


On October 7th, 2023 “Hamas”, a Palestinian terror organization, launched an attack on Israeli residencies surrounding the Gaza Strip. Hamas named its operation “Toufan Al-Aqsa” (in Arabic: األقىص طوفان), meaning “The Flood of Al-Aqsa”.
Inspired by Hamas’ actions and in response to Israeli retaliation against Hamas in Gaza, multiple pro-Palestinian cyber hacktivists were formed and commenced attacks on Israeli infrastructures, companies, and organizations.
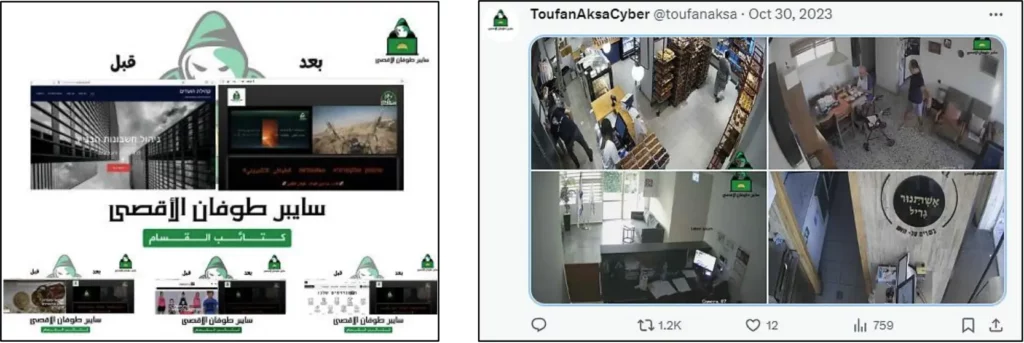
One of the newly emerged hacking groups, known as “Cyber Toufan Al-Aqsa”. The group claims responsibility for different attacks such as website defacement, accessing institutions, businesses, and private people’s homes, security cameras, and data breaches.
This blog is focused on the activity of the Cyber Toufan hacking group, aiming to shed light on the nature of the leaked files and their origin. Cyberint investigated the issue using the Argos Edge™ platform (including our Threat Intelligence module covering thousands of dark, deep, and open web sources), open-source intelligence (OSINT) tools and techniques.
In light of the attack conducted by the Hamas terror organization on October 7th, a recent cyber hacktivist group has emerged, operating under the alias “Cyber Toufan Al-Aqsa”.
The group was initially observed on social media platforms at the end of October. To date, the
group is mainly active on Twitter and Telegram channels. Their known accounts are as follows:
X Accounts:
Telegram Channel:
Active Telegram Channels:
Previous/banned Telegram Channel –

Since the establishment of the group, they claimed responsibility for alleged attacks on Israeli websites and security cameras.
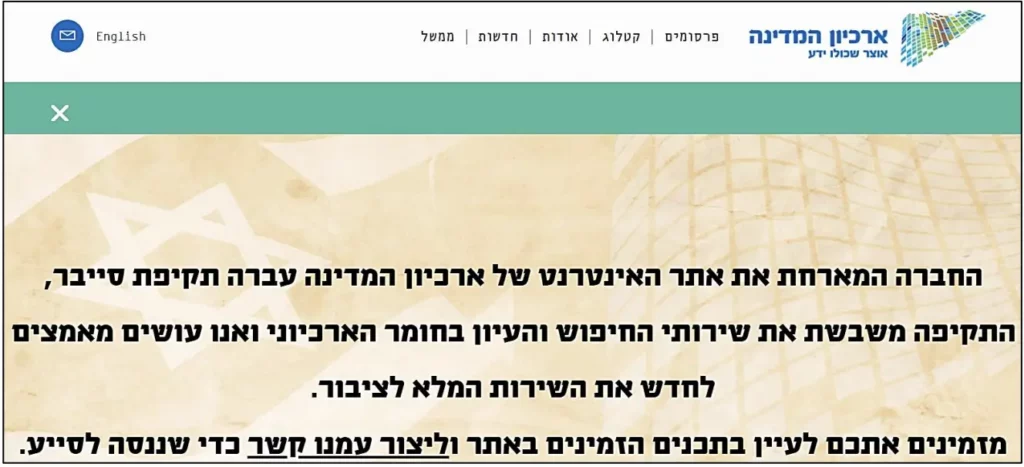
Another notable attack was against the Israeli state archive website (www.archive.gov.il). The group claimed not only to breach into the website’s servers but to use Ransom TTPs and wipe their servers and backups as well. Attempts to access the website show a cyber attack notice(figure 4).
On November 16th, Cyber Toufan announced that they had launched a massive cyber-attack on an Israeli company, later identified as Signature-IT, as part of their operation against Israel. Signature-IT, an Israeli provider of e-commerce and website hosting services, is considered one of the largest in the industry, with clients including government offices, organizations, and major companies such as Ice, Auto Depot, Home Center, Asam, Kravitz, Grafiti, Iscar, Cal-Gav, Unilver, Keter Plastic, Strauss, Toyota, IKEA, etc.
The group claims to have successfully breached Signature-IT and stolen data files totaling approximately 16 gigabytes. These files were seemingly taken from the data repositories (SQL databases) of various internet sites stored on the company’s servers, thereby gaining access to a substantial amount of customer data. This includes a vast list of Israeli companies, both private and government owned.
After the attack on Signature-IT, the group published a press release stating they allegedly wiped and destroyed over 1000 servers and critical databases, belonging to over 150 victims. In the press release, they announce their intention to release new victims’ leaked files every day and night (meaning 2 leaks every day) for the next month, starting on December 1st.

At their statement, they attached a list of affected government offices and organizations, industrial and commercial companies in Israel (figure 6).

It is worth mentioning that a few days after the attack, some of the websites were unavailable due to the security breach.
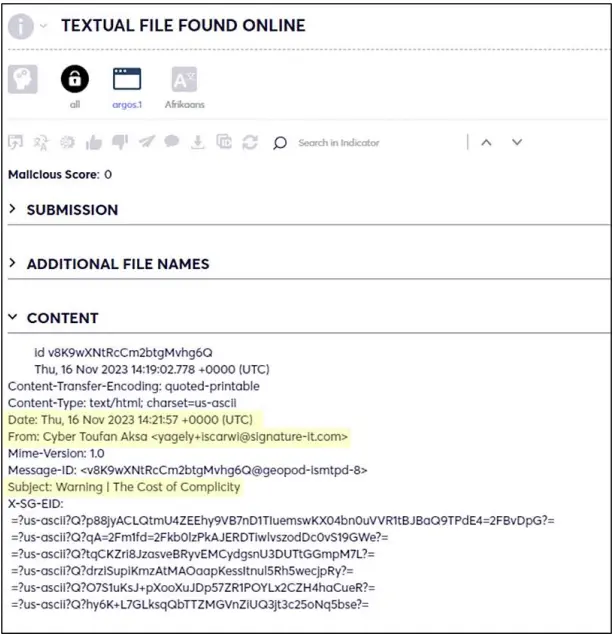
Furthermore, following the attack against Signature-It, Cyberint was also able to detect several menacing emails sent by the group. The emails were directed to thousands of Israeli email addresses with the subject line: “The Cost of Complicity” and were sent on November 16th, right after they announced the attack on Signature-IT, as part of the psychological warfare against Israel.
Further analysis of those emails reveals that one of the detected emails claimed to be sent from the Signature-IT domain “signature-it.com”, was spoofed. The authentication records failed to verify the sender’s authenticity. Also, it was revealed that the original domain owned by Signature-IT is “signature-it.co.il.” This highlights a common tactic used by attackers to deceive recipients by mimicking legitimate domains through email spoofing.
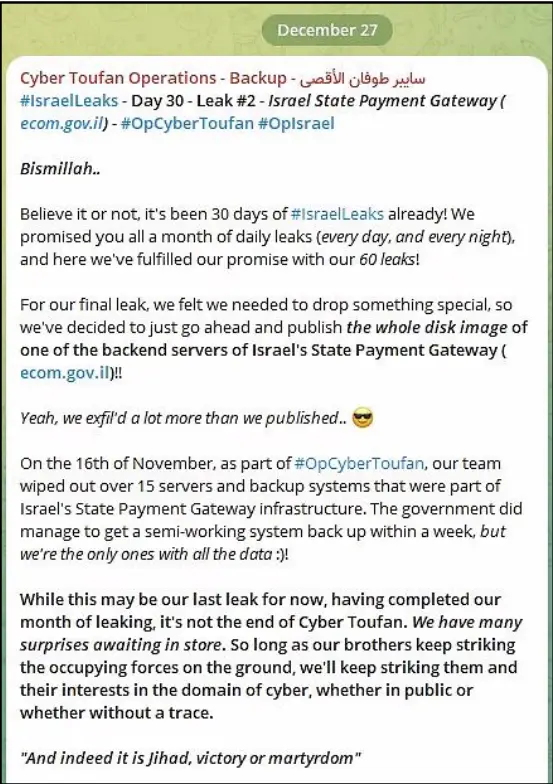
Lastly, on December 27th, the group announced they have completed the 30 days leaking campaign and no additional files were published since then.
During the last month, Cyberint was carefully tracing the group’s activity and managed to acquire and examine the leaked files of different allegedly breached companies that were published on a daily basis. Upon further examination of the files, Cyberint concluded that they were all associated with the primary notorious group’s attack on Signature-It. This finding contradicts the attack group’s statement of new breaches across multiple Israeli companies. The common parameters of the examined files which Cyberint to that assumption are entailed below.
The files were produced by Mysqldump, a utility that performs logical backups of MySQL databases by creating a set of SQL statements intended to essentially clone the original database by reproducing its table definitions and populating these tables with the original data.
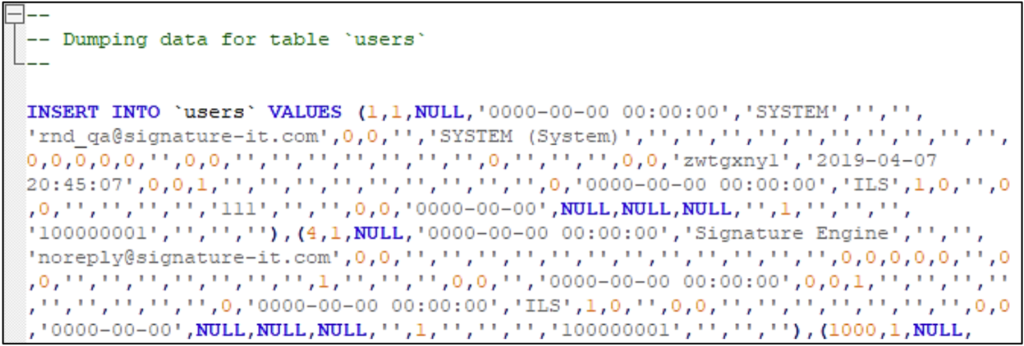
As such, the files include a large amount of similar data entries, including email addresses, names, hashed passwords, and phone numbers, both of regular users and administrators. For example, a “SYSTEM” user with the address “rnd_qa@signature-it.com” is common to all of them.
Leaked files of one allegedly compromised company also contain unrelated information about other companies that have previously experienced breaches attributed to the same group:
The hacking group known as “Cyber Toufan Al-Aqsa,” recently emerged, has claimed responsibility for various notable attacks against Israeli companies in recent months. The group has executed multiple successful attacks, including website defacement, unauthorized access to institutions, businesses, and private residences, compromise of security cameras, and data breaches. Notably, the group gained widespread attention for its attack on Signature-IT, wherein data files totaling approximately 16 gigabytes were pilfered, leading to the daily disclosure of new victims.
Following the attack against Signature-It, Cyberint was also able to detect several menacing emails sent by the group. Further analysis of those emails reveals that one of the detected emails claimed to be sent from the Signature-IT domain “signature-it.com”, was, in fact, spoofed. Also, it was revealed that the genuine domain owned by Signature-IT is “signatureit.co.il. This highlights a common tactic used by attackers to deceive recipients by mimicking legitimate domains through email spoofing.
Further examination of the files constantly published by the group led Cyberint to the conclusion that all of them were associated with the primary notorious group’s attack on Signature-It. This discovery challenges the attack group’s assertion of new breaches across multiple Israeli companies.
To learn more about how our threat intelligence research helps protect businesses against ransomware and other risks, request a demo.

Fill in your business email to start.
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


