Phishing
Intercept emerging phishing threats before an attack is executed.
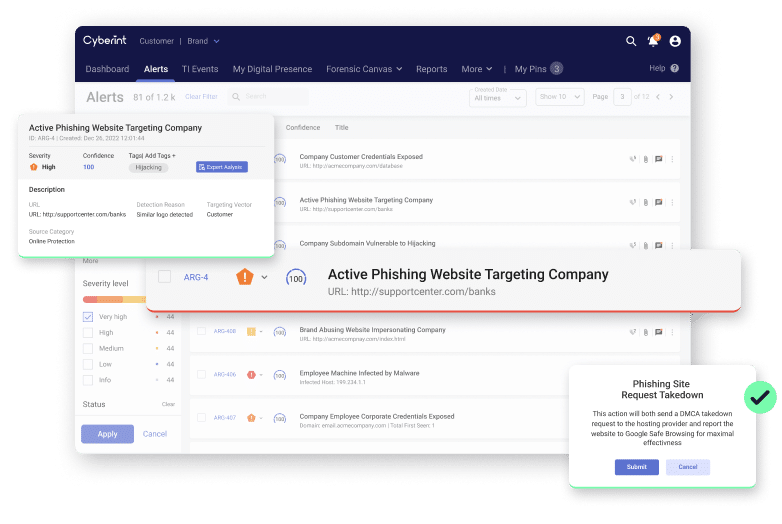
Drastically reduce response time and number of attacks. Detect malicious website clones before they go live. Request take down of phishing pages in a click of a button.
Detection of phishing URLs
Avg. takedowns/month
IP addresses continuously scanned
Takedown success
End-to-end phishing coverage
Cyberint uses various methods to identify potential phishing attacks and ensure end-to-end coverage, detection and protection from phishing attempts.
Identify typosquatting domains
Cyberint continuously monitors for similarities between your domains and the newly registered candidates to provide a level of indication of malicious intent, and alerts you of suspicious newly registered lookalike domains.
Phishing URL feed analysis
For third-party reputation feeds (e.g., permutations).
External chatter monitoring
Mentions of your name, domain/s, logos, and digital assets within the website source code as well as the URL – all from a pool of external and proprietary Resources that surface suspicious candidates.
Phishing Beacon
Detects phishing sites before they negatively impact your organization.
Threat Intelligence
Cyberint’s Threat Intelligence sources aid in supplying intelligence on the trends and phishing options in the threat actor market. This includes detecting indicators of attack from dark web sources.
Mitigation and takedowns
Request a takedown in one click straight from the Argos platform. Cyberint does this quickly and automatically, including all hosts.