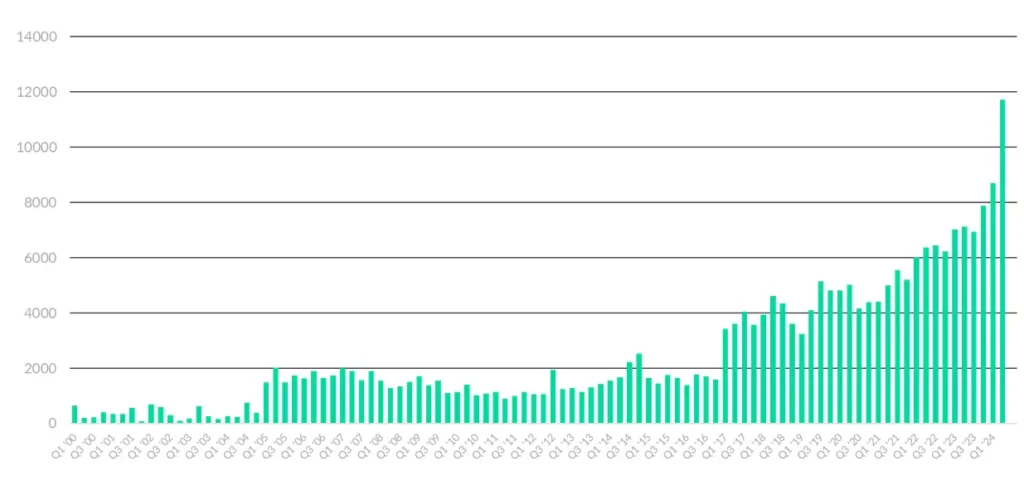
Organizations are overwhelmed by the sheer volume of vulnerabilities detected across their digital assets. Teams risk wasting time on low-impact issues while missing critical vulnerabilities that attackers could exploit. This inefficiency increases exposure to breaches and prolongs Mean Time to Resolution (MTTR). The diagram below shows the number of new vulnerabilities detected per quarter, from the year 2000 to Q1 2024, and the trend is not hard to see:
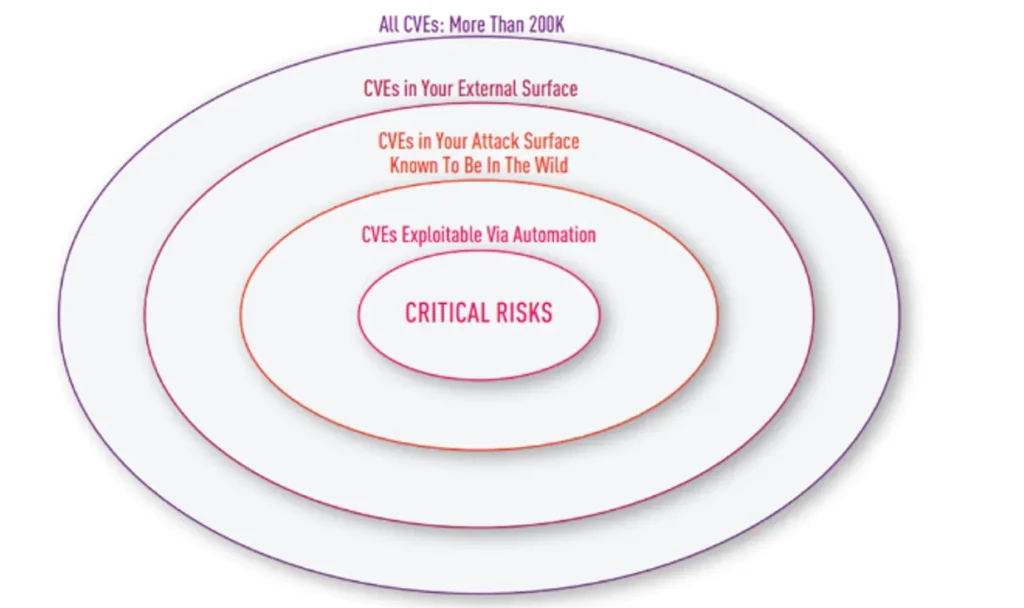
Effective vulnerability management begins with a clear understanding of your digital attack surface. This is where Check Point’s External Attack Surface Management (EASM) lays the foundation. ASM automatically discovers your organization’s exposed assets, both known ones and unseen assets (Shadow IT), including:
Once discovered, ASM analyzes these assets to identify the technologies and services running on them.
After identifying vulnerabilities on your attack surface, EASM can go a step further by executing Active Exposure Validation (AEV). AEV doesn’t just stop at detection. Rather, it actively attempts to exploit CVEs and other security issues, resulting in actionable, high-value alerts that identify urgent risks.
This seamless process turns the overwhelming task of vulnerability management into an efficient and highly targeted effort, saving time and reducing the likelihood of critical threats going unnoticed.
Whereas traditional vulnerability detection techniques merely observe an outdated software product with known CVEs and generate an alert, AEV goes one step further with automated attempts at exploitation. Various environmental factors and security controls can prevent exploitation of some CVEs, even when the software is unpatched and has known vulnerabilities.
AEV is a solution that empowers security teams to act with precision, saving time and resources while strengthening overall security posture. The ROI of implementing AEV is immense. Let us take a closer look at a few real-life use cases where AEV has been shown to give value to our customers.
AEV identifies exploitable vulnerabilities, reducing noise and delivering the highest-value alerts. Let’s explore this use case by looking at the below vulnerability, as shown in the CVE Intel section of the Cyberint solution:
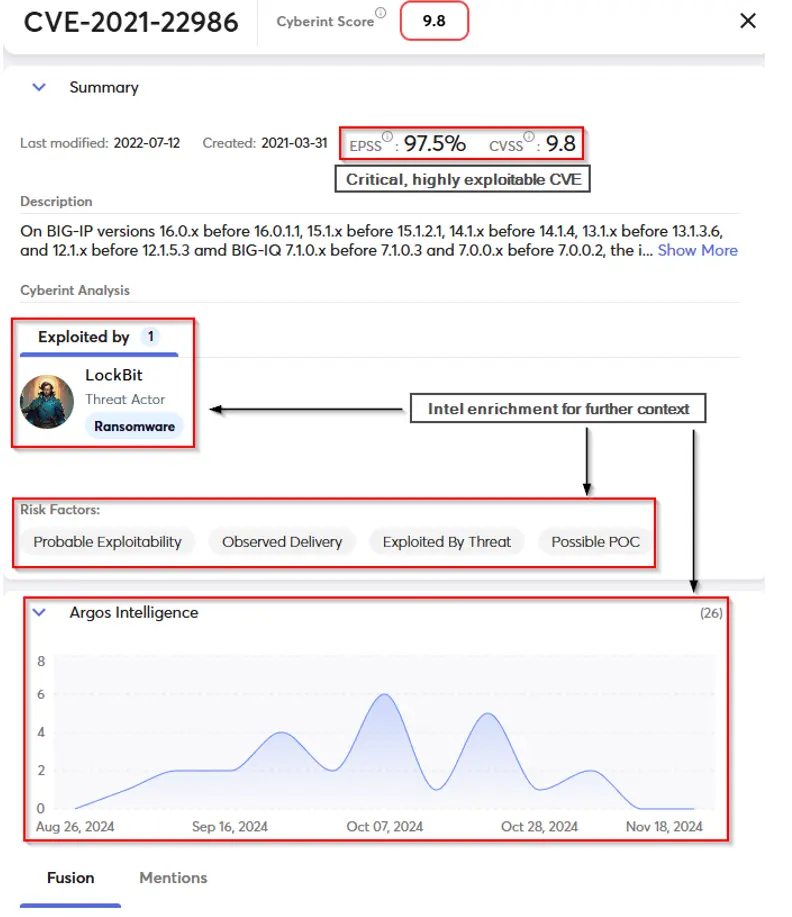
Important things to notice here:
Normally, most security policies would require critical vulnerabilities such as this one, to be fixed within a brief period of one to two weeks. However, given the proven exploitability, likelihood of imminent exploitation, and additional context we provide through our intelligence collection, the policy may be fine-tuned to require a much faster fix, quickly disarming this ticking time-bomb.
As shown above, Active Exposure Validation (AEV) ensures fixes for critical vulnerabilities are not delayed. But it also goes the other way around. With the power of AEV, you can shine light on vulnerabilities which many security policies could easily discard. Let us look at this one:
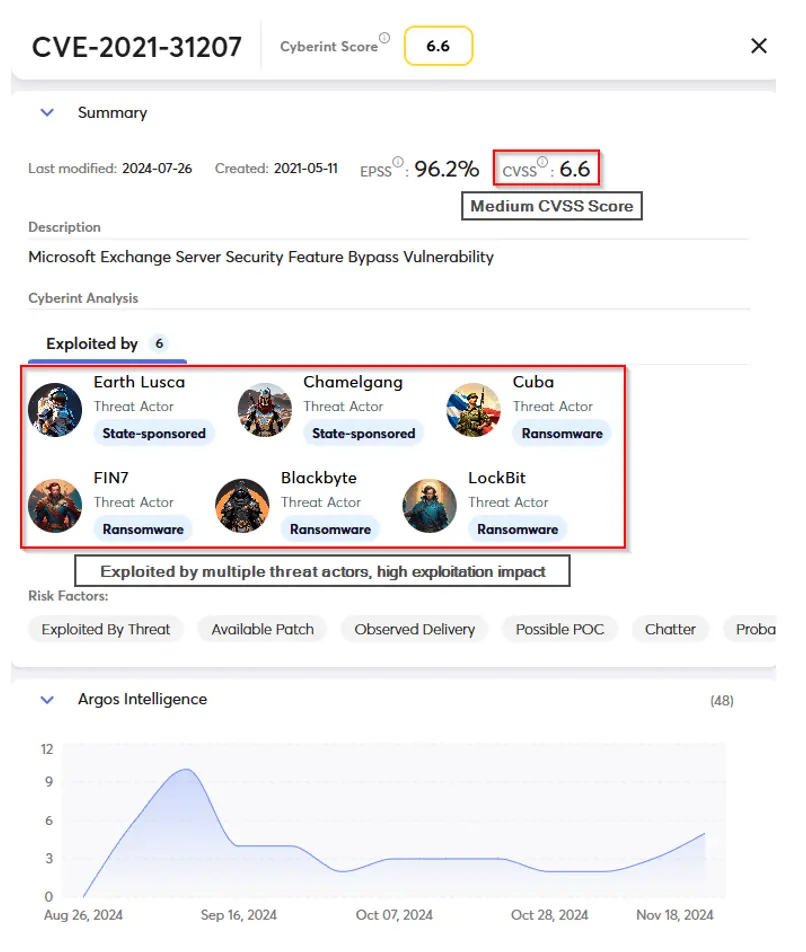
So, what do we see here?
This vulnerability is in fact part of the well-known ProxyShell suite of vulnerabilities, which target the Microsoft Exchange Server and allow for remote code executions.
Many security policies would allow a medium-scored vulnerability such as this one to exist in production environments for months. With AEV, you can fine-tune your policy to mandate a quicker fix, even though the CVSS score is not high.
One challenging aspect of vulnerability management is convincing application owners, IT teams, or engineering teams to prioritize fixing vulnerabilities. Often, these teams face competing demands and may question the urgency of addressing certain risks, especially when they perceive them as low-priority or theoretical.
AEV addresses this challenge by providing detailed exploitability evidence for each vulnerability. This includes clear, actionable data such as the commands or payloads used during validation, along with the exact responses that confirm exploitability. Armed with this information, SOC teams can make compelling, evidence-based arguments to justify why certain vulnerabilities need immediate attention.
By bridging the gap between technical findings and actionable insights, AEV empowers SOC teams to negotiate more effectively, ensuring that the most critical vulnerabilities are addressed without unnecessary delays.
AEV enhances red team operations by providing precise, reproducible evidence for validated vulnerabilities. With this information readily available, red teams can quickly reproduce issues without the need for extensive manual validation. This increases efficiency and saves countless hours.
By streamlining the validation process, AEV frees red teams to focus on deeper investigations, such as identifying additional attack vectors or assessing the broader impact of an exploit. This efficiency not only saves valuable time but also improves the overall quality of red team assessments, making AEV an indispensable tool for collaborative security efforts.
Active Exposure Validation provides a smarter approach to vulnerability management by focusing on real-world exploitability. By helping organizations prioritize risks, refine security policies, and enabling effective collaboration between SOC teams and stakeholders, AEV ensures security efforts are more targeted and efficient. As part of Cyberint’s ASM and Threat Intelligence ecosystems, AEV transforms vulnerability data into actionable insights, reducing MTTR and enhancing an organization’s overall security posture. With ongoing advancements, AEV strives to be a valuable tool in addressing today’s cybersecurity challenges.
At Cyberint, now a Check Point Company our journey with AEV is just getting started. We remain committed to enhancing its capabilities to provide even greater value to our customers. Many exciting new features are on the horizon, including expanded vulnerability coverage, advanced prioritization tools, and deeper integrations to further streamline security workflows.
This dedication to innovation is further amplified by Cyberint’s recent acquisition by Check Point Software Technologies. As part of the Check Point family, we are uniquely positioned to leverage combined expertise and resources to push the boundaries of attack surface management and vulnerability detection. Together, we aim to deliver innovative solutions that empower organizations to stay ahead of emerging threats while maintaining a sharp focus on what matters most: securing your digital assets.
Stay tuned as we continue to evolve Active Exposure Validation and the EASM ecosystem and get a demo by clicking below:

©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start