


We come across many flash based applications during our penetration tests for customers.
We’ve decided to share a fix-it, or trick if you will, that makes our penetration testing for flash applications much easier.
At CyberInt, our pen testing team used to have recurring difficulties when we tried to execute dynamic analyses on Flash applications.
This is how we overcame it among our team:
(By the way, this trick has also helped us a lot with static analyses.)
Our pen-testing team is known for using JPEXS whenever we need to analyse an SWF file.
You can download JPEXS here: https://github.com/jindrapetrik/jpexs-decompiler/releases
What we’ve found in our pen-testing lab is that JPEXS is a simple, yet optimal tool for dynamic analyses on SWF files.
Before you carry out the SWF Dynamic Analysis, you need to do the following:
Download the most updated:
All downloads are available here: https://labs.adobe.com
Once you’ve downloaded the flash player updates, configure JPEXS to load the file downloads;
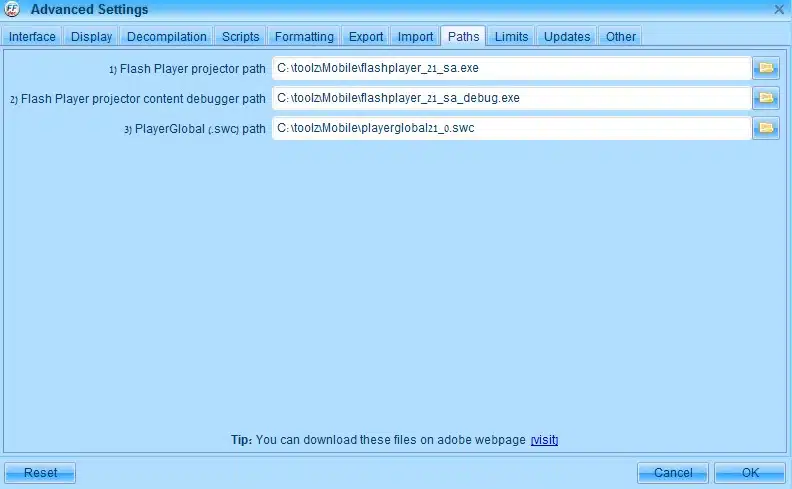
That’s it! Dynamic Analyses is ready to roll;
Example: Adobe Labs’ “Puzzle Game”
Download the Puzzle Game here:
www.adobe.com/devnet/archive/flash/articles/puzzle_game.html
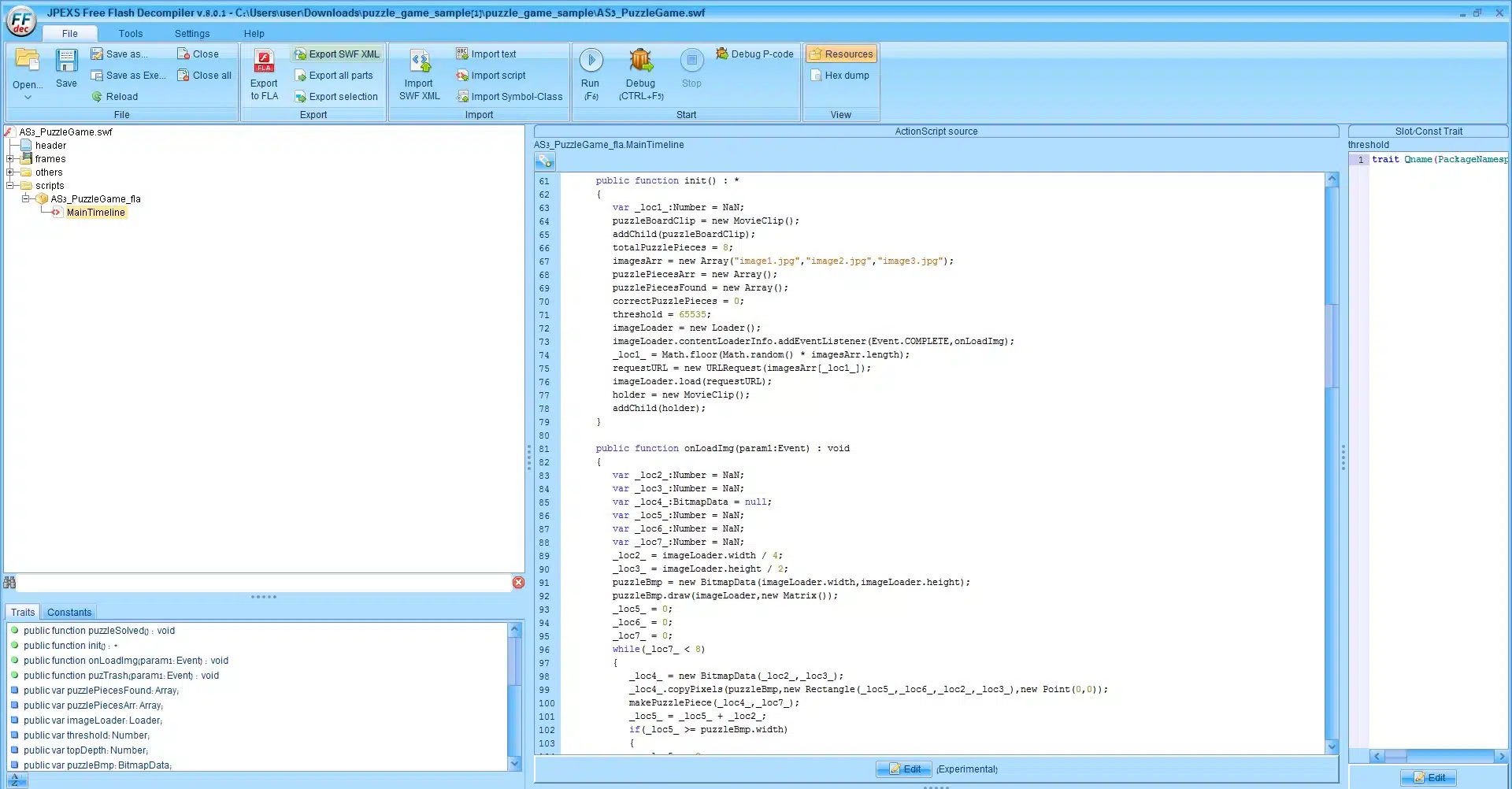
By analyzing the AS3 functions, we have figured that when a player is finish connecting all of the puzzle parts a function named puzzleSolved is called.
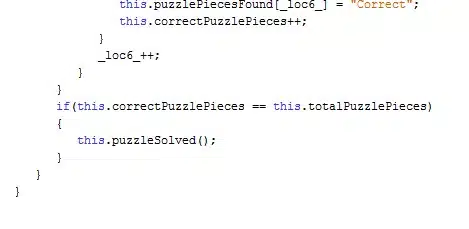
Aha! Moment: as soon as the player connects all the pieces, the puzzleSolved function gets called!
Now we need to find the the function’s code to see if the application can call it from another location;

This is how the application defines the puzzleSolved function:
This is where we realized that there’s no validation of who calls the puzzleSolved function.
Now what?
We need to find a good enough location for calling the puzzleSolved function without actually solving the puzzle.
This is how we did it:
By the way, JPEXS supports editing the game’s AS3 so that you can change the calling point;
We found the MouseDown event, which is defined in the pieceMove function.
The MouseDown event is triggered after each click by the user.
This is a perfect location to relocate the puzzleSolved call.

What’s Next?
Now the tool compiles the application with our changes and saves the SWF to the Temp folder.
C:UsersuserAppDataLocalTemp

Each time the mouseDown event gets triggered, the puzzleSolve function will be called.
See for yourself!

P.S. you can also use JPEXS to perform an SWF static analysis.
How can you protect your SWF files from being analysed by hackers?
One way your SWF files can be obfuscated is by using the general obfuscation tools available via Google search.
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


