I love to get stuck in and let the creative juices flow. My strengths lie in idea generation, development and execution. Over 5 years experience in B2B cybersecurity. I reign supreme when my imagination and creativity can run wild.
TEAM FEARLESS, also known as 𝙏𝙀𝘼𝙈 𝙁𝙀𝘼𝙍𝙇𝙀𝙎𝙎 🇵🇸, is a hacktivist group active in various cyber operations. Their activities are motivated by political and ideological beliefs, primarily in support of Palestine, and they have notably targeted organizations and government entities associated with Israel.
The group primarily conducts Distributed Denial of Service (DDoS) attacks and has claimed responsibility for disrupting services of various organizations. TEAM FEARLESS also forwards messages from other hacktivist channels, such as NoName057(16), and has shown support for actions related to the conflict in Ukraine.
As of early July, their Telegram channel has 977 members. Over the last two months, the group has been very active, with various attacks, targeted corporations, and announcements shared by the group’s administrators.
TEAM FEARLESS has consistently targeted organizations in specific sectors and regions:
Regions affected by their attacks include:
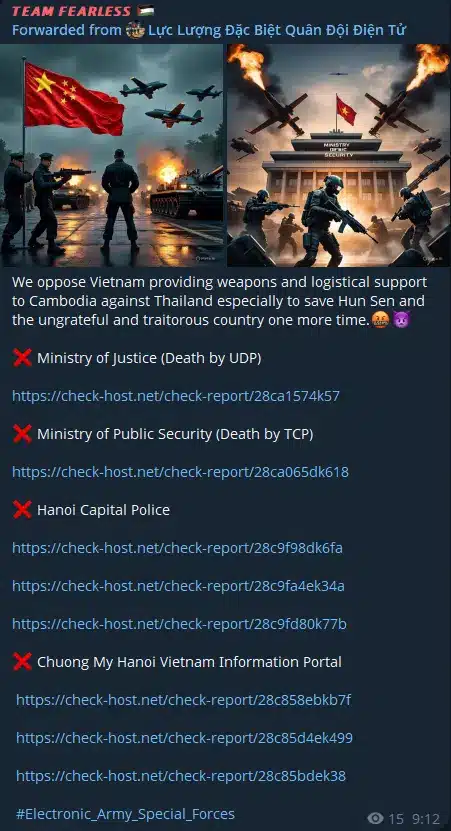
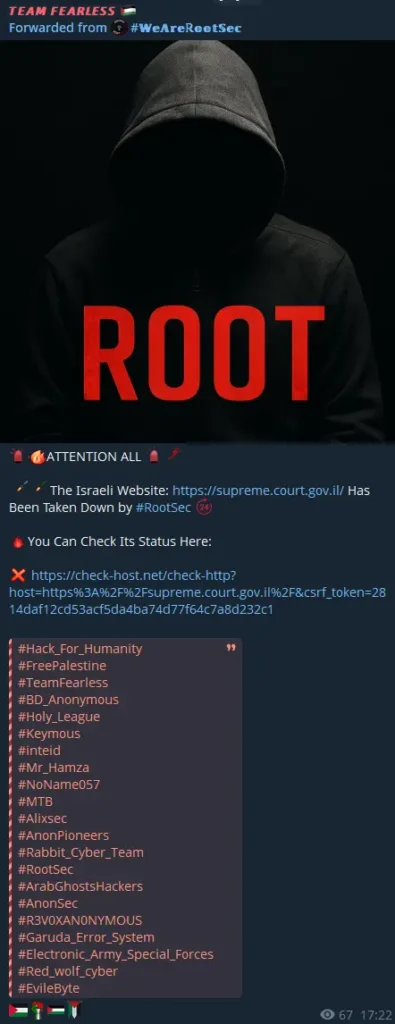
TEAM FEARLESS employs various tactics and techniques, primarily focusing on DDoS attacks to achieve its objectives of disruption and protest. Key attack patterns observed include:
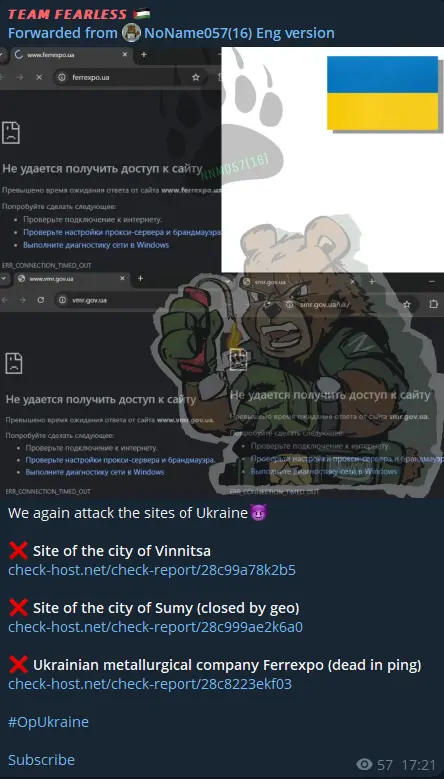
TEAM FEARLESS has actively established alliances with other hacktivist groups, such as CyberVolk and YOGJASEC-XTEAM. These collaborations are a strategic move to enhance their operational capabilities, pooling resources and expertise, and thereby expanding their collective reach and impact.
The existence of such alliances signifies a broader, interconnected ecosystem within the hacktivist community, where groups can leverage each other’s strengths for larger-scale cyber operations. These partnerships are often publicized through their communication channels, which serves to emphasize a united front in their cyber operations, bolstering their perceived strength and deterrent capability.
The group maintains a robust and active presence across various communication platforms, particulaly Telegram. This platform serves as a central hub where they share real-time updates on their ongoing operations, coordinate upcoming attacks with their members and affiliates, and extensively promote their political and ideological beliefs to a wider audience.
They actively utilize specific channels, such as HackNet, for disseminating information and engaging with their followers. Their activity extends beyond Telegram, with a presence on other social media platforms and online forums.
This multi-platform engagement indicates a structured and deliberate approach to recruitment, seeking to attract new members and sympathizers who align with their causes. By leveraging their claimed cyber activities, they foster community engagement and build support for their ideological stance, which is crucial for sustaining their operations and influencing public perception.
Their consistent presence and engagement efforts highlight their focus not only on technical execution but also on maintaining and growing their activist base.
To learn more about how our threat intelligence research helps protect businesses against ransomware and other risks, request a demo.
| Tactic | Technique |
|---|---|
| Reconnaissance | T1593.001 – Social Media |
| Command and Control | T1102.002 – Bidirectional Communication |
| Impact | T1496 – Resource Hijacking |
| Impact | T1498.002 – Reflection Amplification |
| Impact | T1499.001 – OS Exhaustion Flood |
| Impact | T1498 – Network Denial of Service |
Fill in your business email to start