


This blog provides an overview of the situation surrounding the release of the source code, and supplementary ‘injection’ files, for the Android banking trojan ‘Cerberus’. In addition to the source code for two versions of the malicious application along with the control panel being freely available on various underground forums, over two hundred injection files, those being HTML pages that mimic the look of legitimate Android apps, have been distributed and could allow the theft of credentials and/or payment card data.
Given that the current threat from Cerberus was countered by Google Play Protect, Google’s own Android antimalware solution, other threat actors may act on comments from Cerberus’ creators to restore the threat, or simply use the source code to create, or further develop, their own Android threats.
Recent reports indicate that Cerberus is now targeting Android users in Russia as well as countries within the Commonwealth of Independent States (CIS), suggesting that some ‘less-patriotic’ threat groups have modified the source code and removed these previously defined ‘safe countries’. Other than this activity, no other regions have been specifically identified at increased risk.
As time elapses and threat actors gain a better understanding of the released code, others may seek to utilize it, or the injection pages, in their own threats or campaigns. This is especially true given the availability of a Cerberus ‘installation service’, costing just USD 300, that could allow a lower-sophistication threat actor to gain access to a working Cerberus control panel with Android application package (APK) builder for a fraction of its former cost.
Believed to have been in development for some time and used privately for around two years prior to being first observed by cybersecurity researchers in June 2019, Cerberus is an Android banking trojan that was available via a malware-as-as-service (Maas) offering as advertised on underground forums (Figure 1).
Figure 1 – Cerberus advertisement banners (Bottom: Updated for Cerberus V2)
As is common for threats of this nature, Cerberus supports various capabilities out-of-the-box, such as the ability to interact with, and steal data from, a compromised device including contacts, SMS interception and call forwarding, as well as selling addons in the form of ‘injections’ that allow credentials and/or payment card data to be stolen from specific legitimate applications.
Reportedly earning the creators at least USD 10,000 a month during its peak, not withstanding any ill-gotten gains made from stolen data, the MaaS model used to rent access to Cerberus’ infrastructure was, when not discounted (Figure 2), available in three packages (USD 4,000 for 3 months, USD 7,000 for 6 months and USD 12,000 for one year of access) in addition to injections reportedly selling for USD 4,000 each.
Figure 2 – Cerberus ‘Winter Sale’
Having purchased a licence, nefarious users would gain access to the Cerberus control panel which allowed them to build an Android application package (Figure 3), in the form of an ‘APK’ file ready for distribution to victims, as well as providing them with the ability to manage their compromised devices and access any stolen data (Figure 4).
Figure 3 – Cerberus APK builder (added to the platform in July 2019)
Figure 4 – Cerberus Control Panel
Having configured and generated an APK payload file, threat actors would then need to deliver this to victims likely through the use of social engineering tactics and campaigns such as ‘fake media player’ messages shown to Android users visiting a compromised or malicious website (Figure 5) as well as fake mobile apps uploaded to various app stores and even the use of COVID-19 themes during the global pandemic.
Figure 5 – Cerberus distributed via fake Adobe Flash Player (Credit: ESET Research)
Reportedly one of the most successful Android banking trojans and MaaS threats of 2019 and into 2020, Cerberus’ reign came to a somewhat abrupt end in August 2020 with the creator citing ‘internal issues’ that prevented ongoing development and undoubtedly contributed to the threat being detected and blocked by Google’s built-in antimalware protection ‘Google Play Protect’.
Whilst still in development as late as 21 July 2020, seemingly the period between 22 and 26 July 2020 saw Cerberus being detected by Google Play Protect and customers taking to the forum to complain about their ‘bots dropping off’.
In response to these complaints, ‘Android’, Cerberus’ creator or the group’s spokesperson, suggested on 28 July 2020 that the threat was still operational, albeit requiring the use of a ‘cryptor’ to prevent detection (Figure 6).
Figure 6 – ‘Android’ responding in English, rather than Russian, to various complaints about Cerberus on 28 July 2020
Tools known as ‘cryptors’ are often used by malware authors and utilize various encryption routines to thwart the analysis of malicious binaries as well as obfuscating or modifying their code to evade detection signatures. In this instance, it appears that the solution to Cerberus’ problems was not as simple as using a ‘cryptor’ and was promptly followed by the group ceasing development following ‘internal issues’.
In addition to the threat group reportedly disbanding, with existing Ceberus infections being in-operational due to their detection, the malware-as-a-service (MaaS) offering, including all source code, installation guides, and setup scripts along with details of current and prospective customers, was reportedly offered for auction at the end of July 2020 with a starting price of USD 50,000 and a ‘buy-it-now’ price of USD 100,000.
Appearing somewhat steeply priced, it is likely that a suitably motivated and skilled threat actor could have recouped their outlay within a year, especially given the reported USD 10,000 monthly earnings, although, given that the auction failed to find a buyer, the ‘market’ didn’t agree with this valuation or the viability of Cerberus following its detection by Google Play Protect.
Following the failed auction attempt, and potentially in an attempt to restore confidence in the group, ‘Android’ posted a message to the ‘XSS[.]is’ forum on 5 August 2020 to confirm that they would be fulfilling any financial commitments to existing customers, presumably by refunding them any access payments, and that the source code would be made available to the forum’s members (Figure 7).
Figure 7 – Forum post indicating the release of the Cerberus Source Code to members of XSS[.]is
Translation:
v2 version. Flipper.
Since our team (before that the team) ran this business cleanly, as beautifully as possible, we will finish it beautifully.
For 70% of clients, financial obligations have already been closed. The remaining ones are asked to unsubscribe in a PM or Telegram, do not forget to write your Jabber, the license key and the server IP. This is so that I can be sure that you are the owner of the license. It is also advisable to attach the APK file.
Sources to be torn apart, especially for xss[.]is
Cerberus v1 + Cerberus v2 + install scripts + admin panel + sql db
Seemingly available on various underground forums from around 7 August 2020, a subsequent post by ‘Android’ on the XSS[.]is forum on 10 August 2020 included a cleaned-up archive (Figure 8).
Figure 8 – Cerberus source code release on XSS[.]is
Translation:
Guys, and wrap-up.
Cerberus v1 + Cerberus v2 + install scripts + admin panel + sql db
Archive cleared of garbage.
Everything for those who want to start their own business. Full pack.
In the header, I replaced the link to it.
For moderators, please re-upload to other [file sharing services] so that the file will live for a long time.
Analysis of the source code archive indicates that the directories have modification dates of 5 August 2020, confirming the archive creation of the file that aligns with the forum posts, whilst the files, excluding any open-source libraries used, have various modification dates between 31 March 2019 and July 21 2020, again consistent with what is known about Cerberus’ recent development.
Note: For reference, sample file hashes for the released Cerberus source code are provided in Appendix A.
Included within the main archive are four main directories:
moduleBot2 – Java source code and assets for the Cerberus v2 Android payload including build files for use with the ‘Gradle’ build automation tool. Based on application icons found within the directory structure, the threat appears to mimic a ‘Santander’ banking app but it is understood that this would be customizable when using the ‘builder’ control panel.panel_v2 – HTML, JavaScript and PHP source code for the server that provides the Cerberus control panel, APK payload builder and the command and control (C2) call-home ‘gate.php’ script. Notably, the payload builder takes parameters from the threat actor and then executes the Gradle build automation tool before allowing the payload to be downloaded. Additionally, ‘cryptor’ code appears within this directory that could allow payloads to thwart analysis or detection albeit, based on the Google Play Protect detection, this has been countered.restapi_v2 – Seemingly allowing interactions between bots and the C2 server/control panel, the REST API directory includes PHP code and provides an insight into the status of a bot including the relatively short period of time elapsed for it to be considered ‘dead’ (albeit understandable given that most people will keep their mobile phone online at all times):
0 – Online (Bot has been visible within the last 2 minutes); 1 – Offline (Bot has been visible within the 40hrs but not last 2 minutes); 2 – Dead (Bot has not been seen within the last 40hrs);source_mmm – Java source code and assets for the Cerberus v1 Android payload, again including build files for use with the ‘Gradle’ build automation tool.com.connectivityapps.hotmail)com.google.android.gm)com.imo.android.imoim)com.instagram.android)com.mail.mobile.android.mail)com.microsoft.office.outlook)com.snapchat.android)org.telegram.messenger)com.twitter.android)com.ubercab)com.viber.voip)com.tencent.mm)com.whatsapp)com.yahoo.mobile.client.android.mail)Whilst the immediate threat from Cerberus has been countered by Google Play Protect, the release of the source code provides other threat actors with the ability to analyse and understand how Cerberus’ modular capabilities were implemented, potentially allowing others to extend them or reuse the code in other Android threats.
As is to be expected of a successful Android threat, Cerberus claims to work on devices using Android 5 or later and, have gained ‘accessibility’ permissions, can automatically permit additional permissions for itself including:
android.permission.INTERNET;android.permission.CALL_PHONE;android.permission.REQUEST_IGNORE_BATTERY_OPTIMIZATIONS;android.permission.RECEIVE_BOOT_COMPLETED;android.permission.READ_PHONE_STATE;android.permission.REQUEST_DELETE_PACKAGES;android.permission.RECEIVE_SMS;android.permission.READ_SMS;android.permission.SEND_SMS;android.permission.READ_CONTACTS;android.permission.WAKE_LOCK;Given these permissions, many capabilities can be identified, such as those that are consistent with a remote access trojan gaining access to, and control over, the device:
Additionally, specific banking trojan capabilities provide the means to gather credentials and payment card data as well as thwarting additional security measures such as one-time passwords, multi-factor authentication and voice calls:
In an attempt to evade security controls and thwart analysis, Cerberus implemented anti-emulator code to ensure that it was only executed on a valid physical device, attempted to disable Google Play Protect, albeit until its detection, and provided a self-destruct mechanism to remove traces of the bot to prevent post-incident analysis.
Finally, command and control (C2) traffic is RC4 encrypted and base64-encoded using a random key. Subsequently, ‘call home’ communications include useful data about the device which is viewable within the control panel:
Features: hide SMS, lock device, mute sound, keylogger, injection
Cerberus makes use of ‘injections’ to target legitimate applications, including those related to banking, email, messaging, retail and social media, with pages that mimic the targeted application interface and prompt for credentials and/or payment card details from the victim (Figure 9).
Figure 9 – Example ‘injects’ mimicking legitimate application interfaces
These HTML-based injects are provided as a single file asset, allowing them to be easily stored within the command and control (C2) database and distributed to victim devices, integrating cascading style sheets (CSS) to ensure the layout is consistent with the targeted application as well as embedding base64-encoded images (Figure 10).
Figure 10 – Example embedded base64-encoded PNG image within the inject HTML file
Once deployed, a victim would be presented with the inject when attempting to access a targeted application and, assuming they fall for the ruse, the data entered is inserted into a JSON data structure ready for exfiltration by Cerberus to the C2 infrastructure.
Seemingly a ‘starter kit’ was offered by Cerberus with a handful of injections to target Italy, France, Turkey and the United States, whilst additional injections could be purchased (Figure 11).
Figure 11 – Cerberus ‘Tweet’ indicating the sale of injects
Notably, in addition to base64-encoded injects embedded within the SQL dump file distributed with the Cerberus control panel source code, archives of this recent release distributed on underground forums include over 200 additional inject files potentially including some that would have previously been charged for.
Note: For reference, a full list of the injects distributed with the Cerberus source code are provided in Appendix B.
Given that these inject files mimic many current mobile applications, the release of this large set could allow other malware authors to incorporate them into their own mobile threats as well as being of use to any threat actor that can make use of, or further develop, the Cerberus source code.
As is common with cybercrime threats originating from Russia or countries within the Commonwealth of Independent States (CIS), threat actors will only target victims in other countries as confirmed by a string variable within Cerberus’ source code containing a safe list of country codes:
public String strCIS = "[ua][ru][by][tj][uz][tm][az][am][kz][kg][md]";
Since the public release of Cerberus’ source code, other seemingly less-patriotic threat actors have removed or modified this restriction and there is now reportedly an increase in victims within Russia and CIS countries.
Aside than this shift in targeting, no other region has been identified as suffering from increased attacks although, with time, other threat actors may seek to leverage their access to the source code and potentially launch attacks in regions where Android devices are prevalent whilst less likely to be protected by current versions of Google Play Protect.
In addition to threat actors taking the Cerberus source code ‘as-is’ and attempting to launch their own campaigns, especially given that an ‘enterprising’ user on the XSS[.]is forum is offering an installation service for just USD 300 (Figure 12), others may seek to build upon the existing code or create their own variants to resolve the issues that caused Google Play Protect to detect the threat.
Figure 12 – XSS[.]is forum member offering proof of their Cerberus install service
One such example that has been reported as a variant of Cerberus is a threat dubbed ‘Alien’ although, both the creators of Alien and Cerberus have denied any link between the two.
Providing any would-be successor with the necessary information to resolve Cerberus’ issues, two suggestions are given to counter Google Play Protect’s ability to scan application resources (Figure 13).
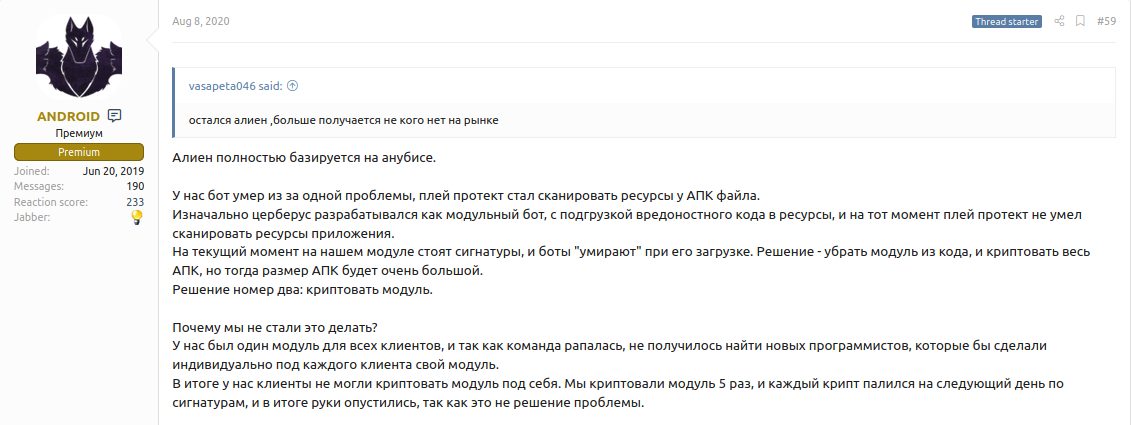
Translation:
Alien is based entirely on Anubis.
Our bot died due to one problem, the play-protection started scanning the resources of the APK file.
Initially, Cerberus was developed as a modular bot, loading malicious code into resources, and at that time Play Protect was unable to scan application resources.
At the moment, our module has signatures, and bots “die” when it is loaded. The solution is to remove the module from the code and encrypt the entire APK, but then the size of the APK will be very large.
Solution number two: encrypt the module.
Why didn’t we do it?
We had one module for all clients, and since the team was crumbling, it was not possible to find new programmers who would make their own module for each client individually.
As a result, our clients could not encrypt the module for themselves. We encrypted the module 5 times, and each crypt fell the next day according to the signatures, and in the end our hands dropped, since this is not a solution to the problem.
Whilst it is likely only a matter of time before a suitably skilled nefarious developer resolves the issues with Cerberus, the release of the source code will undoubtedly assist the Google Play Protect team in creating countermeasures. That being said, organizations should still encourage users to, and individuals should, be cautious whenever prompted to install Android packages (APK) from unverified sources, be that a browser pop-up, an email or from a third-party app marketplace.
The following SHA-256 file hashes relate to the leaked files, as observed on multiple underground forums, and may prove beneficial to security professionals wishing to perform their own analysis of the threat:
cerberus_full_package.7z
2ba17fabce13866b6f161250f00d85e14fefc6334dc1bdd881bb71ba41a69d80CERBERUS_V2.zip
733fc478acd6ef668f88131f505921fddc88e9a207e5ee304b37babf0b8a553dinjects.zip
856ea6fd89f431274335614e91fdd83a99aaa3243395a28d7e55307a04090923cerberus.zip
beabdc7eedea45771c11e2319f810035fdbf67e725b593a80ef54438ee3731f5Given the current status of Cerberus, indicators of compromise (IOC) related to past Cerberus threats are somewhat redundant although the command and control (C2) Tor hidden service still appears to be accessible via cerberesfgqzqou7.onion (Figure 14).
Figure 14 – Cerberus control panel Tor hidden service
Additionally, the following HTTP command and control (C2) communication strings were observed within the source code and may appear in derivative works:
action=getinj&data=;action=injcheck&data=;action=botcheck&data=;||no||;action=registration&data=;action=sendInjectLogs&data=;action=sendSmsLogs&data=;action=timeInject&data=;public String str_http_19 = “action=sendKeylogger&data=”; public String str_http_20 = “action=getModule&data=”; public String str_http_21 = “action=checkAP&data=”;action=sendKeylogger&data=;action=getModule&data=;action=checkAP&data=;Injection files have been provided alongside the Cerberus source code and target the following legitimate Android applications:
com.abanca.bancaempresases.caixagalicia.activamovilcom.abnamro.nl.mobile.paymentscom.akbank.android.apps.akbank_direktpl.allegrocom.amazon.mShop.android.shoppingnz.co.asb.asbmobilees.liberbank.cajasturappcom.tecnocom.cajalaboralcopergmps.rt.pf.android.sp.bmpsro.btrl.mobilees.caixageral.caixageralappcom.itau.empresasnet.inverline.bancosabadell.officelocator.androidcom.bankaustria.android.olbcom.ideomobile.hapoalimwit.android.bcpBankingApp.millenniumPLpl.millennium.corpAppcom.infonow.bofaorg.bom.bankes.cm.androidcom.bankinter.launcherorg.banksa.bankcom.caisseepargne.android.mobilebankingfr.banquepopulaire.cyberpluscom.caisse.epargne.android.tablettecom.barclays.android.barclaysmobilebankingcom.barclays.ke.mobile.android.uicom.bbva.netcashcom.bbva.bbvacontigocom.mtel.androidbeacom.bendigobank.mobilecom.mobikwik_newgt.com.bi.bienlineacom.oxigen.oxigenwalletcom.binance.devcc.bitbank.bitbankjp.coincheck.androidpiuk.blockchain.androidcom.bmo.mobileit.bnl.apps.bankingcom.finanteq.finance.bgzcom.bochk.comcom.bankofqueensland.boqcom.boursorama.android.clientspt.bancobpi.mobile.fiabilizacaopl.bps.bankowoscmobilnapl.bphcom.finanteq.finance.caes.lacaixa.mobile.android.newwapiconcgd.pt.caixadirectaparticulareses.ceca.cajalnetcom.cajasur.androidcom.konylabs.capitaloneit.carigebe.fimaser.smartphonepl.ceneocom.tebcom.chase.sig.androidcom.cibc.android.mobicom.cic_prod.badcom.konylabs.cbplpatcom.arkea.android.application.cmso2org.toshide.comdirect.androidcom.commbank.netbankde.commerzbanking.mobilcom.connectivityapps.hotmailde.consorsbankcom.CredemMobilecom.ocito.cdn.activity.creditdunordcom.cm_prod.badcom.arkea.android.application.cmbcz.csob.smartbankingau.com.cua.mbcom.db.pbc.DBPaycom.db.pwcc.dbmobilecom.ideomobile.discountcom.discoverfinancial.mobilede.dkb.portalappcom.empik.empikappcom.empik.empikfotofinansbank.enparapl.eurobank2es.evobanco.bancamovilcom.clairmail.fthcom.fortuneo.androidcom.garanti.cepsubesicom.getingroup.mobilebankingcom.google.android.gmcom.gmowallet.mobilewalletcom.grupocajamar.wefferentcom.grppl.android.shell.halifaxcom.tmobtech.halkbankcom.htsu.hsbcpersonalbankingeu.unicreditgroup.hvbapptanes.ibercaja.ibercajaapppl.bzwbk.ibiznes24hr.asseco.android.mtoken.boscom.snapwork.IDBIpl.ideabank.mobilebankingpl.pkobp.ikocom.imaginbank.appcom.imo.android.imoimcom.csam.icici.bank.imobilede.ingdiba.bankingappcom.comarch.security.mobilebankingwww.ingdirect.nativeframeit.ingdirect.appcom.instagram.androidcom.latuabancaperandroid_2com.latuabancaperandroidpl.pkobp.ipkobiznescom.pozitron.iscepcom.kraken.tradecom.kutxabank.androidcom.kuveytturk.mobilmobi.societegenerale.mobile.lapplicom.db.pbc.miabancafr.laposte.lapostemobilecom.leumi.leumiwalletcom.quoine.quoinex.lightcom.grppl.android.shell.CMBlloydsTSB73fr.creditagricole.androidappcom.mail.mobile.android.mailpl.mbankfr.lcl.android.customerareanet.bnpparibas.mescomptescom.db.pbc.mibancocom.popular.android.mibancocom.microsoft.office.outlookcom.MizrahiTefahot.nhcom.unicreditcom.comarch.mobile.banking.bgzbnpparibas.bizneseu.inmite.prj.kb.mobilbankpl.raiffeisen.nfcpl.orange.mojeorangepl.ing.mojeingcom.att.myWirelessde.number26.androidau.com.nab.mobilecom.indra.itecban.mobile.novobancopl.nestbank.nestbankcom.moneybookers.skrillpayments.netellercom.db.mm.norisbankfr.oney.mobile.mescompteses.openbank.mobilecom.mobillium.paparacom.paypal.android.p2pmobileeu.eleader.mobilebanking.pekaoeu.eleader.mobilebanking.pekao.firmsoftax.pekao.powerpaycom.fusion.ATMLocatores.pibank.customerseu.eleader.mobilebanking.investma.gbp.pocketbankde.postbank.finanzassistentposteitaliane.posteapp.apppostepaycom.finansbank.mobile.cepsubecom.isis_papyrus.raiffeisen_pay_eyewdgcom.advantage.RaiffeisenBankjp.co.rakuten_bank.rakutenbankcom.rbc.mobile.androidcom.cajasiete.android.cajasietereportpl.com.rossmann.centauroscom.rsies.bancosantander.appsde.santander.presentationes.bancosantander.empresaspl.bzwbk.bzwbk24net.garagecoders.e_llavescotiainfoit.popso.SCRIGNOappde.adesso_mobile.secureapp.netbanktr.com.sekerbilisim.mbankcom.moneybookers.skrillpaymentsit.gruppobper.ams.android.bpercom.snapchat.androidcom.starfinanz.smob.android.sfinanzstatusorg.stgeorge.bankjp.co.netbkau.com.suncorp.SuncorpBankcom.suntrust.mobilebankingcom.targo_prod.badorg.telegram.messengercom.fibi.nativeappat.spardat.bcrmobilecom.indra.itecban.triodosbank.mobile.bankingcom.twitter.androidcom.usbank.mobilebankingcom.ubercabit.nogood.containeres.univia.unicajamovilcom.unionBank.appcom.unionbank.ecommerce.mobile.androidcom.usaa.mobile.android.usaaalior.bankingapp.androidcom.vakifbank.mobilecom.viber.voipat.volksbank.volksbankmobilede.fiducia.smartphone.android.banking.vrcom.tencent.mmcom.wf.wellsfargomobilecom.westernunion.moneytransferr3app.escom.whatsappil.co.yahav.mobbankingcom.yahoo.mobile.client.android.mailcom.ykb.androidcom.sbi.SBIFreedomPluscom.lynxspa.bancopopolarecom.ziraat.ziraatmobil
Fill in your business email to start


