Self-Published Author and a digital marketing specialist. Read his thought leadership articles for information on the Attack Surface and Threat Intelligence.
The typical Security Operations Center (SOC) faces a wide variety of responsibilities. In addition to monitoring internal systems for signs of threats and breaches, modern SOCs are tasked with managing external risks through practices such as:
Each of these practices addresses different types of risks, and it would be wrong to say that any one practice is fundamentally more important than the others.
However, there is one practice – Dark Web monitoring – that can boost all of the rest. When you have effective Dark Web monitoring in place, you’re also in a strong position to detect phishing, prevent social media impersonation and manage third-party risks. By the same token, failure to monitor the Dark Web effectively hampers the SOC’s ability to address other priorities.
“Tracking everything on the Dark Web is mission critical,” as Dark Reading notes.
Here’s how Dark Web monitoring and Dark Web scans help businesses manage all types of external risks, not just those that are directly linked to the Dark Web.

Brand impersonation websites – meaning websites that appear to be owned by a legitimate company, but are actually controlled by threat actors – have become a pervasive attack vector. They’re particularly risky for businesses in industries like retail and finance, where attackers can use impersonated websites to solicit payments directly from customers, as well as to collect customer data that they then use to access funds through legitimate systems.
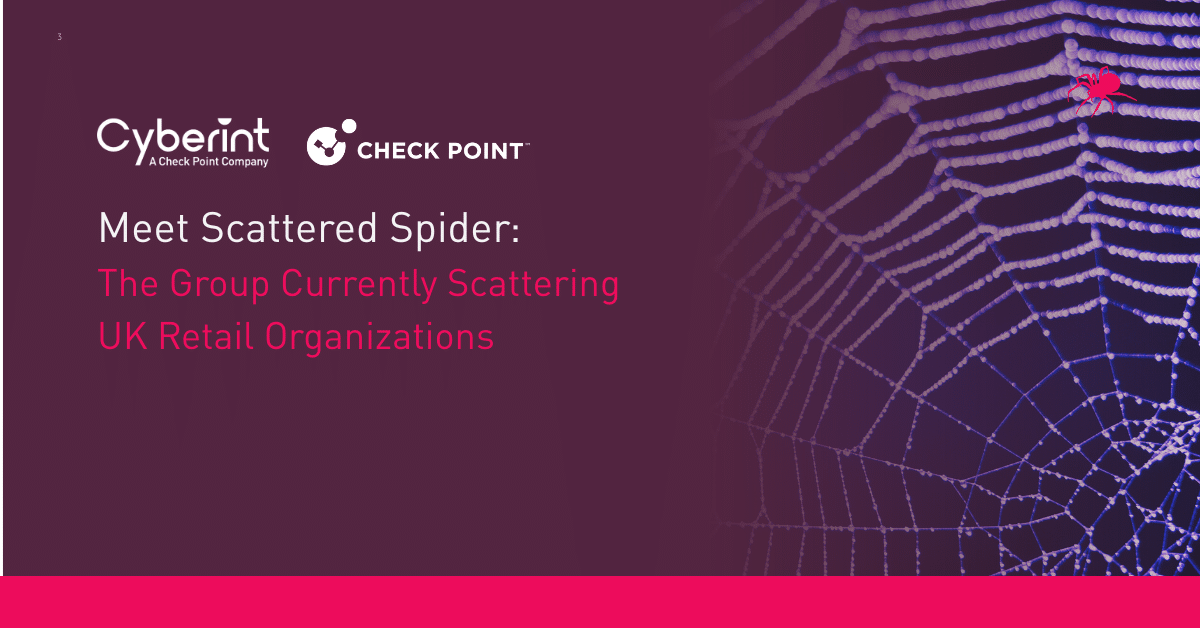
And today, creating impersonation websites is easier than ever, thanks to phishing kits – which essentially provide turnkey solutions for launching websites that copy a business’s brand using a lookalike URL.
However, because phishing kits are typically bought and sold through the Dark Web, Dark Web monitoring offers an effective means of detecting website impersonation attempts. This allows cyber security teams to handle this type of risk proactively by blocking it before the impersonated website is even set up – a faster and more effective approach than taking down the phishing content after the fact.
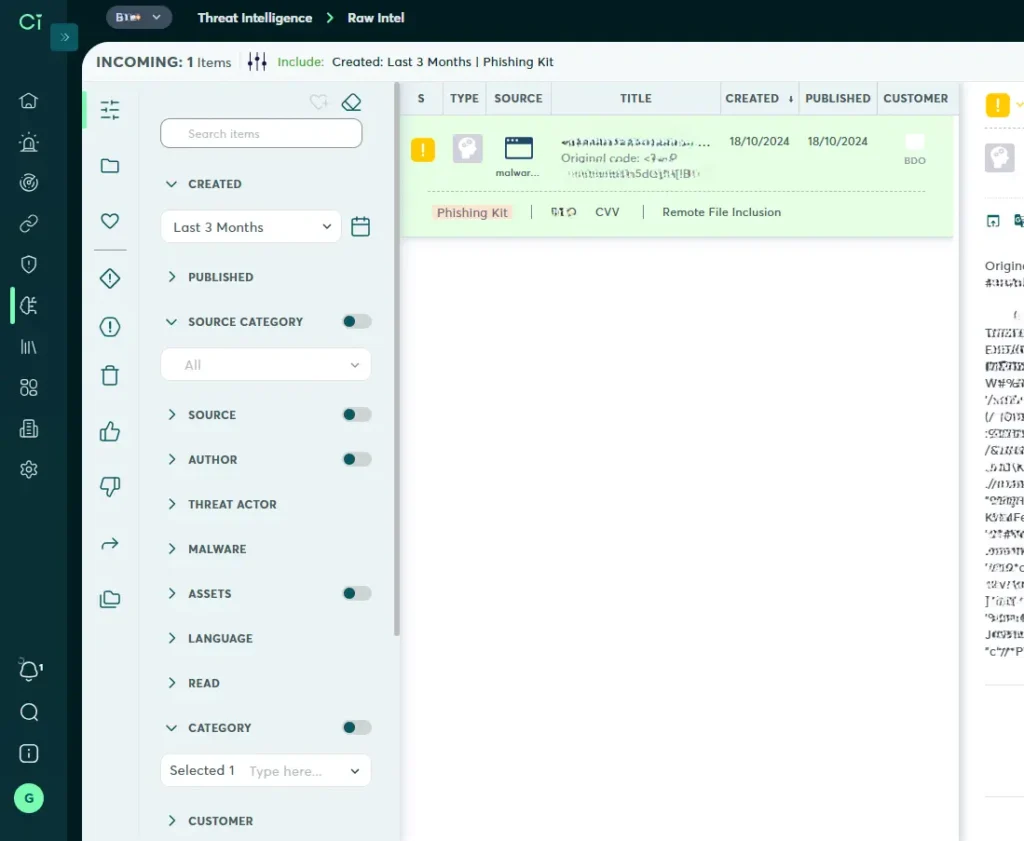
In a similar vein, monitoring for Dark Web phishing activity can help to identify instances where threat actors target corporate executives. When these people are phished, their Personal identifiable information (PII), such as credit card information and social security numbers, is often made available in Dark Web marketplaces. Here again, monitoring for this type of data allows businesses to get ahead of the risk and take action before maximum harm occurs.
Dark Web monitoring can help to map and defend a business’s attack surface in several key ways.
Ideally, SOCs are able to determine when machines owned by their organization have been compromised by malware by monitoring the devices and networks for anomalous activity. But this doesn’t always work (if it did, malware attacks would always be detected quickly).
However, by monitoring the Dark Web for discussions about compromised machines owned by a specific organization, security teams gain another means of identifying breaches. In this way, Dark Web monitoring helps them to catch attacks they might otherwise miss and react to them as quickly as possible, before the malware spreads further within their IT estate.
Similarly, monitoring the Dark Web for leaked credentials associated with a company is an effective way of determining when a breach has occurred. Dark Web leaks of access credentials are one of the most common methods of threat actors, and they account for 86 percent of breaches, according to the 2024 Verizon Data Breach Investigations Report.
Plus, given that it takes an average of 194 days for organizations to detect a breach, SOCs clearly need all the help they can get to catch leaked credential incidents. “There’s never a good time to experience a data breach, but reducing the mean time to detect a breach can make all the difference in how effectively your organization recovers from one,” as Verizon notes.
Monitoring the Dark Web can provide early visibility into leaked credential risks, allowing businesses to identify and respond to the issue rapidly.
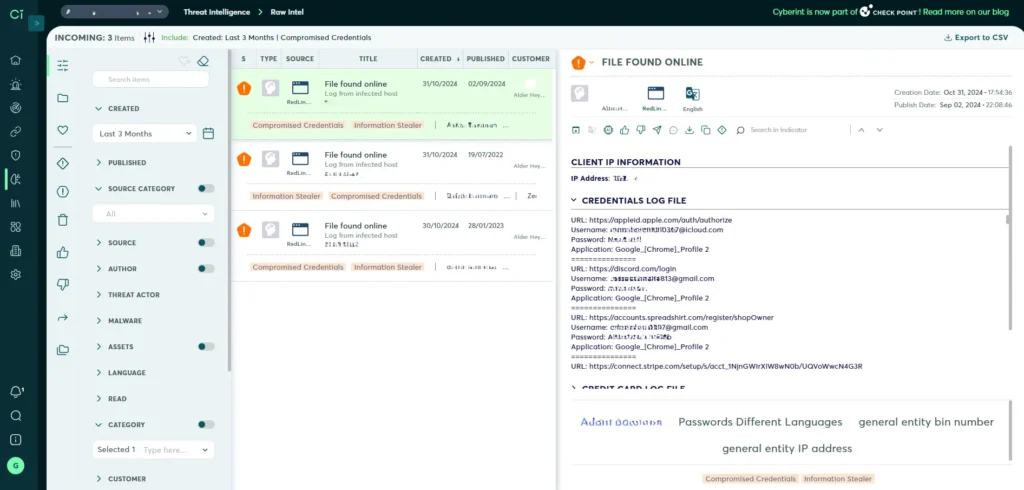
In addition to stealing credentials, threat actors sometimes steal a company’s source code, which can help attackers conduct breaches against both the business that produced the code and any customers that use it, then make it available on the Dark Web. This is another type of resource that Dark Web monitoring can detect, helping to enable proactive protection of assets.
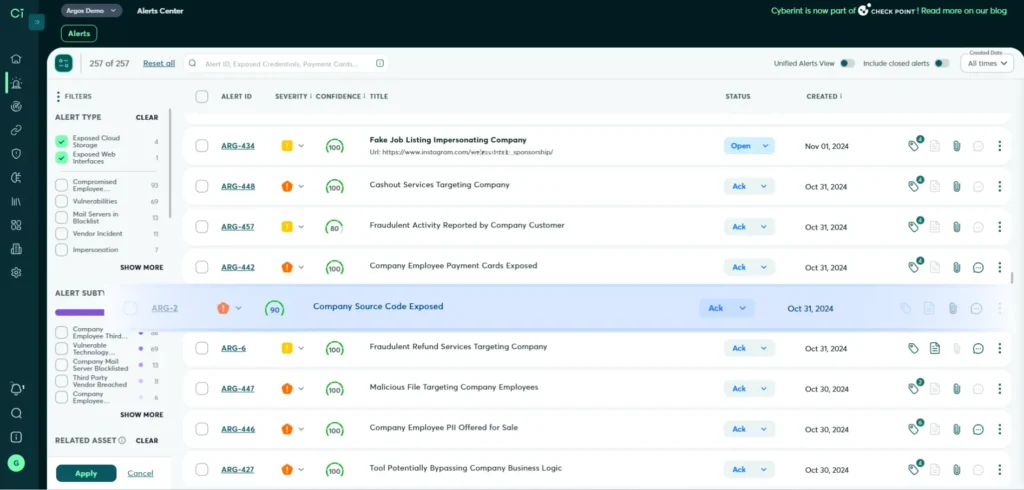
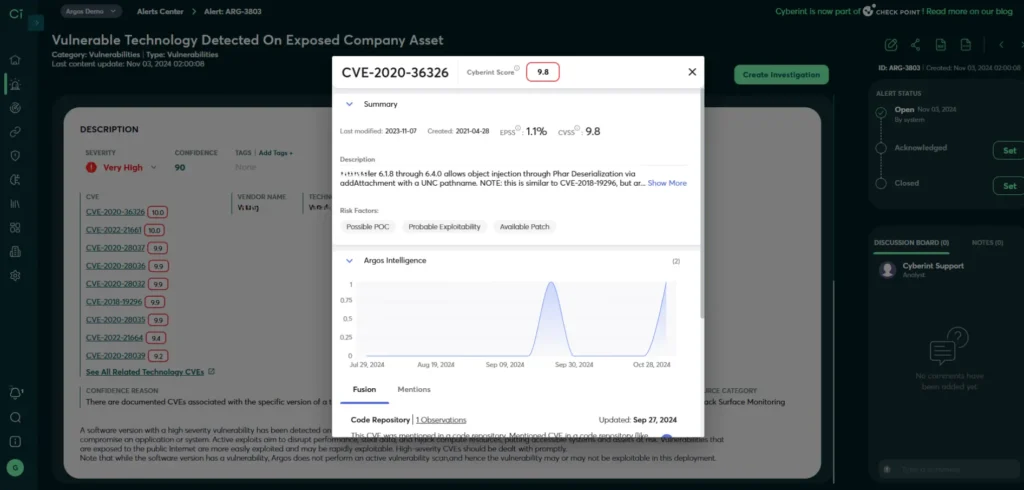
Attack surfaces are complex, and the threats against them are numerous – both of which are factors that can make it challenging to know which risks to prioritize in the context of attack surface management. But by monitoring the Dark Web to determine which threats and threat actor tactics, techniques and procedures (TTP) are trending, security teams can make informed risk prioritization decisions.
Indeed, this is why we built the Cyberint CVE Intel module, which correlates vulnerabilities with businesses’ digital assets to help security teams focus on the most relevant threats based on their unique attack surface.
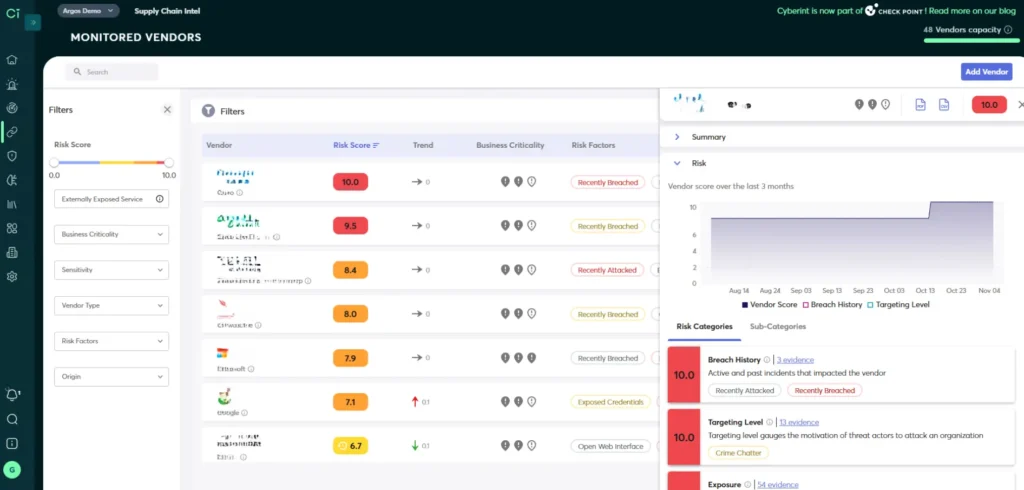
When it comes to monitoring your software supply chain, too, Dark Web monitoring is a powerful technique. Keeping tabs on Dark Web activity helps to provide information into which vendors or partners threat actors have compromised, as well as chatter regarding which businesses attackers are targeting.
With this insight, businesses can determine whether any of their suppliers are at risk, even if the suppliers themselves are not yet aware of an attack.
Again, it’s important to note that Dark Web monitoring alone won’t guarantee protection against risks like phishing attacks or leaked credentials. But it does provide additional threat visibility and context that would not be available through the other monitoring techniques that SOCs typically deploy.
This is why external risk management solutions like Check Point’s Infinity External Risk Management (previously known as Cyberint) have become a linchpin of modern brand protection and risk management.
Schedule a demo to see for yourself just how our enhanced Dark Web monitoring solution can supercharge your SOC.

©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start