For years, the BFSI industry has been a top target for cyberattackers. Yet, despite long-standing awareness of financial cyber risks, the problem is only getting worse as banks, insurance companies, FinTech businesses and other organizations that operate in the finance sector face a growing array of threats and risks.
For example, threat actors are increasingly using financial organizations’ customers as a vector for attack. That means that attack surfaces have grown, and that securing a finance business’s own IT estate isn’t enough to prevent breaches. Organizations also need to think about the risk posed by attacks against customers.
That’s the bad news. The good news is that conquering financial cyber risks is possible – but only if you know which forms the risks take and how to prioritize them. This article breaks down those topics by explaining which types of risks are most prevalent for different types of financial organizations.
Here are the top 3 cyber threats for the banking industry, according to Noel Anthony Llimos, a Senior Intelligence Analyst at Cyberint who has been helping protect banks for more than 6 years.
Banks are often hot targets when it comes to cyber attacks, primarily because when a cyberattack is successful the financial rewards are often immediate and plentiful.
Phishing is not new, but threat actors are taking advantage of novel twists on traditional phishing attacks to breach banks.
One example is malvertising, which means leveraging malicious ads, which they promote through Google Ads, to lure targets into visiting phishing sites designed to steal their information.
Smishing, or the use of bulk SMS messages, are another type of phishing attack that we’re seeing threat actors direct against banks more frequently. Smishing has become easy to execute thanks to bulk SMS services that attackers can purchase on the Deep/Dark Web.
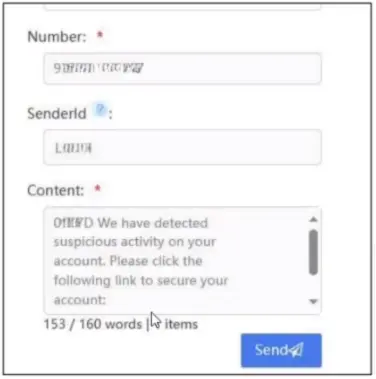
These services make it easy for attackers to send malicious messages to large groups of targets. The messages deliver information – like prompts to report suspicious activity on a bank account – that can result in threat actors gaining access to login credentials or other sensitive information.
Vishing, which means the use of phone calls or voicemail to trick targets into revealing sensitive information, has also surged. It’s especially prevalent as a means of targeting older and more vulnerable people, who are less tech-savvy and more likely to fall for schemes where threat actors call and pose as tech support staff, for example.
In addition to opening new modes of attack, these phishing techniques help threat actors work around more sophisticated access controls on banking websites. For instance, if a bank requires a one-time password for a user to complete a login, a threat actor could launch a vishing attack where he poses as a tech support person, then asks the target to initiate a banking app login and hand over the one-time password code. With that information, the threat actor can then log into the victim’s bank account directly.
Banks frequently rely on third-party vendors and suppliers, and tight regulations in the finance industry mean that banks’ third-party relationships tend not to change frequently (Often many banks in one country use the same small set of vendors; this is especially true in APAC). As a result, threat actors have learned that they can breach banks’ defenses by exploiting vulnerabilities in the third-party organizations they work with.
If you’re a threat actor seeking to breach a bank, then, you might start by searching the Dark Web for information about one of the bank’s suppliers. If you can obtain credentials that give you access to the financial institution that the supplier works with, you get a side door into the bank’s IT estate.
The MOVEit supply chain attack was one example of this type of breach. So was the breach against SXI, which was a major supplier to Philippine banks. When attackers compromised SXI, they gained an entry-point into banks’ own IT estates.
Banks’ own employees can become threats, too – and we’re not talking here just about disgruntled employees out to cause harm to the company. Innovative threat actors may place workers inside a bank, then use their access to compromise the institution.
We see this type of attack play out especially frequently in call centers. Because call center employees typically don’t require specific background skills, it’s easy for threat actors to place someone inside a bank’s call center who, once hired, will act as a malicious insider. Alternatively, employees of call centers are often tempted by the lucrative financial rewards of becoming a malicious insider and approach the threat actor groups themselves.
Here are the top 3 cyber threats for FinTech companies, according to Ariel Friedstadt Rabecoff who has been helping protect FinTechs for more than 10 years.
Like traditional banks, FinTech companies also face phishing risks. Phishing against FinTech businesses can be especially lucrative for threat actors because:
“Even the best technology implemented might not work if a recipient blindly trusts any sender, does not take time to evaluate the legitimacy of content, and presses any link s/he gets,”
Catry, Head of Compliance at ConnectPay said.
FinTech apps are typically designed to make it easy for users to perform actions. Threat actors can leverage that attribute against the apps by using accounts in a fraudulent way (Especially if KYC authentication is weak).
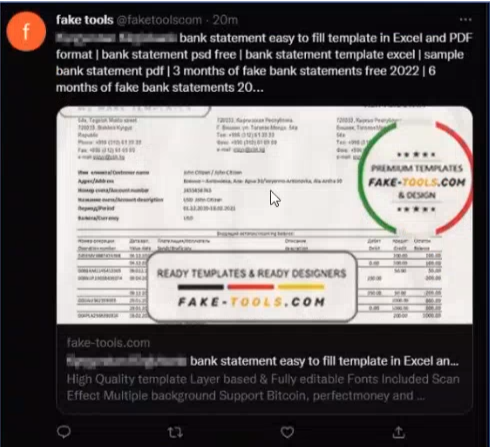
For instance, they can buy user IDs for a FinTech app or obtain those IDs via phishing. Then, they apply for a loan through the app, using falsified documents to support their application.
The above website for example offers fraudulent:
Fraudulent accounts can also be created through the use of a mule’s existing account. Threat actors can buy access from current users and then apply for a loan using that account.
Exploiting software vulnerabilities in FinTech apps is another common type of financial cyber risk. Threat actors might find flaws in the ways an app handles one-time passwords, for example, or even issues with application logic that make it possible to bypass access controls altogether.
These vulnerabilities can exist in any type of app. But given that FinTech companies often aim to move quickly, and that their apps in many cases are relatively new, they may be subject to more vulnerabilities than apps that have existed for years.
Here are the top 3 cyber threats for insurance companies, according to Sacha Goldberg who has been helping protect BFSI companies including insurance for more than 5 years.
Exploitation of software vulnerabilities is a risk for insurance companies, too. In this context, threat actors use vulnerabilities to bypass security controls and access sensitive data.
Threat Actors often target known vulnerabilities in software used by insurance companies. This could involve exploiting zero-day vulnerabilities or taking advantage of known vulnerabilities that have not yet been patched. The vulnerability that enabled the MOVEit breach was used in this way, for example, to breach companies like CareSource, American National and Prudential Malaysia.
This can lead to data breaches, brand damage, significant financial loss and general business disruption.
Insurance companies make for attractive phishing targets because their systems often integrate with those of financial and healthcare institutions. Accessing an insurance company’s network can provide a backdoor to other systems, widening the scope of potential cyberattacks. If threat actors can trick an employee or customer into giving them access to an insurance company’s systems, they may also be able to steal sensitive data from other businesses.
These attacks can also lead to theft of financial assets. Insurance companies control significant assets and funds, and threat actors who breach their systems can redirect payments to themselves or steal funds outright.
Ransomware is another way that threat actors can breach insurance companies. Put simply, “insurance companies have a lot to lose in cyberattacks,” as DarkReading notes.
Attackers who are able to hold these types of data for ransom gain a great deal of leverage over insurers – which is exactly what you want to do if you’re a threat actor seeking to get a large ransom payout.
Threat actors primarily seek:

Fill in your business email to start.
Here are the top 3 cyber threats for the credit card companies according to Jono Angelo Biyo who has been helping protect BFSI businesses for more than 11 years.
Threat card companies, too, face a host of financial cyber risks.
Threat Actors often start with phishing, which threat actors use to gain access to one-time password codes, just as they do for banking apps.
ATM fraud presents another risk, especially in markets where cards aren’t always required to access funds. For example, threat actors can abuse “retiro sin tajeta” (or cardless withdrawal) access policies in Latin America, which allow customers to withdraw funds without having a physical ATM card. Instead, they verify their identities using methods like:
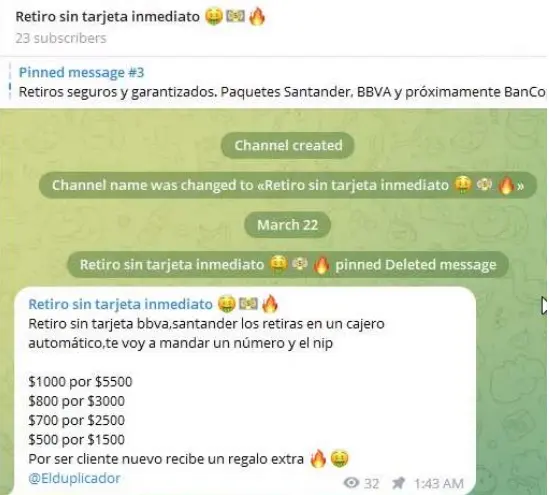
If threat actors can trick targets into performing these actions on their behalf, they can exploit cardless withdrawals to steal funds from a victim’s account. They could use a technique like vishing to convince a target to log into a mobile app and authorize an ATM withdrawal that the attackers have initiated, for example.
Cardless withdrawal is becoming more popular in Latin American and beyond because it simplifies access to funds, but it also gives threat actors new modes of attack. It’s an example of how, “with the growing sophistication of cybercriminals, ATM networks have become prime targets for various cyber threats,” according to Industry Research Co.
But it is not only in Latin America. Many US banks have begun to use the technique too. Below is a list of just some of them.
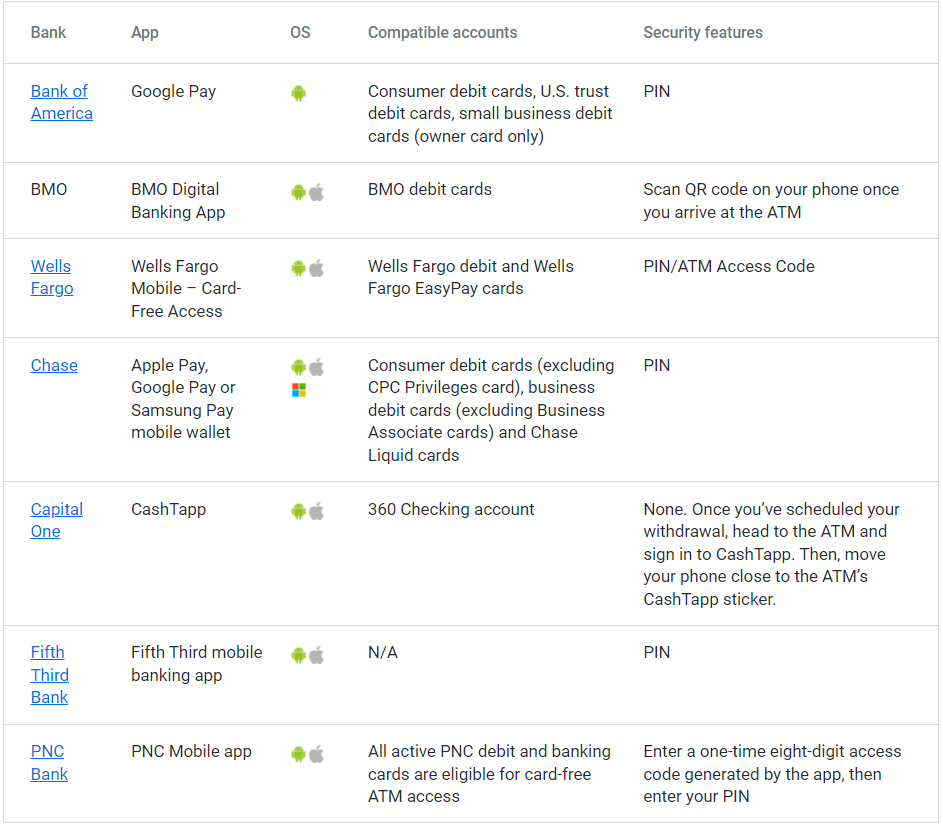
It is important for banks and credit card companies to take precautions to reduce the risk of this type of frauds, by enabling biometric security and two-factor authentication. Additionally it is recommended to advise users that utilize banking Mobile apps to report their stolen devices as soon as it happens in order for the credit card company or the bank to take the necessary precautions and avoid illegitimate activities.
Smaller ecommerce websites often have weaker security and are often breached. This is a major worry for credit card companies as often customer’s PII including credit card details, numbers, emails, names and more are stolen there. Small time hackers often expose the ecommerce sites’ databases. Credit card companies are often held responsible for these other companies’ security flaws.
For all types of financial organization, the key to protecting against cyber risks is prioritizing. You can’t block all risks, but you can react to the most serious ones first.
In general, financial organizations should prioritize risks based on attributes such as:
To assess these risk factors, financial businesses require threat intelligence. Threat intelligence details which vulnerabilities threat actors aim to exploit based on information such as vulnerability discussions on the Dark web.
Threat intelligence can also assess how easy an attack is to carry out by evaluating whether automated exploits are available. And it can provide insight into whether attackers are targeting certain industries or countries with specific types of attacks, so that financial organizations can identify the risks most likely to impact them.
Cyberint delivers the threat intelligence, attack surface management, brand protection and third-party risk protection that businesses in the finance sector and beyond need to stay safe from the array of cyber risks they face today.
Ensure business continuity by enabling your organization’s revenue-generating activities by effectively managing and mitigating cyber risks before they cause disruption. Reduce risk by understanding the threats facing your financial organization and accurately evaluate the risk so you can prioritize and mitigate before major incidents occur. Finally improve efficiency with Cyberint’s low-touch platform, that does not require a huge commitment of time. Empower your team to work more efficiently and focus on the important stuff.
See for yourself by requesting a demo.

Fill in your business email to start