


Over the past forty-eight hours, since 5 April 2018, there have been numerous open source reports of wide spread cyberattacks targeting Cisco networking devices, specifically switches using the Cisco Smart Install Client, primarily within Iran and Russia.
Cisco Talos Intelligence Group reports that multiple organisations, including those operating critical infrastructure, have been targeted worldwide by a protocol misuse issue within the Cisco Smart Install Client, a utility designed to allow zero-touch configuration of Cisco Switches.
Whilst the Cisco Talos report ascertains that these attacks may be associated with nation- state threat actors, other reports link and attribute the attacks to the Russian nexus nation- state threat actor known as Dragonfly, potentially due to the 15 March 2018 alert published by US-CERT that detailed attacks against energy, nuclear and commercial facilities.
Aside from the US-CERT report, the security vendor Embedi published a blog post on 29 March 2018 describing a critical Stack Buffer-Overflow Remote Code Execution (RCE) vulnerability, CVE- 2018-0171, within the same Cisco Smart Install Client that “enables an attacker to remotely execute arbitrary code without authentication” and “allows getting full control over vulnerable network equipment” .
Cisco Smart Install allows organisations to deploy new network switches to locations without the need for preconfiguration. Using plug-and-play configuration and image management features, the smart install devices enable zero-touch deployment by communicating with a common layer-3 switch or router that is acting as a ‘director.’
This director then, provides a single management point, to deploy configurations or device ‘images’. When deploying a new Cisco switch with Smart Install technology, the director detects the device, identifies the appropriate Cisco IOS software image and configuration file before downloading these to the device. Furthermore, the director is able to perform on-demand deployments of software images and configurations to individual or groups of Cisco switches within the managed network.
In addition to earlier reported vulnerabilities, organisations that fail to disable or securely configure the SMI protocol can allow threat actors to abuse functionalities such as:
Over the past few days, numerous reports regarding exploitation of these Cisco Smart Client protocol vulnerabilities or flaws have been made public, including attacks against media and communications organisations within Iran and Russia.
Amongst these, major Russian online media providers such as Fontanka.ru and Komsomolskaya Pravda reportedly suffered outages, while ‘important’ Iranian services and websites where inaccessible due to problems at ISPs in the region.
The threat actor behind these attacks is believed to have exploited a misconfiguration of the Cisco Smart Install protocol to override deployed Cisco IOS images or configurations on vulnerable devices, changing them to display seemingly pro-American messages protesting alleged interference in the presidential elections (Figure 1).
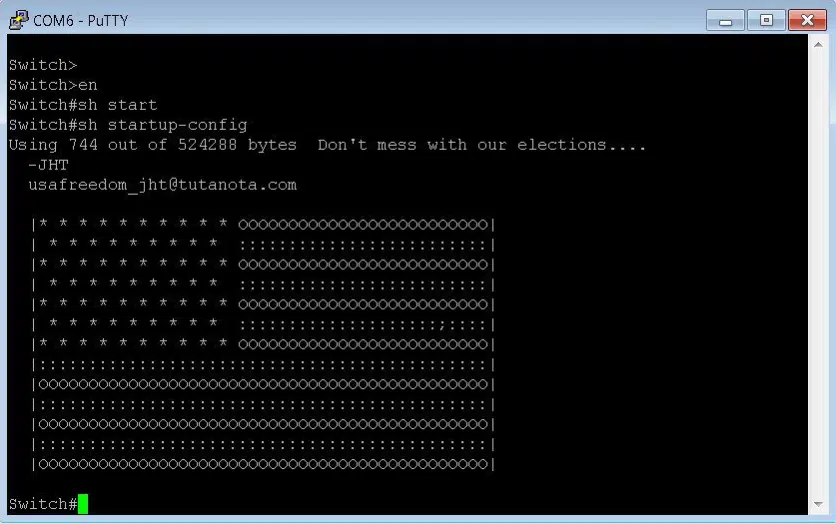
Figure 1 – Compromised Cisco Switch
Given the widespread use of Cisco networking devices within the infrastructure of organisations worldwide, the threat from this vulnerability is widespread. A Shodan search for Cisco devices exposing the Smart Install Client protocol revealed over 168,000 internet-accessible devices (Figure 2).
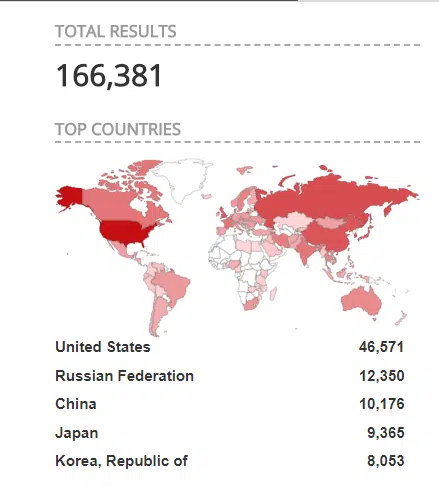
Figure 2 – Cisco Smart Install Client Exposure (Shodan.io)
Scans for SMI-enabled devices (port 4786) have started in February 2017, intensified in October, and doubled after the last Cisco Talos warning in February, this year. (Figure 3)
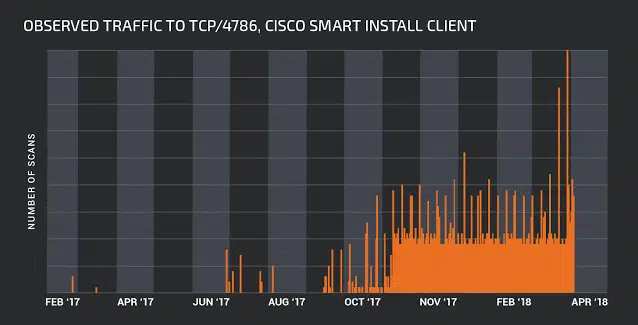
Figure 3 – Observerd Traffic to tcp 4786, cisco smart install client
The misuse of this Cisco IOS smart install feature was first reported by Cisco in February 2017 , with scans for SMI-enabled devices intensifying in October 2017, prompting the release of a configuration guide that details how to disable or harden IOS devices against misuse of protocol, last updated on 26 March 2018 . Furthermore, Cisco Talos have released an open source tool to scan networks to determine if there are any Smart Install enabled devices present.
Whilst the Cisco Talos report links to the recent US-CERT publication attributing attacks to the Russian nexus nation state threat actor known as Dragonfly, it is understood that the recent remote code execution vulnerability, CVE-2018-0171 published by Embedi is not related to this incident .
Furthermore, given the seemingly pro-American sentiment and the reported location of exploited devices, we assess with moderate confidence that these recent events are not related or attributed to any known threat actor. Based on the tactics, techniques and procedures (TTP) observed, combined with the victim geolocation and detail reported thus far, we believe that these incidents are currently unrelated to previous Dragonfly operations.
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


