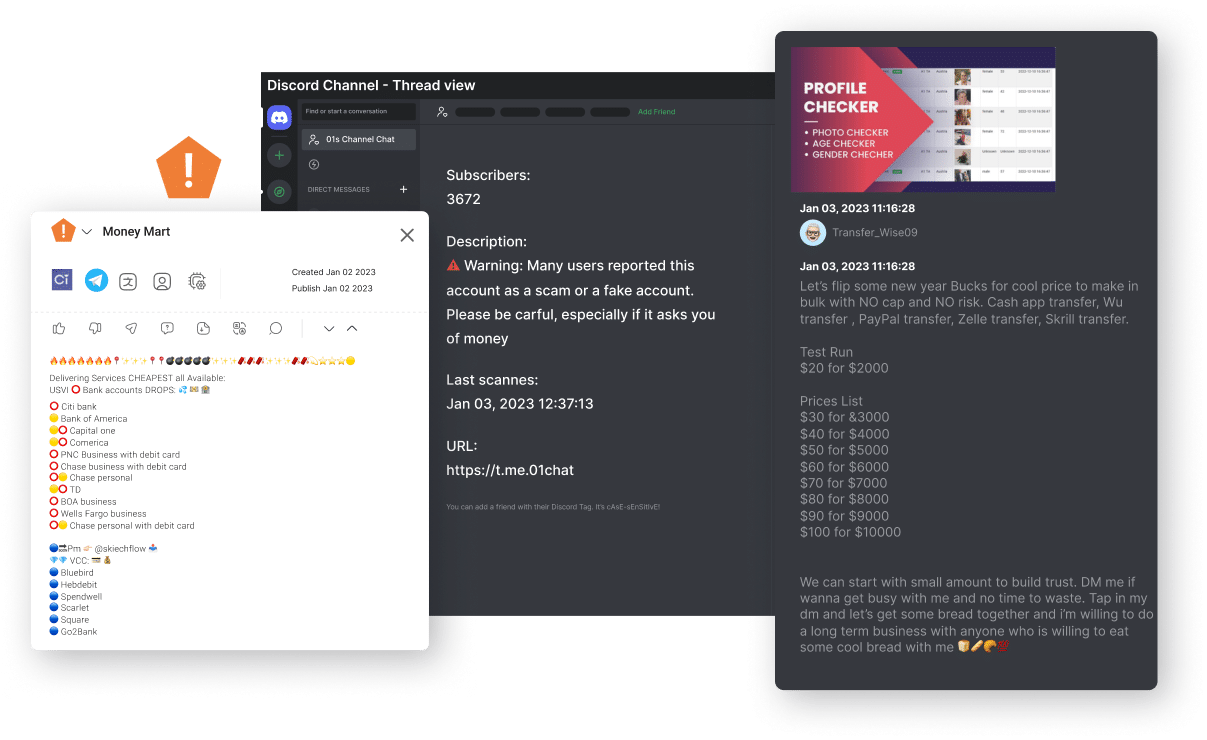
Managing digital risk starts with a deep understanding of the relevant threat landscape. But the increasing complexity and the fast pace of change makes it difficult to prioritize. Argos meets this challenge with real-time monitoring that collects millions of intelligence indicators per day to detect thousands of threat sources. Using Cyberint’s proprietary machine learning algorithm, you can automatically correlate raw intelligence items with your organization’s assets, prioritize threats according to their potential risk and impact, and save your organization time and resources.
Why Customers Choose Cyberint
Real-time, targeted and enriched

Advanced, anonymous crawlers and proxies
Bypasses human authentication and trust mechanisms

Continuously evolving sources and fields

Focus on the chatter that matters
Testimonials
Uncover your compromised credentials from the deep and dark web.
Fill in your business email to start.
Dive into our Resources
Focused intelligence.
Groundbreaking efficiency.
Real-time threat intelligence, tailored to your attack surface