



I love to get stuck in and let the creative juices flow. My strengths lie in idea generation, development and execution. Over 5 years experience in B2B cybersecurity. I reign supreme when my imagination and creativity can run wild.
Predicting when a cyberattack will happen is a lot like forecasting the weather: It’s impossible to know with certainty exactly how events will play out. But with the right strategy and information, you may be able to predict cyberattacks before they start, or catch them in their beginning stages.
We explain the early warning signs of each attack technique, as well as how to assess available data to determine how likely a cyber attack is to happen.
Phishing attacks, in which threat actors attempt to trick employees or users into handing over sensitive information, often require several preliminary preparations before an attack can get underway. By looking for those preparation steps, you can predict when a phishing attack is likely to happen.
Key activities to watch out for include:
An account takeover (ATO) attack happens when threat actors compromise a legitimate account, often using stolen access credentials. It’s similar to the creation of impersonating social media profiles, except with ATO attacks, threat actors take over an official account instead of mimicking an official account.
Since most ATO attacks require threat actors to obtain access credentials ahead of time, monitoring the Dark and Deep Webs for stolen credentials is an effective means of predicting this type of cyberattack. For example, using this technique, Cyberint discovered discussion of an attack involving WooCommerce:
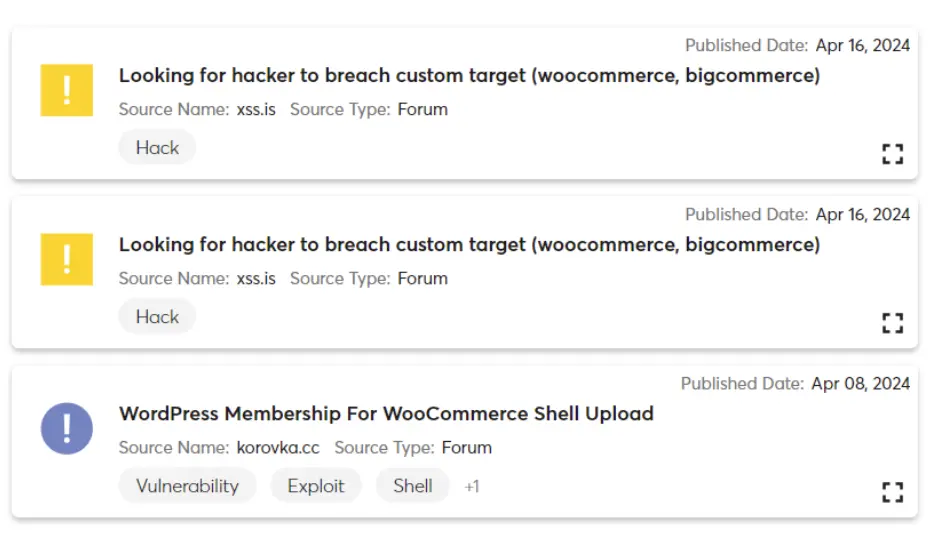
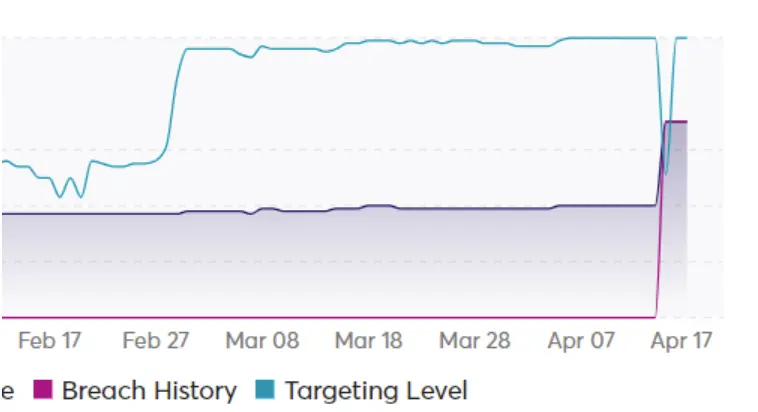
That information allowed us to identify an increase in the targeting level of the company and alert customers before the attack was publicly disclosed:
Distributed Denial-of-Service (DDoS) attacks happen when threat actors overwhelm websites or applications with bogus traffic in a bid to disrupt normal operations. Since the traffic flood often begins suddenly, there are usually few early technical warnings of a DDoS attack.
However, strategic intelligence can help to predict DDoS attacks. Specifically, organizations can track DDoS trends to determine whether threat actors have recently been targeting companies within the same region and industry with DDoS attacks. For instance, if you operate in the energy sector and other companies in that sector have recently been DDoS’d, it’s a sign that you should probably bolster your own anti-DDoS capabilities.
There are two effective strategies for predicting when a supply chain attack involving one of your vendors is likely to happen.
One is to monitor for signs that the vendor is likely to be targeted – such as Cyberint did when predicting the WooCommerce breach mentioned above.
Another is to detect attacks against vendors in their early stages. This doesn’t allow you to forecast an attack before it actually begins, but it does buy you time so that you can isolate any of the vendor’s products within your IT estate before the attack intensifies. Here again, monitoring for discussions of active attacks or stolen credentials can help discover breaches even before vendors become aware of or disclose them.
Ransomware attacks can be challenging to predict because the deployment of ransomware (meaning the malware that encrypts data) is typically the final stage in such an attack. To get to that point, attackers must already have breached your systems using a method like brute-forcing RDP ports (which is not as common today, because many organizations have taken steps to protect themselves) or exploiting zero-day software vulnerabilities (a more popular technique at present, and the one behind breaches involving vendors like ESXi, GoAnywhere and MOVEit).
This means that to get ahead of ransomware attacks, trying to detect the ransomware itself is not the best strategy (because by then it’s too late). Instead, look for early signs of vulnerability exploit techniques that might affect your company. “Security teams need to be able to recognize the initial attack long before any information is stolen and encrypted,” as Rodney Joffe writes for Forbes.
For example, if you know that the Cl0p ransomware gang is exploiting a vulnerability in the MOVEit software, and you know that your company is using MOVEit, you can bet that you’re a target and an attack is either already in progress or coming very soon.
There are many other types of cyberattacks beyond those we’ve covered here, and some are easier to predict than others. For instance, insider attacks are often challenging to anticipate because malicious insiders don’t usually share signals of their intent until the attack is already underway.
However, what matters most in forecasting all types of attacks is gathering all available threat intelligence data, determining which risks are most serious for your business and taking steps to mitigate them. Mapping and managing your attack surface is critical, too, for knowing which types of assets might be at risk.
At Cyberint, we can’t tell you with complete accuracy when every cyber attack will happen. But through threat intelligence, vulnerability intelligence and attack surface monitoring, we can maximize your ability to forecast as many attacks as possible before they begin – and to catch others early, when they are easier to contain.
To learn more about Cyberint’s approach to attack prediction and how we help companies stay a step ahead of threat actors, request a demo.

Fill in your business email to start.
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


