


The National Institute of Standards and Technology (NIST) has released version 2.0 of its Cyber security Framework (CSF), significantly elevating cyber security guidelines. This update brings in major changes that will affect several actors like Chief Information Security Officers (CISOs), Managed Security Service Providers (MSSPs), and individual users, among others.
It’s essential to get familiar with and understand these updates, especially now, when many organizations are struggling with tight cyber security budgets, a worldwide shortage of cyber security experts, and in many industries and countries limited regulatory requirements pushing them to invest in cyber security.
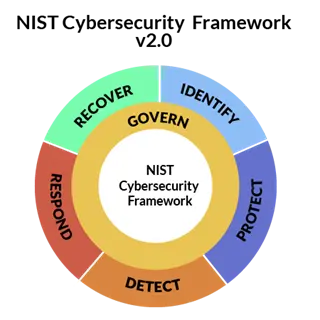
For CISOs, adding the “Govern” function highlights the need to bring cyber security into a more comprehensive enterprise risk management conversation. This shift will inevitably make CISOs work closely with executive leadership and board members to align cyber security goals with broader organizational objectives. It emphasizes the importance of establishing structures and policies that guide cyber security efforts across the entire organization.
With the framework’s expanded scope, CISO’s in various sectors are now encouraged to view NIST 2.0 as a foundational part of their cyber security programs, not only from a Best-Practice standpoint, but also as a necessity to continue making business and to maintain its edge within an even more competitive environment.
Plus, the increased focus on supply chain risk management means CISOs will need to keep a closer eye on the cyber security practices of their vendors and partners, extending the spillovers that we saw with the initial NIST CSF.
– Davis Hake, Co-Founder of Resilience.
Managed Security Service Providers (MSSPs), play a crucial role in delivering cyber security services to organizations, especially those without in-house expertise. With NIST 2.0’s broader applicability, MSSPs can now standardize their service offerings across a range of industries, using a consistent framework to assess and manage cyber security risks.
Even though NIST 1.0 provided a similar opportunity to MSSPs, the inclusion of practical examples in the 2.0 version helps MSSPs turn high-level guidelines into actionable strategies for their clients. And with the spotlight on supply chain risk management, MSSPs have a new opportunity to offer specialized services focused on assessing and reducing risks tied to third-party vendors, expediting both the transformation process and provide day to day execution of these activities.
– David Primor, CEO of Cynomi.
Everyday users’ biggest asset is their data, which is often managed by companies constantly in the eye of malicious agents. While NIST CSF 2.0 primarily targets organizations, individual users also stand to benefit indirectly, as more organizations adopt this updated framework, the overall cyber security landscape improves.
This, in turn enhances the protection of personal data and reduces exposure to cyber threats. Additionally, the framework’s focus on governance and risk management could lead to more user-centered security policies and practices, promoting cyber security awareness among employees and end-use
NIST CSF 2.0 tackles several ongoing challenges in cyber security, such as limited budgets, a worldwide lack of cyber security experts, and unregulated industries. By offering a flexible and comprehensive framework, NIST will help organizations prioritize cyber security spending, even with limited resources, it provides visibility to allocate resources where they are most critical. Also, the framework’s scalability allows organizations to implement controls that match their size and risk level, making it accessible to those with smaller budgets.
In a world where cyber security experts don’t grow on trees, MSSPs have become increasingly crucial for organizations struggling to protect their digital assets. They provide dedicated teams equipped with advanced tools and knowledge to manage and monitor security environments. The fact that NIST 2.0 applies to all industries empowers MSSPs to leverage their expertise into virtually every company, narrowing the gap between the lack of expertise and the fast-paced evolution of malicious actors.
Furthermore, NIST CSF 2.0 becomes a sort of common language for all companies regardless of industries and specific regulations, helping them to engage more efficiently within the broader supply chain. This universally applicable framework enables them to work together in a more resourceful way, reduce extra steps and build trust within both partners and customers. This shared language fosters a more transparent risk management approach between companies while still complying with their unique regulatory obligations. This makes NIST 2.0 a critical player in building a more resilient, united and stronger front against threats, supporting a collective cyber security effort across industries.
In summary, NIST CSF 2.0 provides a solid roadmap for building cyber security resilience, focusing on governance, supply chain risk management and practical guidance. But a key component for navigating these challenges effectively is integrating string threat intelligence into cyber security practices. Threat Intelligence offers real-time insights into emerging threats, enabling organizations to stay proactive and fine-tune their defenses.
By onboarding attack surface management organizations can directly tackle the Identify and the protect functions. By integrating Threat intelligence, companies can better prioritize risks, allocate resources wisely, and embrace a preemptive cyber security strategy in line with NIST 2.0 principles
Ultimately, organizations adopting NIST CSF 2.0 are better positioned to protect consumer data by aligning their cyber security strategies with global standards and proactively managing risks, which will translate into a more secure environment for companies, costumers, and everyday users.
Cyberint, now a Check Point company, reduces risk by helping organizations detect and mitigate external cyber threats before they have an adverse impact. The Check Point External Risk Management solution provides superior visibility through continuous discovery of the evolving attack surface, combined with the automated collection and analysis of vast quantities of intelligence from across the open, deep and dark web.
A team of global military-grade cybersecurity experts work alongside customers to rapidly detect, investigate, and disrupt relevant threats – before they have the chance to develop into major incidents. Global customers, including Fortune 500 leaders across all major market verticals, rely on Check Point External Risk Management to protect themselves from an array of external risks, including vulnerabilities,
misconfigurations, phishing, impersonation attacks, malware infections, exposed credentials, data leaks, fraud, and 3rd party risks.

©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


