


The complex geopolitical landscape in Southeast Asia, influenced by People’s republic of China (PRC)’s strategic interests and territorial disputes, faces a prominent offensive threat from Chinese cyber operations. Southeast Asia’s economic and digital growth make it a prime target for cyber threats.
In the past 8 months Cyberint has been able to identify a major large-scale campaign. It bears the hallmarks of a broader orchestrated attack, most likely by threat actors affiliated with the People’s Republic of China (PRC). The campaign targets scores of notable financial institutions in South-East Asia.
Cyberint effectively identified the threat actors’ Tactics, Techniques, and Procedures (TTPs), Modus Operandi, motivations, and victimology.
This campaign is driven by a malicious objective: stealing identities and valuable financial data. Impersonating the largest and most known banks and financial organizations in South-East Asia, the perpetrators trick unsuspecting victims into revealing their credentials. This results in a series of devastating consequences including financial losses and reputational harm. What makes this campaign noteworthy are its geopolitical implications, as growing evidence suggests ties to actors linked to China.
The campaign lures customers to access the phishing sites via their mobile phones. It offers them attractive loans and entices them to share additional personally identifiable information (PII), such as Social Security Numbers, date of birth, address, credit card details, income information, phone number, copy of ID, and even a handwritten signature.
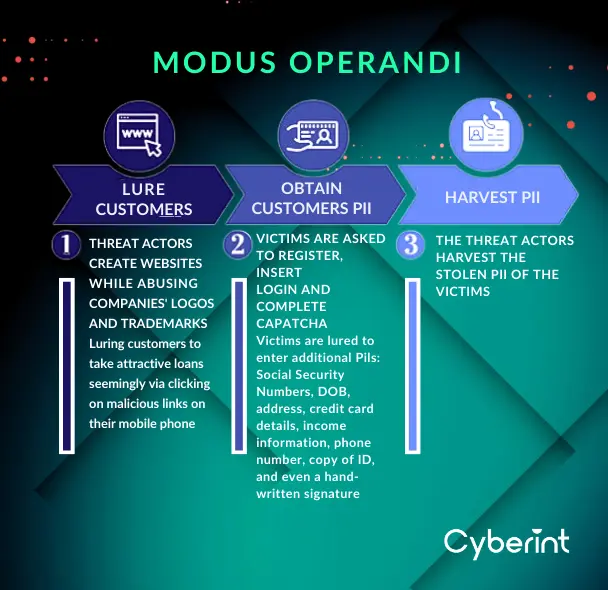
The designs of the sites are usually made of graphic materials, seemingly taken from the official sites and social media accounts of the targeted financial institutions. By abusing their logo and trademark, the malicious sites gain credibility.
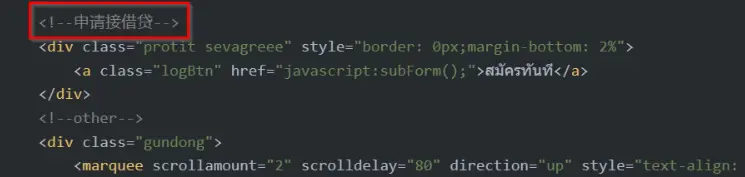
Cyberint was able to analyze the HTML code of the phishing sites throughout the time of the campaign. Notably, the site’s HTML code is built without mentioning any of the companies’ names or brand names, possibly to avoid detection.
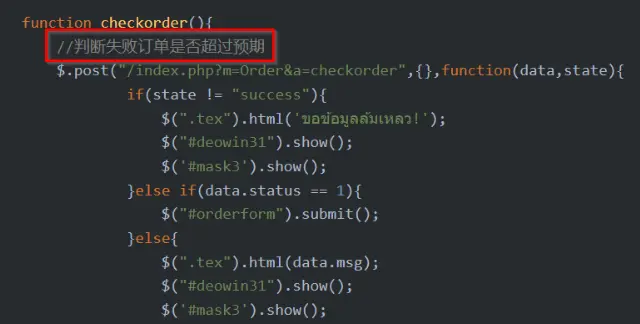
The below multiple code snippets showing notes and comments written in Simplified Mandarin (Chinese):
判断失败订单是否超过预期 (in Chinese: Determine whether failed orders exceed expectations)
The Cyberint Threat Intelligence team used several tools as well as VPN and proxies services, to perform scans on the accessible sites, aiming to ascertain whether they are deliberately blocked in specific geographical locations across the globe. The results of the scans showed that in certain areas of China the sites are not accessible.
The above-detailed findings bear the hallmarks of a campaign strongly attributed to China-affiliated threat actors. Analysis of the HTML webpage of the sites reveals numerous embedded comments written in simplified Mandarin (Chinese).
Additionally, historical WHOIS records for certain leads of the investigation suggest that related domains were registered by multiple China-based entities. Further inspection of the sites indicates deliberate inaccessibility in certain areas of China.

With time, the campaign has grown more sophisticated, aiming to evade detection and shutdowns by cybersecurity firms. The threat actors stopped explicitly mentioning targeted financial institutions on the sites and avoided using exact copies of photos and logos (obfuscations).
Cyberint extensively utilized various photo forensic and Exif tools to analyze the graphics on the sites. Upon analysis, it was clear that the graphics were sourced from authentic company websites and social media accounts but had undergone significant alterations to obscure genuine metadata and Exif data.
Additionally, certain elements, like brand names, were intentionally blurred or obscured, indicating a deliberate effort to deceive users about their origin. This tactic suggests a high level of sophistication, as the threat actors meticulously manipulated legitimate visuals to create a false sense of authenticity on their fraudulent sites.
The Threat actors behind this campaign applied a network tunnel to mask the true origin of their activity. While typically used for legitimate purposes like secure remote administration or establishing virtual private networks (VPNs), the malicious actors in question exploit this technology to conceal the true IP address of the attack.
Multiple indications and findings suggest that the orchestration of the campaign is being done by automation. The extensive number of websites, coupled with minimal variations between them, suggests automated generation. During remediation efforts, it became apparent that after successfully taking down one site, a new one promptly emerges with minor modifications to the domain name or TLDs.
Cyberint strongly recommends consistently executing website takedowns based on copyright infringement as soon as they are detected.
Takedowns are crucial for remediating phishing websites as they prevent harm to potential victims, halt the spread of phishing links, disrupt threat actor operations, protect brand reputation, and ensure legal compliance.
Given that the campaign is directed at numerous Southeast Asia financial institutions, impacting more than just one institutions’ customer base, it is recommended for the affected institutions to collaborate with the legal and security teams of these institutions. This unified effort can efficiently address the sophisticated phishing campaign affecting their respective clienteles.
Cyberint recommends taking proactive steps by engaging sector-specific institutions such as F-ISACs (Financial Services Information Sharing and Analysis Centers) to raise awareness about the significance of combating this widespread phishing campaign. Encouraging collaboration and information-sharing within the sector through partnerships with organizations like F-ISACs is crucial for addressing cybersecurity challenges specific to the sector as a whole.
It is advisable to inform customers about the phishing campaign through various channels, including email alerts, website banners, and mobile app notifications. The message should be concise, emphasizing the following points:
By proactively communicating these recommendations, the organization can raise awareness about the phishing threat and empower customers to protect themselves from fraudulent attacks.
Cyberint, the Impactful Intelligence company, reduces risk by helping organizations detect and mitigate external cyber threats before they have an adverse impact. The Cyberint Argos platform’s patented technology provides superior visibility through continuous discovery of the evolving attack surface, combined with the automated collection and analysis of vast quantities of intelligence from across the open, deep and dark web. A team of global military-grade cybersecurity experts work alongside customers to rapidly detect, investigate, and disrupt relevant threats – before they have the chance to develop into major incidents.
Global customers, including Fortune 500 leaders across all major market verticals, rely on Cyberint to protect themselves from an array of external risks, including vulnerabilities, misconfigurations, phishing, impersonation attacks, malware infections, exposed credentials, data leaks, fraud, and 3rd party risks.

Fill in your business email to start.
Fill in your business email to start


