


The Cyberint (now a Check Point Company) Philippine Threat Landscape 2024-2025 report unravels the evolving cyber threats and scam operations targeting organizations in the Philippines—mainly within the Government, Education, Financial, and Telecommunications sectors.
Data from Cyberint sources indicates a surge in cyber threats such as malware, social engineering, and system exploitations. This increase is driven by political and sociological ideologies, global conflicts, technological shifts, and local scam operations, particularly involving Philippine hacktivists.
In 2024, malware infections, especially InfoStealers, continue to rise, exposing sensitive information like confidential files and credentials. Philippine-based threat actors and scam operators use advanced techniques to conduct phishing campaigns, impersonating local organizations —from government to telecommunication sectors—to target financial industry customers.
Meanwhile, DDoS attacks have become a trend in the Philippines. It began during the “April Lulz” event, a campaign celebrated by local threat actors annually, where they actively conduct cyber attacks targeting local entities for the whole month of April. Amidst the numerous cyber attacks, it’s encouraging to note that we reported a significant decline in ransomware attacks targeting the Philippines.

Cyberint’s Philippine Threat Landscape Report 2024-2025 employs a comprehensive intelligence strategy that combines both proprietary and public data sources. Our intelligence is gathered from Cyberint and Check Point sources, that track a variety of threat vectors using modules like Attack Surface Management, Darkweb Threat Intelligence, Supply Chain Intelligence, Malware Intelligence, Phishing Detection, Social Media Monitoring, and more.
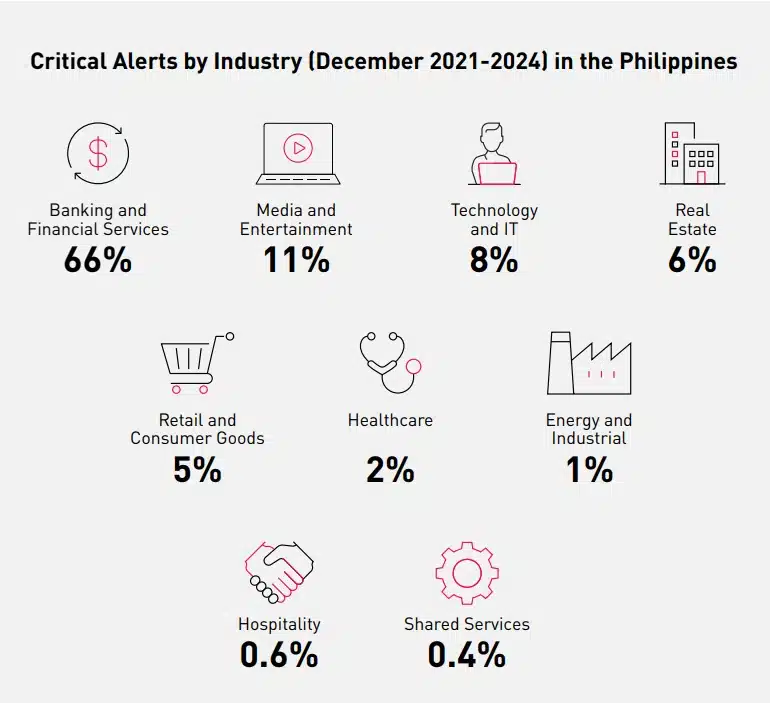
Cyberint, now a Check Point Company delivers essential alerts and indicators that shape our analysis, enabling us to present an intelligence-driven overview of the cyber security threat landscape in the Philippines. The information in this report is based on a sample of around 127,000 intelligence alerts collected from December 1, 2021, to December 1, 2024, from around 15 companies across various industries in the Philippines.
We also utilize open-source intelligence (OSINT) by incorporating threat feeds, news articles, and research publications from cyber security professionals and regulatory authorities.
Social Engineering remains a highly effective attack vector in the Philippine threat landscape. Local threat actors continue to operate Phishing campaigns, where some of them leverage new techniques to lure more users into falling into their fraudulent schemes.
Malware remains the top cyber threat in the Philippine threat landscape, considering its broad category, including trojans, worms, spyware, and viruses. Based on Cyberint sources, we have observed a continuous trend in Malware-as-a-Service (MaaS) being offered in the dark web, which allows even some inept threat actors to deploy sophisticated malware.
Impersonations are everywhere! Threat actors nowadays can easily impersonate organizations, including high-ranking officials, through social media platforms. By effectively impersonating a known entity, threat actors can initiate a scam operation targeting company employees and customers.
Newly discovered local threat actors are now conducting Distributed Denial-of-Service (DDoS) attacks, mainly targeting financial, government, media, and educational institutions. Some are already offering DDoS tools in the underground, making it easier, even for unskilled threat actors, to conduct their own DDoS campaign.
Supply Chain attacks continue to increase in 2024. As Philippine-based organizations leverage new technologies and services, risks for data exposure due to supply chain incidents will rise.
The race between vulnerabilities and threat actors has been constant in 2024 and will persist in 2025. With more innovations every year, we can expect a continuous curve for vulnerabilities, thus giving more exploitation vectors for threat actors to gain a foothold in targeted organizations.
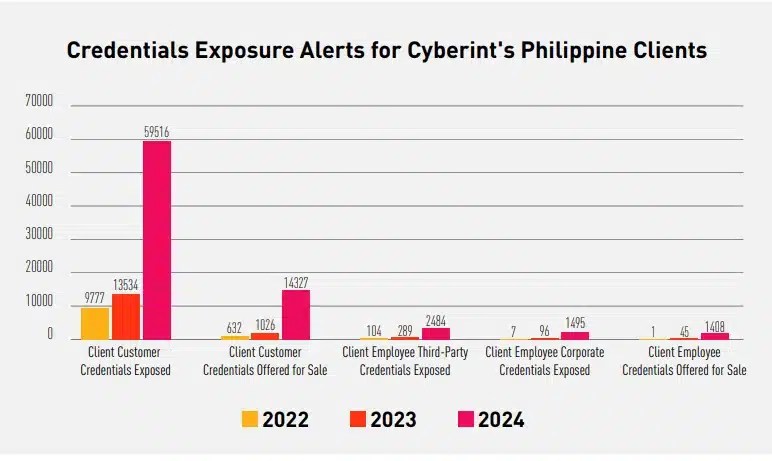
As we continue to enhance our sources and services, more malware infections for our clients’ employee machines have been discovered. The majority of these malware infections came from the personal devices of clients’ employees, which were utilized for work-related activities.
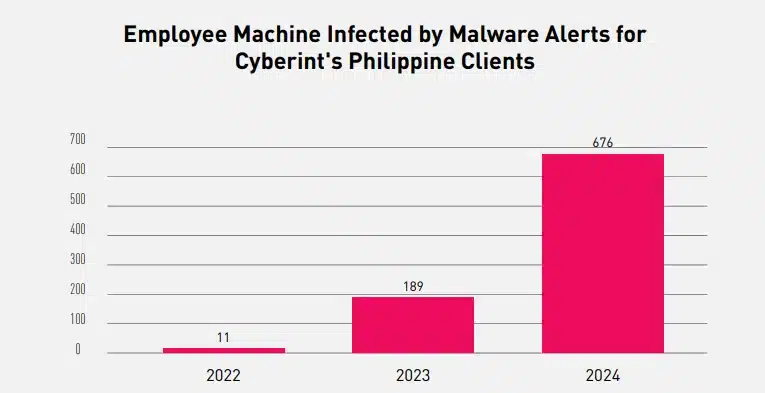
In the Philippines, Information Stealers (a.k.a. Infostealers), a type of malware that can exfiltrate sensitive information (i.e., browser credentials, cookies, cache, crypto wallets, desktop files, etc.), became the gateway for threat actors to easily gain unauthorized access to insecure portals, resulting in exposure of sensitive information. Nowadays, Infostealer logs are scattered across the dark web, making it easier for threat actors to source exposed credentials of their targeted entity.
Infostealers became more effective against Philippine-based organizations’ employees during and after the COVID-19 pandemic due to the adjustments made by the Philippine government. In contrast, most local companies are now allowing work-from-home setups.
Based on Cyberint (now a Check Point Company) sources, many Filipinos who work from home are more susceptible to violating an organization’s information security policies. We have observed a massive number of Filipino employees who use their personal devices (i.e., desktops, laptops, etc.) to access work-related portals, thus amplifying the risks of having credentials exposure whenever these personal devices get infected by Infostealers.
Ransomware continues to be one of the most critical threats, not only in the Philippines but around the globe. However, we have observed a decrease in ransomware attacks targeting the Philippines in 2024 compared to 2023.
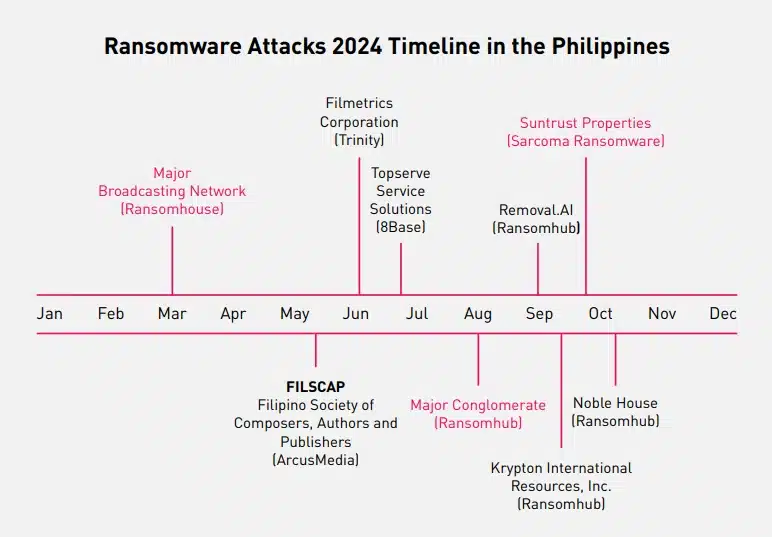
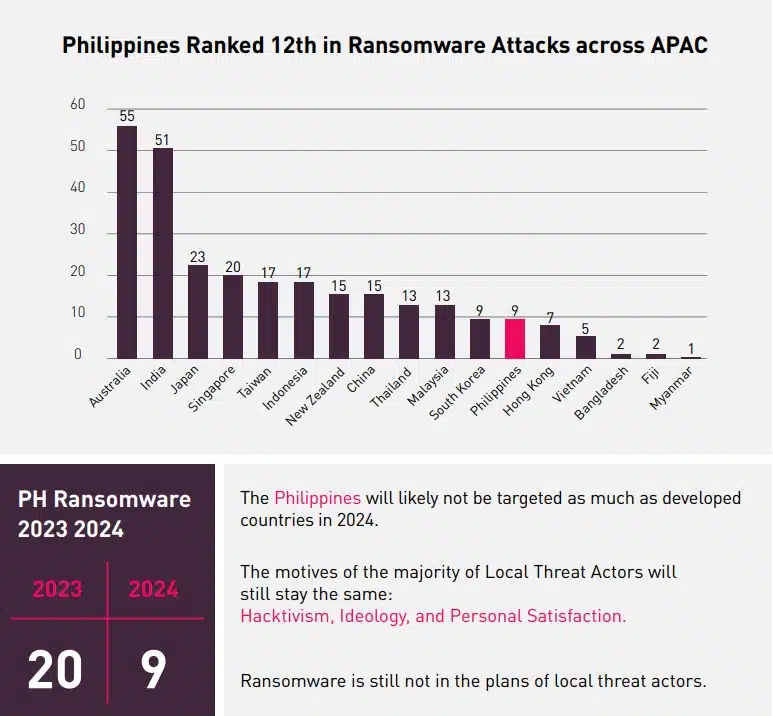
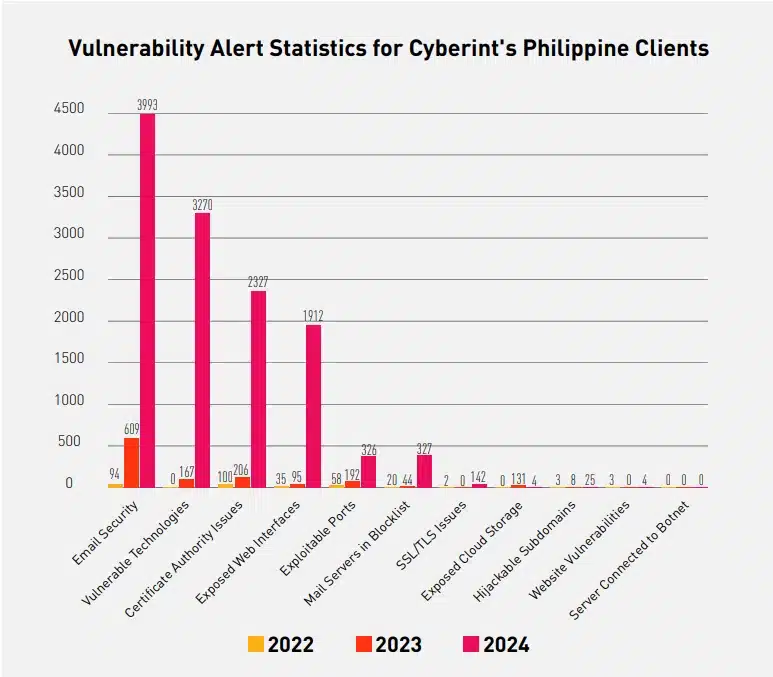
Cyberint observed a rise in most vulnerability exposure items for our Philippine clients in 2024 compared to past years. Several factors for this increase include new clients, more Attack Surface Management assets (i.e., domains, subdomains, and IP addresses)—added or discovered for monitoring—for each client, new vulnerabilities affecting our clients’ assets and technologies, and improvements in Cyberint’s Attack Surface Monitoring module for a better external risk management service.

In terms of social engineering techniques, phishing operations are rampant in the Philippines, mainly targeting the financial sector. In 2024, a decrease in phishing alerts targeting Cyberint’s clients was observed compared to 2023. Cyberint, now a Check Point Company believes that this decline in typical local Phishing operations is due to new techniques being explored by threat actors in preparation for 2025. In contrast, we have observed an increase in social engineering campaigns leveraging social media advertisements (ads) and impersonating pages.
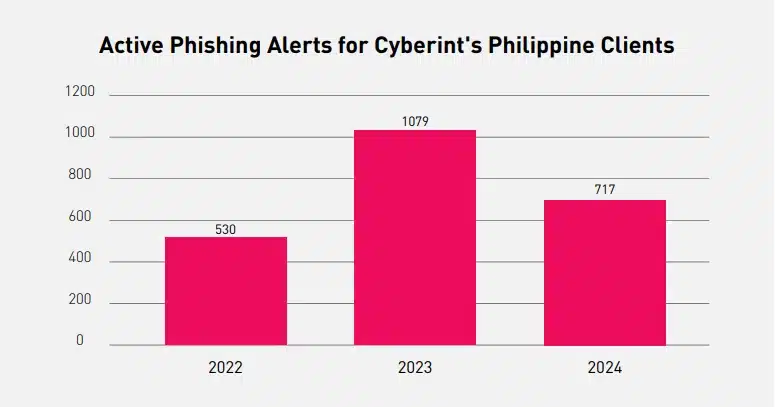
Phishing operations in the Philippines have evolved significantly, with a dramatic surge in both sophistication and frequency. Over the past few years, local threat actors have been looking for new ways to conduct phishing operations.
They started with the traditional phishing techniques and shifted to a more sophisticated one known as True Login Phishing, where they automate the exfiltration of credentials and OTPs by abusing insecure APIs or any vulnerabilities from an online service, such as online or mobile banking applications.
Cyber criminals have become more adept at exploiting digital communication channels, often tricking individuals into providing sensitive information through fake websites, promotions, or app downloads.
Despite efforts like the SIM Card Registration Law, which aims to trace scammers more effectively, these threats persist, highlighting the need for enhanced cyber security measures and public awareness.
In 2024, Smishing—Phishing via SMS—took the spotlight in the Philippine threat landscape. During the 1st quarter of the year, a Smishing campaign began operating. This campaign initially impersonated government and logistics organizations, such as the Land Transportation Office (LTO), Social Security System (SSS), PHLPost, and more.
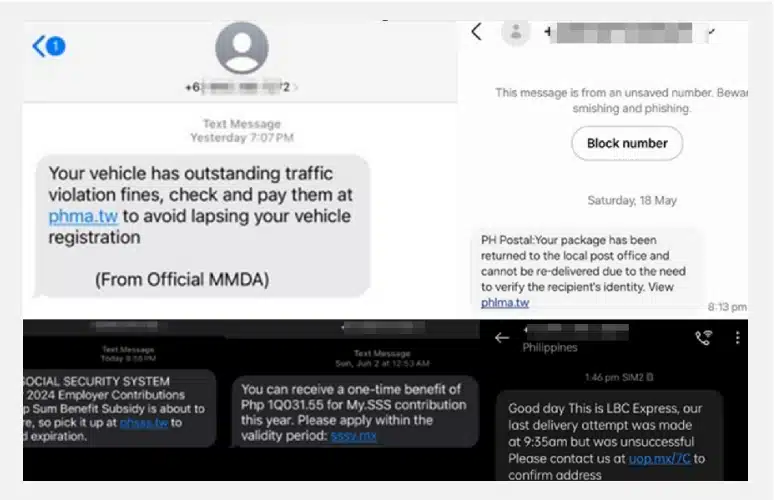
Over the past months, multiple local scam hubs were consecutively infiltrated by the National Bureau of Investigation (NBI), resulting in the arrest of several Chinese and Filipino nationals who mainly conduct scam operations, including Phishing targeting local banks’ customers.

As per Cyberint, now a Check Point Company’s observation, these successive apprehensions have led to an abrupt interruption of the smishing campaign around September 2024. However, in October 2024, the campaign returned with a new theme—this time impersonating telecommunications companies, luring the users into believing a fake deactivation of SIM card notification and tricking users into reprocessing their SIM card registration by clicking the Phishing link.
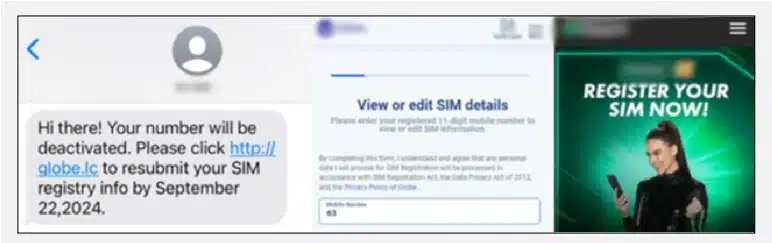
The main goal of this smishing campaign is to steal the online banking credentials of victims by
impersonating online banking pages as their final landing pages.
The latest local phishing operations leverage techniques that threat actors are utilizing in targeting well-developed countries, like the United States of America and the European region.
This technique is known as Device and Geo Filtering, which recent threat actors apply to hosted phishing domains to ensure that they will only be accessible when visited from a Philippine-based IP address using a mobile device. Thus, enhancing their defense mechanism to evade detection through sandbox and other security controls.
A device for intercepting mobile phone traffic leveraged in well-developed countries like the United States—known as IMSI (International Mobile Subscriber Identity) Catcher, also known as Cell-Site Simulators or Stingrays—is being leveraged by Smishing operators targeting Filipinos in 2024.
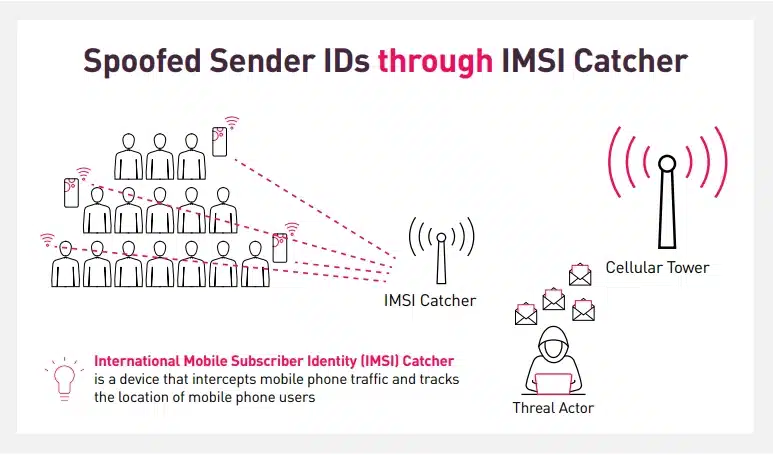
The local Smishing campaign leveraging IMSI-Catcher devices was highly observed during the November 1 and 2 holidays—All Saints and Souls’ Day (a.k.a. Undas). During these busy days when Filipinos visit cemeteries for the holidays, threat actors have seen a gateway to conduct Smishing attacks.
Several people reportedly received malicious SMS text messages impersonating local digital wallets. Based on the text messages received by random individuals, the Sender IDs used by the Smishing operators are the official Sender IDs used by the digital wallets for their SMS notifications.
Based on how the Smishing attacks are being delivered, security professionals, including Cyberint, are highly confident that these were conducted using IMSI-Catchers after correlating all the evidence and data from our sources.
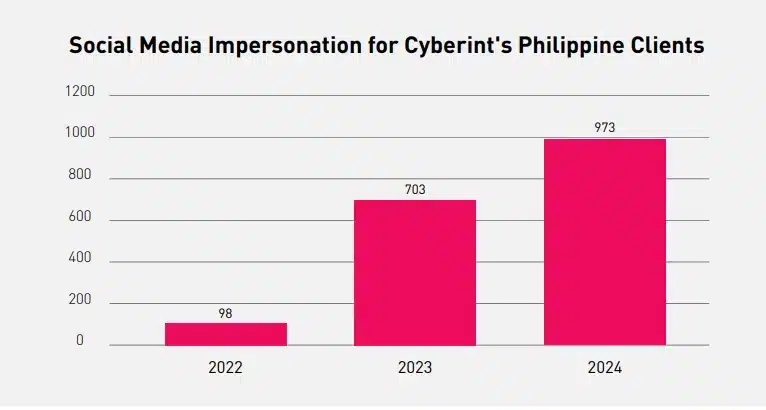
Cyberint observed a rising curve in terms of social media impersonations based on alerts raised to our Philippine clients.
Scam operators choose to build up fake social media profiles and conduct scam operations targeting gullible people by offering fake promotions and services. Fraudulent content associated with these fake profiles or pages is being distributed across different social media platforms through posting and advertisements (ads).
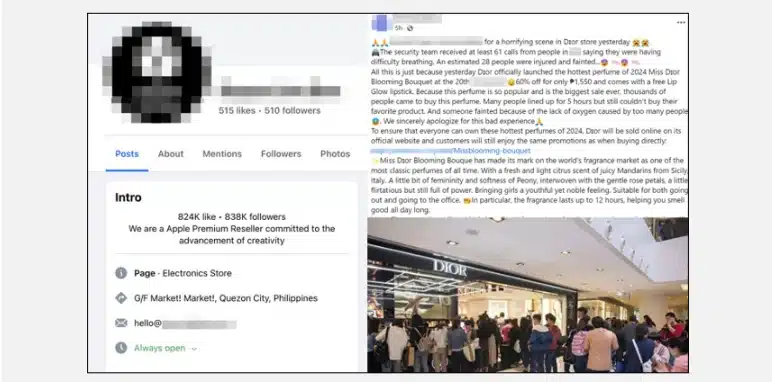
One of the significant highlights of 2024 is data leak incidents. Several data breach incidents have occurred in the Philippines, and they have been claimed by various local and global threat actors and groups, targeting several sectors, such as government, financial, retail, healthcare, education, and media.
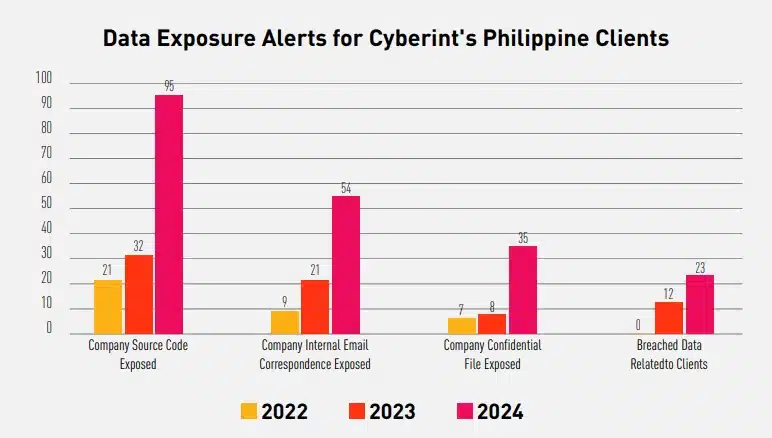
A rising curve in terms of data exposure for Cyberint, now a Check Point Company’s clients has been observed over the past few years.
With the increase in Company Source Code exposure—mainly related to APIs (i.e., UAT, tokens, secrets, and requests), internal projects, and more—chances for threat actors to abuse these source codes for fraudulent activities will also increase.
Other exposed data, such as internal email correspondence and confidential files, can be utilized by threat actors to effectively plan their next steps and targets.
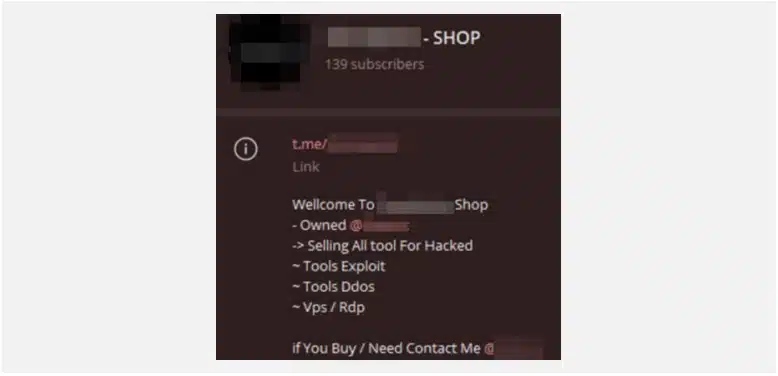
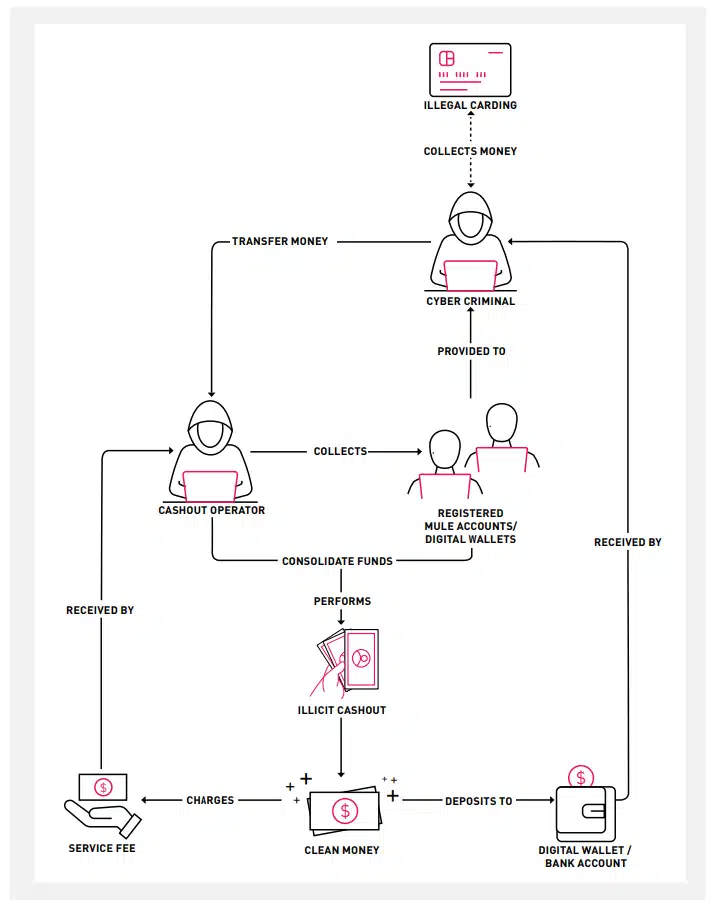
As more technologies and services rise, threat actors ensure that they are catching up with these innovations. This has led to an increase in attackware being sold on the dark web.
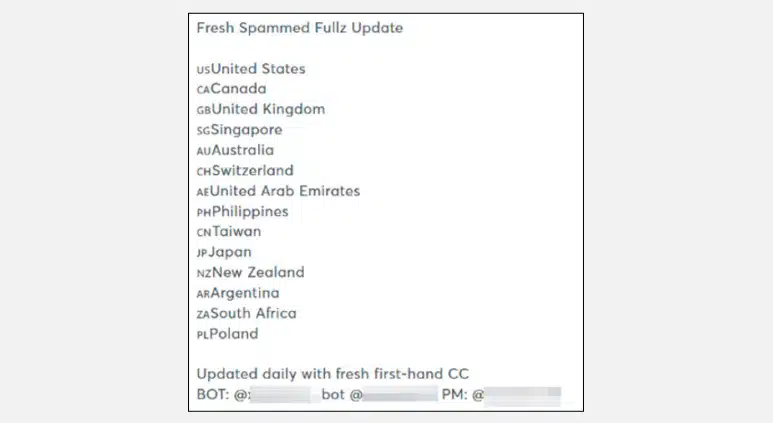
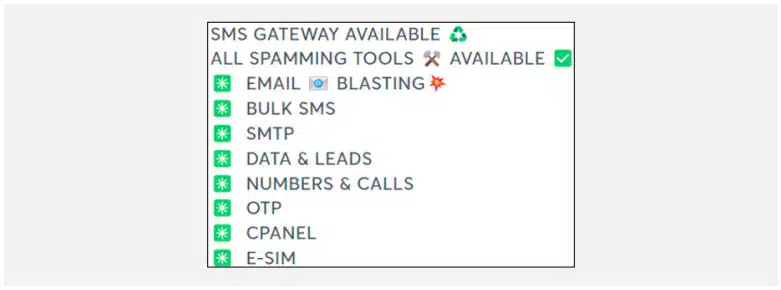
Cyberint, now a Check Point Company continuously monitors underground marketplaces, which offer several attackware and illicit services that can be used to conduct nefarious activities. In 2024, Cyberint observed a 100% increase in Telegram’s underground marketplace activities involving thePhilippines compared to 2023.
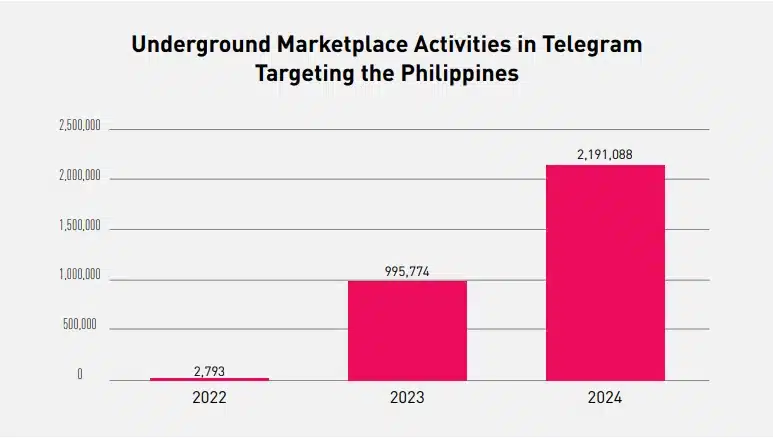
Some of the common items/services being offered in the underground are:
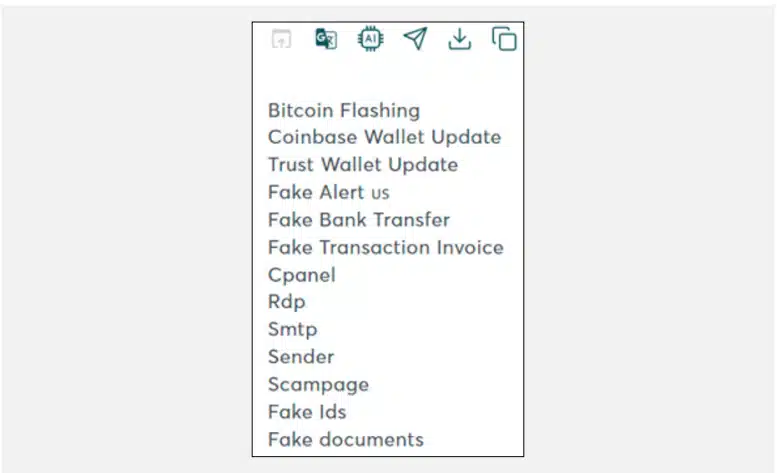
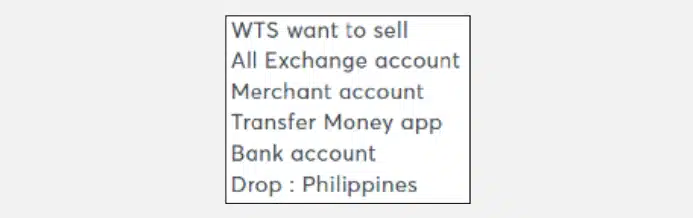
With Cyberint, now a Check Point Company’s latest technology, Supply Chain Intelligence, we were able to raise eight (8) Third-Party Vendor Breach alerts to our Philippine clients in 2024 within a few months, thus automatically notifying them based on the risk criticality and breaches circulating from our sources relating to any of their vendors configured within their Cyberint environments
As we approach 2025, the cyber threat landscape is set to become more intricate due to rapid technological advancements, changes in work environments, and geopolitical tensions (i.e., tensions between the Philippines and China regarding the South China Sea). The following key threats are anticipated to dominate the cyber security space in 2025, necessitating proactive planning and strategic responses from organizations across various industries.
Phishing attacks have long been a favored method for cyber criminals, but with the advent of Artificial Intelligence (AI), these attacks are set to become much more advanced. Threat actors will leverage AI to craft highly personalized phishing emails, texts, or social media messages tailored to individual targets by analyzing publicly available data. These AI-driven phishing campaigns will be challenging to detect due to their human-like language, dynamic content creation, and ability to evade traditional filters.
Aside from AI, threat actors will highly likely enhance their phishing operations by continuing the use of IMSI-Catchers to distribute smishing messages with spoofed Sender IDs, bypassing any validations from official telecommunication towers locally.
The rise in phishing attacks underscores the importance of robust security practices and the rapid adoption of advanced technologies to protect against these evolving threats. With this advancement in social engineering methodologies, organizations will need to implement advanced AI-based defense mechanisms capable of identifying subtle anomalies in communication patterns to counter this growing threat. Additionally, security awareness training must evolve to help employees recognize these highly convincing phishing attempts.
In line with social engineering techniques, one of the easiest ways to conduct scam operations and fraudulent activities in the Philippines is through Brand Impersonation (a.k.a. Social Media Impersonation). Local scam operators will continue to create fake social media pages, impersonating a well-known brand, entity, or even high-ranking officials. Therefore, organizations should be equipped with brand and VIP monitoring tools to immediately detect fake social media pages or profiles before scam operators begin their operations.
Threat actors will start to leverage AI more, such as Deepfakes, for impersonation attacks, which was already observed in 2024. Deepfakes will highly likely be used to impersonate well-known people in the country and use these for fake advertisements on social media platforms.
Supply chain attacks, where cyber criminals exploit vulnerabilities in third-party vendors or software suppliers, are expected to increase in 2025. As organizations depend more on external vendors for critical operations, this interconnectedness creates a larger attack surface for cyber threats. These attacks can disrupt entire supply chains by exploiting weaknesses in software update mechanisms or third-party cloud infrastructure.
Attackers are likely to use these vulnerabilities to gain lateral access to corporate networks, steal sensitive data, or distribute malware. To mitigate these risks, continuous vendor security assessments, stricter contractual cyber security standards, and real-time monitoring of supply chain activities will be crucial.
As the tensions between the Philippines and China regarding the South China Sea rise, threat actors in the Philippines initiated a campaign known as #OpChina. This campaign will mainly target Chinese-related entities and organizations as part of the local threat actors’ ideology against the rising tensions between both countries. Meanwhile, over the past few months, some Chinese APT groups attempted to bribe some Philippine threat groups to conduct a cooperative attack against the Philippine government, whereas the local threat actors declined these offers.
Cyberint, now a Check Point company, reduces risk by helping organizations detect and mitigate external cyber threats before they have an adverse impact. The Check Point External Risk Management solution provides superior visibility through continuous discovery of the evolving attack surface, combined with the automated collection and analysis of vast quantities of intelligence from across the open, deep and dark web.

©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


