


Seemingly favored by many big game hunter ransomware threat groups, VPN and network infrastructure devices are regularly used as the initial attack vector, especially given that some organizations neglect to include ‘hardware’ appliances within their patch and update regimes.
In this instance, SonicWall, a content and network security vendor, released an urgent security notice [1] on July 14, 2021, advising customers of a critical risk to end-of-life or ‘limited retirement’ SonicWall Secure Mobile Access (SMA) and Secure Remote Access (SRA) products.
Based on recent observations, ransomware threat actors have been actively exploiting a two year old pre-authentication SQL injection (SQLi) vulnerability in these products, identified as CVE-2019-7481, leading to network access without the need to brute-force accounts.
Given SonicWall’s urgent alert, it is likely that many organizations are known to be still using these vulnerable products and, potentially fueled by increased publicity, other ransomware groups or threat actors may seek to identify and exploit vulnerable deployments in their financially motivated ransomware and extortion campaigns.
Whilst only assigned a CVSS score of 7.5, and therefore classified as ‘high’ rather than ‘critical’, the severity of this current situation arises from CVE-2019-7481 being actively exploited in end-of-life products that will are not supported or set to be updated by SonicWall.
Initially reported as only affecting firmware version 9.0.0.3, or earlier, and thought to have been resolved with the release of firmware version 9.0.0.5, recent indications suggest that devices running version 9.0.0.5, and older, remain vulnerable to CVE-2019-7481.
As such, the following end-of-life products are reportedly affected and the continued use of these should be considered a serious security risk:
Additionally, the following ‘limited retirement’ products using firmware version 9.0.0.5 or older remain affected:
In addition to this vulnerability being actively exploited-in-the wild by big game hunter ransomware groups, proof-of-concept code is believed to be available and potentially vulnerable SonicWall devices can likely be easily identified through the use of online tools rather than needing to actively probe target networks.
For example, a basic Shodan search for ‘SonicWall’ returns some 750 thousand results (Figure 1) that, when tuned to include product or version details, could likely identify vulnerable devices.
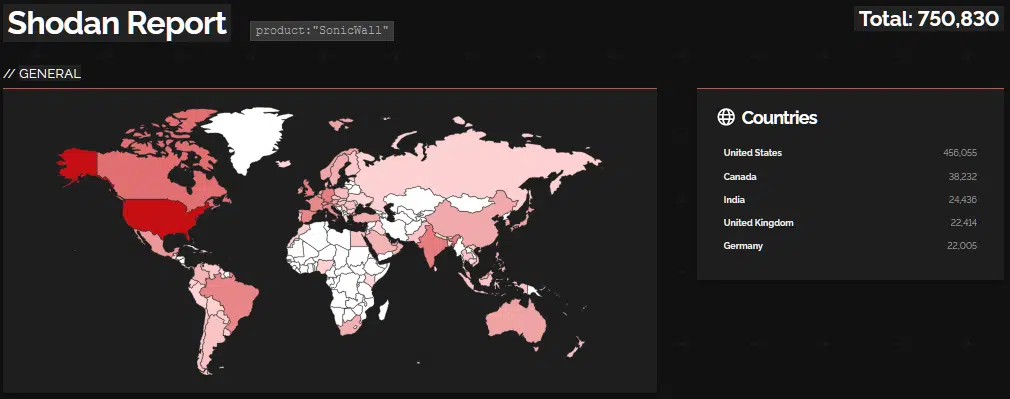
Figure 1 – Basic Shodan search for ‘SonicWall’
Those with potentially vulnerable devices can, after acting upon the recommendations, review their VPN and access logs for indicators of post compromise including:
/cgi-bin/supportInstaller/cgi-bin/supportLoginpython-requests/x.xx.x, where x.xx.x is the library version.Virtual Assist Installing Customer App.©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


