

In the past few months, Cyberint has observed a series of suspicious PDF files mentioning different retail brands, scanned to an anti-virus repository. Seeing as the files were flagged as malicious by the repository, Cyberint’s working assumption is that the retailers were mentioned in order to lure their employees or customers into opening the files. Initial investigation revealed that a hyperlink disguised as a CAPTCHA test at the head of each file redirects victims to several domains, causing a malware payload to be downloaded by the victim’s machine. The following report details Cyberint’s analysis of the malicious file, and recommendations for targeted organizations.
All files consist of the same following components:
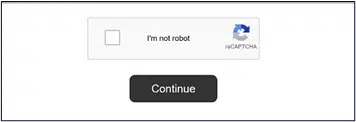
Picture of CAPTCHA test on header: The files begin with an image impersonating a CAPTCHA test. In practice, the picture itself is a hyperlink that redirects the victim to other pages, usually triggering the download of malware to the victim’s machine. This process varies among different victim machines and PDF files.

Long, incoherent paragraph: containing product descriptions that were likely scraped from online marketplaces.
The targeted retailer names usually appear within this text, and it is assumed that the paragraph is used as an SEO (Search Engine Optimization) tool, attracting users to open the file when they are searching for similar content online.
Several links: for other PDF files of a similar format. The linked PDF files are not related to the targeted brand and are hosted on domains which were likely compromised by the Threat Actor for this purpose.

The resemblance between the files, alongside experience from similar cases, suggests that the files are the output of an automated tool. The document displays several characteristics of an automated output, such as blank pages separating the CAPTCHA from the paragraph. Nevertheless, while all the files detected contain the CAPTCHA and the paragraph, not all of them include links to other files. The reason for this is unclear, but it might imply misconfigurations or different versions of the file-generation tool.
As mentioned above, the infection process follows an interaction with a picture of a CAPTCHA test.
Cyberint’s analysis of several samples shows that the next stages of infection vary and depend on different parameters, such as the specific PDF document that initiated the process and the IP address of the victim. In some cases, the CAPTCHA image redirects the victim to a domain that requests additional approval from the victim in order to download the malware, while in other cases the process does not result in a download at all.
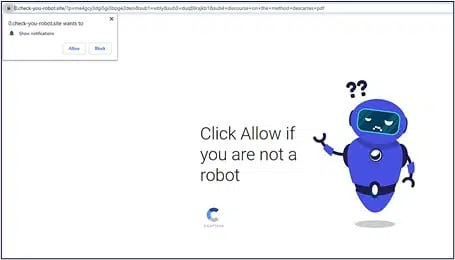
However, most of the samples initiated the following process:
The victim is redirected to the domain: traff.ru/traff.com/etc. (full list available in Related IOCs section). The path includes the name of the EXE file that will eventually be downloaded. This information is likely extracted from the PDF file. The ttraff domain does not host any content, but functions as a redirector only.
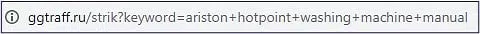
The user is redirected to another domain, usually mob1ledev1ces.com. This domain has been detected hosting malicious activity several times since its registration in 2018. The malware is automatically downloaded from the last domain.
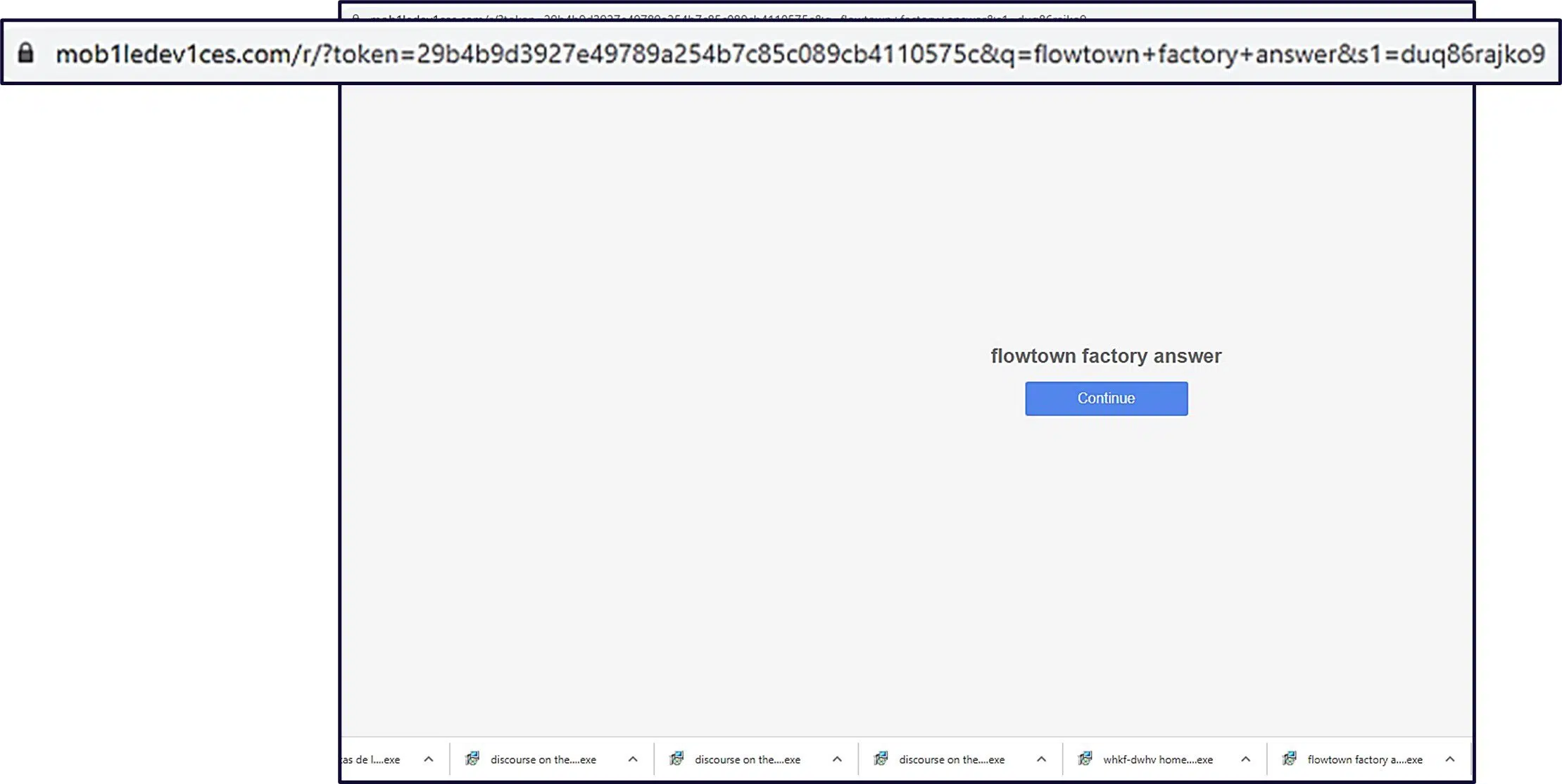
Cyberint collected the most common domains that trigger a download; however, these are only the ones related to the samples examined during the investigation and might not cover all scenarios.
As part of Cyberint’s attempts to trace the infection steps, an interesting feature was revealed: while using browser tools for web analysis (in order to examine the PDF’s redirection requests), the HTTP requests seemed to be blocked or paused. The current domain would not be replaced by the next one, and the process would continue only once the analysis tools are disabled. Presumably, this “awareness” of the code is a detection evasion mechanism, added to prevent researchers from analyzing the campaign.
At the end of the infection process, an EXE file is downloaded to the victim’s computer. Although all files examined contained the same software, they were downloaded under different names, according to the PDF that triggered them. The file, also known as topahawk.exe, is likely an adware[1][2], similar to previous campaigns involving mob1ledev1ces.com. Adware is software that automatically generates push notifications ads and unwanted pop-up ads on the user’s interface. It is considered malicious as it often degrades computer performance, gathers information regarding the user’s browsing habits, and is sometimes related to additional malware infections.
Currently, the campaign is not associated to a known Threat Actor. According to the file meta-data, there is a unique author for each document, from an unrecognized region. For instance, Nakife Nenefufowe, and Nofiti Xageti are signed as authors and creators of some of the files. The names are likely the aliases of the same Threat Actor who is responsible for this trend, or an additional output of the files’ generator, as the mentioned authors were not found related to any attributed actor.
Although the phenomenon was first observed on anti-virus repositories only, Cyberint recently detected malicious PDFs appearing on Google Search results. While at first it was assumed that the average user will not encounter them, the appearance on a Google indexing increases the probability that a user will interact with the file.
Furthermore, as Cyberint has monitored this trend over the past few months, it was noticed that the domains initiating the redirection chain (e.g. ttraff.ru) were slightly modified over time. At the time of writing this report, all domains from Cyberint’s first detections had been taken down, likely due to the malicious activity they hosted. Nevertheless, as Cyberint continues to detect new generated PDFs, new domains registered for the same purpose are expected to be detected in the near future.
Cyberint recommends organizations raise customer and employee awareness regarding these types of files, or any PDF file that contains the same components and structure. Additionally, it is recommended to block the IOCs listed below within the company network.
Cyberint will continue to monitor and alert on any changes and evolutions of the campaign, and will update the IOC list accordingly.
[1] https://www.pcrisk.com/removal-guides/18293-check-you-robot-site-ads
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


