


In the early days of this campaign, Nevada was the leading group to initiate the campaign. Not too long after, we have seen another new group, ESXiArgs, abusing ESXi vulnerabilities and claiming many victims.
Although this incident was mostly around one particular CVE (CVE-2021-21974), we assume that more CVEs are being exploited in this campaign that can lead to RCE by threat actors such as:
We believe that this is the real issue now. It’s important to understand that these two groups are relatively new and you can see by the ransom note of ESXiArgs that they don’t even have a leak site.
As this campaign is getting bigger by the hour, it is not about one particular family but rather several that might join this campaign as they see the victims count rise.
The real problem is that veteran and professional groups such as ALPHV and LockBit3.0 see the potential damage they can do and are very likely to join this campaign. Hence, the issue became more about the unpatched systems than the families and the relations between them
EXECUTIVE SUMMARY
Over the weekend, a relatively new ransomware group named Nevada Ransomware initiated a first massive campaign, targeting any ESXi machine that is exposed to the internet. The group seemed to compromise hundreds of servers over the weekend and caused major damage. Although the scale of this campaign is one of the biggest we have seen, it might already have a solution.
WHO IS NEVADA?
Nevada group was first introduced to the cybercrime industry in December 10, 2021, as they published an announcement of recruiting new members to their Ransomware-as-a-Service plan.
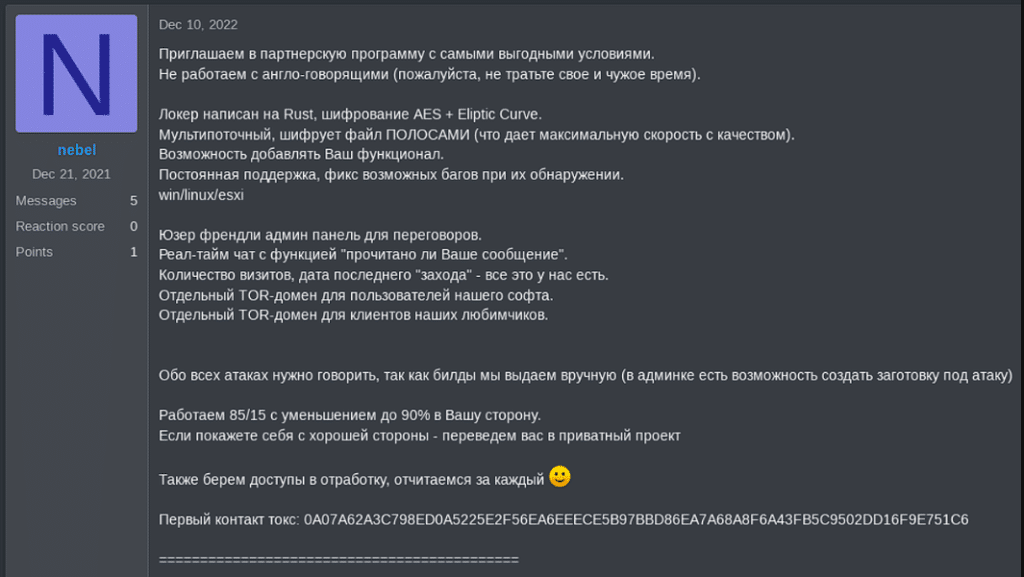
Nevada group’s first recruiting announcement
The group works only with Russian and Chinese-speaking individuals.
Their encryption module is built in Rust and is currently still under development as the group claim they will target Windows and Linux machines in addition to ESXi.
As the group is still very new, there is a chance that this incident was merely an initial experiment for their products and a free PR they have received given the fact that any threat actor in the cybercrime industry knows their name.
CONTROL PANEL
The group has a dashboard for each member to log in that grants access to private information about ongoing campaigns, chat with other members and so on.
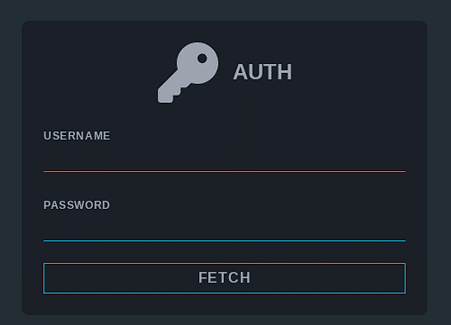
Nevada login page
VICTIMOLOGY
As mentioned, the group includes only Russian and Chinese speakers. Due to that, the group’s encryption module does not target Russia, Albania, Hungary, Vietnam, Malaysia, Thailand, Turkey and Iran.
Over the weekend, the group targeted any front-facing ESXi machine that could find and exploited multiple related vulnerabilities. A big part of the victims’ count is focused on France.
The group encrypts the configuration files of the ESXi systems instead of encrypting the vmdk disks themselves.
Then, a ransomware note is left for the victim with contact information for negotiations.
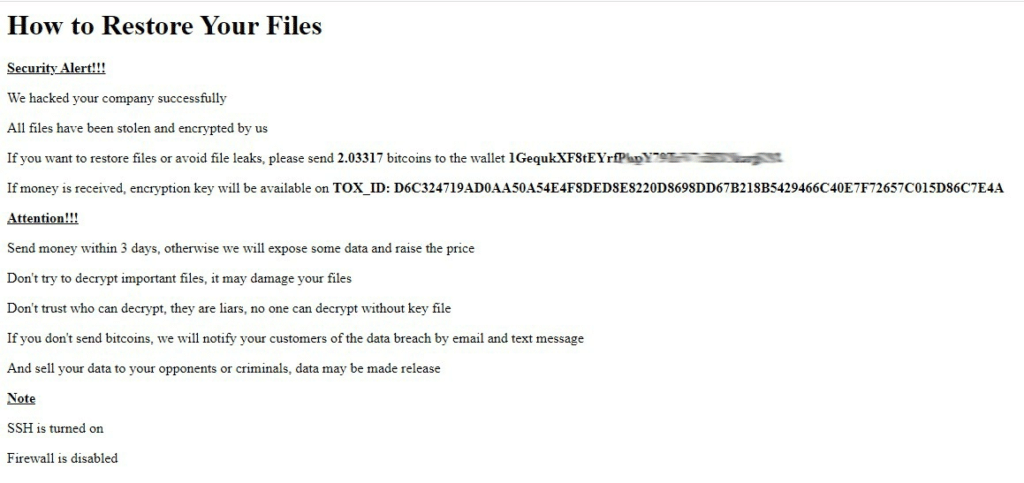
Nevada ransomware note
A SUCCESS STORY?
At first glance, it seems like the ultimate success story for any new threat group out there – hundreds of victims in one weekend with only few weeks of operation.
The group was able to cause a lot of damage to its victims which is true, but currently it seems that not a lot of victims has paid the ransom.
When tracking the balance in the wallet addresses the group provided in their ransom notes it seems that there had 0.5BTC transferred to their wallets – not much for this scale of a campaign.
Overall, the group might still take this event as a major win and a massive debut both because of the number of victims that goes by the hundreds and the major PR the group has received as any criminal in the cybercrime industry knows who they are which might help in recruiting some talented people.
CONCLUSIONS
Nevada Ransomware group is a new and interesting group. comparing their debut to other new groups such as BianLian, Royal and BlackBasta on 2022, no one was able to obtain the victims’ count Nevada did.
Overall, the group might consider their debut as very successful although it seems to have little profit in the matter of finance.
The group is at a very early stage and it will take a bit of time and effort to recruit and develop their modules in order to make some impactful campaigns, but the Cyberint Research Team is convinced that they might be a solid new threat in our landscape in the near future.
RECOMMENDATIONS
IOCS
©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start

