As a Group Leader in the R&D team at Cyberint before the acquisition, we worked tirelessly to push the boundaries. Whether it was outpacing the competition with cutting-edge technology, delivering exceptional UI/UX, or ensuring our customers were satisfied with the precision and impact of our findings, we did it with a team that was small but mighty. We always said, “The skies are not the limit; we can go beyond.” And we lived by that motto, staying at the forefront of innovation with advanced automation and top-tier findings.
Then came the acquisition by Check Point—and wow, how do I put this? The “skies are not the limit” concept has shifted entirely. It feels like the possibilities have expanded infinitely. We now have the opportunity to combine Cyberint’s groundbreaking technology with Check Point’s robust suite of security products, forming an iron fist against cyber criminals. Together, we’ll make it incredibly difficult for anyone to breach our customers’ systems or cause harm.
Every time I sit at my desk and reflect on what’s next, I’m overwhelmed by the endless options. Should we integrate with Playblocks? Quantum Security Gateway? Harmony Endpoint? Perhaps enrich our IOC feeds so customers gain deeper insights into threats? It’s like being a kid in a candy store, with so many amazing opportunities ahead.
So, where did we start? Well, why limit ourselves to one thing? We’re tackling four integrations in parallel! After just one month as part of Check Point, we’ve nearly completed the integration into the Infinity Portal and are diving deep into other innovative connections.
And for those who worry that we’ll lose focus on improving ERM, don’t fret. If you know Cyberint’s R&D, you know we excel at handling multiple priorities while maintaining exceptional quality. Rest assured, the impactful alerting and insights you’ve come to expect from us are not only here to stay but will soon be better than ever.

Playblocks, powered by Cyberint’s ERM, can automatically reset exposed employee credentials after ERM identifies a breach notification. This removes manual intervention, speeds up response times, and reduces potential damage.
When Cyberint’s ERM detects exploitable vulnerabilities or uncovers breach techniques, integration with Check Point’s Quantum Security Gateway offers a powerful mechanism to respond through virtual patching.
Virtual patching provides a way to protect against vulnerabilities without requiring immediate software updates. Instead of taking drastic actions like closing a port, which may not be feasible if a mission-critical service relies on it, Quantum can apply tailored signatures or rules to block malicious activity targeting the vulnerability.
For example, if ERM simulates an attack and successfully breaches an asset using a new method, these findings can be directly fed into Quantum’s IPS (Intrusion Prevention System). The IPS can then create and deploy enhanced rules to address the specific vulnerability, ensuring real-time protection without disrupting operations.
This approach ensures:
This integration not only reinforces the immediate security posture but also helps evolve Check Point’s threat prevention systems, creating a more adaptive and intelligent defense ecosystem.
Cyberint can feed its advanced malware intelligence into Harmony Endpoint Researchers, enabling the creation of new malware signatures to proactively defend endpoints from evolving threats. This not only improves endpoint security but also helps build a more adaptive and resilient ecosystem.
Through integration with Check Point’s Quantum Security Gateway, we can derive critical insights from blocked traffic due to exploit attempts:
While the integration between Cyberint and Check Point brings infinite possibilities, it also presents unique challenges—technological, operational, and strategic. These challenges aren’t obstacles but rather opportunities to refine and innovate as we build a seamless security ecosystem for our customers.
Integrating Cyberint’s ERM with Check Point products involves handling vast amounts of IOCs (Indicators of Compromise) and threat intelligence. Scaling our systems to manage this massive influx of data efficiently is no small feat. Ensuring the pipelines remain robust while providing real-time updates to customers is critical.
Performance is paramount. For example, when ERM identifies exposed credentials and triggers Playblocks automation to reset those credentials, the process must be near-instantaneous to minimize the potential for exploitation. Similarly, automated actions, such as closing ports in Quantum Security Gateway, demand low-latency responses to be effective. The challenge lies in maintaining this speed while ensuring accuracy and avoiding false positives.
In a world of infinite possibilities, deciding where to start is a challenge in itself. Should we focus on automating employee credential resets first? Or prioritize enriching IOC feeds? What provides the greatest ROI for both our customers and our development efforts? Balancing immediate needs with long-term goals requires meticulous planning and cross-team collaboration.
In theory, integration sounds simple, connect Product A with Product B, and you’re done. But in practice, it’s far more nuanced.
Each challenge forces us to collaborate closely with Check Point teams, learn from their deep expertise, and adapt our approaches accordingly. By doing so, we not only enhance the integration process but also discover untapped opportunities for synergy.
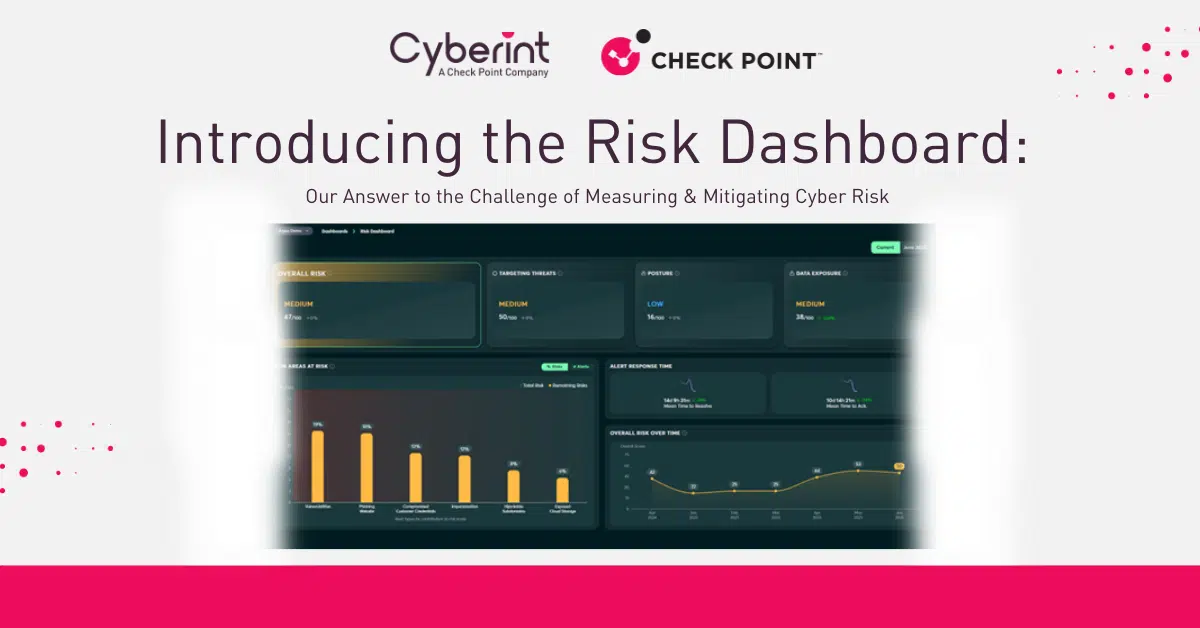
Cyberint, now a Check Point company, reduces risk by helping organizations detect and mitigate external cyber threats before they have an adverse impact. The Check Point External Risk Management solution provides superior visibility through continuous discovery of the evolving attack surface, combined with the automated collection and analysis of vast quantities of intelligence from across the open, deep and dark web.
A team of global military-grade cybersecurity experts work alongside customers to rapidly detect, investigate, and disrupt relevant threats – before they have the chance to develop into major incidents. Global customers, including Fortune 500 leaders across all major market verticals, rely on Check Point External Risk Management to protect themselves from an array of external risks, including vulnerabilities,
misconfigurations, phishing, impersonation attacks, malware infections, exposed credentials, data leaks, fraud, and 3rd party risks.

©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start