


Last weekend, top-tier publishers such as NYTimes and the BBC UK’s sites (and 11 other sites) started serving a new type of content: malicious online ads to every visitor.
This time, we’re dealing with ‘Ransomware delivered by Angler Exploit Kit’.
The hackers involved got a good run for their money. The damage was heavy, yet the costs were as light as a feather.
The hackers acquired the expired domains of small advertising companies, which was their backdoor to get past malware blockers. The malicious traffic was identified as legitimate and verified, and could, therefore bypass the blockers freely.
Once the cyber criminals infused the online ads into NYTimes and BBC’s sites, the innocent ad-clicking users were redirected to malware-hosting servers, where the Angler exploit kit was waiting for them.
The victim’s computer was officially hacked, and a ransomware trojan (CryptoLocker) encrypted the hard drive. The only way the publishers’ viewers and subscribers could get their computer system back was to pay up a ransom fee in bitcoins.
Ransomware costs companies big bucks and big damage. And this cyber risk only getting more popular; hackers can’t get enough of it. As far as payload methods go, “it’s a quick payout with little overhead”, says Malwarebytes Security Researcher, Jerome Segura.
The business value in online advertising and in social media doesn’t need much convincing. Viral content is considered the best of its kind; the more retweets and followers the better; the more clicks a PPC campaign caught, the higher its success. This time, we want the biggest traffic jam we can get our hands on.
But what goes around comes around — and that’s almost never a good sign.
How much traffic are we talking?
Let’s look at two of the top online news publishers;
These are unusually high traffic rankings.
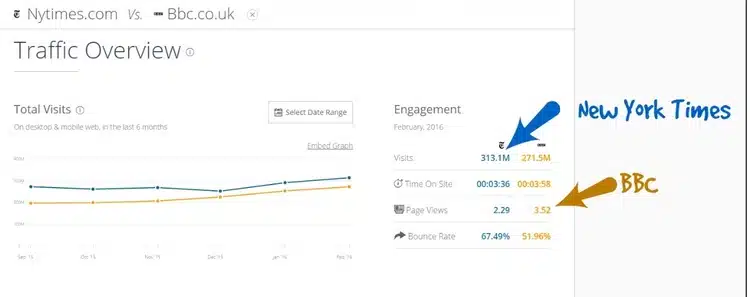
(taken from SimilarWeb.com)
With 313.1M visiting the NYTimes website in the month of February, means 10,793,103 views per day. If every (unique) monthly view involved one malicious ad, that means 10,793,103 devices or accounts would be affected per day.
What’s more, if even one of these ads carried malicious content, the amount of people (and their devices) threatened by this cyber risk multiplies by the minute.
Neither publisher nor advertising company intended for this kind of exposure. Companies and agencies who advertise on the NYTimes site pay:
Ads start at an $8.00 CPM (cost per thousand impressions) and increase by $2.50 with each additional layer of targeting ($10.50 CPM to target California residents, for example).
But if the NYT or their customers knew the level of cyber risk involved with the malware that targets their ads, no profit or revenue would be worth the damage at stake.
Investing money in online ad campaigns is not only a heavy financial investment, it’s a commitment. Companies can’t always predict how many impressions their ads will generate, but once they decide to fork over the cash for the cause, they’ve embraced the bang for the buck needed to grow their audience.
As much as these traffic flows are worth the prices involved, the more money spent, the greater the cyber risk.
Whether your average online user can spot it or not, the growing numbers of fake social profiles and accounts, whether on Twitter, LinkedIn, Facebook, etc., are ever-present in our social media ecosystem.
The boundaries within social media are often too blurry to hold back these identity thefts from our line of vision.
The idea behind a social network is to widen your horizons; Why reject a friend request? Why not gain another Twitter follower? What have you got to lose?
Your security.
Hackers have gotten quite good at creating fake accounts that claim they are a specific business professional, retail company, etc., by simply gathering information from online interactions that seem perfectly harmless at the surface.
Once you let a hacker into your network, you’re sharing personal information with him, without knowing that he can’t be trusted to behave.
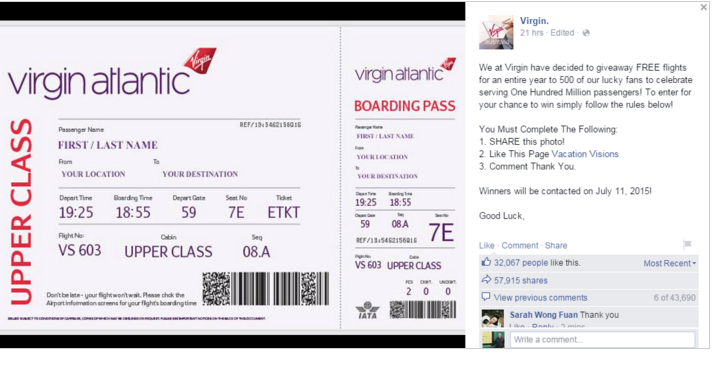
Whoever managed to forge a Virgin Atlantic campaign for free tickets, did it quite well. With 32,076 ‘Likes’, there were certainly plenty of Facebook followers that assumed the campaign to be true.
But again, would Virgin customers really want to win a free flight if they knew it meant their payment credentials would be stolen?
Probably not.
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


