


Over the past decade, cryptocurrency has significantly disrupted the economic and business landscape. Its popularity has soared, driven by the promise of anonymous transactions and the potential for substantial returns on investment. However, the crypto market’s vulnerabilities, coupled with limited government oversight, have provided fertile ground for cybercrime to flourish.
Major platforms like Ethereum and Bitcoin have been entangled in crypto scams, leading to the misappropriation of $3.8 billion in cryptocurrency in 2022 alone.
Crypto scammers exhibit remarkable creativity in luring victims and extracting personal information. Consequently, many crypto scams involve impersonation and a repertoire of carefully concocted lies tailored to specific victims.
Discussions between threat actors in underground forums about cryptocurrency cover diverse topics. This report looks at how threat actors offer their services, seek partners, and share insights on employing social engineering and hacking tools to attack victims and steal their cryptocurrency assets.
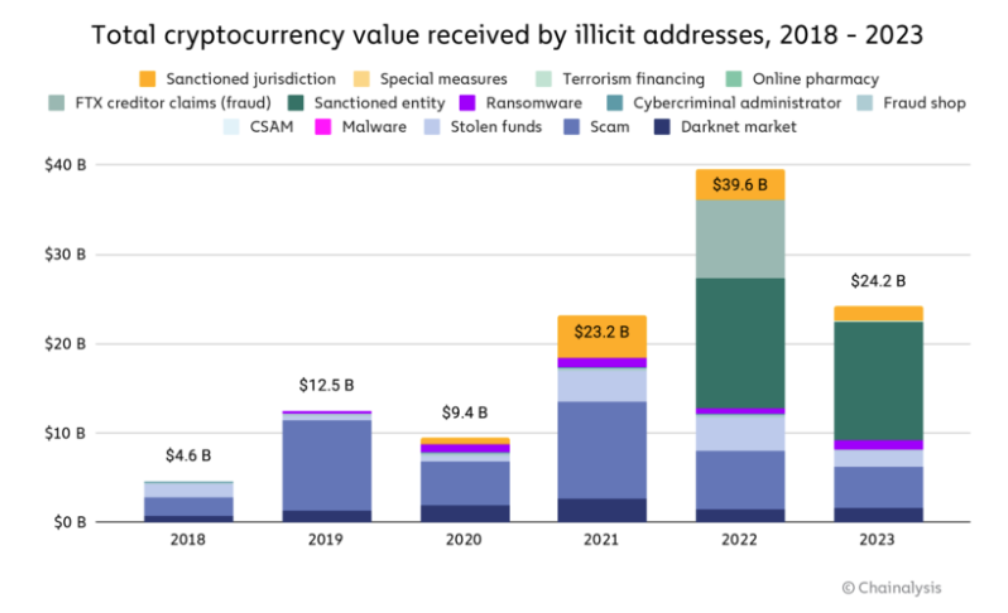
According to the Chainanalysis report, 2023 saw a considerable decline in the value received by illicit cryptocurrency addresses, totaling $24.2 billion. It is imperative to note that these figures represent conservative estimates, relying on identified inflows to illicit addresses as of today. Anticipated future revisions will likely result in higher totals, reflecting the identification of additional illicit addresses and the inclusion of their historical activities.
For context, the Crypto Crime Report from 2022 estimated $20.6 billion worth of illicit transaction volume. A year later, the updated estimate for 2022 stands at $39.6 billion, driven by the discovery of previously unknown, highly active addresses hosted by sanctioned services and the inclusion of transaction volume associated with services in sanctioned jurisdictions to illicit totals.
What unfolds when threat actors employ social engineering techniques to target crypto assets, potentially infiltrating the organization’s internal network through malware?
In November 2023, suspected North Korean hackers affiliated with the Lazarus Group were observed directing their efforts toward blockchain engineers engaged in cryptocurrency exchange platforms. Their weapon of choice was a newly discovered macOS malware named Kandykorn.
This intrusion leveraged a blend of both custom and open-source capabilities to secure initial access and facilitate post-exploitation on macOS systems.
The attack unfolded as the assailants posed as members of the blockchain engineering community on a public Discord server, and successfully persuaded victims to download and unpack a ZIP archive containing malicious code. The victims, under the impression that they were installing an arbitrage bot to capitalize on cryptocurrency rate differentials, unwittingly became part of the malware scheme.
In March 2022, the Ronin Network publicly disclosed that they had fallen prey to a social engineering scam involving a senior engineer downloading a PDF file embedded with spyware.
This enabled the attacker to gain control over four of the network’s private validator keys, leading to the theft of over 173,000 Ethereum valued at $595 million at that time, in addition to another $25.5 million from a bank account.
Ronin Network, a blockchain platform developed by Sky Mavis for the online game Axie Infinity, confirmed that its DAO validator nodes had been compromised, resulting in the siphoning of funds through two transactions. The U.S. Treasury Department later attributed the attack to North Korea’s Lazarus group. Subsequently, Ronin Network relaunched three months later and compensated those affected.
2024 began with significant volatility, notably impacting Bitcoin, the leading global cryptocurrency. In a span of just 15 minutes, on January 9 the price of Bitcoin surged to $48,000, only to subsequently fall to $45,000. The cause: Malicious actors infiltrated the X account of the US Securities and Exchange Commission (SEC) and disseminated a message, ostensibly from SEC Chairman Gary Gensler, falsely proclaiming approval for a Bitcoin spot exchange-traded fund. Gensler had to use his account to refute the eagerly awaited news, and revealed it as a hoax.
Just two days later, the SEC officially confirmed the approval of Bitcoin-linked exchange-traded funds, genuinely heralding the facilitation of Bitcoin investment without the necessity to acquire the cryptocurrency itself, akin to traditional commodities like gold or oil. Intriguingly, in contrast to the false announcement’s impact, the crypto’s price exhibited minimal fluctuations, remaining stable at around $46,000.
To underscore this point, we delved into underground forums to assess the prevalence of discussions about cryptocurrency scams and their associated components, such as phishing, malware, drainers, and more, as illustrated in the chart below.
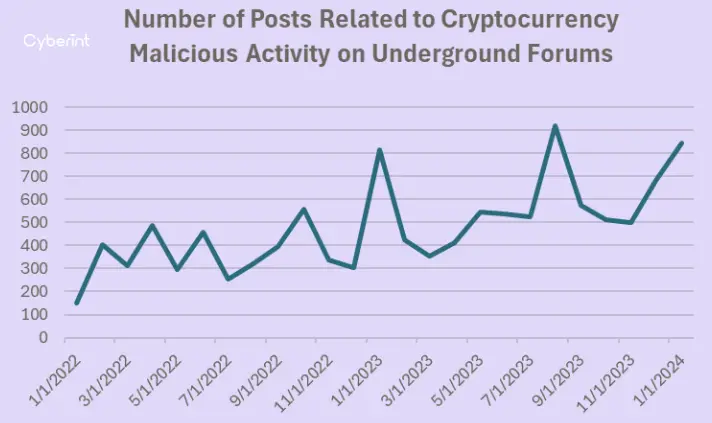
Despite a notable increase in the number of posts reaching new peaks in 2023 and continuing a steady ascent into 2024, both cryptocurrency scams and hacking revenue experienced significant declines in 2023, plummeting by 29.2% and 54.3%, respectively. This downturn may be attributed to the enhanced capabilities of security vendors who efficiently combat various techniques and tools, adapting to the evolving landscape. Nevertheless, the surge in discussions surrounding these topics indicates that threat actors persist in devising novel ways and tactics to scam, harm, and steal from cryptocurrency holders and organizations. The escalating discourse suggests that the storm is yet to abate.
In underground forums and marketplaces, threat actors engage in the exchange of insights, strategies, and techniques associated with cryptocurrency scams. This includes discussions on successful tactics, vulnerabilities, and emerging trends in the cryptocurrency domain. An example is the sharing of Guides and Tutorials between threat actor communities, aimed at enhancing knowledge in specific areas while concurrently building a reputation within the community.
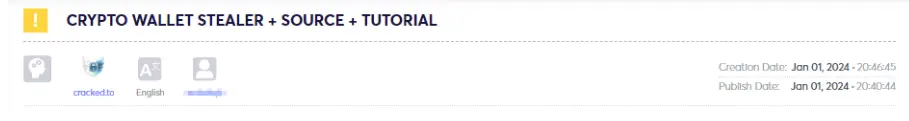
Educational Content/Guides and Tutorials: Forums often host guides and tutorials that offer step-by-step instructions for executing various types of cryptocurrency scams. This educational content serves as a means for less experienced individuals to enter the realm of cybercrime, ranging from malware builder tutorials (depicted in figures 3 and 4) to eBooks providing guidance on future cryptocurrency scams for beginners (depicted in figure 5).
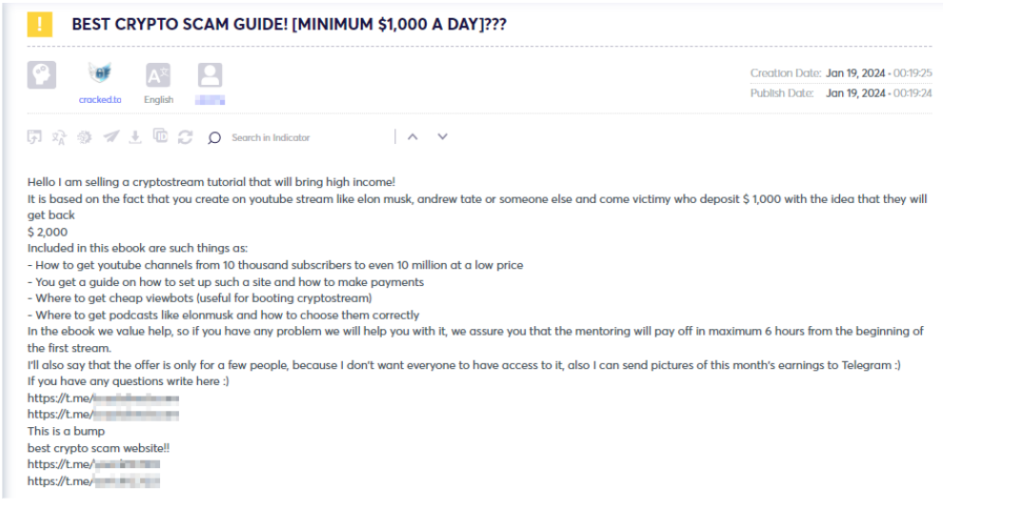
While certain threat actors opt for solitary endeavors, larger-scale operations often necessitate collaboration involving diverse specializations. Typically, these collaborations involve the sharing of key details such as the operation’s main title, the specific expertise sought, a brief overview of the ongoing activities, and details about compensation.
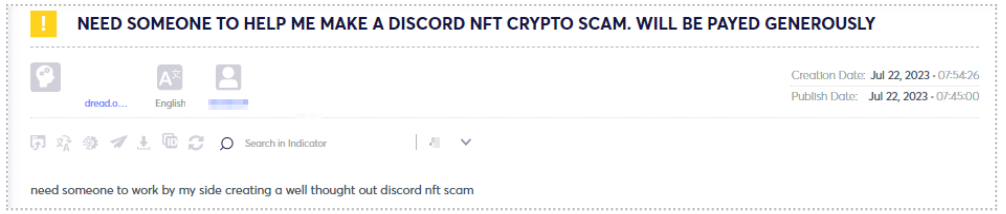
In contrast, some threat actors choose not to disclose information about the project, as depicted in the figure below.
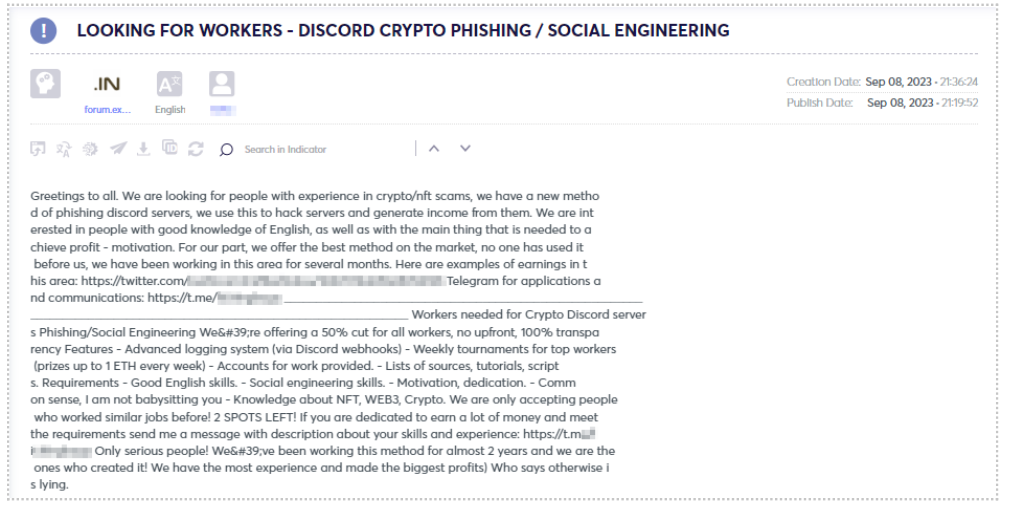
Others provide extensive details about the project’s status, its current position, and specific expectations of those opting to join (see Figures 7 and 8). According to the threat actor, they devised a novel phishing method utilizing Discord servers. Moreover, they actively seek individuals who are proficient in English and highly motivated. Compensation is set at a 50% share of all profits, a common arrangement in this domain, with no upfront payment required.
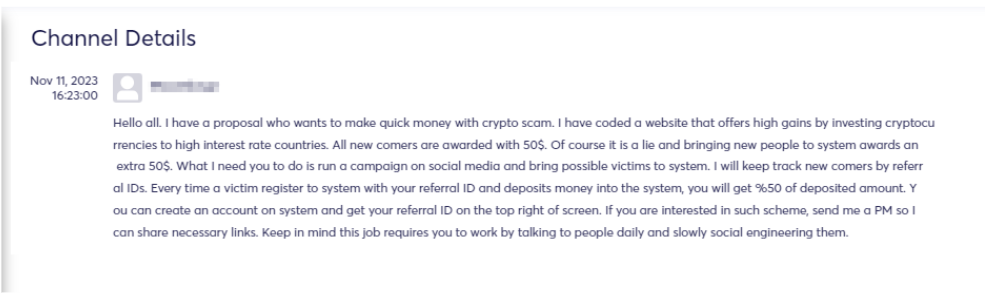
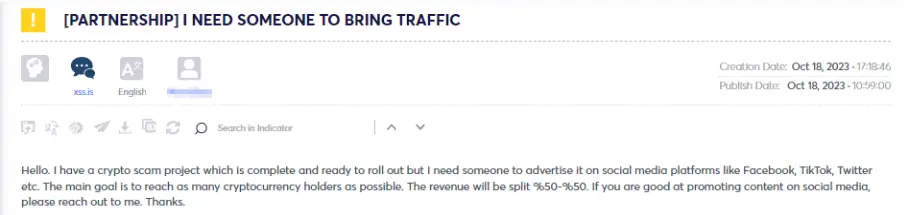
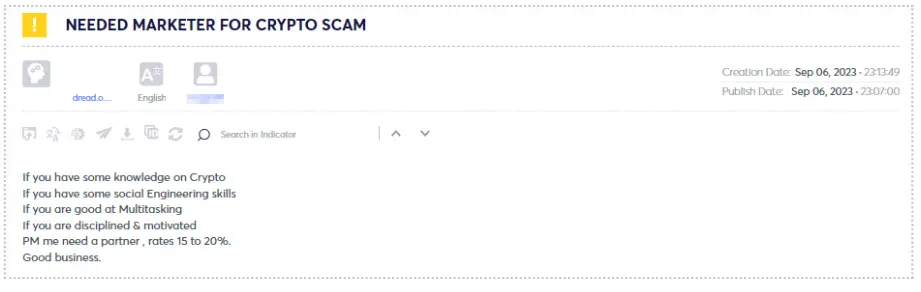
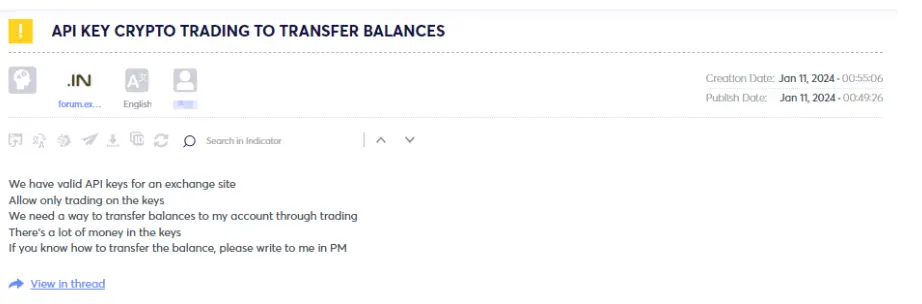
As observed, various collaborations exist among threat actors, ranging from enlisting marketers (see figures 9 & 10) who can drive traffic through social media platforms like Facebook, TikTok, Twitter, and others to engaging in more technical and sophisticated tasks like transferring balances via API keys on different exchange sites (see figure 12).
Underground forums and chat platforms can function as marketplaces where phishing kits, tools, and services are bought and sold. This facilitates the engagement of less technically proficient individuals in conducting phishing attacks.
Phishing services entail developing and disseminating deceptive schemes, such as counterfeit websites or emails, designed to deceive individuals into disclosing sensitive information, including private keys or login credentials. These services often employ social engineering techniques to replicate authentic cryptocurrency platforms or communication channels. Victims are enticed into divulging their private information, which is subsequently exploited by malicious actors. The primary goal of phishing services is to amass sensitive information that can be utilized for unauthorized access to cryptocurrency accounts or other fraudulent activities.
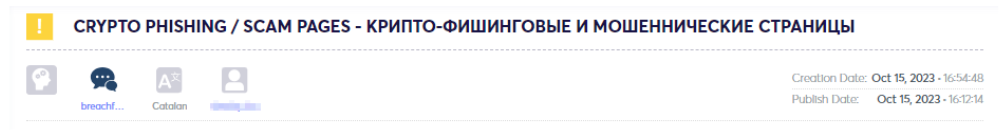
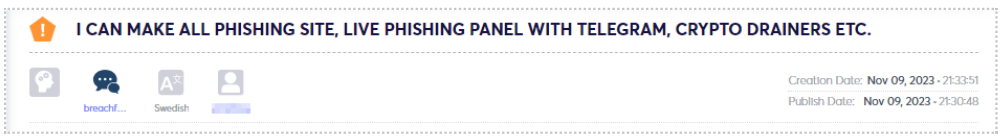
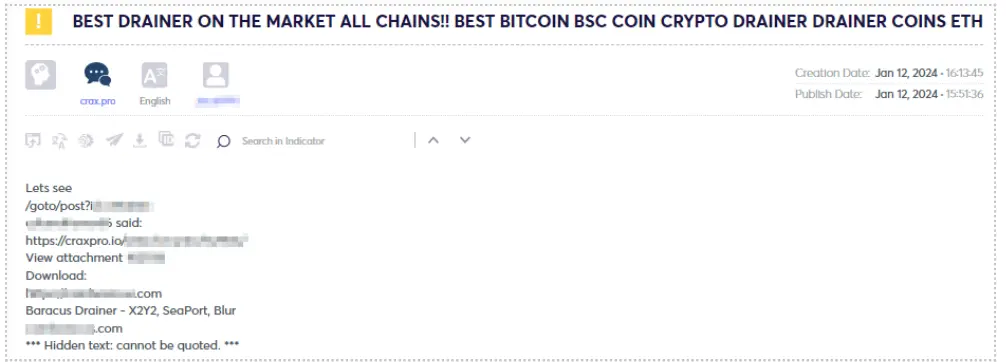
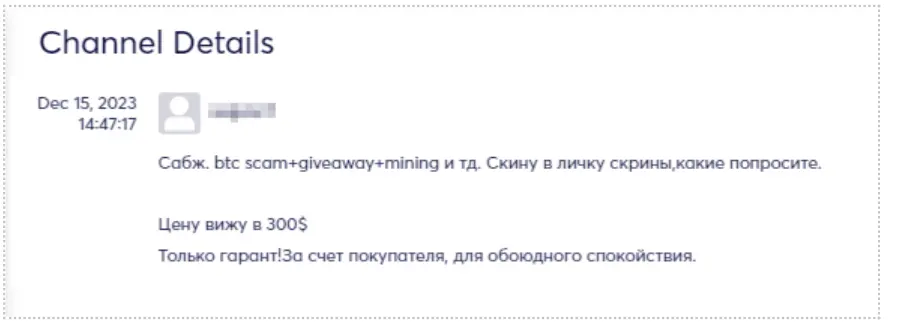
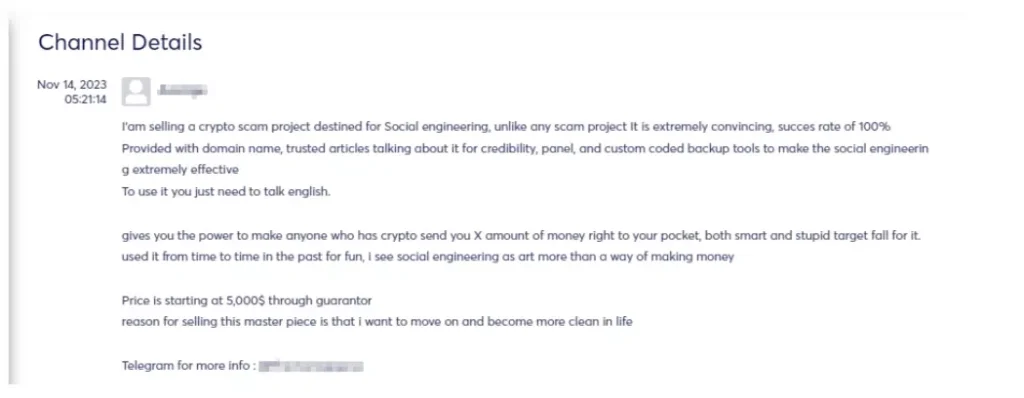
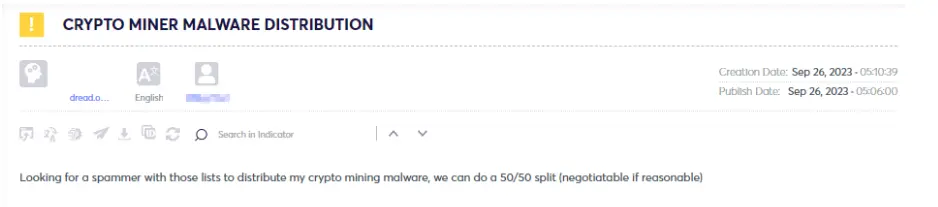
In recent years, there has been a proliferation of various malware and attack methodologies orchestrated by threat actors targeting both cryptocurrency entities and private users. Drainers, whether individual actors or groups, specialize in exploiting vulnerabilities on cryptocurrency platforms, exchanges, or wallets to illicitly siphon funds from unsuspecting victims. Their tactics encompass a range of strategies, including capitalizing on security protocol weaknesses, engaging in social engineering ploys, or utilizing malware to gain unauthorized entry into crypto accounts.
The primary objective of drainers is to deplete cryptocurrency holdings from their targeted accounts, invariably resulting in financial losses for the victims. These actors often collaborate on underground forums to share insights, tools, and techniques related to the latest vulnerabilities in cryptocurrency systems.
Following is a more detailed breakdown:
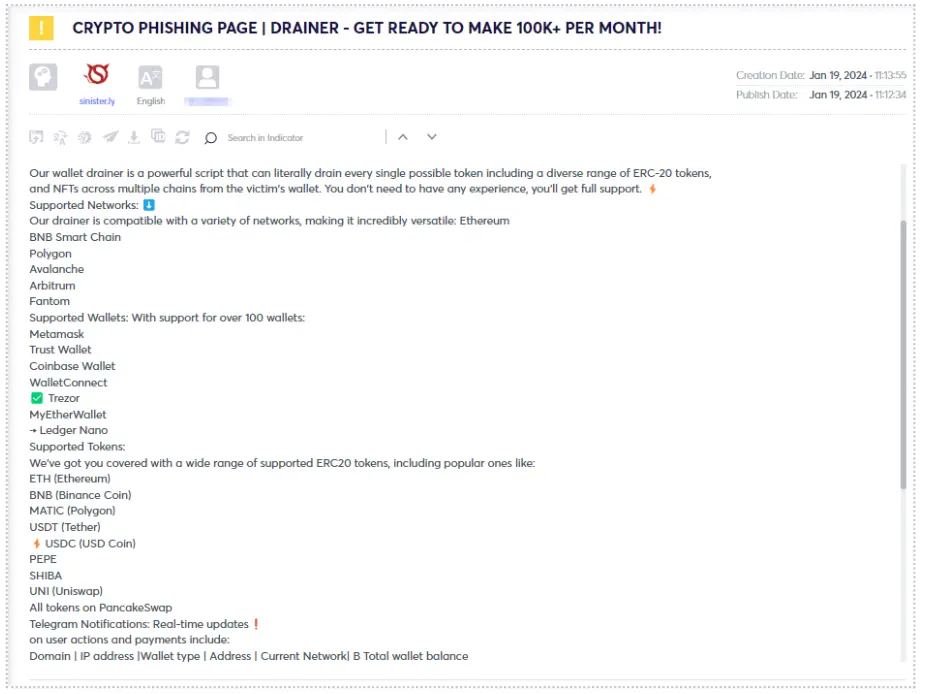
In the example above, a threat actor is selling prepared script of a wallet drainer, which works on multiple crypto wallets (over 100) such as: Coinbase, MetaMask, Trust Wallet and others.
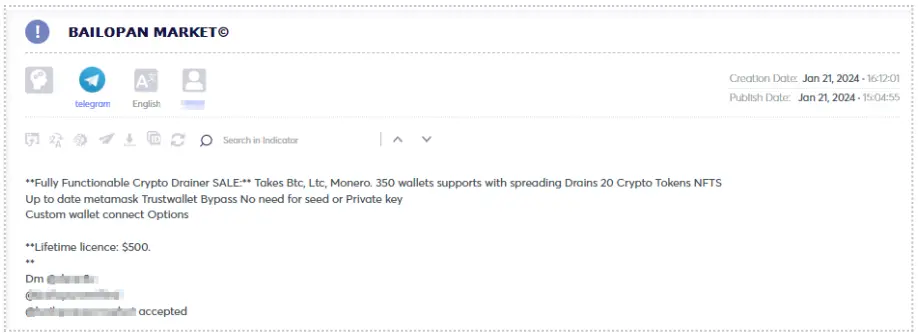
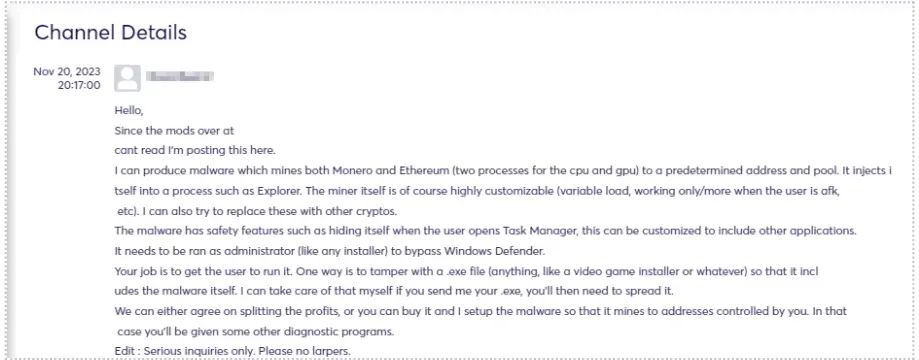
The advent of this type of malware has transformed the landscape of cryptocurrency fraud, presenting an additional threat to investors who may face substantial losses if they fall prey to phishing schemes. The financial repercussions can escalate into the millions.
Illustrating the detrimental impact of drainers is the case of the “Inferno Drainer.” This sophisticated phishing campaign, known as “Inferno Drainer,” successfully drained over $80 million in cryptocurrency from 137,000 unsuspecting victims over the period of a year. The perpetrators employed an impersonation strategy, utilizing 100 different cryptocurrency brands. Throughout the campaign, which spanned from November 2022 to November 2023, the attackers hosted phishing pages across more than 16,000 distinct domains, which was ultimately disrupted at the campaign’s conclusion.
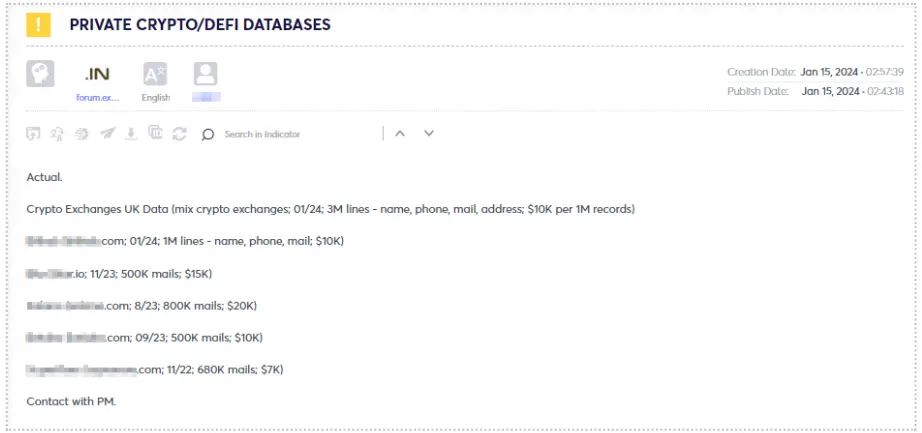
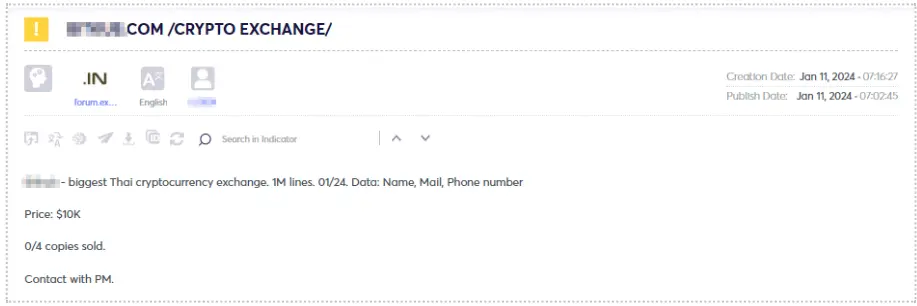
Threat actors distribute combo lists and databases containing information about cryptocurrency users sourced from exchange sites, gambling platforms, and other outlets, posing risks to individual users, the broader cryptocurrency community, and affiliated organizations.
This data may originate from various sources, including data breaches, the compilation of stealer logs, phishing campaigns, among others. What makes this information so valuable to threat actors? In the aftermath of a data breach, credentials obtained from such sources often prove outdated and invalid, particularly if the breached company has mandated password changes for its users.
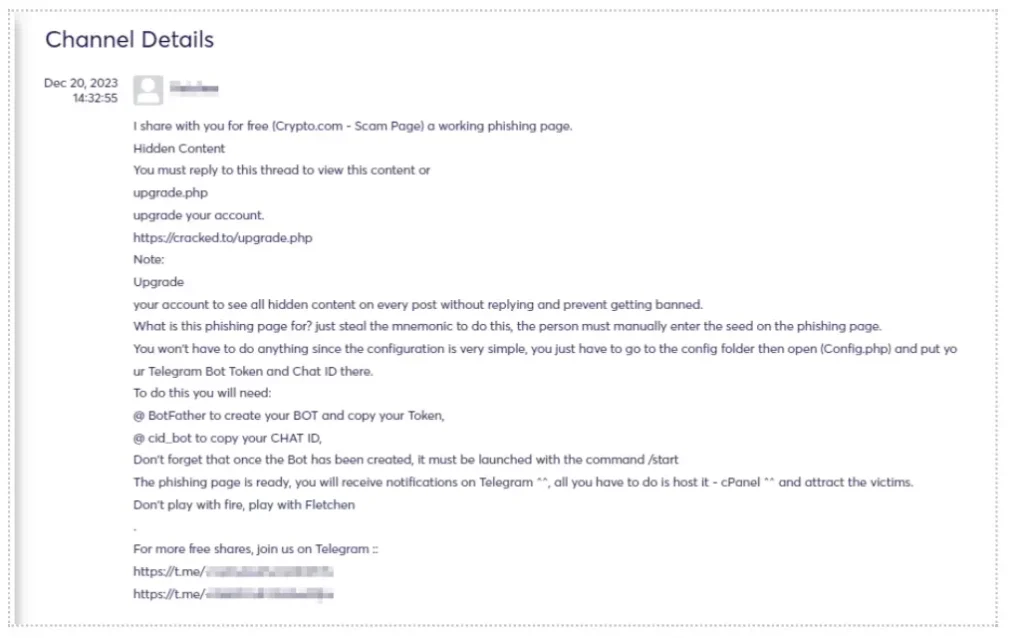
A noteworthy indicator is when threat actors freely share this information, potentially aiming to enhance their reputation and establish new connections within the community (see figure).
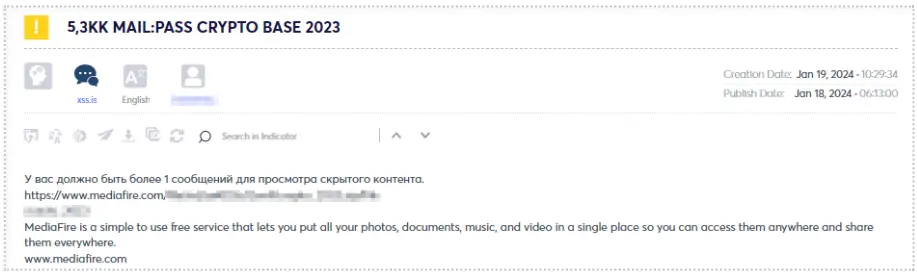
In the context of a recent data breach or the acquisition of stealer logs, these datasets are typically of premium quality. Stealer logs originate from malware and capture the most recent, valid, and crucial personal information directly from a compromised machine’s browser and autofill data – a repository for login credentials on various websites, including cryptocurrency platforms in our case.
These databases are frequently available for purchase, as illustrated in the examples below. When the price is relatively low, it might indicate potentially non-useful data, while on the other hand, a high price could suggest valuable information.
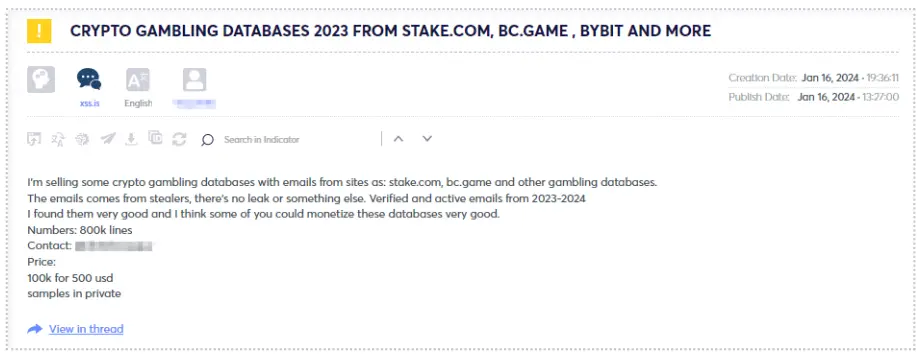
Following our examination of cryptocurrency through the lens of threat actors’ perspectives, let’s delve into instances of prevalent scam types and explore protective measures to safeguard yourself from them.
A Bitcoin (BTC) transaction is a recorded entry on the blockchain, encompassing details such as sender and recipient wallet addresses, the transferred Bitcoin amount, confirmations, and additional information. This transaction undergoes validation and inclusion in the blockchain, serving as the foundational element of the Bitcoin blockchain – an avenue for transferring value between wallets.
An unconfirmed Bitcoin transaction refers to an operation broadcast to the network but not yet included in a block. Until picked up by miners and added to a block, these pending transactions are held in a mempool (memory pool).
The mempool acts as a queue for operations awaiting validation by miners. Once miners select, validate, and incorporate the transaction into a block, it attains confirmation status, becoming an immutable part of the blockchain. Scammers exploit unconfirmed transactions using various social engineering techniques to deceive users into accepting “fake BTC” for services, investments, or products, ultimately evading payment. This prevalent scam impacts users globally on a daily basis.
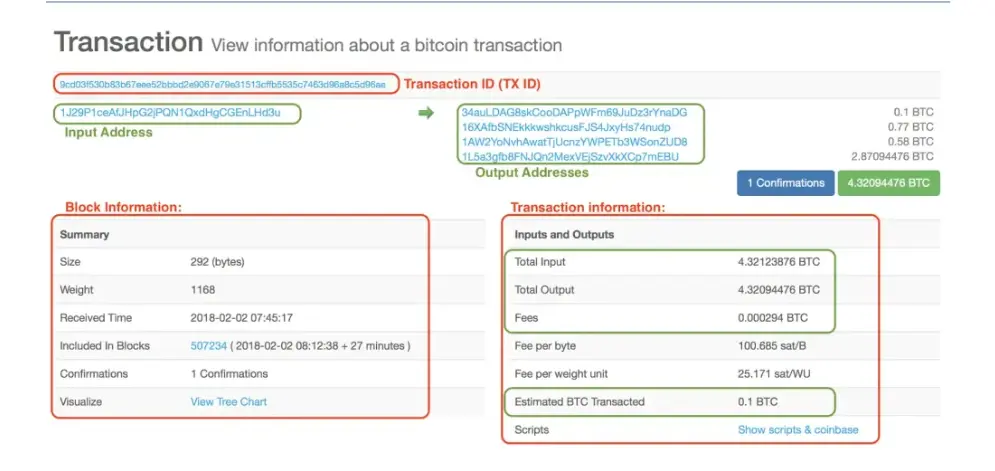
Replace-by-fee (RBF) is a feature that allows users to replace an unconfirmed transaction with a version offering a higher transaction fee, a process that can be repeated multiple times during the unconfirmed stage.
RBF provides the flexibility to gradually increase the fee until the transaction is accepted into a block. In cases where transaction confirmation becomes more urgent than anticipated, RBF enables the sender to expedite the transaction for inclusion in the next block.
To safeguard against RBF scams, it is crucial to verify cryptocurrency receipts by checking the transaction status. A confirmed transaction should display “CONFIRMED” in the app. Another verification method involves checking the transaction on a “block explorer.” If the transaction is not found, it indicates that it was never broadcast to the blockchain network.
Additionally, users should follow specific steps before engaging in cryptocurrency transactions with others:
Multi-Signature Wallets
To mitigate risks tied to irreversible Bitcoin transactions, users can opt for multi-signature wallets. These wallets necessitate more than one signature or private key for transaction authorization, introducing an added layer of security to protect against potential hacks or thefts.
While multi-signature wallets enhance security, they may present increased complexity, particularly for crypto beginners.
Reputable exchanges play a pivotal role in minimizing risks associated with irreversible Bitcoin transactions. Key considerations when selecting an exchange include:
Choosing a reputable exchange diminishes the risk of cryptocurrency loss due to fraud or security breaches, ensuring a secure and efficient trading experience with competitive pricing.
The convergence of artificial intelligence (AI), deepfakes, and cryptocurrency forms a potentially disastrous concoction when falling into the wrong hands. Cybercriminals exploit AI to generate deepfakes featuring recognizable figures and celebrities, commandeering YouTube channels and executing classic “Double Your Crypto” scams.
Until a few months ago, around October 2023, criminals primarily used looped videos of prominent figures in crypto conferences or celebrities discussing the crypto world. Overlaid on these loops were malicious links, QR codes, and other elements designed to deceive users into surrendering their crypto, enticing them with the illusionary promise of doubling their funds.
However, recent advancements in AI have elevated the threat, with criminals now utilizing deepfakes to impersonate well-known public figures. For instance, a deepfake video of MicroStrategy’s former CEO emerged, encouraging the community to partake in a fraudulent giveaway by scanning a QR code and following instructions on a deceptive website.
Despite the complexity of the technologies employed by criminals, this scam ultimately relies on a high degree of human gullibility. Users can safeguard themselves by scrutinizing videos with click-bait titles that lure investments in crypto or promise substantial returns in Bitcoin. It is crucial to avoid scanning the QR codes in videos that promote free crypto giveaways. A healthy dose of skepticism is warranted when encountering offers that seem too good to be true.
Scammers frequently establish fake cryptocurrency trading platforms or counterfeit versions of official crypto wallets to deceive unsuspecting victims. These fraudulent websites often adopt domain names that closely resemble legitimate sites, making it challenging to distinguish between them. Fake crypto sites typically operate in one of two modes:
Crypto phishing scams specifically target information linked to online wallets, focusing on obtaining private keys required to access funds. Users are urged to exercise caution and vigilance, and recognize warning signs such as promises of guaranteed returns, the absence of a whitepaper, excessive marketing efforts, undisclosed team members, and offers of free money in cash or cryptocurrency.
The primary objective of engaging in money laundering in the realm of cryptocurrency is to transfer funds to addresses that obscure their original criminal source, ultimately facilitating their conversion into cash – typically through cryptocurrency exchanges. The existence of such avenues is crucial for incentivizing criminal activities involving cryptocurrency.
Money laundering in the cryptocurrency space commonly revolves around two categories of on-chain entities and services:
According to Chainalysis, illicit addresses transmitted nearly $23.8 billion worth of cryptocurrency in 2022, reflecting a 68.0% increase from 2021. Mainstream centralized exchanges were the predominant recipients of illicit cryptocurrency, accounting for just under half of all funds sent from illicit addresses. This is noteworthy not only because such exchanges typically implement compliance measures to report suspicious activities and take corrective actions against users, but also because these exchanges serve as fiat off-ramps, facilitating the conversion of illicit cryptocurrency into cash.
Another trend observed in money laundering involves the rise of underground services, which are not as publicly accessible or well-known as conventional mixers. These services are often accessible only through private messaging apps or the Tor browser, and are typically advertised on darknet forums.
Remedial Actions if Victimized by a Crypto Scam
Falling prey to a cryptocurrency scam can be devastating, necessitating swift action if payments are made or personal information is disclosed.
Victims are advised to contact their bank immediately, particularly if payments were executed through debit/credit cards, bank transfers, or personal details were shared.
Changing usernames and passwords across all platforms is crucial, as compromised details are often sold to other criminals.
Social media crypto scams can be reported to the relevant platform, and fraud incidents can be reported to the appropriate regulatory bodies based on jurisdiction, such as the Federal Trade Commission in the US.
Cyberint, the Impactful Intelligence company, reduces risk by helping organizations detect and mitigate external cyber threats before they have an adverse impact. The Cyberint Argos platform’s patented technology provides superior visibility through continuous discovery of the evolving attack surface, combined with the automated collection and analysis of vast quantities of intelligence from across the open, deep and dark web. A team of global military-grade cybersecurity experts work alongside customers to rapidly detect, investigate, and disrupt relevant threats – before they have the chance to develop into major incidents.
Global customers, including Fortune 500 leaders across all major market verticals, rely on Cyberint to protect themselves from an array of external risks, including vulnerabilities, misconfigurations, phishing, impersonation attacks, malware infections, exposed credentials, data leaks, fraud, and 3rd party risks.
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


