


Initial Access Brokers (IABs) are threat actors who infiltrate networks, systems, or organizations and sell this unauthorized access to other malicious actors. Instead of executing the entire cyberattack, IABs focus on the initial breach and monetize it by selling access to compromised systems. They assist ransomware operations, particularly RaaS schemes, by streamlining attacks and reducing workload at the start.
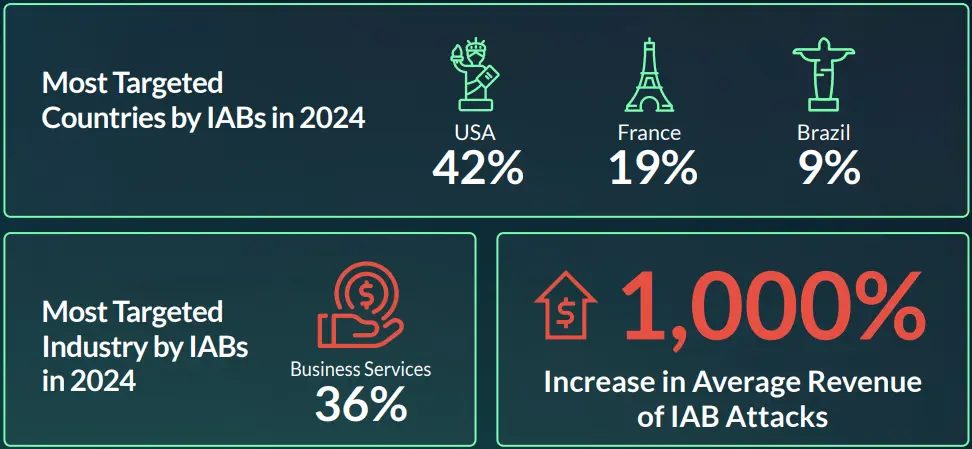
The report, based on data from Cyberint’s research team over the past year and a half, highlights that the US was the prime target of Initial Access Broker market in 2023, with over 48% of attacks targeting the country. In 2024, France and Brazil have been increasingly targeted. IABs target various industries, with the business services sector being the most frequently targeted, similar to ransomware trends. The retail industry has remained consistently in the top 3 in 2023 and 2024, but the manufacturing industry has been increasingly targeted in 2024, creeping up from just 14% of attacks in 2023 to 23% in 2024.
In 2024, large-scale organizations were the most targeted due to their high revenue potential. Threat actors increasingly targeted organizations with over $1 billion in revenue, making up 27% of all initial access listings for sale. This increased the average revenue of IAB attacks to $1,961,335,406.50, representing a 1000% increase.
There are three primary types of IABs driving most ransomware attacks today. In 2023, those offering servers compromised through exposed Remote Desktop Protocol (RDP) were the most common (>60%). However, in 2024, VPN access surged, challenging RDP access for the top spot (45% VPN vs. 41% RDP).
Most Initial Access Broker posts fall within a price range of $500 to $2,000 for corporate access, though high-value listings occasionally appear, exceeding $10,000.
Protecting against IABs requires a multi-layered security approach, implementing both technical and organizational measures to minimize vulnerabilities.
Ransomware attacks, data breaches, leaks, espionage, and other significant cybersecurity incidents often originate from access purchased on dark web forums and marketplaces.
How do cybercriminals acquire this access? They buy it from Initial Access Brokers (IABs).
IABs are cybercriminals or groups that specialize in infiltrating networks, systems, or organizations and then selling this access to other malicious actors. Instead of carrying out the entire cyberattack themselves, IABs focus on the initial breach, which they monetize by then selling access to the compromised systems.
This report highlights data analyzed by Cyberint’s research team over the past year and a half, gathered from prominent underground forums and marketplaces on the dark web. The data encompasses all the information we extracted from a single listing, allowing us to delve into details such as targeted countries, industries, average prices, organizational revenue, security products in use, number of hosts, and more.
An Initial Access Broker (IAB) is a threat actor specializing in infiltrating computer systems and networks, then selling unauthorized access to other malicious actors. IABs are skilled at identifying and exploiting security vulnerabilities, providing services to ransomware groups and other threat actors. IABs perpetuate malicious activities and enable entry into compromised systems by acting as intermediaries.
IABs are skilled at exploiting common hacking techniques to gain unauthorized access to networks, leveraging social engineering attacks, brute force attacks, and other attack vectors. The asking price for IAB services depends on factors such as the size and type of the target and the type of access offered.
By selling access instead of carrying out attacks themselves, IABs mitigate the risks associated with executing a ransomware attack, focusing instead on breaching networks and capitalizing on their expertise.
IABs primarily operate on dark web forums and underground markets and can function as individual actors or as part of larger organizations like Ransomware-as-a-Service (RaaS) gangs. Their clientele consists of groups with malicious intent who leverage the purchased access to launch ransomware attacks, execute data breaches, and engage in other malicious activities—typically for financial gain.
In general, IABs help ransomware operations, particularly RaaS schemes, to streamline their attacks and reduce their workload at the beginning of an attack. IABs take on the difficult work of finding targets and gaining access. In doing so, they enable ransomware groups to attack at scale because they’re not wasting time trying to secure a foothold in target networks. They can immediately procure that access via an IAB and get to work encrypting the victim’s data.
With certain RaaS groups, the benefit of working with IABs goes a step further. Evidence suggests that some IABs work directly for ransomware groups or affiliates of RaaS groups. This significantly speeds up a ransomware attack, as affiliates can leverage procured access and almost immediately conduct their attack rather than wasting time gaining access. The IAB passes access to the affiliate, who then launches the attack, infects the victim’s network, and in turn passes things off to other parts of the operation to cash out.
Such direct collaboration doesn’t just benefit RaaS groups. It also helps IABs. As discussed by Ransomware.org, IABs who work for RaaS groups don’t need to advertise their services publicly on underground forums. They already have steady work, so there’s no need to market themselves for more. This comes with the added bonus of reduced public visibility, which provides cover when law enforcement shuts down a marketplace and goes after its members.
Initial Access Brokers (IABs) serve as intermediaries in ransomware attacks and data breaches, becoming increasingly vital with the rise of Ransomware-as-a-Service (RaaS). Their services are in high demand, as seen in the growing number of dark web listings over recent years. These brokers typically advertise access to compromised organizations with vague details, attracting ransomware operators, state-sponsored actors, and hacktivists looking for potential targets.
Listings on cybercriminal forums generally follow certain conventions: vendors avoid directly naming the targeted organizations to keep victims unaware of their compromise before the access is sold. Instead, they provide a vague description, often mentioning the victim’s location, industry, revenue, and the type and privilege level of access being sold, along with technical details like the number of employees, hosts, antivirus used, and accessible data.
Some IABs sell access individually, while others offer it in bundles. Highly trusted IABs may not advertise specific access at all, relying on pinned posts to indicate they sell initial access, requiring interested buyers to contact them privately for more information. On many Russian forums, vendors often use criminal slang and other writing conventions to further obscure details from outsiders.
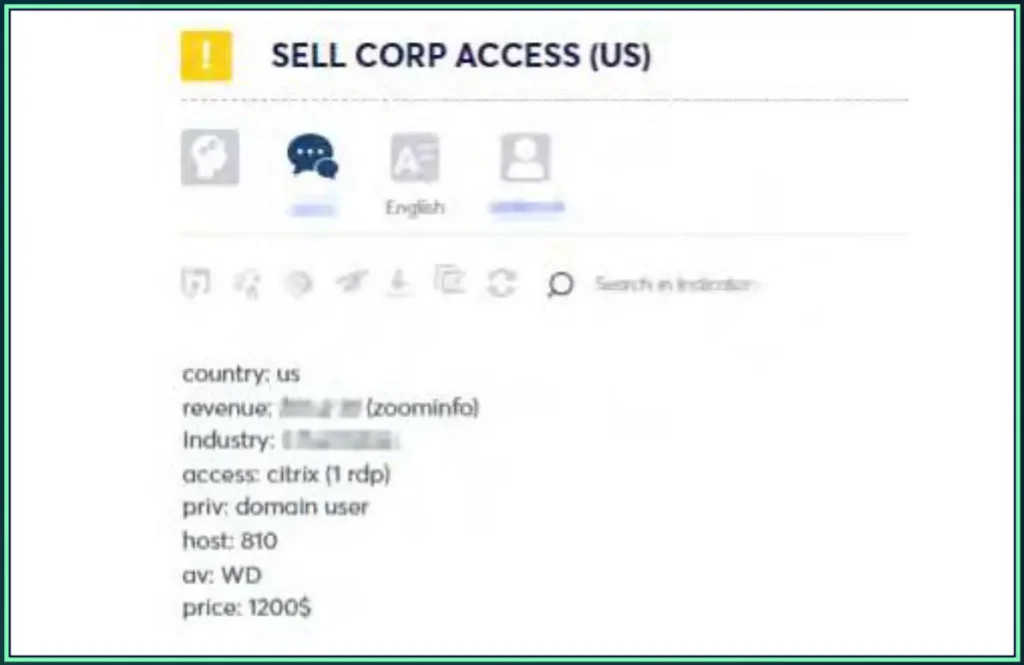
Let’s look at the example below (figure 1), where a familiar seller from a known underground Russian hacking forum is offering access to an American corporation for sale.
The access is by RDP session, using the Citrix platform to connect. Moreover, we can see the revenue and industry (which are obfuscated due to security reasons), the privilege (domain user), and the number of hosts, which is an indication of the number of employees, machines and users on the active directory. The price for that access stands at $1200.
Initial access brokers, much like other cybercriminals such as ransomware gangs, carefully select their targets. They focus on the most competitive markets where they have the greatest chances of gaining access and selling it at the highest price while maximizing its attractiveness. And yes, you guessed it—the United States of America is their prime target.
The U.S. is the most targeted country in almost any cyber security matter. As we can see from the graph below, during 2023 the U.S. remained the number one targeted country by initial access brokers.
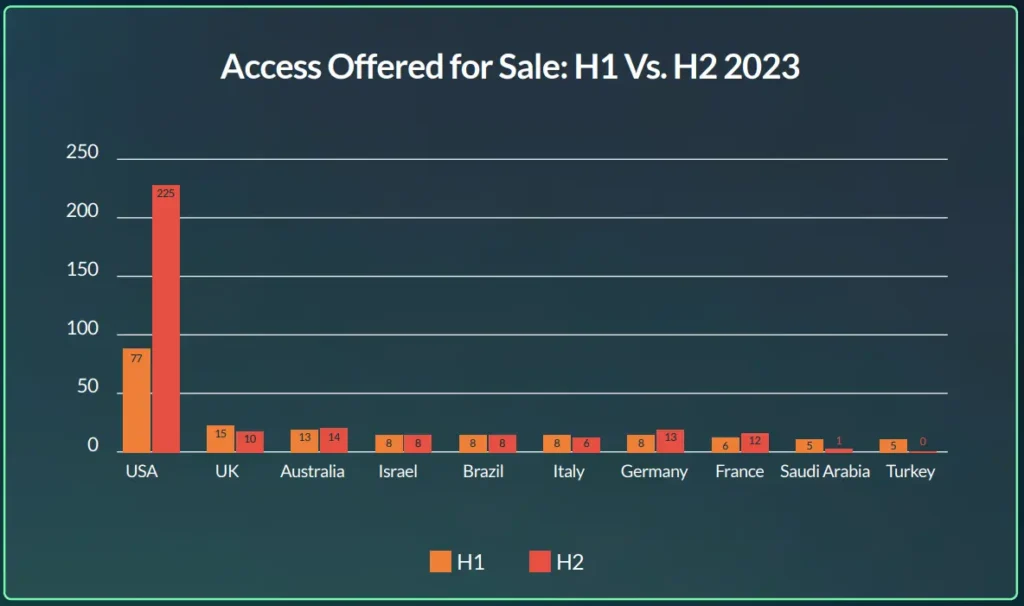
Organizations in the U.S. are most targeted in cybersecurity attacks, and as we can see most threatened by IABs as well for several reasons:
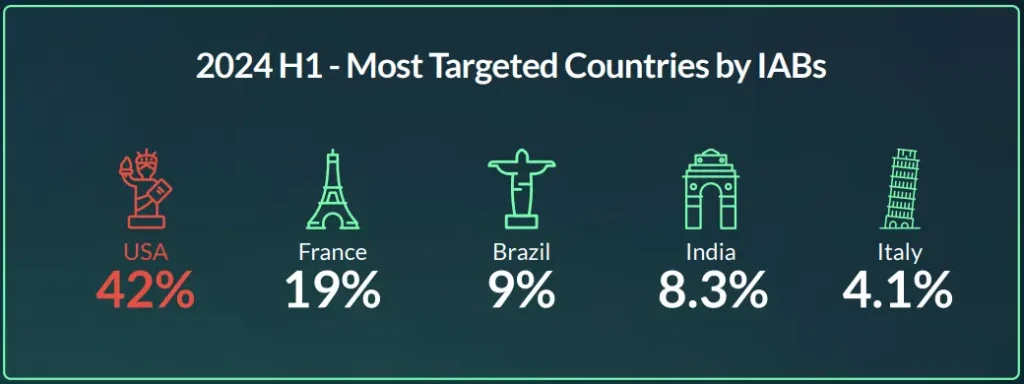
As observed, the trend of targeting U.S. organizations more than any other country in the world continues in the first half of 2024 (see figure 3). Notably, France has moved into the top 10, securing the second spot with 50 unique initial access listings available for sale targeting organizations based there.
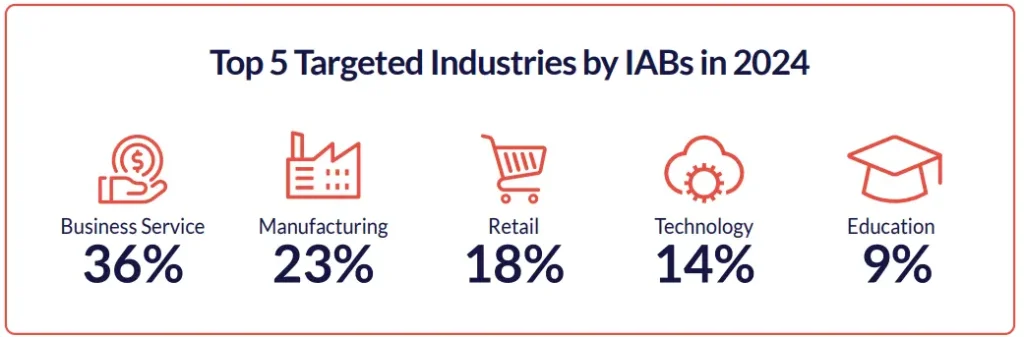
The industry of an organization in an initial access listing for sale can provide several important insights:




IABs target various industries, with the business services sector being the most frequently targeted, similar to trends observed in the ransomware landscape. However, it’s important to recognize that the numbers may not fully capture the situation, as some listings lack information about the industry, which could potentially alter the statistics. That said, more than 75% of the listings do include the sector name, providing a solid foundation for these statistics.

In 2024, the business services sector continues to lead as the most targeted industry, while the financial sector has seen a significant drop, decreasing by 50% compared to the average number of listings in each half of 2023. Additionally, the education sector has become a more frequent target this year, rising to the fifth spot on the list.
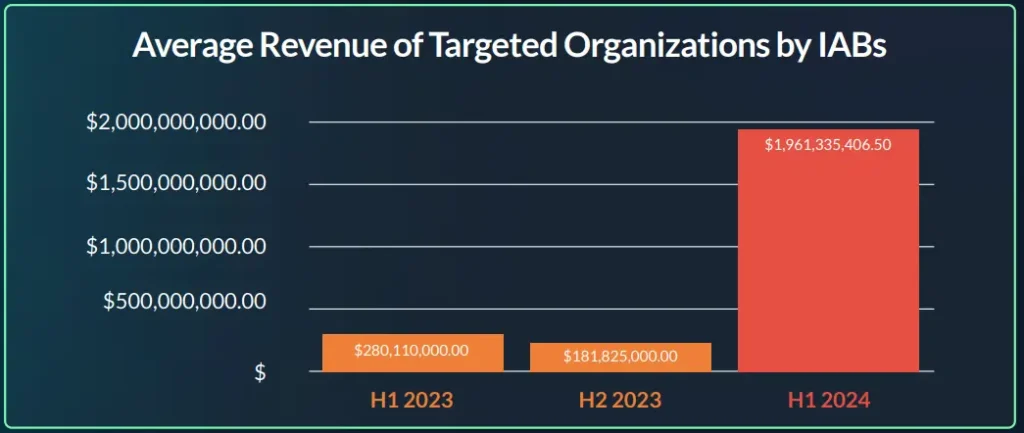
Revenue is likely the key field for buyers to look at before buying access from the sellers. Revenue provides an indication of the size of the company. Higher revenue often suggests that the company has a significant market presence, a large customer base, or a broad product or service offering. Moreover, revenue reflects the demand for the company’s products or services.
As a result, the largest organizations became more sought-after targets for access brokers, largely because of the increased income from the higher price they will demand. Not surprisingly, we see this trend of targeting large scale organizations took place in 2024, with an average revenue of $1,961,335,406.50, which indicates an approximately 1000% increase!
Usually, threat actors take the revenue data from known data sources providers, such as ZoomInfo. From the data we collected in 2023, we noticed that there are 4 major groups we can divide the targeted organizations’ revenue into, as seen in the graph below (figure 7).
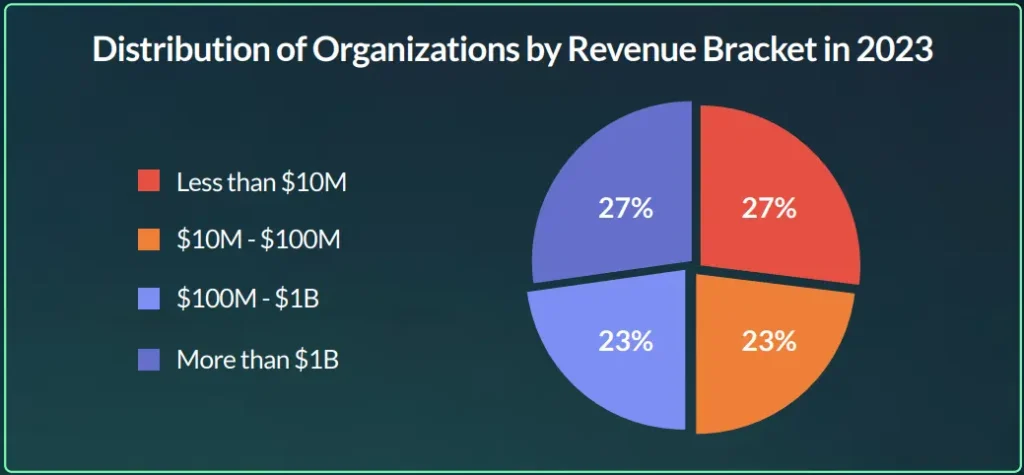
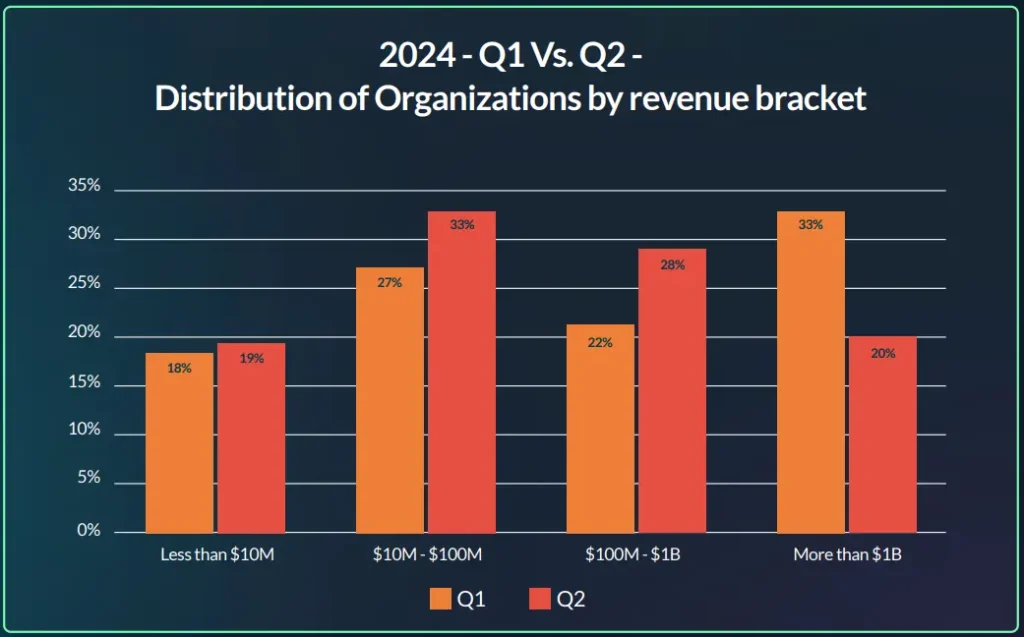
However, the second quarter of 2024 shows a different distribution compared to 2023 and the first quarter of 2024. Threat actors are increasingly targeting organizations in the highest revenue bracket, with over $1 billion in revenue, making up 33% of all initial access listings for sale.
Additionally, the average revenue and distribution of organizations by revenue bracket over the past year and a half indicates that threat actors are focusing more on larger organizations. They are increasingly targeting the higher end of each revenue group, particularly in 2024, as they aim to carry out operations on a larger scale.
IABs offer various types of access and privileges to compromised systems and networks. These access types and privileges can vary widely in terms of what they enable a buyer to do within a target organization.
There are three primary types of initial access brokers driving most ransomware attacks today: those selling access to systems compromised with backdoors or malware, those offering servers compromised through exposed Remote Desktop Protocol (RDP), and those dealing in compromised network devices. Brokers selling backdoored systems offer access to computers infected with malware, often within corporate networks, which are then sold to other cybercriminals, including ransomware groups.
Brokers targeting RDP systems sell access to corporate servers compromised through brute-force attacks on unprotected systems with weak credentials. Finally, brokers exploit known vulnerabilities in network devices such as VPN servers and firewalls to gain control of internal networks, selling this access to threat actors on the dark web.
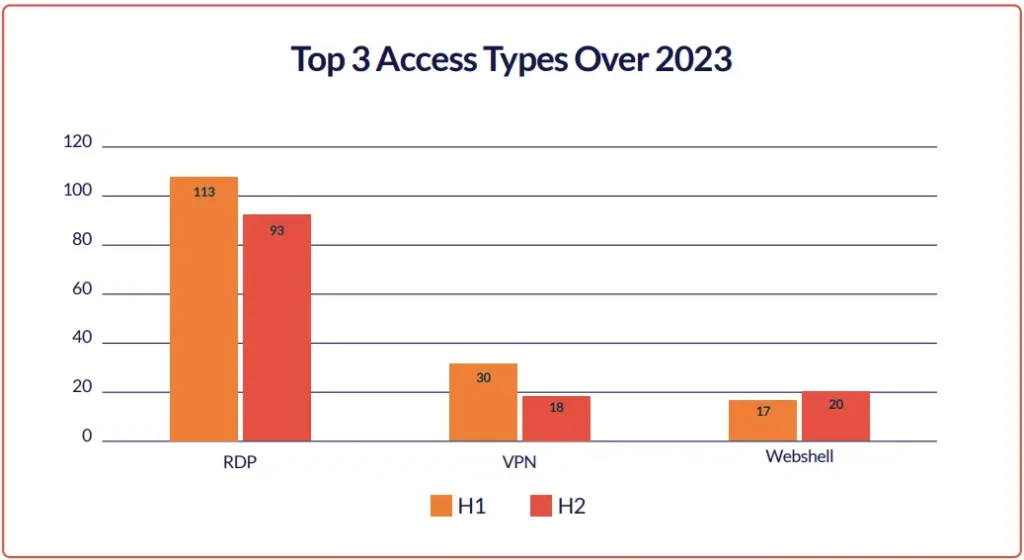
As shown in the figure above, RDP access was by far the most frequently offered type for sale. This suggests that RDP-related products and activities were particularly vulnerable to attacks by threat actors, who frequently employed techniques to steal credentials.
However, as we’ve observed various shifts in 2024 concerning IAB targets, VPN access has surged by hundreds of percentage points compared to 2023, challenging RDP access for the top spot (see figure below).

Generally, these are the most common types of access types:
User Authentication is a big deal in any organization. In most outfits, this is done through Windows. They deal with their users by making use of an Active Directory Server. In IAB sales we often see 3 types of privileges:
As you might expect, the higher the privilege level, the more valuable the access becomes, which in turn drives up its price. According to our data, the average price for “Domain Admin” privilege is 85% higher than the average price.
According to the figure below, Domain Admin and Local Admin were the most common privilege types offered for sale as part of the initial access information provided. In general, they share almost 80% of all privilege types we collected in H1 2023.
However, the second half of 2023 was a bit different. Here we saw an increase in domain user privilege type, which made the distribution between these 3 privilege types more equal.
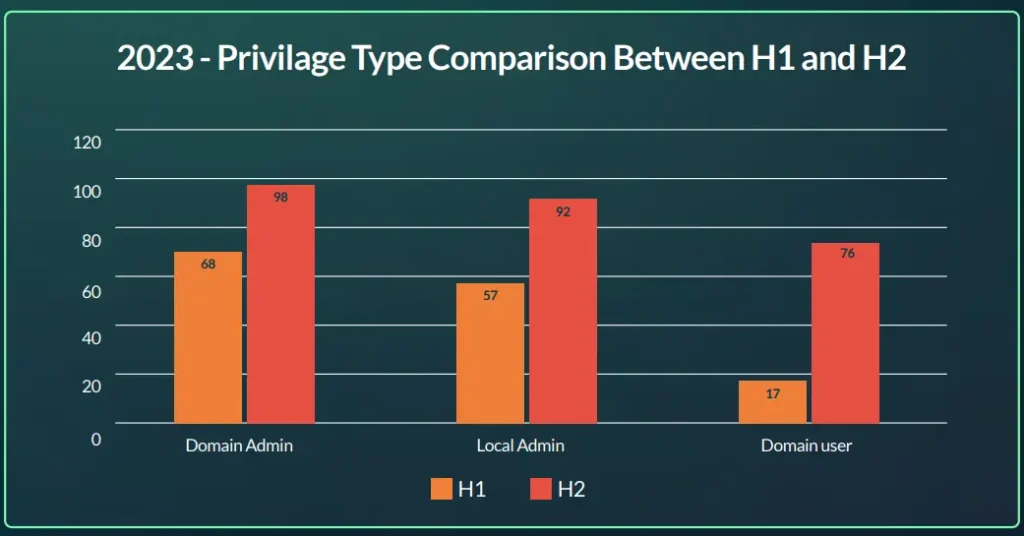
In 2024 things have remained in order, as we can see in the graph below, the “Domain user” privilege type is the most common with 107 instances. The distribution remains as follows in 2024.
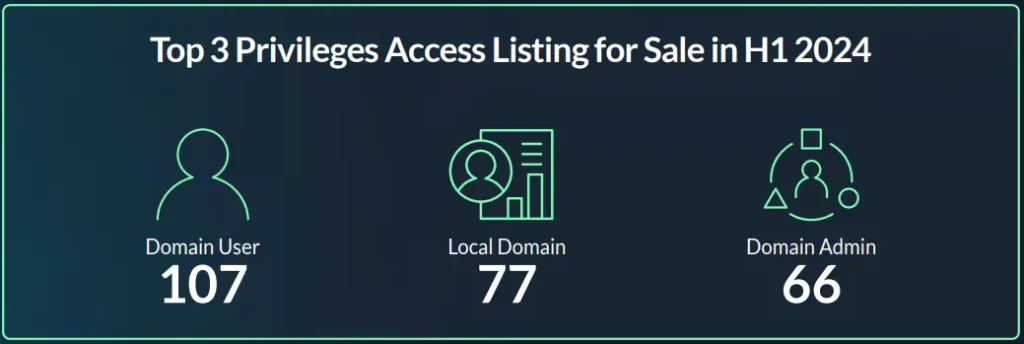
Generally, we observed different privilege types offered as part of the access sale but in very small numbers compared to the other three mentioned, such as:
The majority of IAB posts fell within a relatively narrow price range, typically between $500 and $2,000 for corporate access. However, on occasion, a particularly high value listing appears, offering access to a uniquely valuable environment, which can drive prices into the tens of thousands of dollars, with some listings exceeding $10,000.
In 2023, the average price for a listing was $3,066, while the median price was $1,500. Despite these figures, it’s important to note that 65% of listings in 2023 were priced under $2,000, and 77% were under $3,000. The higher average price is skewed by these high value listings, where prices can be significantly higher, sometimes hundreds of percent above the average.
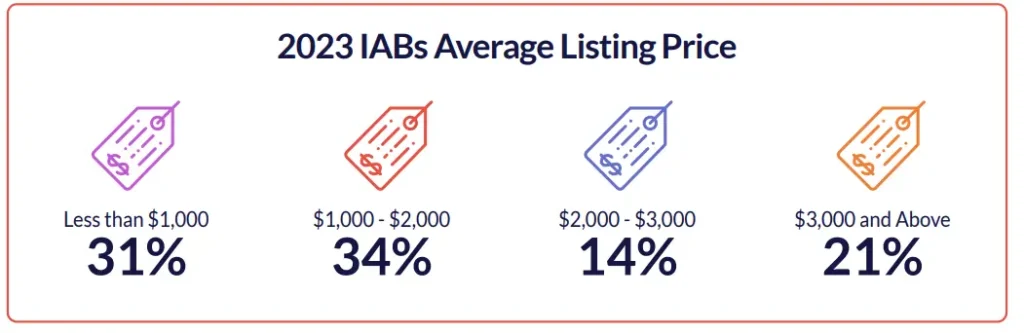
In 2024, threat actors have shifted their focus to targeting higher-revenue organizations, yet they have reduced the prices relative to the access value of these organizations. The average price has dropped significantly to $1,295, which is an approximately 60% decrease.
As illustrated in the chart below, the vast majority of listings are now priced under $1,000, a notable change from what we observed in 2023. The proportion of high value accesses has also decreased, now accounting for only 9% of all listings available for sale.
It’s important to highlight that there are hundreds of listings at these lower average prices, which can still cause significant damage and provide threat actors with substantial financial gain, even more so than the more expensive listings.

Most listings for sale pertain to personal machines of users, could allow an attacker to control various systems and private databases depending on the access type and privileges. However, purchasing initial access does not guarantee that the attacker will avoid detection or capture during their activities.
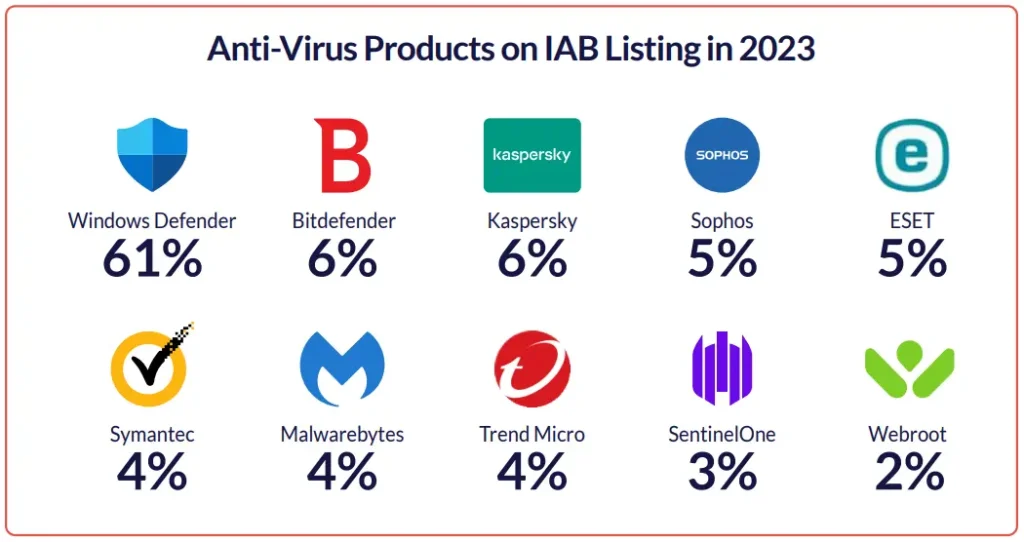
This is why the brokers sometimes add another information field to the listing called “AV”, which is a short cut for “Anti-Virus”. Not all the listings contain this information, whereas almost 40% don’t provide this information. Still, we extracted enough information from thousands of listings to create a picture of the leading security products that were installed on the compromised machines.
The image below shows that over 60% of the machines are only equipped with Windows Defender, highlighting a significant security gap within the organization. This suggests a lack of additional protective software, which could leave these systems more vulnerable to attacks.
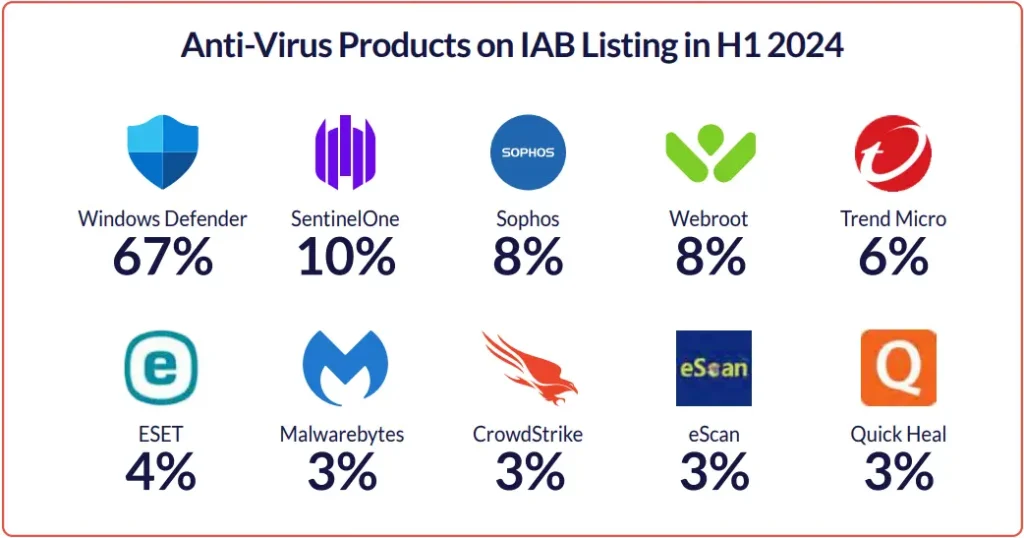
In 2024, the trend continues with initial access brokers predominantly offering machines for sale that only have the default Windows Defender as their security product.
It’s worth noting that there might be additional security measures on the compromised accounts that the broker either couldn’t detect or overlooked.
The presence or type of security product on a compromised account doesn’t necessarily reflect the value of the access or the organization itself. There are listings with only Windows Defender that are priced higher than accounts protected by three security products.
IABs are a critical part of the broader cybercrime ecosystem. They provide the necessary foothold for more destructive activities like ransomware attacks, data breaches, and espionage, effectively lowering the barrier to entry for less technically skilled cybercriminals who can purchase ready-made access rather than gaining it themselves.
Protecting yourself and your organization from IABs requires a multi-layered approach to security. Since IABs specialize in gaining unauthorized access to networks and systems, it’s crucial to implement both technical and organizational measures to minimize vulnerabilities.
By implementing these measures, you can reduce the risk of becoming a target for IABs and enhance the overall security posture of your organization.
Cyberint, the Impactful Intelligence company, reduces risk by helping organizations detect and mitigate external cyber threats before they have an adverse impact. The Cyberint Argos platform’s patented technology provides superior visibility through continuous discovery of the evolving attack surface, combined with the automated collection and analysis of vast quantities of intelligence from across the open, deep and dark web. A team of global military-grade cybersecurity experts work alongside customers to rapidly detect, investigate, and disrupt relevant threats – before they have the chance to develop into major incidents. Global customers, including Fortune 500 leaders across all major market verticals, rely on Cyberint to protect themselves from an array of external risks, including vulnerabilities, misconfigurations, phishing, impersonation attacks, malware infections, exposed credentials, data leaks, fraud, and 3rd party risks.

©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


