



I love to get stuck in and let the creative juices flow. My strengths lie in idea generation, development and execution. Over 5 years experience in B2B cybersecurity. I reign supreme when my imagination and creativity can run wild.
The Attack Surface is Growing, and fast. What once was considered the attack surface is no longer. Instead organizations are faced with a sprawling attack surface, including not just domains, IPs and sub-domains, but also third parties, brand risks and more.
Businesses in the finance sector face two additional challenges:
This blog focuses on banks, FinTech companies and insurance providers, as they are among the largest types of entities in the financial sector. That said, most of the guidance below applies to any type of financial organization seeking to understand the special nature of financial attack surface risks.
Ask most people to describe their attack surface, and their minds will probably go to traditional types of assets (like PCs and servers) and traditional attack techniques (like exploiting vulnerabilities in software applications).
Those are indeed core components of conventional attack surfaces in the financial sector and beyond. But again, advanced threat actors are always on the lookout for new ways to breach organizations, which means that the list of assets and attack techniques they could exploit – in other words, the attack surface – is growing.
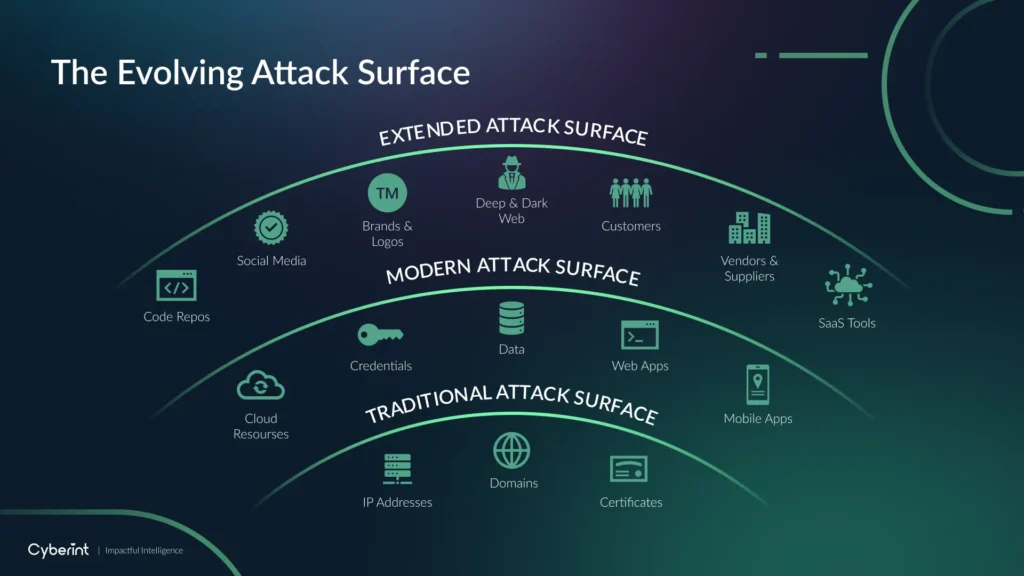
For example, threat actors are now deploying attack techniques like the following alongside more traditional methods:
Although these attacks aren’t entirely new, they are on the rise. For example, supply chain attacks were one of the main drivers fueling a data breach, an increase of 72 percent in 2023. This means that businesses that once did not have to worry much about these types of risks when developing attack surface management strategy now face a longer list of potential threats. To learn more, read about the eight most common cyber threats to the financial industry and how to mitigate them.
The problem of the expanding attack surface applies to almost all types of businesses across all sectors. But for financial organizations these specific challenges rise to the forefront:
Threats like these are among the reasons that Ernest and Young conclude that “cybersecurity has risen to the top of the list of near-term risks for banks.”
To illustrate how these unique challenges can play out for financial organizations, let’s consider the example of phishing.
Virtually everyone today is familiar with the basics of conventional phishing techniques, such as sending emails designed to download a malicious attachment or click on a malicious link to a phishing site. The site then solicits sensitive information from targets. But in the financial sector, threat actors motivated by the high reward of a successful breach are likely to turn to more sophisticated phishing methodologies.
They might, for example, impersonate a bank on social media or create a fake website hosted on a domain that is spelled similarly to the bank’s legitimate domain name – something that is relatively easy to set up with the help of a phishing kit. If they are able to direct the bank’s customers to the impersonated account or lookalike domain, they could collect account login details, then use them to access customers’ actual accounts and steal money.
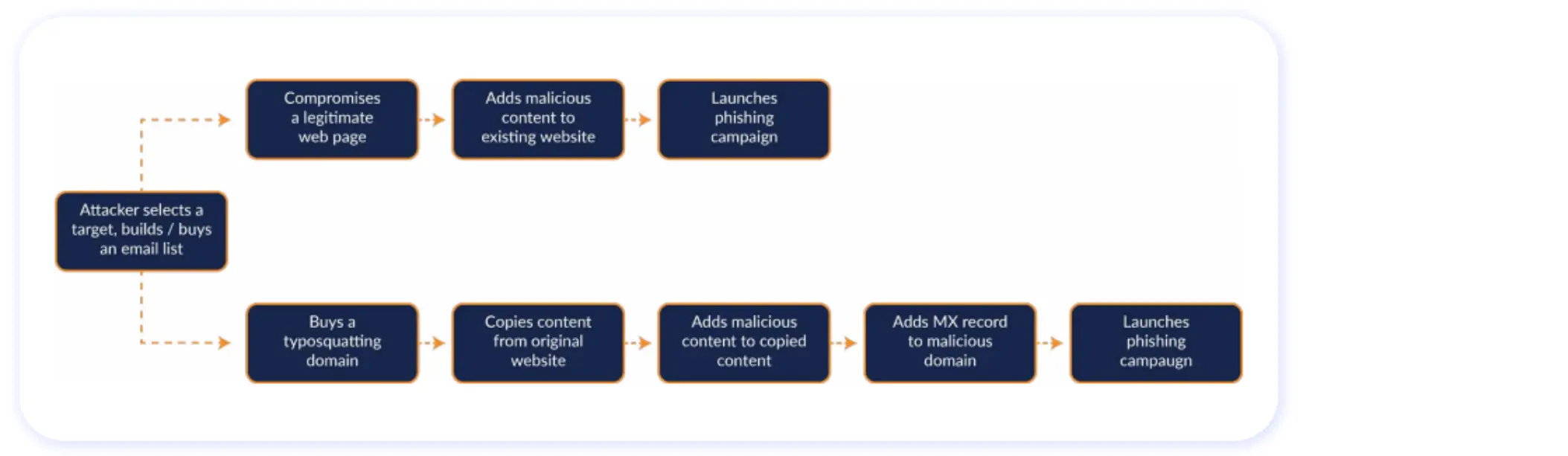
Protections like multi-factor authentication (MFA) can help to mitigate these risks, of course. But as the IT department at UNC-Chapel Hill notes, “phishers, scammers and other malicious actors are highly motivated to find ways around this protection so they can steal valuable data.” Their workaround techniques include using phishing strategies like vishing (which means engaging with targets via voice channels) or smishing (the use of SMS for phishing).
When attackers log into their victims’ legitimate accounts, they can make phone calls or send SMS messages to their targets asking them to approve a second authentication factor, thereby defeating the MFA protections.
Customer awareness campaigns can help as well, and they’re certainly worth the investment for financial organizations seeking to minimize their risks. But these plans are not foolproof.
That means that the only way for financial organizations to gain real protection against phishing risks is to deploy advanced defenses – such as phishing tools that can detect all types of phishing, not just conventional methods like email-based attacks. Dark and Deep web monitoring can help as well by providing early insight into attacks that threat actors may be planning.
Note, too, that some attack surface defenses can be automated or managed with help from AI. But ultimately, analysis by expert humans is the only way to identify and understand the most serious types of attacks
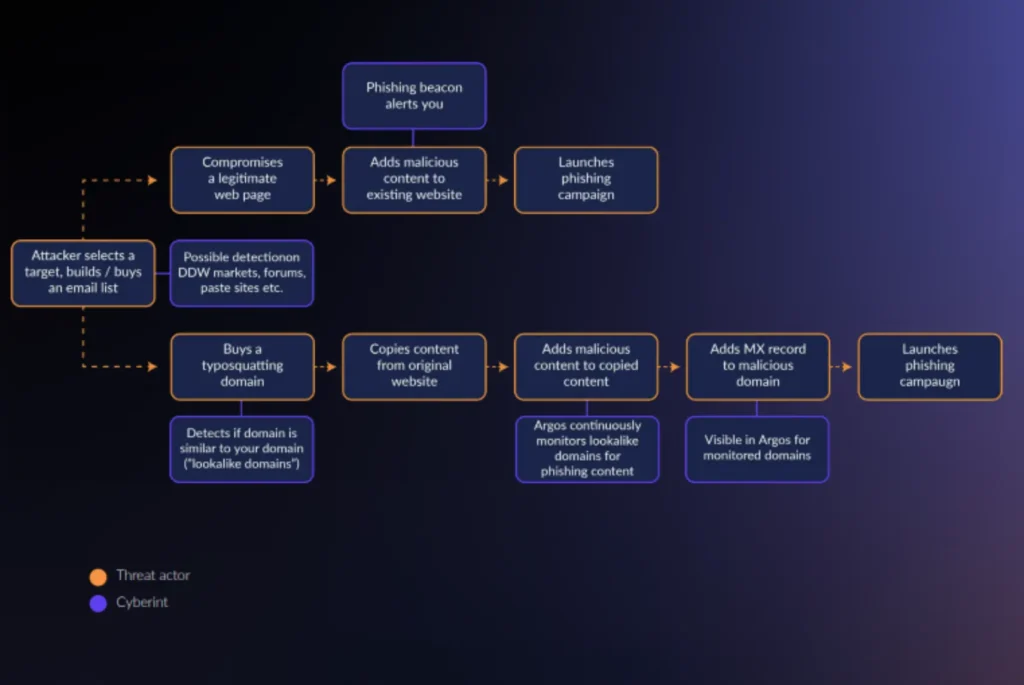
Cyberint offers the comprehensive suite of solutions that organizations need to defend the ever-expanding financial attack surface. With Cyberint, banks, FinTech companies and insurance providers gain all of the core tools they need to manage their attack surfaces, including:
But that’s not all. Cyberint also delivers advanced attack surface management capabilities, such as:
By packing all of these capabilities into a single platform, Cyberint not only makes it easy to defend all facets of your attack surface. It also reduces tooling costs by allowing businesses in the financial sector and beyond to consolidate their cybersecurity solutions into a single offering.

©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


