

First published May 8th 2025
Updated Oct 5th 2025
Editor’s Note: This blog builds on our recent analysis of the DragonForce ransomware cartel, which claimed responsibility for a wave of UK retail attacks in April–May 2025. While DragonForce took credit for the extortion and data leak phase, growing evidence suggests that another group—Scattered Spider—may have played a foundational role in enabling those attacks. Known for its cloud-first, identity-centric intrusion methods, Scattered Spider is emerging as a likely access broker or collaborator within the DragonForce affiliate model.
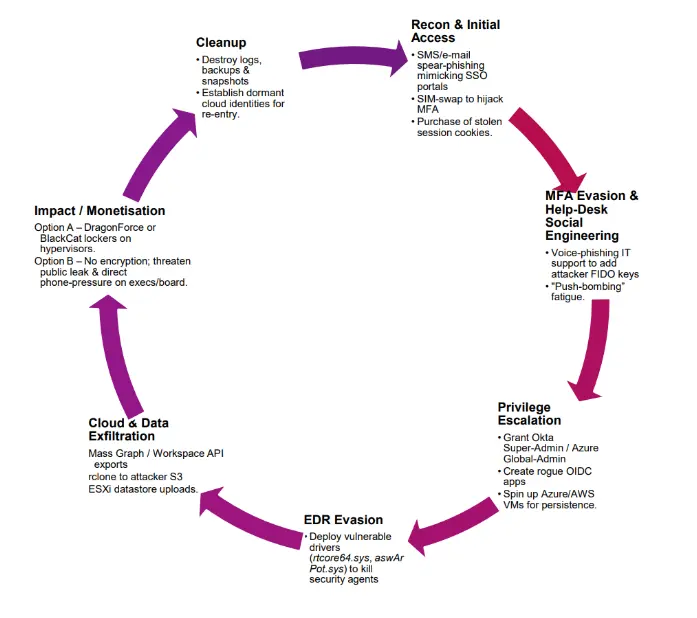
Scattered Spider (also known as Roasting 0ktapus and Scatter Swine) is a financially motivated threat actor that has been actively operating since May 2022. Historically focused on telecommunications and business process outsourcing (BPO), the group has evolved to target high-leverage industries, including critical infrastructure and, more recently, UK and US retail organizations.
While Scattered Spider has not publicly claimed responsibility for the UK/US retail intrusions, the initial access tactics, cloud exploitation, and social engineering techniques observed in those breaches align closely with the group’s known behavior. It is increasingly likely that Scattered Spider was involved in the early-stage intrusion, which was then followed by ransomware deployment and extortion by DragonForce or one of its affiliates.
This evolving threat model reflects a broader shift in the ransomware ecosystem, where access operators, malware developers, and extortion actors collaborate without co-branding, often using white-labeled infrastructure.
Potential targeting of UK/US retail and telco supply chains highlights a focus on high-leverage industries during peak seasons. Scattered Spider’s combination of social engineering and cloud exploitation, emphasizing persistence and stealth, poses significant risks.
This is particularly true for the UK/US retail industry due to third-party vendor dependencies and the group’s adeptness at lateral movement. High helpdesk turnover and seasonal staff vulnerabilities to vishing during peak sales periods facilitates password resets and MFA attacks, while loyalty data and payment tokens remain valuable targets even without encryption.
Despite this shift in targets, Scattered Spider remains committed to employing an array of social engineering tactics in their attacks. These tactics include Telegram and SMS phishing, SIM swapping, exploiting Multi-Factor Authentication (MFA) fatigue, and other strategies. They have recently participated in a malicious recruitment campaign as detailed below.
Notably, the group has frequently posed as IT personnel to deceive individuals into divulging their credentials or granting remote access to their computers. Scattered Spider has also been associated with various past phishing campaigns and the deployment of malicious kernel drivers, including the use of a signed but malicious version of the Windows Intel Ethernet diagnostics driver.
In mid-2023, it was reported that Scattered Spider became involved in the BlackCat ransomware operation, initiating the deployment of ransomware payloads on both Windows and Linux systems, and subsequently targeting VMWare ESXi servers.
Representatives of BlackCat have stated that they collaborate exclusively with Russian-speaking affiliates. Therefore, Scattered Spider’s participation as an affiliate in this Ransomware-as-a-Service (RaaS) likely reflects the ongoing evolution of a Russian-speaking RaaS group focused on maximizing financial gains. It is probable that a key condition for recruiting affiliates is to refrain from targeting organizations within the Commonwealth of Independent States (CIS).
In August 2022, an American cloud communications company detected an unauthorized breach that exposed information pertaining to 163 of its customers. The compromised data included mobile phone numbers and SMS messages containing one-time passwords, which Scattered Spider gained access to through the console. The threat actor employed a phishing kit designed to capture usernames, passwords, and one-time password (OTP) factors. Their targets primarily encompassed technology companies, telecommunications providers, and entities and individuals associated with cryptocurrency.
In December 2022, a campaign by Scattered Spider was found, targeting organizations within the telecom and business process outsourcing (BPO) sectors with an end objective of gaining access to mobile carrier networks.
As of January 2023, Scattered Spider had been implicated in over six incidents that transpired since mid-2022. These incidents revolved around the targeting of prominent outsourcing firms catering to crypto-currency entities and individuals of substantial value.
Recently, they have been targeting UK/US retail companies.
Scattered Spider is known for theft of sensitive data and leveraging trusted organizational infrastructure for follow-on attacks on downstream customers.
Scattered Spider typically capitalizes on vulnerabilities like CVE-2015-2291 and utilizes tools such as STONESTOP and POORTRY to disable security software, evading detection. This group exhibits a profound comprehension of the Azure environment and effectively employs built-in tools during their operations. Following initial access acquisition, Scattered Spider has been observed conducting reconnaissance across a range of environments, including Windows, Linux, Google Workspace, Azure Active Directory, Microsoft 365, and AWS. Additionally, they engage in lateral movement and download supplementary tools to exfiltrate VPN and MFA enrollment data in specific instances. The group also establishes persistence through legitimate remote access tools like AnyDesk, LogMeIn, and ConnectWise Control.
POORTRY is a malicious driver employed for the purpose of terminating specific processes on Windows systems, such as an Endpoint Detection and Response (EDR) agent running on an endpoint. To avoid detection, attackers have gone to the extent of signing the POORTRY driver with a Microsoft Windows Hardware Compatibility Authenticode signature.
STONESTOP, on the other hand, is a Windows userland utility that endeavors to cease processes by generating and introducing a malicious driver. This utility operates both as a loader and installer for POORTRY and serves as an orchestrator for instructing the driver regarding the actions it should execute.
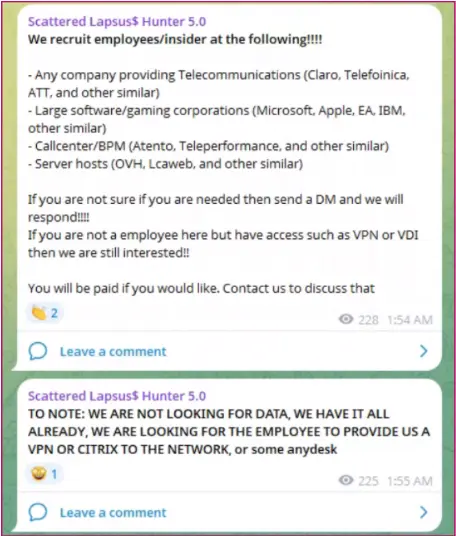
As part of Cyberint’s ongoing monitoring of Telegram channels associated with Scattered Spider, ShinyHunters, and Lapsus$ threat actors, our team observed some posts that warrant attention.
Aside from leaking their victims’ data and selling compromised access to various corporations on Telegram, the threat actors were recently observed recruiting Initial Access Brokers (IABs) to target a wide range of sectors.
Specifically on August 31, 2025, the threat actor posted a message saying they were recruiting insiders working at several companies, including:
· Telecoms
· Large software or gaming corporations
· Call centers or Business Process Management (BPM) companies (
· Server hosts
These insiders are typically needed to help facilitate malicious operations while avoiding detection. The group is also looking for any individual with VPN, VDI, Citrix, or AnyDesk access to these organizations.
Scattered Lapsus$ Hunter threat actors seek insiders at strategic corporations.
The organizations listed on the Telegram post are seen as prime targets for Scattered Spider/ShinyHunters/Lapsus$ because of their strategic position within broader supply chains and the unique social engineering opportunities they present.
For instance, access to telecom systems could enable them to intercept communications, and impersonate support agents, providing a gateway to target high-value individuals or organizations, especially when credentials or OTPs are transmitted via mobile networks.
Large software are deeply integrated into the operations of thousands of other businesses, and any access could enable effective social engineering and make lateral movement easier through SSO and extensive developer networks.
Call centers and BPM companies provide service to corporations and corporate access could allow attackers to impersonate agents and access company systems, while major server hosts manage critical infrastructure that attackers can exploit to manipulate servers, hijack victims’ domains, and launch phishing campaigns.
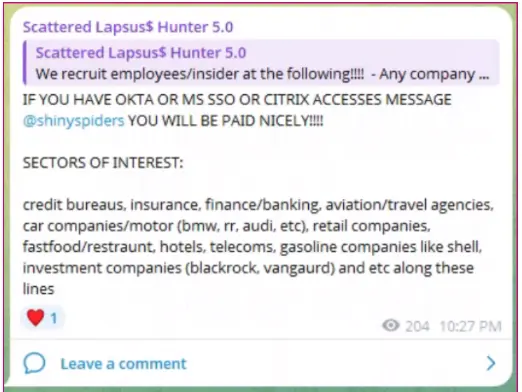
Moreover, Scattered Lapsus$ Hunter threat actors were observed actively seeking SSO and login access across companies in a wide range of sectors, including:
· Credit bureaus
· Insurance
· Finance/banking
· Aviation/travel agencies
· Automobile
· Retail
· Fast Food
· Hospitality
· Telecommunications
· Gas
· Investments
This points to the likelihood of imminent campaigns against these sectors, and affected organizations should take steps to reinforce their defenses and stay alert to potential threats.
Scattered Spider is recognized for its exploitation of CVE-2015-2291, a vulnerability residing in the Intel Ethernet diagnostics driver for Windows (iqvw64.sys). This flaw enables local users to potentially trigger a denial of service or execute arbitrary code with kernel privileges by means of meticulously crafted IOCTL calls, specifically (a) 0x80862013, (b) 0x8086200B, (c) 0x8086200F, or (d) 0x80862007. To implement their scheme, Scattered Spider leveraged CVE-2015-2291 to introduce a malicious kernel driver within the Intel Ethernet diagnostics driver for Windows (iqvw64.sys).
In addition, Scattered Spider has exploited CVE-2021-35464, a vulnerability identified in the ForgeRock AM server. Versions of ForgeRock AM server preceding 7.0 were found to have a Java deserialization vulnerability associated with the jato.pageSession parameter across multiple pages. This exploitation does not necessitate authentication, and it can lead to remote code execution by dispatching a specifically crafted /ccversion/* request to the server. This vulnerability arises from the utilization of Sun ONE Application Framework (JATO) present in Java 8 or earlier versions. Scattered Spider harnessed CVE-2021-35464 to execute code and elevate their privileges on an AWS instance that utilized the Apache Tomcat user. This was achieved through the request and assumption of permissions corresponding to an instance role, facilitated by a compromised AWS token.
Origins and Affiliates:
As we mentioned, in April 2023, ALPHV (BlackCat) ransomware group used an updated version of POORTRY to compromise the US payments giant NCR, leading to an outage on its Aloha point of sale platform. This information may indicate that the scattered spider operations are in Eastern Europe.
Cyberint’s observations suggest likely targeted attacks against the mentioned sectors, alongside an overall heightened risk of additional supply chain incidents. To reduce the risk, organizations should take the following proactive measures:
Cyberint, now a Check Point company, reduces risk by helping organizations detect and mitigate external cyber threats before they have an adverse impact. The Check Point External Risk Management solution provides superior visibility through continuous discovery of the evolving attack surface, combined with the automated collection and analysis of vast quantities of intelligence from across the open, deep and dark web.

| Type | Value | Last Observation Date |
|---|---|---|
| IPv4-Addr | 98.100.141.70 | Apr 30, 2025 |
| Url | http://138.68.27.0 | Apr 30, 2025 |
| IPv4-Addr | 198.44.136.180 | Apr 30, 2025 |
| IPv4-Addr | 195.206.107.147 | Apr 30, 2025 |
| IPv4-Addr | 195.206.105.118 | Apr 30, 2025 |
| IPv4-Addr | 194.37.96.188 | Apr 30, 2025 |
| IPv4-Addr | 193.37.255.114 | Apr 30, 2025 |
| IPv4-Addr | 193.27.13.184 | Apr 30, 2025 |
| IPv4-Addr | 193.149.129.177 | Apr 30, 2025 |
| IPv4-Addr | 192.166.244.248 | Apr 30, 2025 |
| IPv4-Addr | 188.214.129.7 | Apr 30, 2025 |
| IPv4-Addr | 188.166.92.55 | Apr 30, 2025 |
| IPv4-Addr | 188.166.117.31 | Apr 30, 2025 |
| IPv4-Addr | 188.166.101.65 | Apr 30, 2025 |
| CVE ID | Score | Description | Published | Exploited By | Products |
|---|---|---|---|---|---|
| CVE-2021-35464 | 9.8 | ForgeRock AM server before 7.0 has a Java deserialization vulnerability in the jato.pageSession parameter on multiple pages. The exploitation does not require authentication, and remote code execution can be triggered by sending a single crafted /ccversion/* request to the server. The vulnerability exists due to the usage of Sun ONE Application Framework (JATO) found in versions of Java 8 or earlier | Jul 22, 2021 | 1 Threats | access_management, openam |
| CVE-2015-2291 | 7.8 | (1) IQVW32.sys before 1.3.1.0 and (2) IQVW64.sys before 1.3.1.0 in the Intel Ethernet diagnostics driver for Windows allows local users to cause a denial of service or possibly execute arbitrary code with kernel privileges via a crafted (a) 0x80862013, (b) 0x8086200B, (c) 0x8086200F, or (d) 0x80862007 IOCTL call. | Aug 09, 2017 | 1 Threats | ethernet_diagnostics_driver_iqvw32.sys, ethernet_diagnostics_driver_iqvw64.sys, windows |
| CVE-2024-37085 | 6.8 | VMware ESXi contains an authentication bypass vulnerability. A malicious actor with sufficient Active Directory (AD) permissions can gain full access to an ESXi host that was previously configured to use AD for user management https://blogs.vmware.com/vsphere/2012/09/joining-vsphere-hosts-to-active-directory.html by re-creating the configured AD group (‘ESXi Admins’ by default) after it was deleted from AD. | Jun 25, 2024 | 1 Threats | cloud_foundation, esxi |
| Tactic | Technique |
|---|---|
| Impact | T1496 – Resource Hijacking |
| Defense Evasion | T1134.001 – Token Impersonation/Theft |
| Privilege Escalation | T1134.001 – Token Impersonation/Theft |
| Privilege Escalation | T1068 – Exploitation for Privilege Escalation |
| Persistence | T1053 – Scheduled Task/Job |
| Execution | T1053 – Scheduled Task/Job |
| Privilege Escalation | T1053 – Scheduled Task/Job |
| Execution | T1059 – Command and Scripting Interpreter |
| Execution | T1106 – Native API |
| Initial Access | T1195.002 – Compromise Software Supply Chain |
| Initial Access | T1190 – Exploit Public-Facing Application |
| Persistence | T1133 – External Remote Services |
| Initial Access | T1133 – External Remote Services |
| Initial Access | T1566 – Phishing |
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


