


With the PyeongChang 2018 Olympic Winter Games well underway, CyberInt researchers have been hitting the cyber-slopes in order to further ‘carve up’ threats directed at the organisers and participants of this, and potentially future, Olympic events.
As reported in late December 2017 and early January 2018, a malicious campaign targeting several organisations associated with the PyeongChang 2018 Olympic Winter Games was active between 22 and 28 December 2017. This campaign saw malicious Microsoft Word documents being sent as attachments to emails masquerading as originating from the South Korean National Counter-Terrorism Center (NCTC).
Once the malicious document was opened, the victim is lured, using Korean text, into clicking on the Microsoft Word ‘Enable Content’ security warning to “adjust this document to your version”. In reality, enabling the active content allows a Visual Basic macro to execute which then launches the next phase of the attack, a PowerShell script. This subsequent script attempts to download an image file from a remote server which, using the steganography tool ‘Invoke-PSImage'[1], contains an additional obfuscated PowerShell script payload. This script, then attempts to connect to a seemingly compromised website using HTTPS which may then act as a command and control (C2) server.
Additionally, the malicious script creates two string values within the ‘HKCUSoftwareMicrosoftWindowsCurrentVersionThemes’ registry key that contain the obfuscated PowerShell script (Figure 1).
Figure 1: PowerShell script within ‘HKCUSoftwareMicrosoftWindowsCurrentVersionThemes’
These registry keys are then referenced by a newly created scheduled task (Figure 2) named ‘MSDefaultTaskCore’ that serves as a persistence mechanism.
Figure 2: Scheduled task named ‘MSDefaultTaskCore’ used for persistence
Following this, McAfee’s Advanced Threat Research team observed[2] a second malicious document file which, rather than performing the multiple steps above and containing macros, used OLE streams to launch a HTA file payload containing the PowerShell script whenever the document is opened.
Whilst this initial attack took place in December 2017, there is potential for the threat actor to continue to use these techniques to target organisations associated with the PyeongChang 2018 Olympic Winter Games whilst they are underway. Given this CyberInt‘s research team have been investigating the reported techniques and indicators to determine if any other instances of the campaign can be found.
The following indicators of compromise (IOC) were attributed to the initial attack as reported by McAfee:
File Hashes (SHA-1)
File Names
IP Addresses
Domains
URLs
An analysis of the malicious document file containing OLE streams, identified by McAfee as SHA-1 ‘c388b693d10e2b84af52ab2c29eb9328e47c3c16′[3], allows two OLE Objects to be observed, both of which appear to be detected by a number of antivirus (AV) engines:
Additionally, the obfuscated PowerScript payload can also be observed along with strings that provide a HTA filename of ‘Error 733 .hta’ and insight into the threat actor’s configuration, specifically, the files were created by a Windows user named ‘john’ based on their profile directory name (Figure 3).
Figure 3: Windows user profile directory & HTA filename
Pivoting on these document traits permits the discovery of similar samples that may be associated with the same threat actor. In this instance, e34481533b68157d803aba3fac04e98283f740d5[6], a Microsoft Word document file named ‘New folder.docx’ created on 19 December 2017, was uploaded to VirusTotal via the Tor anonymisation network on 20 December 2017, some two days before the reported initial attack and the file contains suspicious OLE content.
Analysis of the file’s OLE content, 0b95b71b579ccd2aaee296ed4d7aa5a05d7aa2b8[7], identifies similar traits to the malicious document, references the same user profile directory name, and provides a HTA filename of ‘test.hta’ (Figure 4).
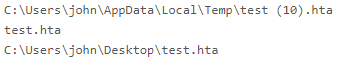
As before, the script payload can be observed and appears to contain benign code (Figure 5) that attempts to launch the Windows Calculator, a common test technique and unsurprisingly resulting in no AV engines detecting this file as a threat.
Figure 5: Test script
Given the benign nature of this file and embedded code, it is potentially indicative of the threat actor testing their weaponisation techniques, presumably to observe AV detection rates, prior to launching their actual attack. Furthermore, the use of Tor to upload the sample to VirusTotal demonstrates a level of operational security (OPSEC) in that the threat actor does not want their true IP address or location to be linked to the sample.
Further pivots identify another sample, SHA-1 ‘7ae731d666e547b4f3442fe5675c8e8719d8d862’, created on 5 February 2018 at 1728hrs UTC and first submitted to VirusTotal[8] seemingly from a South Korean source at 2316hrs UTC on the same day.
This file exhibits the same characteristics as the others and appears to have been created by the same threat actor. Additionally, the document is named ‘협박전화테러 예방.doc’ (Translation: Threatening telephone terrorism prevention.doc) which may suggest that the threat actor is continuing to use lures that masquerade as documents sent from the NCTC.
In this instance, the document utilises a macro containing obfuscated code (Figure 6) which decodes to a PowerShell script that appears to have been generated by ‘ObfuscatedEmpire'[9].
Figure 6: Obfuscated Macro code
Deobfuscation of this macro uses two main techniques, the conversion of hexadecimal strings to their corresponding ASCII character followed by a simple character rotation of ‘minus five’. The use of these techniques is mixed within the code and therefore it is necessary to perform the hexadecimal to ASCII conversion first, concatenate the results with the non-hexadecimal content and then perform the character rotation (Figure 7).
Figure 7: Macro deobfuscation
The use of ObfuscatedEmpire generates obfuscated PowerShell code that executes a channel to the threat actor’s C2 infrastructure in memory which, given the lack of disk interaction, can be used to evade AV detection.
Basic deobfuscation of the PowerShell code involves reorganising elements of an array into the correct order and this can be used to extract useful information such as the C2 server (Figure 8).
Figure 8: ‘ObfuscatedEmpire’ generated PowerShell code
Having deobfuscated the content within this threat, the C2 server and path can be obtained and, much like the earlier campaign, appears to reside on a compromised webserver:
Additionally, this server hosts the obfuscated PowerShell script in a file named ‘access_log’:
The domain ‘minibodegaslock.cl’, in this case used by a self-storage business in Chile, resolves to ‘201.238.211.140’, an IP address assigned to Gtd Internet S.A. (CL), and is used to host numerous seemingly legitimate websites.
Once executed, additional hosts appear as strings within memory, all of which resolve to the same Chilean IP address ‘201.238.211.140’ and are potentially indicative of further C2 infrastructure:
During our investigation, all of the PowerShell scripts executed were observed as beaconing to the same C2 domain ‘napoleon.smart.cl:443’ on the above IP address. Aside from the other similarities in the lure and initial obfuscated code, this provides a strong indicator that the campaign is being coordinated and operated by the same threat actor.
Additionally, the domain ‘patiolareina.cl’ was observed as hosting two instances of the PowerShell script that references the C2 server ‘minbodegaslock.cl’ albeit located in a slightly path:
Based on these findings, we can conclude that the threat actor responsible for the reported attack in December 2017 against organisations associated with the PyeongChang 2018 Olympic Winter Games likely tested their methods prior to the attack and currently have infrastructure in place, along with the recently detected lure, to continue their campaign against relevant targets.
Given this, users should be reminded to exercise caution when receiving unsolicited or suspicious attachments as well as taking heed of security alerts such as those displayed by Microsoft Word. Furthermore, infrastructure owners may wish to monitor their environments for any communication involving the IP addresses and hosts identified above as these may serve as an indication of compromise.
References:
[1] https://github.com/peewpw/Invoke-PSImage
[2] https://securingtomorrow.mcafee.com/mcafee-labs/malicious-document-targets-pyeongchang-olympics/
[3] https://www.virustotal.com/#/file/d88ea493cdd719ff2e2c02cea66dd15d358f914ea8741d6d6d3dd60b66adf923/
[4] https://www.virustotal.com/#/file/15643534a9c9d8b1445d604293f91191ef1814448dc77aaa5edee1d2f47fe17e/
[5] https://www.virustotal.com/#/file/f2bce76a36e7eba67bc469ebf42b8d1e4fce57820c4648157e6f09f3747e4e90/
[6] https://www.virustotal.com/#/file/0a5ae9735de90ae572031644ce83372a3083475e9712f43d9e2d344fb0f74db4/
[7] https://www.virustotal.com/#/file/1a906ebc2633c0cb53e687b9623400952a9ded8200beb5cc59f30d29677f3449/
[8] https://www.virustotal.com/#/file/cceb8abae023acf0db3e98f4aabfc92ab3ca933483f4370d621d957fcef0e2b4/
[9] https://cobbr.io/ObfuscatedEmpire.html
Fill in your business email to start


