


It’s been almost a month since the Bangladesh Bank hack was brought to global attention, causing finance professionals and consumers alike to raise concern for the SWIFT technology, that was initially considered to be an optimally secure messaging system for interbank financial transactions.
In that time, many banks and governance bodies, namely Bank of England, and Singapore’s Central Bank have been proactive in their strategic responses; each of whom implemented and issued orders for compliance and security-beefing measures.
These risk-management strategies are (retroactively) well endorsed by the recent Symantec report, which states that hackers aspire to hack finance institutions directly, as opposed to end users, given the former’s higher lucrativity as an attack target.
Indicators of Compromise
In a privately held communication (somewhere between mid-to-late April) between the BoE and UK banks, BoE have ordered the British banks to “check for indicators of compromise” on every and any computer connected to the SWIFT messaging service.
Banks are expected to deduce these indicators from digital evidence found in computer logs, which can also include IP and email address linked to recent attacks.
As a protective measure for the future, BoE is instructing the banks to conduct ‘user entitlement reviews’, which will demand that SWIFT applications and messaging gateway are only accessible to exclusively authorised staff members.
Systems Audit
UK banks were also instructed by BoE to conduct an audit of any system connected to SWIFT. In total, 11,000 institutions worldwide use SWIFT to respectively communicate and transfer funds.
Compliance Check
Each UK bank were also called upon to perform a compliance check on their systems, and to confirm that they are abiding by SWIFT’s recommended security practices.
On behalf of the Monetary Authority of Singapore, Singapore’s Central Bank requested that their banks’ respective IT systems maintain a high level of security, given the recent SWIFT cyberheist.
But what’s even more notable about the Singapore finance realm and their response to the attacks is the memo they issued to the SWIFT society itself: a formal invitation (sent on behalf of the Association of Banks in Singapore (ABS) for a meeting in June that will discuss the most recent cyber attacks on banks in Bangladesh and Vietnam.
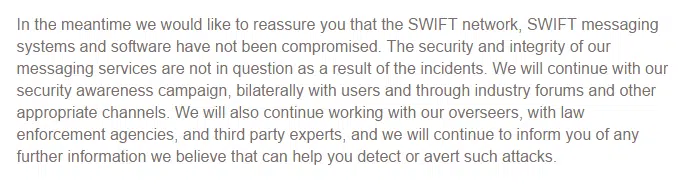
As shown in this excerpt, (taken from SWIFT’s Customer Communication Memo, issued on 13 May 2016), SWIFT has (continuously) stated that their clients’ credentials were not compromised in the recent cyber attacks, neither in the successful Bangladesh Bank theft nor in the attempted attack at Vietnam’s TPBank.
That being said, last year, when over $12 million were stolen from Banco del Austro (BDA), SWIFT spokesperson, Natasha De Teran, reported that the firm were not informed of the attack and theft, and therefore were unable to ‘inform the wider community’ about the hack.
“The planned meeting between ABS and SWIFT (for June in Singapore), may allow for a conducive dialogue between the two — one which would put (positive) pressure on SWIFT to improve what they have previously lacked in their cybersecurity strategy: an up-to-par threat model, which translates to better authentication and integrity controls, as well as a transparent accountability and information sharing approach when there is a breach”, says Itay Yanovski, Founder and SVP Strategy at CyberInt.
All that being said, despite their assurance that “no SWIFT messaging systems or softwares have been compromised”, on Friday (20 May), SWIFT informed clients that “it is essential that you share critical security information related to SWIFT with us.”
Scrutinizing response measures have also been initiated, such as (official) information-access requests, submitted by both Tom Carper (U.S Homeland Security and Affairs) and by Bank of Bangladesh itself, both of whom were direct victims of the first (discovered) attack, and are now requesting investigative information and assistance from the SWIFT Society itself.
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


