Dark Web monitoring strategies need to evolve. Gone are the days when the Dark Web was a haven mostly only for people who wanted to post illicit content anonymously. Today, the Dark Web has expanded into a hotbed for threat actors, who use Dark Web forums and apps to distribute malware and sell the fruits of their hacking activities.
The Dark Web has been around at least since 2000, when U.S. Navy efforts to create an anonymous Internet space for espionage purposes gave birth to the first Dark Web communities.
In its early years, the Dark Web was a relatively small and uncomplicated space. The introduction of cryptocurrency, which debuted when Bitcoin launched in early 2009 led to a significant increase in anonymous business transactions both on the Dark Web and elsewhere.
The Dark Web combined with crypto created the perfect environment for threat actors to operate in. They could use the Dark Web as a base for planning their operations, then use it to sell the data they exfiltrated when they completed a Dark Web data breach.
The distribution of stolen data on the Dark Web “happens a lot,” according to Bruce Schneier of Harvard’s Berkman Center for Internet and Society. “There’s a big data breach, and then someone will try the same username and password at a bank, at Google.”
The shift of cybercrime to the Dark Web also reflects increased awareness over the past decade of how government agencies can track people on the conventional Web – a fact underlined by the Snowden revelations of 2013 – this gave threat actors added incentive to move their operations to the Dark Web.
Fast forward to today and the Dark Web has become a massive, dynamic space. Analysts estimate that about $1.5 billion changed hands on the Dark Web in 2022, and that around 2.5 million people visit Dark Web sites or apps every day.
Key recent trends include:
Increased use of the Dark Web to share not just items like stolen passports or to buy and sell illegal drugs, but also to sell malware and PII stolen by threat actors. This change reflects increased reliance on the Dark Web by threat actors. “The Dark Web now has hundreds of thriving marketplaces where a wide variety of professional ransomware products and services can be had at a variety of price points,” as cybersecurity writer Jai Vijayan notes.
The shift to DeepWeb forums. In the past the majority of criminal activity occurred on the DarkWeb, but in recent years there has been a significant shift to Deep Web forums such as BreachForums, etc. Users can access these forums with a regular internet browser, such as Chrome, and VPNs are supposed to hide the threat actor’s true IP address from deep web applications, such as closed threat actor forums or marketplaces. This is meant to provide enough of a veil for them to keep their true identity concealed without needing to use Tor. But there are many cases of VPNs not providing the necessary anonymity, such as when NordVPN was hacked and when SuperVPN was hacked.
Apps help to protect users’ anonymity because they can prevent some tracking techniques that are possible within browsers. Threat actors can purchase a prepaid sim or use a virtual number to remain anonymous. There are several reasons for this shift:
New Dark Web forums appear on a regular basis as part of threat actors’ efforts to circumvent the closure of existing forums (like BreachForums and Genesis) by government authorities. Whereas in the past you might see one or two new forums appear in a year, over the past 12 months we have seen more than 4 leading forums appear/disappear. First there was RaidForums, then BreachForums, then Genesis Market and now ExposedVC Forum (Although Genesis Market is still live and up to date on Tor).
There has been a growth in the internationalization of the Dark Web, specifically more movement from the US to Chinese Dark Web Forums. The FBI closures have also triggered a migration to forums outside of the US for many threat actors.
Information security experts generally agree that the rise of ChatGPT will lead to an increase in the volume of malware being exchanged on the deep and dark web. ChatGPT has the potential to speed up the malware production process, increasing the amount of threat actor activity that must be tracked on the DarkWeb.
Now organizations need to monitor what is being said and sold about their vendors on the Dark Web too. With the boom in vendors and suppliers over the past 5 years, the supply chain is becoming many organizations weak point. Now, they not only need to monitor what is being said about them, they also need to know if their vendors are being targeted too.

All of these usage changes have led to two main challenges. They are only exacerbated by the fact that many cyber teams are currently stretched thin due to the economic slowdown.
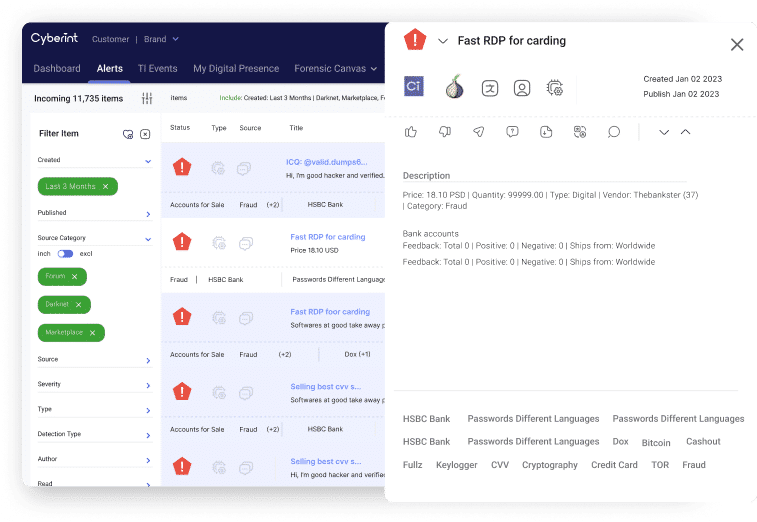
Despite the above challenge and the emerging trends, monitoring the Dark and Deep Web remains critical. Since the Dark/Deep Web is the place threat actors both plan breaches and sell data, you need to monitor Dark Web forums and apps if you want to stay ahead of attackers
Effective Dark Web monitoring as of 2024 requires the ability to do the following:
When you do these things, you turn the Dark Web into an asset for your cybersecurity strategy, not for threat actors. If you can gain visibility into the Dark Web and use it as a source of insight into cyber threats, it becomes a great way of anticipating emerging threats.
At Cyberint, we know a thing or two about Dark Web monitoring, and we want to help businesses incorporate it into their cybersecurity strategies. Learn more by downloading our free eBook, The Big Book of Deep and Dark Web.
©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start