


Following the recent discovery of suspicious script files exposed on dynamic DNS (DDNS) hosts, presumably due to misconfiguration by the threat actor given that the ‘directory listing’ option was enabled (Figure 1), Cyberint investigated the content to determine its nature.
Following an analysis of all files, including multiple levels of script deobfuscation, these DDNS hosts appear to contain lures and payloads consistent with an Iranian nexus state-sponsored threat actor. Given the organisations identified within this content, the intended victims are likely individuals working in the petrochemical industry with an apparent focus on Saudi Arabia.
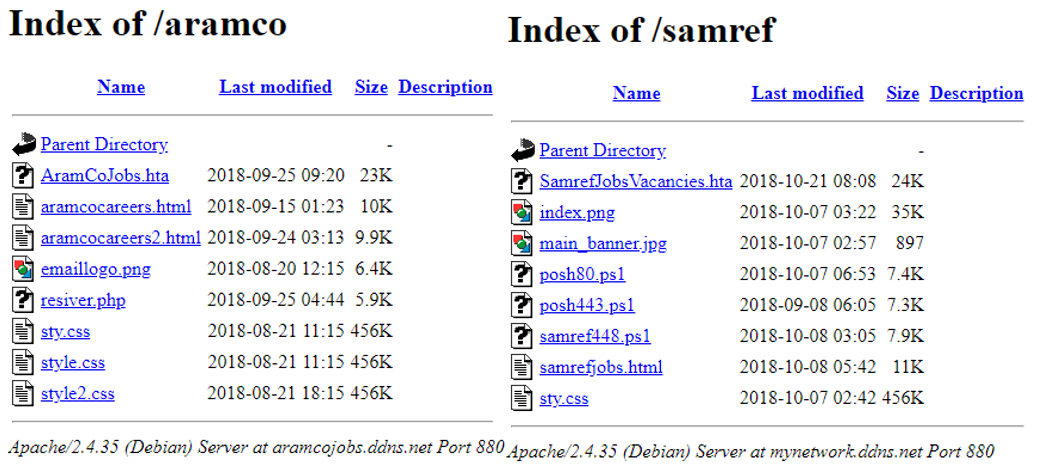
Based on the content found within this, and subsequently further identified, threat actor command and control (C2) infrastructure, the campaigns utilize a lure masquerading as a job vacancy relevant to the target and, through the download and execution of multiple stages of encoded scripts, appear to result in victim information being transmitted to this C2 infrastructure, the delivery of further payloads and the execution of a reverse HTTP shell.
An initial investigation into the observed tactics, techniques and procedures (TTP) along with the identified indicators of compromise (IOC) suggest consistencies and similarities between this campaign and previous APT33 activity, as reported by FireEye in 2017.
APT33, widely attributed as an Iranian state-sponsored threat actor, is believed to have been operating since at least 2013 and was reported on during 2017. Typical targets for this threat actor appear to align with Iranian national interests, specifically the aerospace, defence and petrochemical industries in Saudi Arabia, South Korea and the United States. As observed in this campaign, previously identified APT33 TTP includes the use of spear-phishing emails with weaponized HTML application files, often masquerading as job vacancies, as well as the creation of domains and Dynamic DNS hosts, acting as C2 infrastructure, that utilize names impersonating legitimate organisations relevant to the attack.
Download the full report to read mote about including Attack Summary and File Analysis
Whilst the initial distribution vector has yet to be identified, previous campaigns sharing similar TTP suggest that victims would be specifically targeted and lured into executing a weaponized HTML application (HTA). As with previous campaigns, the HTA files contain job descriptions cloned from legitimate websites that would presumably be of interest to the target victim. In the past, it is reported that victims would be targeted with spear-phishing emails, recruitment-themed lures, containing links to the weaponized HTA file.
When lured into opening the HTA file, the victim is presented with the cloned job description whilst, in the background, multiple malicious scripts are executed. In addition to ‘calling-home’, these scripts download additional payloads to the victim as well as configuring scheduled tasks for persistence.
Rather than delivering multiple executable files, this campaign makes use of numerous JavaScript (JS), Visual Basic (VBS) and PowerShell (PS) scripts which, along with utilizing native Windows functions, allows the threat to ‘live off the land’ and maintain a smaller footprint to evade detection. To counter analysis and potentially signature-based detection, multiple layers of script obfuscation have also been employed and a file-less payload delivered for execution in memory rather than being saved to disk.
Download the full report to read more about including Attack Summary and File Analysis
Fill in your business email to start


