


CrowdStrike released a new update on their Falcon Sensor product. Unfortunately, the update caused technical issues, resulting in major outages globally to Microsoft Windows machines.
The issue caused the “Blue Screen of Death” and several reports worldwide stated that several industries were affected, such as airlines, banks, media, etc. According to CrowdStrike Tech Alert, they became aware of reports of crashes on Windows hosts related to the CrowdStrike Sensors.
Unsurprisingly, the outage wasn’t only observed by employees, customers, and IT staff. It also drew the attention of Threat Actors who sought to exploit the ensuing chaos to steal credentials, attempt to infiltrate corporations with trojans and engage in other malicious activities.
A multitude of cybersecurity professionals have been meticulously monitoring the situation and have observed an increase in the registration of suspicious typosquatting domains, coinciding with the day of the outage. These domains appear to mirror the unfolding events.
Cyberint has initiated an investigation of the shared IOCs to assess the comprehensive threat landscape, and also closely monitored the situation. Based on our investigation, the recently registered domains exhibit a spectrum of intentions, ranging from malicious websites to benign blogs. Additionally, some actors are attempting to capitalize on the event by selling merchandise, the quality of which can only be described as subpar.
Nevertheless, there is no risk in monitoring these benign blogs and domains and including them in the blocklists, as they could also be altered to host malicious content in the future.
The threat has been reported in numerous unofficial communication channels, which exist between Cyberint employees and other cybersecurity professionals (the specifics of which cannot be shared).
Threat Actors have been attempting to impersonate CrowdStrike support staff or IT personnel to steal credentials and potentially infect systems with a Trojan. This underscores the importance of vigilance in the face of current events.
Through the collaborative efforts of Cyberint’s partners and various unofficial channels, it has been reported that numerous entities affected by the outages have experienced a surge in targeted attacks. These Threat Actors have been attempting to impersonate supposed support staff from CrowdStrike. The modes of these attacks have been diverse, ranging from phone calls to phishing emails.
As the outages continue to directly impact a growing number of industries, these entities inevitably become attractive targets for more sophisticated Threat Actors. These malicious actors are likely to exploit the situation to attempt to steal sensitive credentials or attempt to install malware on the machines of employees.
Cyberint initially observed 17 typo-squatting domains, as of writing most of which are either benign or parked domains with no online content. The vast majority of domains that could have been considered malicious were taken down on short notice, limiting further analysis.
Cyberint noticed a pattern between the various groups of investigated IOCs, which can be summarized as follows:
The second most significant activity detected after the benign domains are suspiciously registered domains that are seemingly financially motivated.
For example, two such domains were observed copying and sharing Crowdstrike’s workaround fix – and seemingly taking credit for the fix, trying to collect donations. The exact motive is unclear, as Cyberint was able to follow the breadcrumbs and PayPal donation to a software engineer – Aliaksandr Skuratovich, who also posted the website on his LinkedIn page. The donation could be intended as a joke.
![Figure 1: Workaround Fix Shared with Donation Link at crowdstrike-bsod[.]com & fix-crowrdstrike-bsod[.]com](https://cyberint.com/wp-content/uploads/2024/07/Screenshot-2024-07-21-085540.webp)
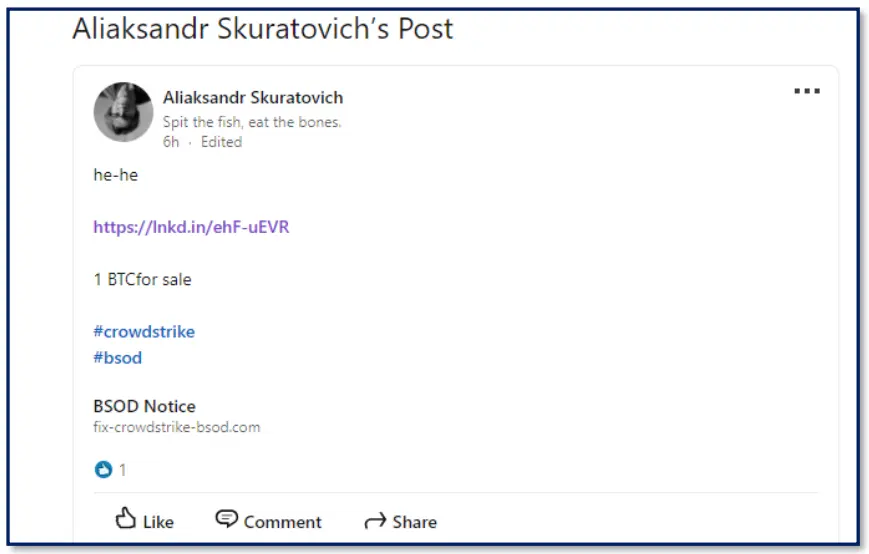
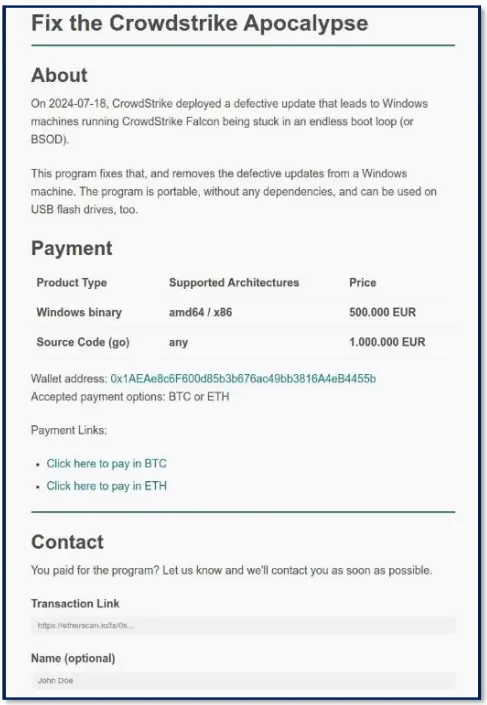
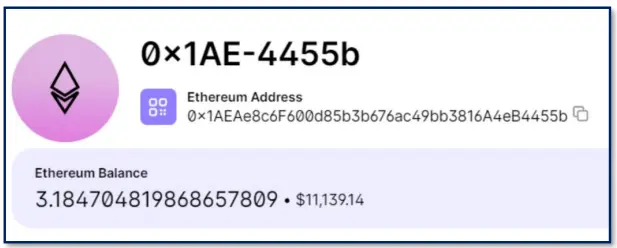
Other notable domains are more evidently malicious in nature – trying to claim to own a fix and offering their service for a fee of 500 or 1,000 Euros via a crypto account. The domains were promptly taken down and were not online during the investigation. Unfortunately, several entities fell victim to these scams, and a wallet linked to the scam has been observed with over 11,000 USD in funds. The fraud may also be distributed via phishing emails.
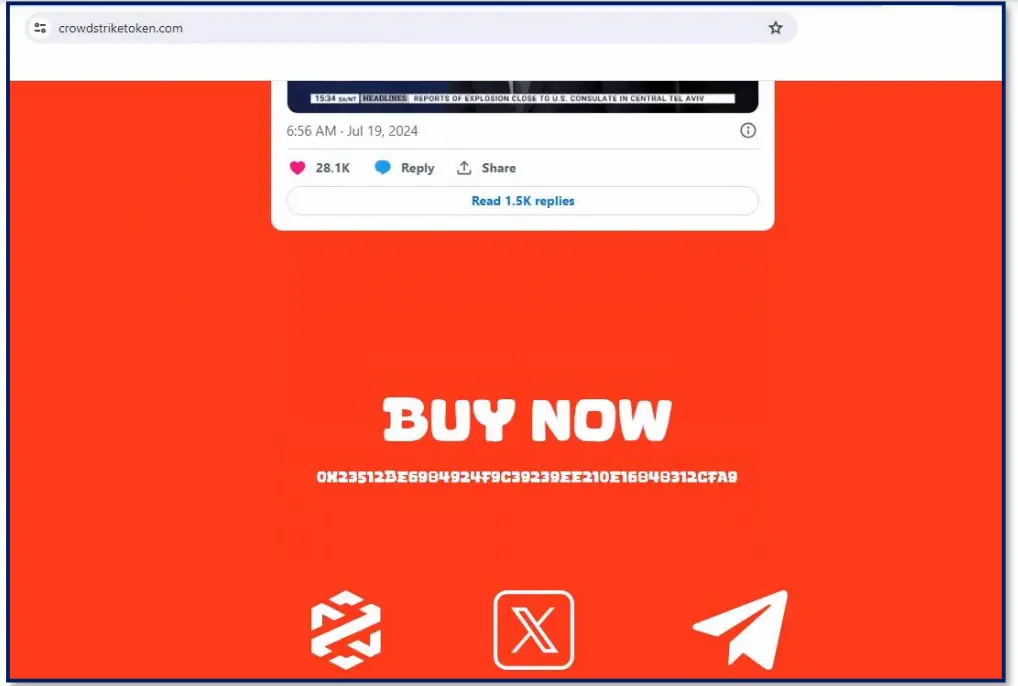
Surprisingly even crypto scams related to Crowdtrike were observed with a whole social media presence infringing on the Crowdstrike brand. Said group has been observed selling supposed cheap stakes of crypto shares related to Crowdstrike.
A significant proportion of the lookalike domains targeting Crowdstrike, which were registered on July 19th, are presently inactive and distributed across a variety of hosting providers. A small majority of these domains are hosted on Squarespace. At the time of writing, the majority of these domains do not possess a mail exchange server, which could potentially signify the intention to initiate a phishing campaign.
However, due to the limited record data currently available due to their parked nature, there is no corroborating evidence to suggest that these inactive domains have been registered by the same individual.
Furthermore, in addition to the aforementioned domains, several benign domains include a variety of blogs. Some of these blogs appear to be merely replicating data that describes CrowdStrike, while others seem to be altruistic in nature, providing explanations about the outage, detailing the industries affected, and offering links to official CrowdStrike sources.
Additionally, some other domains are just joke domains, distributing memes and trashing Crowdstrike’s reputation. While these benign domains do not have malicious content as of writing, this situation could rapidly evolve into a phishing campaign in the future.
During severe outages and industry disruptions, it is almost inevitable that Threat Actors will seek to exploit the resulting chaos for their benefit. Coincidently, the creation of various benign blogs and domains for humor can inadvertently serve as an effective smokescreen for their activities while also wasting time for cybersecurity professionals.
During such events, it becomes crucial to maintain a heightened level of vigilance. It is particularly important to meticulously investigate any support emails that offer unsolicited assistance or solutions. These could potentially be deceptive tactics employed by Threat Actors. Therefore, it’s always advisable to verify the source and authenticity of such communications to safeguard against potential threats.
| Domains of Interest | IP Address of Interest | Other Info |
|---|---|---|
| fix-crowdstrike-apocalypse.com | 80.78.22.84 | Domain is Down |
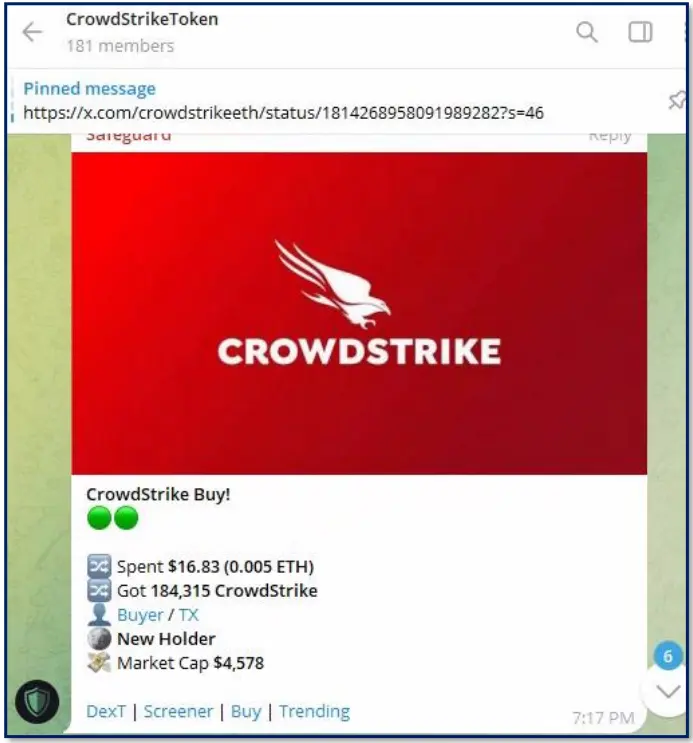
| crowdstriketoken.com | Suspicious Crypto Scam | |
| crowdstuck.org | ||
| crowdstrikebluescreen.com | Possibly Benign – Computer Repair Shop redirection | |
| clownstrike.co.uk | Meme Site | |
| whatiscrowdstrike.com | Benign Blog | |
| crowdstrikeoutage.info | Benign Blog – Offers supposed helpful info. Caution is advised | |
| fix-crowrdstrike-bsod.com | Owned by LinkedIn User – | |
| crowdstrike-bsod.com | Workaround Fix & Donation | |
| clownstrike.co | Redirects to e-commerce site | |
| crowdstrikedown.site | Redirects to e-commerce site | |
| crowdstrikefix.com | Parked | |
| crowdstrikedoomsday.com | Parked – for sale | |
| crowdstrikeupdate.com | Parked | |
| crowdstrike-helpdesk.com | Parked (suspicious intent) | |
| microsoftcrowdstrike.com | Parked (suspicious intent) | |
| crowdstrike0day.com | Parked | |
| crowdstuck.org |
Cyberint recommends the following:
How to check if your version of CrowdStrike is affected by the Blue Screen of Death issue:
Note: CrowdStrike recommended the following workaround, however, several users reported that the workaround did not work for them. It is highly recommended to take precautions when implementing workarounds.
Possible workaround:
We want to assure you that our systems and services are not affected by this issue. Our team is continuously monitoring the situation to ensure that our operations remain uninterrupted. Your satisfaction and security are our top priorities. While we are not impacted by the current issue, we are closely monitoring the status of our customers to provide any necessary support. If you have any concerns or need assistance, please do not hesitate to reach out to our support team.
Cyberint, the Impactful Intelligence company, reduces risk by helping organizations detect and mitigate external cyber threats before they have an adverse impact. The Cyberint Argos platform’s patented technology provides superior visibility through continuous discovery of the evolving attack surface, combined with the automated collection and analysis of vast quantities of intelligence from across the open, deep and dark web. A team of global military-grade cybersecurity experts work alongside customers to rapidly detect, investigate, and disrupt relevant threats – before they have the chance to develop into major incidents. Global customers, including Fortune 500 leaders across all major market verticals, rely on Cyberint to protect themselves from an array of external risks, including vulnerabilities, misconfigurations, phishing, impersonation attacks, malware infections, exposed credentials, data leaks, fraud, and 3rd party risks.
Fill in your business email to start


